Steemit Crypto Academy, Season 3: Week 2 || Homework for Teacher @pelon53: Hash and Cryptography by @feliicia
My appreciation goes to the teams behind this project, and I want to appreciate the professor of this lecture of @pelon53.

Q1.- Explain what does the resistance to collision mean? And what does resistance to preimage mean?
Since resistance to collision and resistance to preimage are properties of hash function, then I will quickly like to define what hash function is.
Hash function is when a string of arbitrary length and a string of fixed length functions are compressed. A hash function is used to allocate and store a record from a file in a consistent manner.
What is Resistance to collision?
Collision resistance is comparable to the second preimage resistance, and as a result, collision resistance is sometimes referred to as "weak collision resistance." Nevertheless, a hash function must be at least 160 bits long in order to be considered collision resistant.
Collision resistance is a feature of cryptographic hash functions, which are primarily designed to prevent collisions. Nonetheless, certain hash functions that were formerly thought to be collision-resistant were later found to be ineffective. MD5 and SHA-1 specifically, are established algorithms that are more effective than brute force when it comes to locating a collision.
As a result, the majority of hash functions demonstrate that detecting a collision is as tough as solving some of the most challenging mathematical equations, such as quantum computation or discrete logarithms. The hash functions in question are referred to as "provably secure."
What does resistance to preimage mean?
Preimage resistance is a tough aspect of the hashing algorithm to turn. If a hash function is given within the range of a component, it is hoped that finding the input that match that element will be computationally infeasible.
The one-way hash function was first used in cryptography by Diffie and Hellman in 1976. A one-way function is a calculation function that has a simple direction but gets more challenging when reversed. Preimage resistance is similar to that of a one-way function, making file protection extremely simple.
To be preimage resistant, a hash function must have an output of at least 80 bits. Preimage resistance is distinct from second preimage resistance and collision resistance, which are both hash function equivalents. A hash function must first be preimage resistance and then second preimage resistance before it can be reffered to as being one-way
The output value repeats repeatedly due to preimage resistance. After that, selecting the hash function ensures that it is uniform. An attacker is tasked with making the hash function chosen work. The attacker wins if he or she can find the value in the preimage.
This means that the preimage hash function ought to be secure enough that an intruder won't be able to retrieve the output value's preimage. Because the intruder lacks secure variant knowledge of the hash function, this is the case. That definition may not be useful in practice because an attacker may be able to guess the strings even if they lack basic knowledge of the variant.

Q2.- Use tronscan and etherscan to verify the hash of the last block and the hash of that transaction. Screenshot is required for checking.
Using Troncan:
To verify the hash of the last block, we will be using tronscan.com for the verification.
- At the homepage, the information of block is displayed, one have to be fast with this because it takes a short time for another one to comes in. We can see the last block as I have highlighted in the screenshot below.
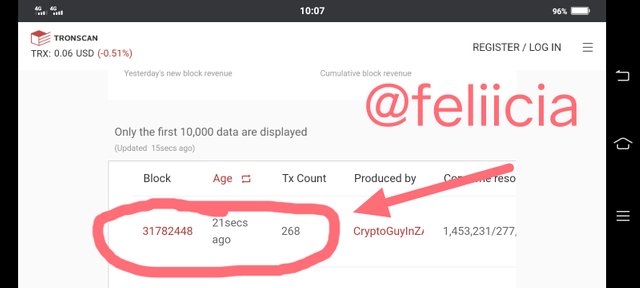
- To see the rest of the information for the highlighted block, click on the number of the block.
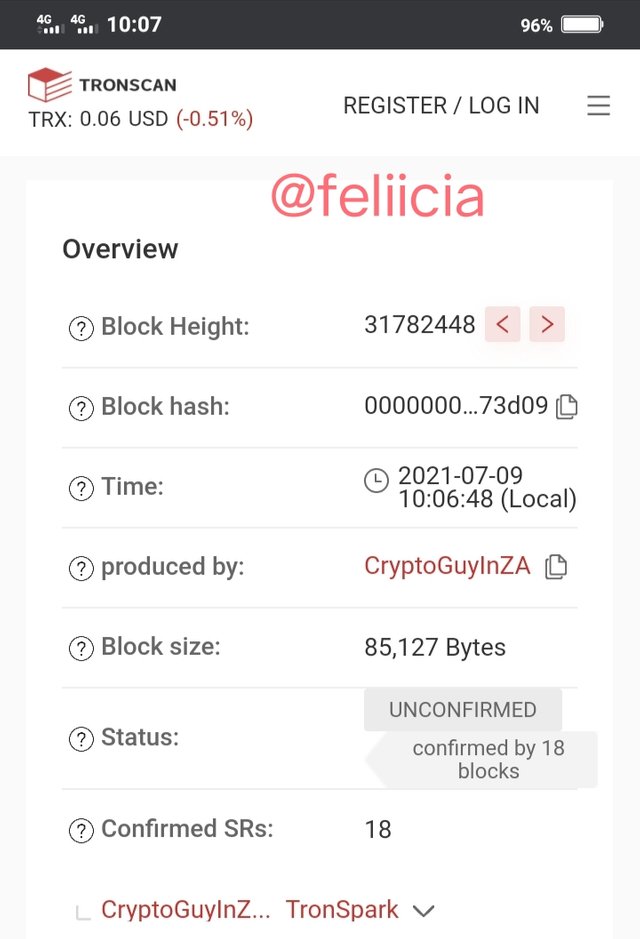
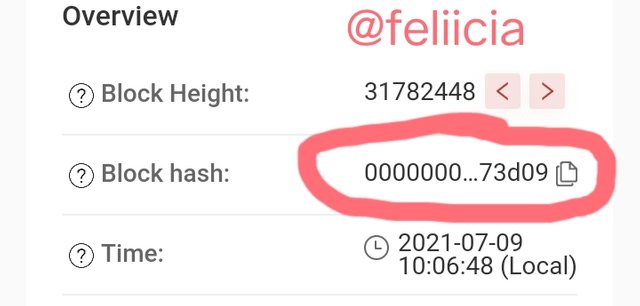
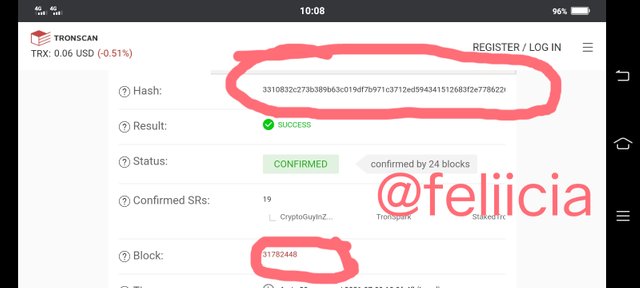
Therefore, the hash for the blok:31782448 Using the Tronscan is
0000000001e4f5b012441e289c35e0e1c7c4f309724c408d0417b7d8a87e158d
- To verify the hash of the last transaction, from the page last page where the block information was displayed, we will scroll down, and that is where we will find the hash of that transaction. Click on the hash and the full details will come up
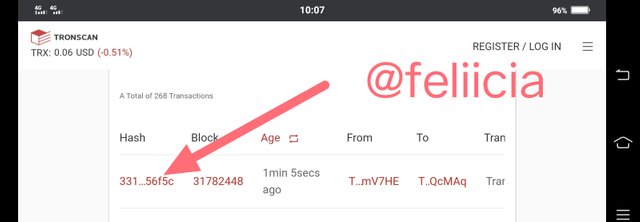
The hash for the last transaction is
3310832c273b389b63c019df7b971c3712ed594341512683f2e7786226f56f5c

Using the Etherscan
To verify the hash with Etherscan, the link: https://etherscan.io/ will be used.
- From the Homepage, we can see the recent blocks and the last one as shown in the image below
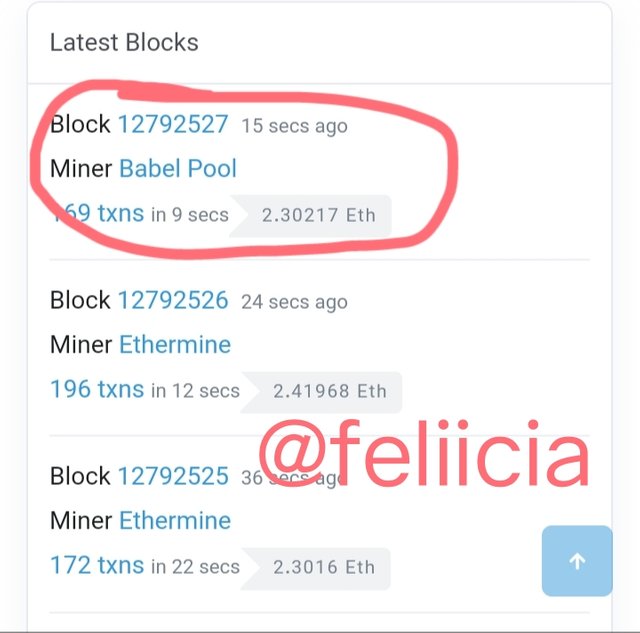
- When we click on that block, the block information will show up. There will will get the hash of the last block.
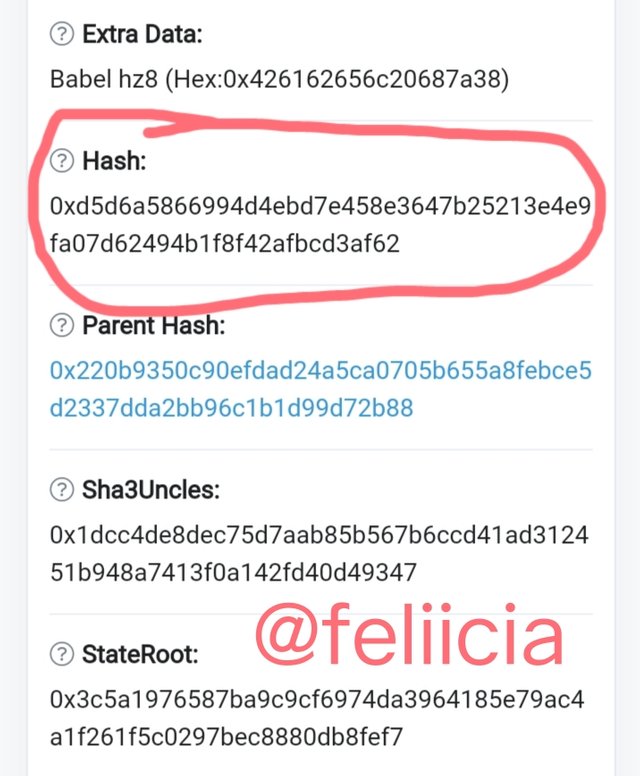
Hash of the last block: 0xd5d6a5866994d4ebd7e458e3647b25213e4e9fa07d62494b1f8f42afbcd3af62
- In the same page where we get the "Hash of last transaction", when we scroll up we will see the transactions in that blog and we click on it to see the last transaction.
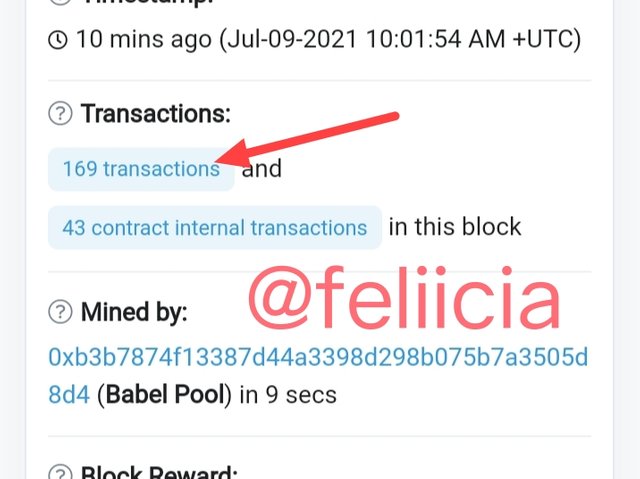
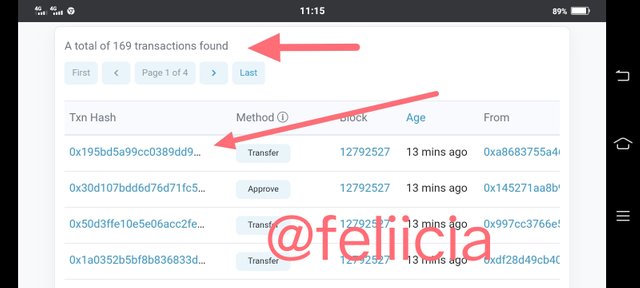
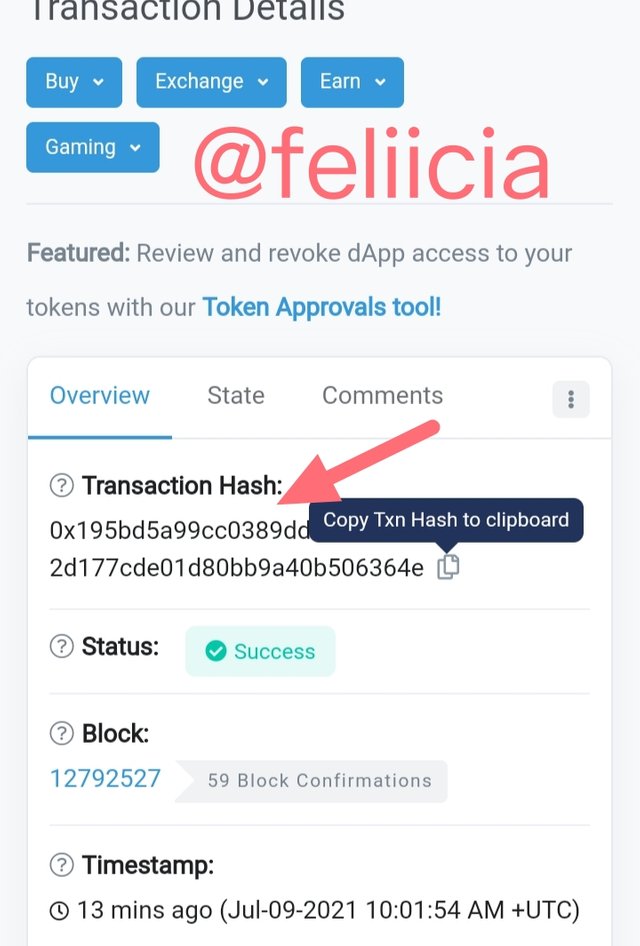
Hash of last transaction: 0x195bd5a99cc0389dd9cc83344b8d4da9f3e4e2d177cde01d80bb9a40b506364e
.png)
Q3.- Generate the hash using SHA-256 , from the word CryptoAcademy and from cryptoacademy. Screenshot required. Do you see any difference between the two words? Explain.
To be able to generate the hash for the two words, I will be using this link: https://passwordsgenerator.net/sha256-hash-generator/
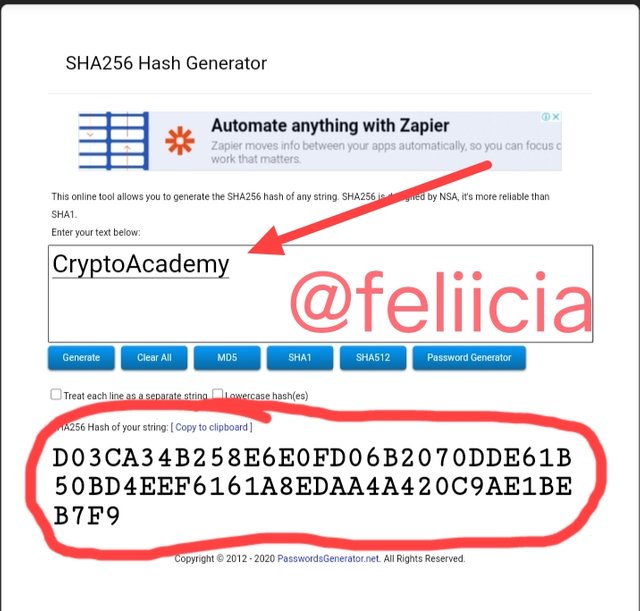
For the first word: CryptoAcademy
the hash is:
AD0783CC92D6D26EC1A4137EEA1A05CC89701F7FF6A07F1CEEE5D8B0C13285A4BB12339FEF0A7BB8674ED664496EC02FEF11CC86353FF99B656F4897EF3AA2AF
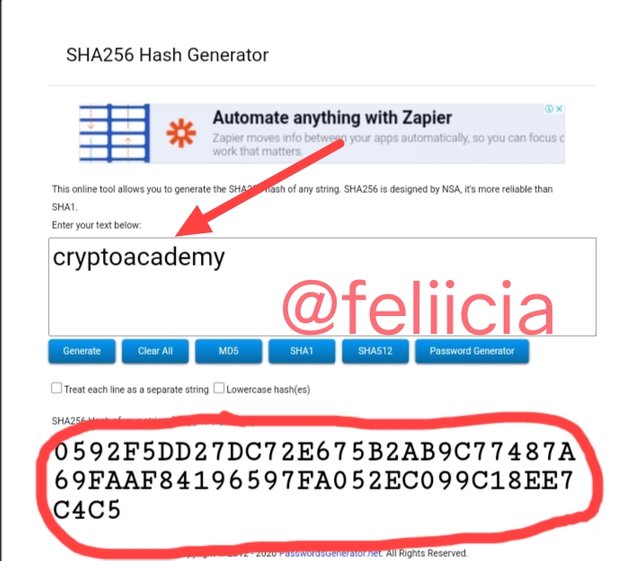
For the second word "cryptoacademy", the hash is:
0592F5DD27DC72E675B2AB9C77487A69FAAF84196597FA052EC099C18EE7C4C5
Observation:
The two words are different in the sense that one is with with two capital letters "CryptoAcademy" and the other one doesn't have any capital letter "cryptoacademy" and this is the reason why there hash is different.
.png)
4.- In your own words explain the difference between hash and cryptography.
What is hash?
Hash refers to a one-way procedure in which data is converted to a defined length called as a hash value using an algorithm (also known as a hash digest). Although the length of the hash created is normally fixed and less than the actual text or word, it varies greatly with even minor input alterations. Reverting a successful hashed digest back to its original state is nearly impossible.
What is Cryptography?
Cryptography is the method of converting data into a string of unreadable words of varying lengths. The main difference with cryptography and hash is that with the appropriate key, unreadable data may be decrypted to reveal the original plaintext data, whereas this is not possible with hashing.
The use of cryptographic keys allows data to be encrypted. Prior to transmission, the information is encrypted, and the user decrypts it.
hash can be used to authenticate the integrity of a data by identifying all modifications and converting them to a hash result, whereas Cryptography is the process of encoding data in order to keep it safe and secure. To reversibly convert encoded data to plain text, it involves a private key.
Cryptography is a two-way function that involves both encryption and decryption, whereas hashing is a one-way function that transforms plain text into an irreversible unique digest.
The Original content that has undergone hashing into an unreadable text cannot be converted back into its former readable text. In Cryptography, with the use of cryptographic keys, the encrypted data may be decoded and turned into a string of readable letters (unencrypted data).

.jpeg)

Gracias por participar en Steemit Crypto Academy Season 3:
Espero seguir leyendo tus publicaciones.
No explicas lo que es realmente la resistencia a la colisión.
Las diferencias deben ser más concretas.
Recomendaciones:
Explicar cada pregunta en forma clara y sencilla que otras personas puedan entender.
Las conclusiones finales son necesarias.
Calificación: 7.5