Crypto Academy Season Three Week Eight: Homework Post for @stream4u. : Let's Open The Cryptography.
Greetings everyone, I am delighted to be part of yet another exciting season of this homework assignment for our noble professor in the person of @stream4u.
This week, we have been taught another great lesson that is very delicate in the crypto world since it deals with important activities. That is to say, when we take a good look at the current world we find ourselves in, we need some level of privacy in our everyday dealings. When we want to communicate to individuals who are not close to us and we don't want any message leaking or getting to the wrong ears, there is a program that is possible in the crypto world. I hereby make my homework submission after understanding the lecture notes of our noble professor.
Explain the Blockchain CryptoGraphy and mention few names which are the Blockchain Platforms?
As I mentioned earlier, in this world we find ourselves in, we need a certain level of privacy in our everyday dealings that is when communicating with one another when distance is a barrier or factor.
When we talk of Blockchain Cryptography it is simply a situation in which a communication is made between two areas whereby the details of the communication are not changed nor made known to everyone. That is, blockchain cryptography makes it possible for information to be delivered from a sender to a receiver and this message or information is not leaked or changed. The whole concept of Blockchain Cryptography makes it safe in communicating since the message can't be accessed by anyone unless the recipient in question has the key to be able to read and understand the message or information.
Moving further, the concept works in such a way that, when the message is been sent to a particular recipient, the individual sending the information or message makes encryption to the data or information. This makes the data change from the normal human language to that of machine language. By so doing, it is not understandable by anyone but only the specific receiver who will be able to make decryption to the data with the correct key used. When this is done, the message or data is then sent back to normal human form for the receiver to be able to understand the text involved.
As we know, Blockchain is every secured technique in this world. The Blockchain Cryptography also makes it very safe in communicating with people and also it, therefore, maintains privacy among individuals.
In the crypto ecosystem, the cryptocurrencies we have operate on the concept of cryptography which is the key cryptography whereby the use of the private and public key happens.
These are:
- Steem Blockchain
- Ethereum Blockchain
- TRON Blockchain
- Ripple Blockchain and so on.
Explain the Public Key CryptoGraphy.
The Public Key Cryptography works along with that of the Private Key. That is, they are in pairs in such a way, it is used to tell which receiver is the message directed to. Also in the Public Key Cryptography, the private and public key works together for the encrypting and decrypting of messages and also transactions made. The Public key is made known to the public and does not cause any harm to the 'srecipient's safety. The Public Key operates with that of the Private in such a way that, when a message is to be sent to a specific destination, the public key is been encrypted with that of the message and then sent. The receiver then uses his or her private key which is in line with the public key to decrypt the message and then understand its details.
The Public key is the combination of numbers and alphabets, as well as hash functions to create public addresses for the making of transactions.
Moving further, public key cryptography is used in the signing o transactions. This is done with the presence of the Private Key. As a result of this, it is referred to as asymmetric Cryptography since it operates alongside the Private key.
In summary, we can say that the Public Key Cryptography is used in the encrypting of messages in such a way that, the sender and the receivers's public keys are used in the encrypting of the message whiles the receiver's private which is linked with that of the sender's public key is used to decrypt the message to be able to understand the details.
In addition, when we look at the concept of the creating of digital signatures, the private keys are used to create such digital signatures whereby the individual involved with the linked public key can be able to gain access to the details of the digital signature and the message involved.
The Public Key Cryptography really serves a good purpose to the blockchain in such a way that, it protects the safety and the privacy of information that is been sent from one source to another. It also goes in a long run to make sure that, the messages which are been sent from one source to another are nothing but the real and actual ones since we have digital signatures involved in the process.
Explain the Private Key CryptoGraphy.
In the Private Key Cryptography, this concept does not operate with different keys but rather only one key which is not shared to everyone but only the two sources involved. That is, only one key which should be known between the two sources involved must know the details of the key and not the general public. This key is used for the processes of encrypting and decrypting messages sent between the two parties involved.
Moving further, in the Private Key Cryptography, there is a generating of a key which should be known by the sender and receiver since they will use it in the encrypting and decrypting of messages going to be communicated. That is, the parties or individuals have to come together to generate this key which will be known to only the parties involved.
The private key contains a combination of numbers and alphabets which together. This key is used to keep safe the wallets of users to make sure transactions made are safe and free from any harm. This Key is also needed in the signing of transactions made on the blockchain.
Therefore the Private key is used by the receiver for the decrypting of the messages or data or transactions made by a sender since this key should be kept private and should not be disclosed to anyone. The Private Keys are mostly saved in software and are used for the signing, verification, and creations of transactions made.
Explain the Digital Signatures CryptoGraphy and what is Singing Of Transaction/Message?
When dealing with issues relating to finances mostly the key identity used to make sure the dealings are valid is the use of the signatures. That is since we have various signatures which people can't copy or fake, they serve us the gateway to our fund's security.
When we come to the digital world that is dealing with cryptocurrencies, Digital signature cryptography is the concept whereby there is a generating of a hash to verify transactions that is made on the blockchain platform. This signature is done by the addition of private keys and that or public keys to sign and alongside verify transactions that are made on the blockchain platform. This is done to ensure that, the actual receiver who is also verified gets hold o the details of the information or transactions made.
The Digital signatures undergo two processes for it to be able to be qualified or for the transactions to be verified and completed.
That is the authentification of the sender's details. This involves the creation of encryption hash and also private keys. This process ensures the Transactions made to be real or actual and not ake.
The next one involves the validity and verification of the transactions or information. Here, the public keys and the digital signature which are signed are checked and corrected in case of errors or any misfunctions. It, therefore, ensures the verification of the information of the transactions made.
The Signing of a Transaction is the act of making good use of the private keys by making an addition of digital signatures to a transaction made on the blockchain. This is done to show that the transaction made is valid and correct from any error. The process begins by the generating of a hash making good use of a hash function whereby the sender puts in the hash value by signing it digitally. The data is then sent to the destination for verification to be carried out. The Public Keys in then used for the verification of the data whereby the hash value is then created. In the verification proces feedback is received which is then compared with the hash value to ensure the validity of the signature.
Explain what is Symmetric and Asymmetric cryptography?
In Cryptography, we have some two types of processes or technologies involved, these are the Symmetric and Asymmetric Cryptography. I will therefore make an exploration of these two types below.
Symmetric Cryptography is a type of cryptography in which one key is used in the encryption and decryption of data to be able to understand its details. In this type, we don't have a private or public key involved but only one key called secret key is used which is known among the parties involved. This will enable the users involved to be able to encrypt and then decrypt the data or message been carried across.
This single key know as the secret key is used by the sender to send the data or message across, this message or data is encrypted into a machine language format with the help of the single key and the data or message is then broadcasted on the blockchain platform. The destination of the message or the receiver then uses the same secret key to decrypt the message into a normal form to be able to read and understand the content.
This type of cryptography is an advantage in such a way that, there is a faster transfer of files and also the small space needed for storage. This is as a result of the small energy needed for the computational of the symmetric key algorithm.
However, in a situation where there are a lot of individuals involved, there will be a lot of keys needed in which the keeping of these keys will be a problem.
Some examples of Symmetric Cryptography include International Data Encryption Algo, Advance Encryption Standard, and so on.
Furthermore, Block and Stream Symmetric Cryptography are the types of cryptography we have. With the Block type of symmetric cryptography, the encryption of data or information is made at a specific size. These data are saved in blocks until the encryption is completed. The Stream on the other hand is a type of symmetric cryptography whereby the encryption of the data or information is made at a continuing pace and then broadcasted on the blockchain without saving the encrypted data like the Block symmetric cryptography.
In this type of Cryptography, two keys of different content are needed for the encryption and decryption of data or information in the blockchain platform. That is, these keys should be linked together in such a way they should be related. These keys are the private and the public keys. The keys are used in combination for the decrypting and encrypting of data or information on the blockchain network. The Private key should not be disclosed to any individual apart from the individuals' involved whiles the public key is distributed to nodes that are connected in the blockchain network. The Public Key is used for the encrypting of data or information whiles the Private key is used for the decrypting of the data to be able to understand its details.
Moving further, the nodes which are connected in the blockchain makes a change of the public key which the sender uses for the encryption of the data or information and also makes an addition of a digital signature and finally makes it available to the platform. The recipient then uses the private key which is related to the public key to decrypt the data or information to be able to understand its details. The two keys are used to generate public addresses when used together with hash algorithms which are very safe and secured.
Asymmetric cryptography is of advantage in the sense that, small keys are needed to undertake a transaction even when there are a lot of individuals involved. It is also very secured and also safe from any harm.
However, there more energy is needed for the computational for asymmetric key algorithm thereby making it very slow and more space needed for storage.
Some examples of Asymmetric cryptography include Digital Signature Standard (DSS), River Shamir Adleman, and so on.
How Blockchain Wallets CryptoGraphy works and explains the available types of Crypto Wallets.
In the crypto space, we have certain software programs that keep the keys of the blockchain platform, that is the public and the private keys. These keys are made available only to their keys pairs types. These keys serve as the gateway to the wallets in the sense that, they are used hand in hand to perform a transaction on the blockchain platform. The Public key of the wallet is used in the collection of funds whiles the private key of the wallet is used to claim ownership of the wallet and also adds signatures to a transaction made on the platform.
Moving further, we have to take note of the fact that, crypto-wallets addresses cannot be the same, and also they do not have stored in them any cryptocurrency but only the details of the history of transactions made in the blockchain platform. Just like the traditional world in terms of the banking system, there are situations of hacks, this is also present in the crypto wallet in a situation whereby the private key is been hacked by someone all the funds are gone to waste.
The Crypto wallet addresses are created by using hash algorithms and also public keys which makes them very safe from any harm. The signing and verification of transactions is doen by using the private keys and the hash algorithms. The signing is made digitally in this case.
In the crypto space, we have Software wallets, Hardware wallets, and Paper wallets as the types of crypto wallets.
Also, wallets have been categorized in two forms which are known as cold and hot wallets. Cold wallets are wallets that are stored offline where are Hot wallets are wallets that are stored and connected to internet access.
As the name implies, they are wallets that use software programs to store keys and that of crypto assets. With this type of wallet, an internet connection is required to be able to gain access to the various assets that are been stored in them. These crypto-assets or keys are been ran on digital devices. For instance, we have web wallets, desktop, and mobile wallets as some examples of software wallets.
On the contrary to the above, hardware wallets are wallets that save keys offline. That is unlike the software wallets, hardware wallets do not need an internet connection or online connection to store keys or assets, and also, no connection is needed to gain access to the stored or saved content.
This type of wallet is just like the hardware wallet but with this type, the keys or crypto assets are stored in a document form. This wallet type is not safe since the document can be missing at any point in time.,
What is the Merkle trees and What its importance in blockchain?
Merkle Tree is a diagram or structure that contains different blocks of data which are in presented in a tree like form. The Merkle Tree was brought into the crypto space by one Mr Ralp Merkle in the year 1979. The Merkle tree was brought up so as to help in the vefrication of data in a very fast manner. The Merkle Tree has been of great help in the blockchain platform.
The Merkle Tree begins with the top block been the Root has which goes in that other of where all the other hashes of the transactions are involved. The Merkle Tree gives miners the chance to verify transactions in a simpler way or manner.
Moving further, The Merkle tree is comes in form of the root been at the to and the leafs at the bottom with branches at the middle. The leafs are known as leafs nodes. In the merkle tree, the leaf nodes represents various transactions hash that are made and they are entered into the block. Moving to the branches level, the hashes are then combined into pairs till they come together to form the Root Hash. At the Root hash, all transactions in the tree structure presents a specific length of hash. This therefore helps in the safe keeping of data in the blockchain platform. The Merkle Tree also goes make the verification of transactions simple by the reduction of energy consumption, the space or storage consumption and so on.
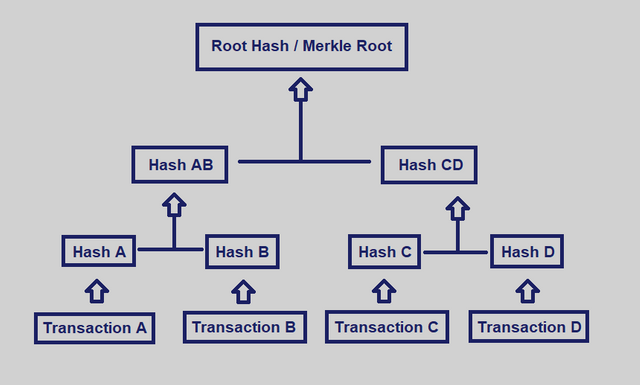
From the above Merkle Tree, The Transactions of which have labeled has Transaction A,B,C and D with the leafs nodes been Hash A, Hash B, Hash C and that of Hash D. These represents various transactions with different details involved.
Moving further, the branches aspect cab be seen in the sense that the leaf nodes have been paired to form Hash AB and also Hash CD in different blocks. The final aspect is the top is the Root Hash which is seen as the Merkle root this is the combination of all the four hashes. This will enable the verification of transactions made very simple and easy.
Whne the leaf nodes are odd in number, the transactions at the final aspect will be doubled.
- The Merkle Tree is of important to the blockchain is a sense that, it makes the validation of transaction data very simple and great.
- The Merkle Tree also help in the reduction of data storage space needed for the validation of transaction made on the blockchain.
- The Merkle Tree also goes in a long run to help reduce the time needed for the validation of transactions made on the blockchain.
Practical + Theory, do some practical research, study on Blockchain Demo: Public / Private Keys & Signing and then explain the functionality of Key, Signature, Transaction, Blockchain with proper screenshots of yours practical. (Do study well for this topic)
With the aspect o cryptography specifically the asymmetric cryptography, two keys are needed or the encrypting and decrypting of data or messages to be sent and received. These keys should have a relation between them in a sense that they are supposed to be linked together. With the help of this link I will practically show that the Privat keys and the public keys have a link in such a way that, every new private key brings up a public key.
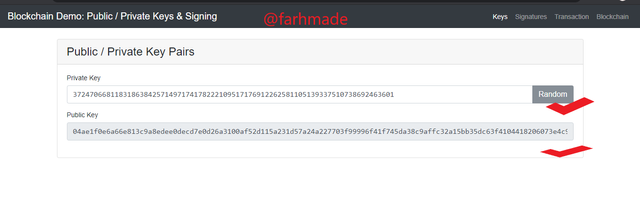
From the screenshot above, it can be seen that a Private Key which was had just by random process along side a Public Key.
Private Key
37247066811831863842571497174178222109517176912262581105139337510738692463601
Public Key
04ae1f0e6a66e813c9a8edee0decd7e0d26a3100af52d115a231d57a24a227703f99996f41f745da38c9affc32a15bb35dc63f4104418206073e4c94dc1a81314c
Moving Further, I will generate a new Privagte Key to see if there will be a new generation of a Public Key again to help explain the concept that every new Private Key produces a new Public Key.
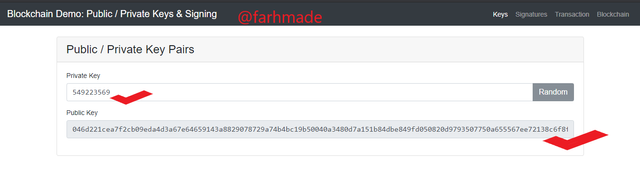
From the screenshot above, it can be seen that I generated a new Private Key which also brought about another New Public Key. This shows that a New Private Key Brings about a New Public Key.
New Private Key
549223569
New Public Key
046d221cea7f2cb09eda4d3a67e64659143a8829078729a74b4bc19b50040a3480d7a151b84dbe849fd050820d9793507750a655567ee72138c6f8ffccdcdebc57
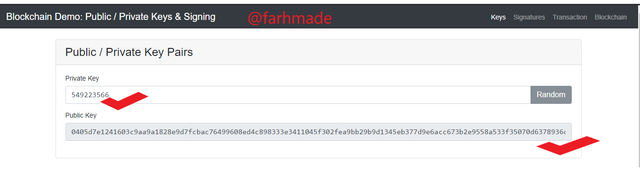
I made another change to the Private New to generate a new one which is shown below and this brought about another new Public Key. This is enough evidence that for any Private Key, there is a Public Key linked to it.
New Private Key
549223566
New Public Key
0405d7e1241603c9aa9a1828e9d7fcbac76499608ed4c898333e3411045f302fea9bb29b9d1345eb377d9e6acc673b2e9558a533f35070d6378936c2cb0be09f30
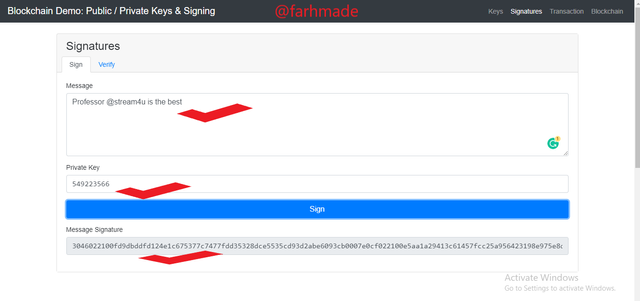
Moving further to this aspect, I will make a singing of a message with my private key 549223566 which I generated from the above exploration. The Message to be signed is Professor @stream4u is the best. After Putting in the message, I clicked on the sign button to conitune.
Message Signature
3046022100fd9dbddfd124e1c675377c7477fdd35328dce5535cd93d2abe6093cb0007e0cf022100e5aa1a29413c61457fcc25a956423198e975e8d621c95a67e3963ad5802d5f18
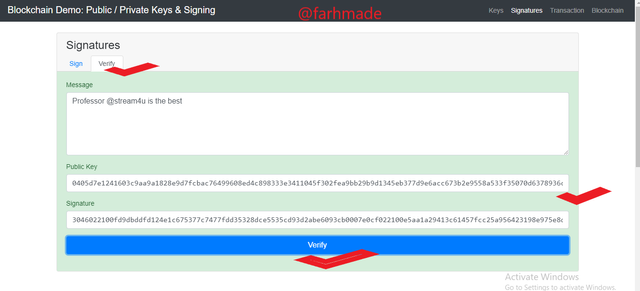
Moving further, the Verification of the message is then done by putting in the related Public key to the Private Key entered and then click on the Verify button ti validate the block by the colour changing to green to show that.
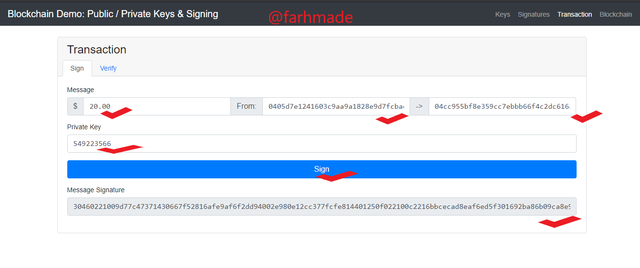
Moivng to the Transactions aspect, I am to make a transaction of $20 from a wallet to another wallet which their addresses are shown below.
Private Key Used In The Transaction
549223566
From Wallet Address
0405d7e1241603c9aa9a1828e9d7fcbac76499608ed4c898333e3411045f302fea9bb29b9d1345eb377d9e6acc673b2e9558a533f35070d6378936c2cb0be09f30
To Wallet Address
04cc955bf8e359cc7ebbb66f4c2dc616a93e8ba08e93d27996e20299ba92cba9cbd73c2ff46ed27a3727ba09486ba32b5ac35dd20c0adec020536996ca4d9f3d74
Message Signature
30460221009d77c47371430667f52816afe9af6f2dd94002e980e12cc377fcfe814401250f022100c2216bbcecad8eaf6ed5f301692ba86b09ca8e93b7cd1e23042bdced10260f3a
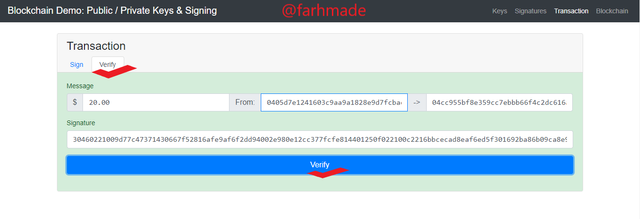
Moving further, we now verify the transaction by putting in the message signature and then clicking on the verify button. The Block beomes verify by the colour changing to green. This shows the transactions has been confirmed and gone through.
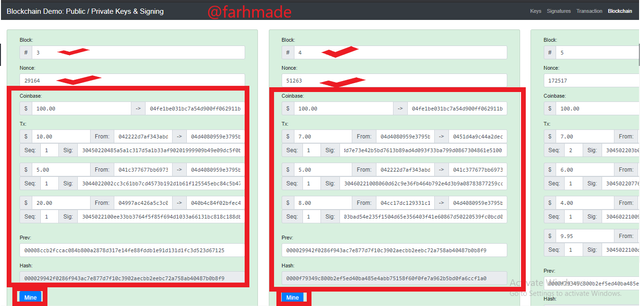
Moving further to the Blockchain area, I am going to make an exploration on the various transactions and how they are saved on the Blocks and the Hash created. The Trasactions are stored in blocks with the Hash functions s a cryptography entity.
The Screenshot above shows the various valid blocks of 3 and 4 with their details off transactions and that o the Hash.
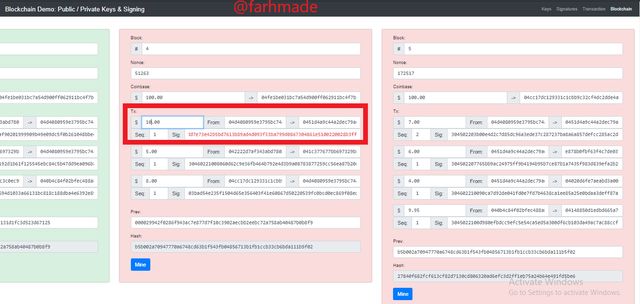
Moving further, changes are going to made to the transactions of Block 4 to see what will happen. The current amount there is $7 which I am going to change to a new amount o 10$ to see what will occur in the Blockchain.
From the above screenshot, it can be seen that, Block 4 and that of Block 5 has changed from green colour to Red colour indicating that it is is invalid as a result of the changes made. The changes made to the Block 4 had an effect on the Block 5 indicating that when a Block is invalid the preceding Block also becomes invalid since for a Block to valid it is dependent on the previous block hash. That is when a hash of a block is invalid it has an effect on the following Block since the previous validity of the Hash has an effect on the following Block.
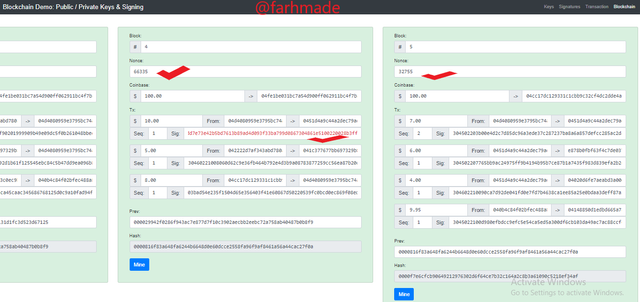
To make the Block to be Valid, we need to re-mine Block 4 and that off Block 5 for it to be validated. The validity o a block depends on the Nonce of it. Therefore, the Nonce are chnmaged by re-minign the block to make it valid. We have to note that, the Signature will still remain invalid as a result of the variety of Private Key and Public Key that was used in the signing off the transaction at the initial exploration.
The Nonce of Block 4 and that of Block 5 are 51263 and 172517 respectively. After the re-mine, the new Nonces became 66335 and 32755. This can be seen in the screenshot below.
In a nut shell, the security and Privacy has been of great deal as result of the existence of the concept of Cryptography. Cryptography has made the Blockchain very safe and the privacy level to very high. The issue of wrong data and also transaction does not exitsi on the Blockchain as a result of the existence of Cryptography since every activity carried out on the cryptography is been validated before.
The Symmetric and Asymmetric aspect of the cryptography which entails the keys that are been used in the signing of the transactions. The Symmetric needs only one private key for the encrypting and decrypting of messages or data whiles Asymmetric cryptography needed the private key and the public key for the encrypting and decrypting of data or messages.
Moving further, the digital signature has made the cryptography very secured as well since one is able to sign transactions or documents.
There isn't any possibility of changing the details of transactions made or messages sent as a result of the presence of the Hash which is from the Hash functions. This makes the cryptography very safe and secured.
I am pleased to be part of this great lesscon of our noble professor in the person o @stream4u for this great lesson thought which has enlighten my knowledge in the crypto space.
Thank you or your humble attention.
Best regards @farhmade.