Steemit Crypto Academy, Season 3: Week 2 || Hash and Cryptography for @pelon53

Good day all, I want to first thank @pelon53 for this wonderful lecture that focused a lot on what has and cryptography is all about. These two are a vital part of the blockchain world.

1. Explain what does the resistance to collision mean? And what does resistance to preimage mean?

Before we start answering the question, let’s define what is a hash cause a hash is something that links both topics we were asked about
What is a hash?
A hash is a unique group of alphanumeric characters generated specifically for a particular group of words using what is called a hash function.
A hash function is a function that resizes any amount of data to a fixed size group of alphanumeric characters called a hash. This when applied in blockchain allows large information in a block to be collected into a fixed number of alphanumeric characters.
The unique nature of a hash for a particular group of words makes it that only the same group of words can Produce a particular so any alteration will result in a change in hash
The history of the hash function can be traced far before the creation of the first blockchain. It was in the early 1960s that the first set of hash functions came into existence through Hans Peter Luhn. It has evolved through the MD’s series until the RIPE series came into existence with the aim of replacing MD4
The MD series were not necessary very secure but the ripe series were created to solve the security problems of MDs.
The latest model of hash function been used is the SHA hash function produced in 1993. SHA means secure hash algorithm and it is regarded as the most secure of all the hashes. The SHA model is very famous and it is the SHA-256 model that is used in the blockchain world.
We are going to talk about some characteristics of hash functions which were asked by our prof @pelon53 which are resistance to collusion and resistance to a preimage

WHAT IS RESISTANCE TO COLLISION

It is normal for two different actions or reaction processes to give rise to the same product. This may be normal in life but this happening in a business setting means someone can use a different key to access another’s money. The need to avoid this was part of the reasons hash was used in cryptocurrency.
Resistance to Collision is a characteristic of a hash function where two different inputs can’t give the same output. Like I said above hash for a group of words is unique to it. No other word can generate this same hash. Since nothing in this world is 100% we can say that these characteristics of hash mean that it is 99% impossible for different inputs to give the same output.

Resistance to preimage

Another feature of hash is - resistance to preimage. What is a preimage, this is the ability to see what makes up content like let’s use cake, the preimage of a cake is the flour, sugar, etc used in baking the cake.
So resistance to preimage means that the hash system doesn’t allow one access to the information that generated the hash quite easily. When I said quite easily, it means that it can be found out but it takes time and high-level computing to get the contents.
This feature of hash is highly applied in mining where the hash of data needs to be solved but this feature of preimage makes it very hard so, it takes only a fast and good and a supercomputer to solve the problem of figuring the data that generated the hash

NO2: Use tronscan and etherscan to verify the hash of the last block and the hash of that transaction. Screenshot is required for checking.

We are going to start with tronscan.org. Transaction on tronsacn.org is many with each transacting in miniseconds. When I wanted to do this assignment, the transaction I was able to screenshot was the stakedtron transaction . So we will be using it for this example
- First of all , we open the site www.tronscan.org and click on blocks.
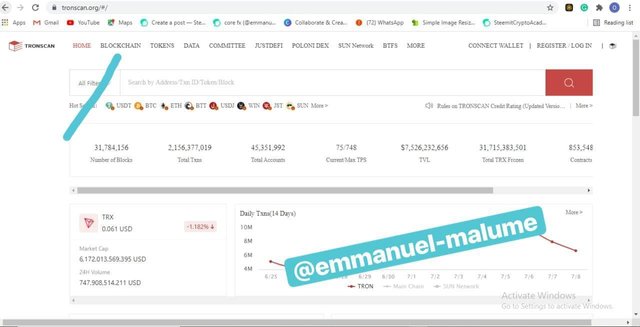
SCREENSHOT GOTTEN FROM TRONSCAN.ORG
2.A set of recent blocks appeared and the most recent at the time of this screenshot is produced by staked tron which we clicked to check the hash of the transaction and hash of the block
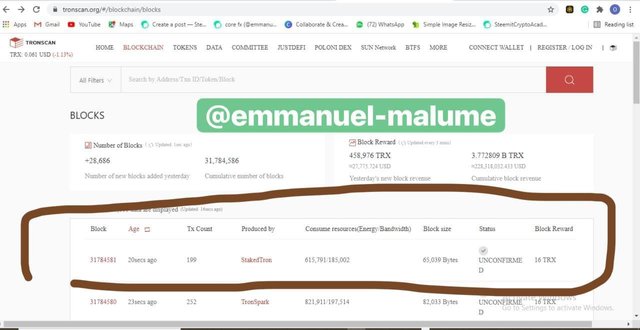 SCREENSHOT GOTTEN FROM TRONSCAN.ORG
SCREENSHOT GOTTEN FROM TRONSCAN.ORG3.Upon clicking on the transaction, a page opens that shows the hash and some details about the transaction and we copy the block hash -0000000001e4fe85b57c0a3529b5a90973a9deb07e20a4db23e4ed635684cb41
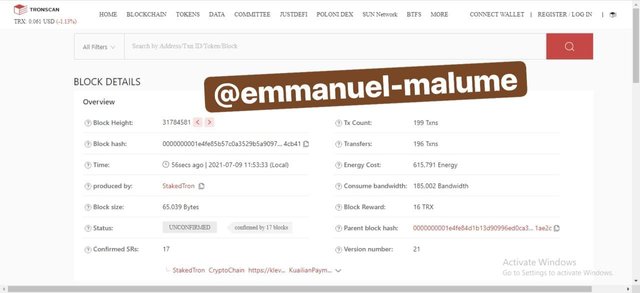 SCREENSHOT GOTTEN FROM TRONSCAN.ORG
SCREENSHOT GOTTEN FROM TRONSCAN.ORG4.To verify the transaction, we scroll down to where transaction details are displayed and clicked on that particular transaction and copy the hash there
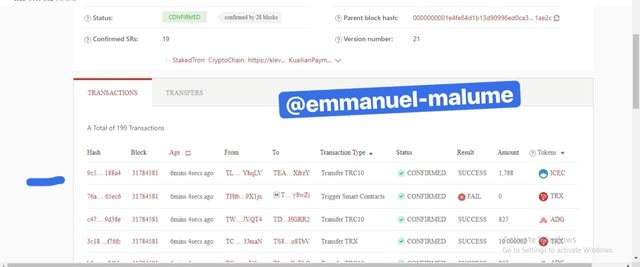 SCREENSHOT GOTTEN FROM TRONSCAN.ORG
SCREENSHOT GOTTEN FROM TRONSCAN.ORG5.Upon clicking a page opens that shows that the transaction was successful while showing the hash of the transaction which is 9c51cdbee2c93029bf39fa8ccaa331398e381869f4070b5bf049e772930188a4
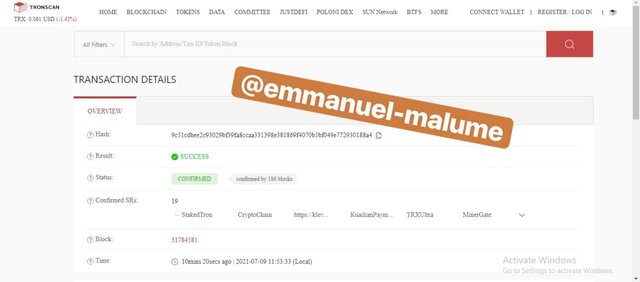 SCREENSHOT GOTTEN FROM TRONSCAN.ORG
SCREENSHOT GOTTEN FROM TRONSCAN.ORGlink for transaction details-https://tronscan.org/#/transaction/9c51cdbee2c93029bf39fa8ccaa331398e381869f4070b5bf049e772930188a4


1.Firstly we go to the site https://etherscan.io/. This site shows a lot of details about etherum from its coinmarketcap to number of transaction and price
SCREENSHOT GOTTEN FROM etherscan,io/
2.Click blockchain and then click on blocks
SCREENSHOT GOTTEN FROM etherscan,io/
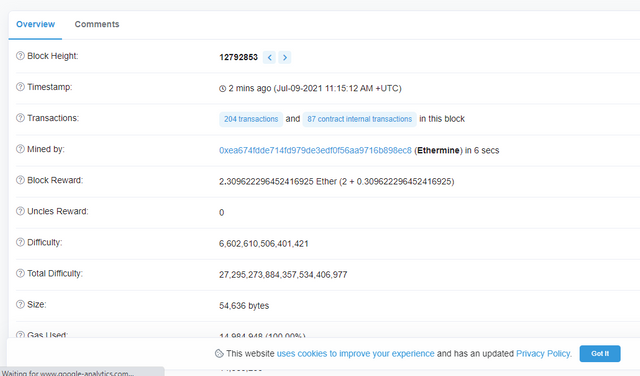
3.From the screenshot we took at the time of doing this assignment we would be using the block mined by ethermine
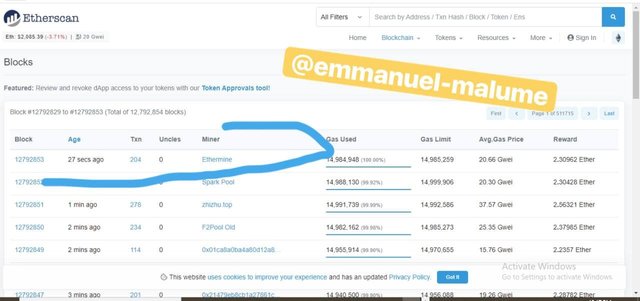 SCREENSHOT GOTTEN FROM etherscan,io/
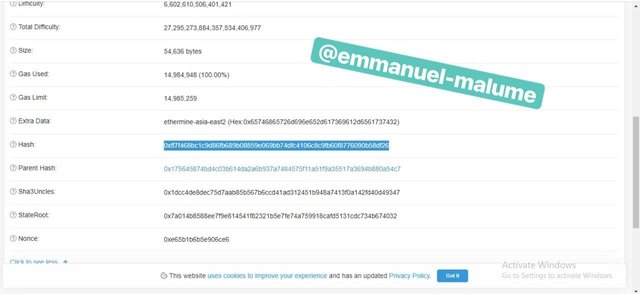
SCREENSHOT GOTTEN FROM etherscan,io/4.We click on the newly formed block and then we see the details contained in it from its block height which is
12792853 to gas limit of transaction. our focus is on hash of block which is gotten by scrolling down and clicking on more data and then we copy the block hash -
0xff7f468bc1c9d86fb689b08859e069bb74dfc4106c8c9fb60f8776090b58df26
 SCREENSHOT GOTTEN FROM etherscan,io/
SCREENSHOT GOTTEN FROM etherscan,io/5.To locate the transaction hash, we go back up to where we are seeing 204 transaction and click on it and a page appears and then a page opens and we click on the latest transaction and copy the hash
 SCREENSHOT GOTTEN FROM etherscan,io/
SCREENSHOT GOTTEN FROM etherscan,io/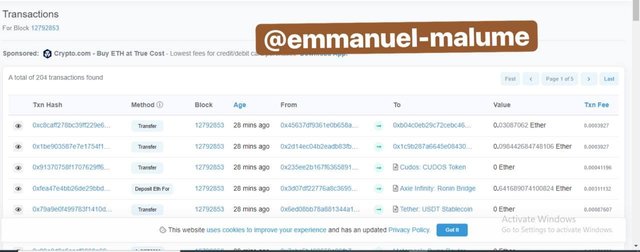
SCREENSHOT GOTTEN FROM etherscan,io/
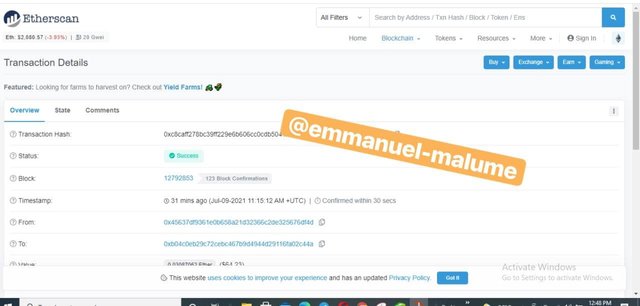
6.We copy the transaction hash there and we have --0xc8caff278bc39ff229e6b606cc0cdb504123490c997c914bd028c4fdcf8c3218 for the hash
SCREENSHOT GOTTEN FROM etherscan,io/
link for the transaction detail -https://etherscan.io/tx/0xc8caff278bc39ff229e6b606cc0cdb504123490c997c914bd028c4fdcf8c3218

NO 3: Generate the hash using SHA-256 , from the word CryptoAcademy and from cryptoacademy. Screenshot required. Do you see any difference between the two words? Explain.

Generate the hash using SHA-256, from the word CryptoAcademy and from crypto academy. Screenshot required. Do you see any difference between the two words? Explain
- we visit this site https://passwordsgenerator.net/sha256-hash-generator/
 screenshot from source
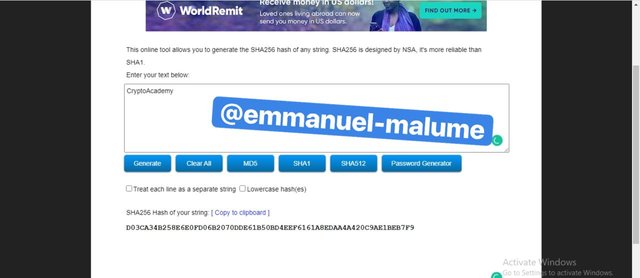
screenshot from source2.We start With the first word ‘CryptoAcademy’ and the hash generated
 screenshot from source
screenshot from sourceIt gave the following hash-D03CA34B258E6E0FD06B2070DDE61B50BD4EEF6161A8EDAA4A420C9AE1BEB7F9
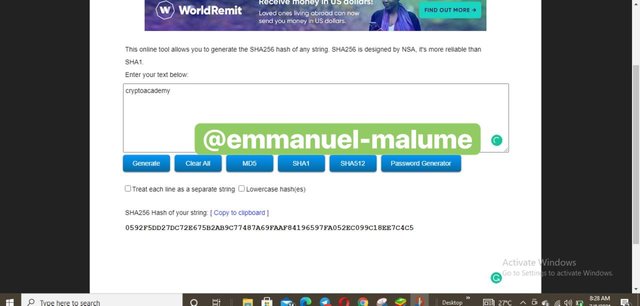
3.For the next word which is ‘cryptoacademy’ , let’s look at the hash generated
 screenshot from source
screenshot from sourceThe hash generated-0592F5DD27DC72E675B2AB9C77487A69FAAF84196597FA052EC099C18EE7C4C5
From what we can see above, as much as the two words are the same. There was a change in capital letters at ‘C’ and ‘All, a change at these two points altered the hash generated for the word even though they are the same. When we talked about hash function properties, we said about resistance to a collision where it’s impossible for two different inputs to give the same output and this is clearly seen here. Provided there is a slight difference in the input, a new hash is generated for it

NO 4: In your own words explain the difference between hash and cryptography. To avoid repetition the explanation of hash has been given before the first question.

In this question, we are expected to differentiate between has and cryptography. We have earlier defined what a hash is above. now let's talk a little about cryptography
Cryptography is a process of bypassing third parties in transactions. It is the process of making sure only the sender and receiver could decode the message. This way of preventing third-party interference required the use of keys .
Originally there was only one type of cryptography which was the symmetrical type where only one key was used and it was very fast in transaction speed aspect but it had this problem that the key can be compromised by either the sender himself or the receiver cause the both of them needed to have it.
This lead to the creation of a new version where two types of keys were used. The public and private keys.
it was slower than the symmetrical and this led to the creation of hybrid cryptography that combined the good features of symmetrical and asymmetrical types
| HASH | CRYPTOGRAPHY |
|---|---|
| There are no keys | Keys are used |
| It is used to resize any amount of information into a fixed number of characters | It’s used to remove third party interference |
| The message in it can be easily interpreted once one has the keys | It takes a long time even centuries to decode a hash and know the data inside it or the use of a very super-fast computer |
| Represents only a particular set of information | The keys can give access to variable information which can be updated |
| A hash function is used to generate it | There is no hash function used here |


This class really educated me on what hash is and cryptography. It is quite noting that the steemit continuity runs on hybrid cryptography where two keys are used and transactions are fast. Cryptography is something that the blockchain needed to increase its integrity and also allow one to perform a transaction without needing a third party. Thank you @pelon53 for this great lecture
Gracias por participar en Steemit Crypto Academy Season 3:
Espero seguir leyendo tus publicaciones.
👆Realmente es evitar que eso ocurra. Es la menor probabilidad de permitir que 2 entradas diferentes generen el mismo hash.
Recomendaciones:
Entender lo que lees al investigar, te dará mejores resultados en las respuestas dadas.
Cuando sea difícil ver el resultado, debes copiar y pegar, o simplemente anotarlo. Debe estar en un sitio visible.
Calificación: 7.7
Alright thank you sir I will take the correction and improve on the report