Crypto Academy / Season 3 / Week 8 - Homework Post for [@stream4u] | Let's Open the Cryptography
Continuing learning in steemit cryptoacademy, today i am writing homework task for professor @stream4u which is about "opening of cryptography".
Explain the Blockchain CryptoGraphy and mention few names which are the Blockchain Platforms?
Blockchain cryptography is a technology that ensures encrypted communication between two parties. Blockchain cryptography is a secure means of communication between two parties in a codified language to preclude access from malicious third parties. Cryptography converts a readable form of text to a coded or ciphered text that is not readable by humans unless decrypted with the help of keys. The inherent features of blockchain when combined with cryptography ensures data integrity, authenticity and confidentiality of highest level possible.
To put it simply, blockchain cryptography is a technological advancement that has evolved to avoid spying of private communication of any level between two parties. Hacking of emails has become a talk of town now day in and day out. Email is a means of private communication channel between two or multiple users involved in the thread. But it is not a secure means of communication because any malicious users can gain access to your inbox and stole the data. On the contrary, blockchain cryptography converrs your message to a non readable text for malicious third party users but readable for your peers who hold the key to convert non readable text to readable form.
This seemingly fascinating concept has its darkside too. It has raised suspicion of espionage and sedition among authorities in our centralized system of administration. However, to keep the sanctity of the concept alive, we may have to face some problems.
The concept is gaining popularity in diverse fileds like communication, DeFi, Dapps etc.
Some of the leading blockchain platforms are Ethereum, Steem, Fantom, EOS, REEF, Neo and Tezos etc.
Explain the Public Key CryptoGraphy.
Public key as the name implies is a alphanumeric cryptographic code that is cryptographically hashed to produce public address which is used to receive funds into the Crypto wallets and can be shared with anyone. Message is codified with the help of private key but decrypted with the help of sender's public key . Private and public key are interrelated and randomly generated on blockchain. Change in private key leads to chamge in public key and thereby public address. Any attempt to forge these keys invalidate the transaction.
So the take home messages are ;
Public and private key are cryptographic codes.
These keys are interconnected and change in one leads to change in other.
Generation of private key from public key is not computationaly feasible to forge the data .
Private key gives proof of ownership as shown by signing transactions and encryption of data.
Public address is recipient address used for receiving funds and decryption of messages.
Explain the Private Key CryptoGraphy.
Private key as the name implies is a key specific to user account which give users an ownership over account . Any compromise in private key means compromise In users account. so this is a sensitive code which need to be handled with care. Private key cryptography involves only secret key for encryption and decryption.
So the take home messages are ;
Private key is a unique cryptographic codes.
Private key entitle you to ownership.
Compromise in private key snatches your ownership.
Private key gives proof of ownership as shown by signing transactions and encryption of data.
Private key is the sole source which is used to generate signature of a transaction .
**
Explain what is Symmetric and Asymmetric cryptography?
Assymetric cryptography.
Whitfield Diffie and Martin Hellman proposed this concept of cryptography in 1976. This cryptographic system involves two keys namely public key and private key. As is clear by the names that public key can be shared with others just like email id. You can share your email id to recieve mails. Whereas private key is a secret key like a password of email id which is used to access the mails recieved.
In public key cryptography, a user sends his message to amother user. The message is converted to a unreadable text by making use of public key or we can say that message is encrypted with the help of public key and sent. Recipient cannot read this cryptographically coded message unless decrypted. So recipient will make use of private key to decrypt the message. So the importance of private key is reinforced.
Although private and public keys are related to each other but it is not possible to decipher one from other. Had it been like that, than no body would share public key with any one.
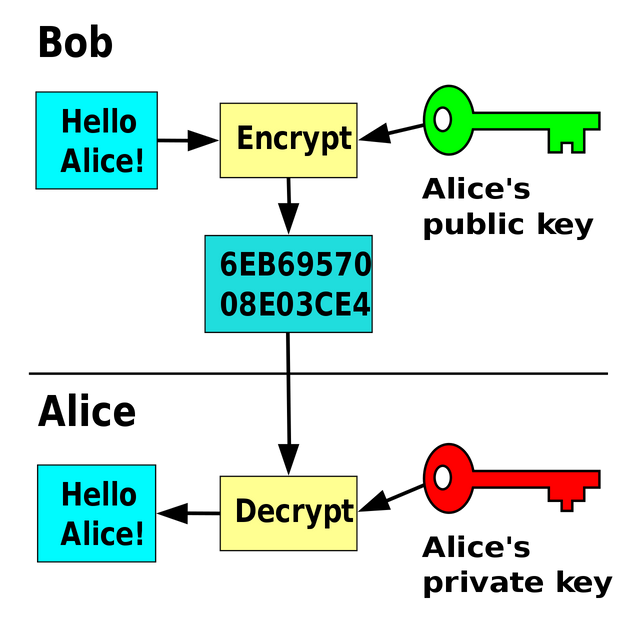
We can see in the above image that Alice encrypted the message with the help or public key amd BOB deceypred it with the help of private key.
Symmetric key cryptography.
In symmetric key cryptography , only private keyis involved to encrypt or decrypt the message unlike assymetric key cryptography where encryption is done by public key and decryption by private key. Here sender and recipent need to share the privare key before communication. This system of cryptography is faster than public key cryptography.
The problem with private key system is that here we need to share keys and key management is also difficult because number of keys that are to be manage is large. For example, to establish communication between 4 people say, A, B, C and D. number of required are six.
A___B
A ___C
A___D
B____C
B___D
C___D
So to generalize, for n mumber of individuals n (n-1) /2 keys are required. Example, for 10o people, 100(100-1) /2 = 9900/2= 4950.
In assymetric key cryptography, 100 individuals require only 200 keys.
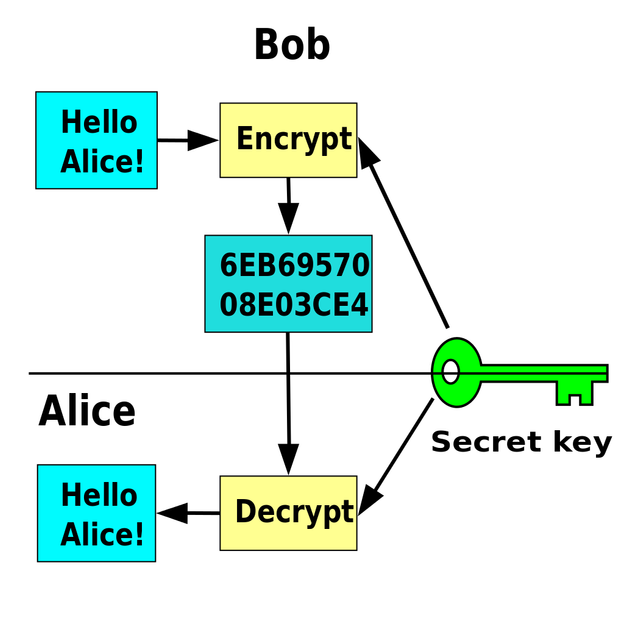
We can see that in the above example, Alias and BOB sharing the same secret key to encrypt and decrypt the message.
There are two variants of symmetric key cryptography. In one variant the whole information stored in a block is ciphered or encrypted. Where as in other vairnat the indiviuual streaks or threads of text is ciphered. We can easily correlate former one in blockchain because we know that blocks form the basic storage unit of information.
Explain the Digital Signatures CryptoGraphy and what is Singing Of Transaction/Message?
A digital signature is an electronic comuterpart of handwritten signature intended to serve the purpose of validation and verification of a message. We know that every official documemt
Is signed by concerned authorities at the end to authenticate the document. Similarly, to authenticate online data, concept of digital signature has unfolded.
Digital signature cryptography is therefore an algorithm to produce digital signatures on the documents and therefore is an additional layer of security. Digital signature is generated with the help of private key with respect to information to be sent. Digital signature is not fixed to a user, which means, that you do not have a same signature all the time but it keeps on changing with the message. So digital signature is a mathametical code unique for each message. Recipient than uses the senders public key to verify the authenticity of the signature.
Once a sender produces digital signature, he cannot refuse production because it is verifiable with the help of keys. In addition, the blockchain attaches timestamp to the transaction too that is another safety factor in place.
When compared to the handwritten signature, digital signatures can't be forged because for that sander's private key is needed. The message and signature are interconnected in a way that if signature is changed, messages becomes invalid and changing message without changing signature can be grave but it is computationally infeasible.
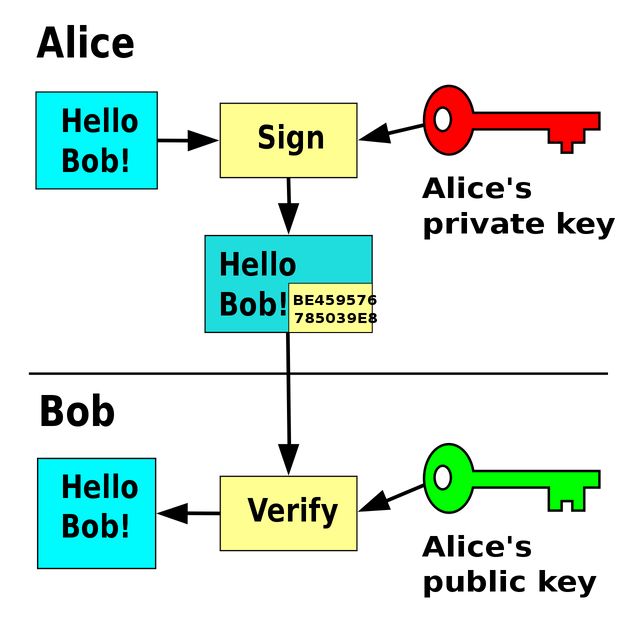
We can see that communication between Alice and Bob above making use of private key by Alice to produce a mathematical code as a signature and use of Alice's public key by bob to verifiy the signature and decode the message.
How Blockchain Wallets CryptoGraphy works and explains the available types of Crypto Wallets.
Working of Blockchain wallet cryptography .
Blockchain wallets are digital wallets used to store , send, and recieve digital assets or tokens. The wallets are secured with cryptographic codes known as keys. Each wallet has a public key and private key. Public key is analogous to bank account number which can be shared with anyone without harm. Public key is shared with the recipient to receive funds into the wallet . Private key is used to sign the transaction and therefore give a proof of ownership. Another type of key is known as mneumonic or seed key that help to export both private and public keys. Private key is analogue to banking password or pin which is used to finalise the transactions.
Types of wallets.
- Hot wallets : Hot wallets are the type of wallets that are connected to internet . These wallets are easy to use but are susceptible to web based attacks and are therefore less secure than cold wallets. These wallets are available as desktop or mobile apps. Example, exchange based wallets.
Cold Wallets : These wallets are not connected to internet and are therefore more secure than hot wallets. Example, paper wallet.
Software wallet : These wallets are run on software installed on desktop or Mobile. These wallets are inexpensive, easy to install and operate.
Hardware wallet : A type of wallet that comes in the form of hardware devices like pendrives. Example includes Trezor, KeepKey etc. These are safe as they are not connected to internet.However they are expensive and have difficult learning curve.
Single Chain wallet : These wallets support only one digital currency or tokens of only one blockchain like MyEther wallet support only Enterium blockchain tokens.
Multichain wallets : Such type of wallets support digital currencies of multiple blockchains like Trust wallet.
Custodian or centralised wallets : It refers to a type of wallet where user doesn't operate the wallet with the help ot private key but with the help of password set by them. These wallets have a Central authority to have absolute control over your funds as they have access to your private keys.
Non custodian or decentralised wallets : These wallets don't have any governing authority. You are owner of your wallet as well as your private key. You have absolute
control over your funds.
What is the Merkle trees and What its importance in blockchain?
Merkle tree is a graphical representation of cryptographically encrypted data in the form of hashes gifted by Ralph Merkle in 1979. The basic structure of tree begin from leaf to branches than to root. Each leaf node of the merkle tree is formed by single hash and the first branch is binary ( combination of two leaf node hashes) and second order branch is combination of first order branches . The concentration of hashes continues untill we reach root hash or master hash. Merkel tree has gained popularity for its enhanced security and simplification of data verification.
Let's suppose we are having data from which we have to construct amerkle tree.
Let's say we habe data like;
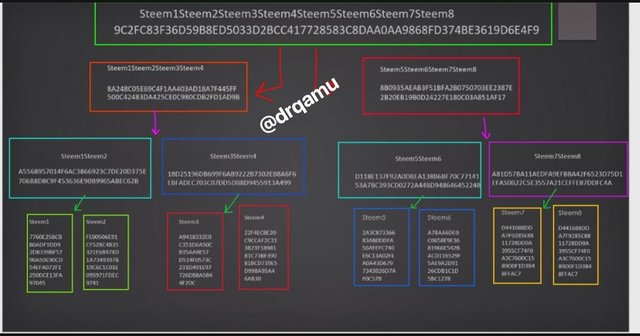
steem1 steem2 steem3 steem4 stee5 steem6 steem7 steem8
Its merkle tree would be like
For details of construction of Merkel tree, click here and read from my old post.
Importance of Merkel tree.
It has simplified the data verification process.
it enhanced security of blockchain as wrong info is easy to filter.
In terms of storage capacity needed, Merkel tree requires less space as well as less computational power.
Practical + Theory, do some practical research, study on Blockchain Demo: Public / Private Keys & Signing and then explain the functionality of Key, Signature, Transaction, Blockchain with proper screenshots of yours practical. (Do study well for this topic)
Let's go to blockchain demo website and gain some experience on keys. We can see that we have private and public keys there. These are randomly generated alphanumeric combinations that are interconnected in a way that as for their generation is concerned, change in private key results in change in public key.
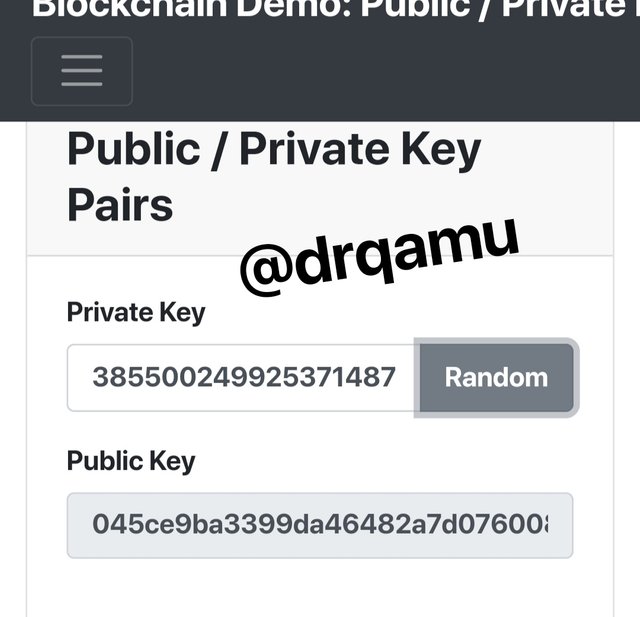
Let's click on Random and see the results.
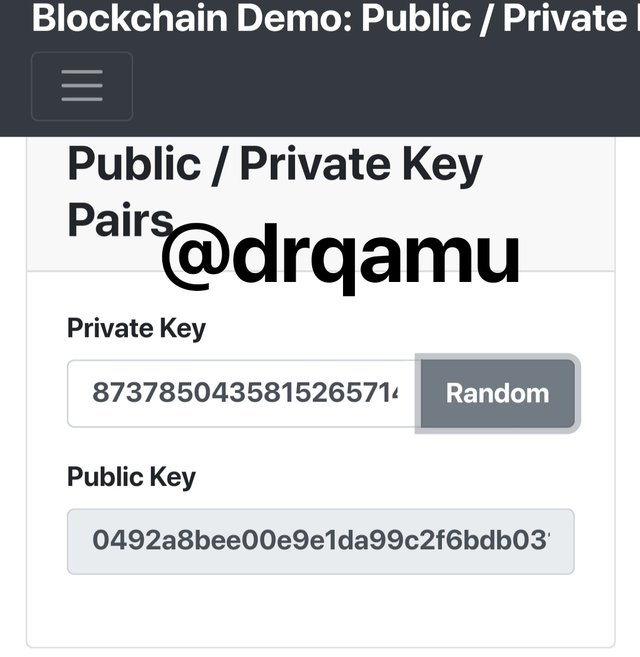
We saw that, new set of keys are generated.
Signature.
As mentioned above that digital signatures are mathematical algorithms assigned to each message.. It is generated with the help of private key. Let's type any message, say 'Hello , what's up? " and click on sign .
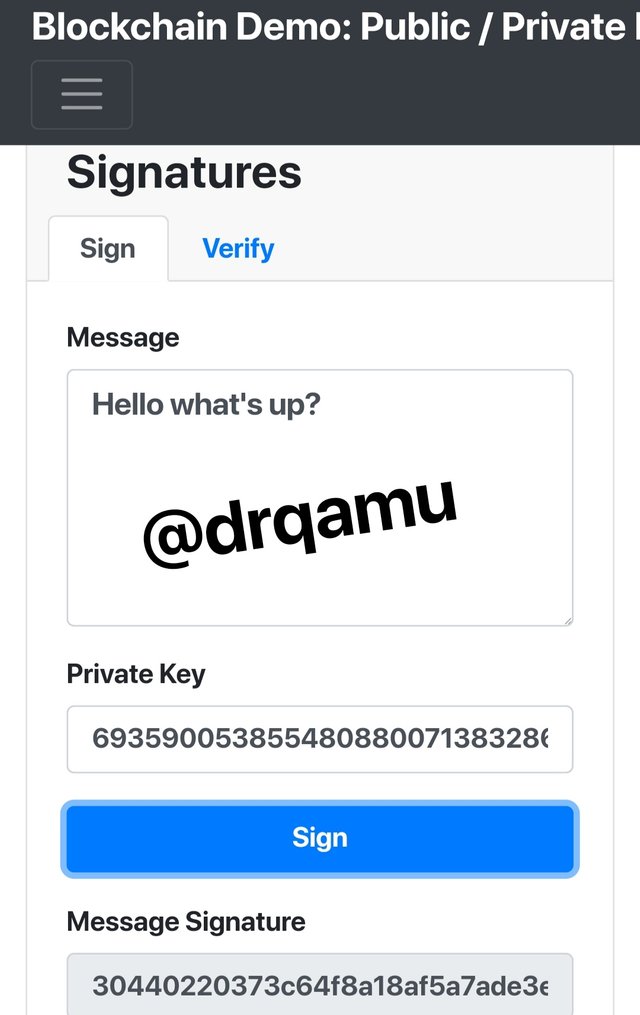
We saw that a digital code or signature was generated and is tied to the message.
Message
Hello what's up?
Private key
69359005385548088007138328680231208316762416321230095749683464695966745804522
30440220373c64f8a18af5a7ade3ee733c174a7cc396990dbc340ad5eed5efc3c8e6e21a02200830ab5d8a1528e6f60f333697d705d2aa4d4c138f862e1200244cad65138f32
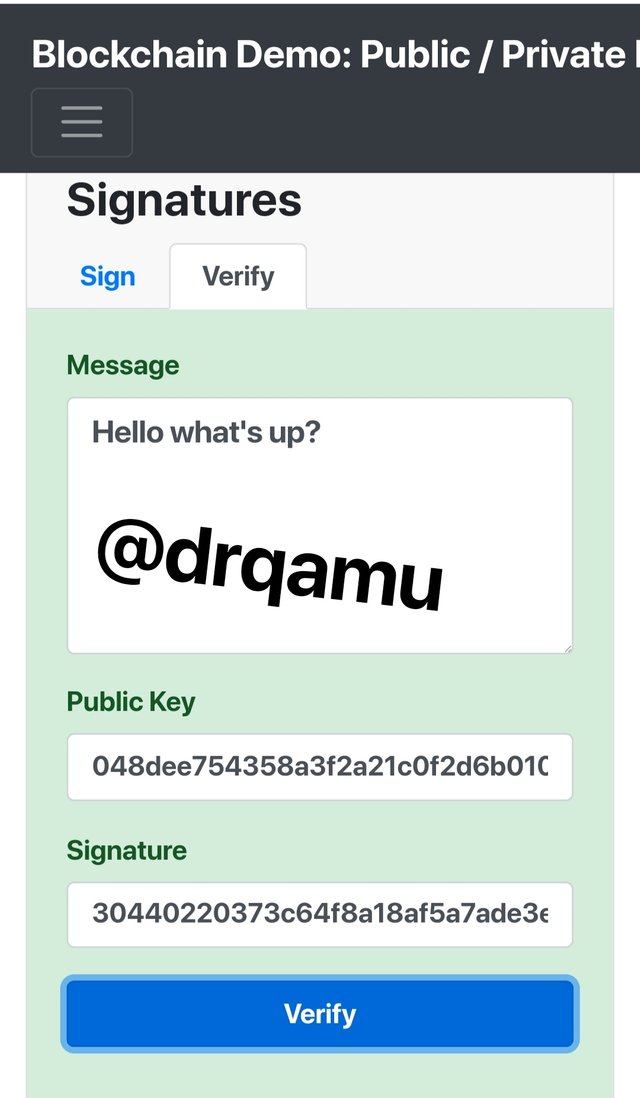
Let's try to verify the authenticity of the data with the valid public key and signature
Public Key
048dee754358a3f2a21c0f2d6b010dc35a2e73b2ec88aa593fda469fb674bf6514f54e77af875374649e8a84a537861daca1ed1aa8e76d960989062104cfbb48d6
Signature
30440220373c64f8a18af5a7ade3ee733c174a7cc396990dbc340ad5eed5efc3c8e6e21a02200830ab5d8a1528e6f60f333697d705d2aa4d4c138f862e1200244cad65138f32
Click Verify and we see no color chamge.
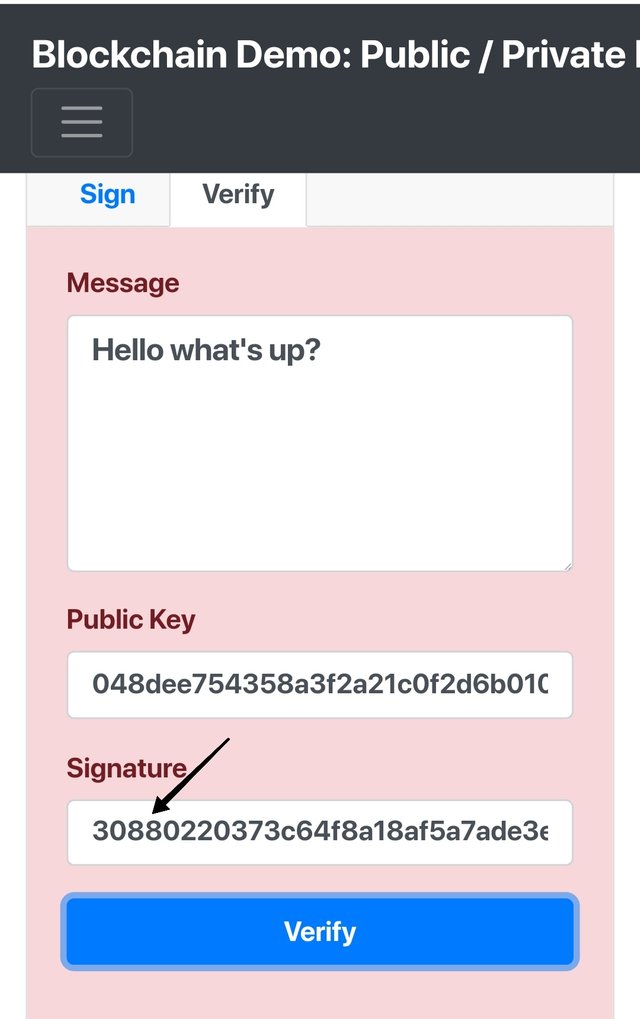
Data forging
Let's try to change signature from 3044 to 3088 and keep message as it is and click verify and note the color chamge to red indicating forgery.
Now let's try to change the message with correct signature and click verify. Again we noticed that transaction is invalid as indicated by color change to red.
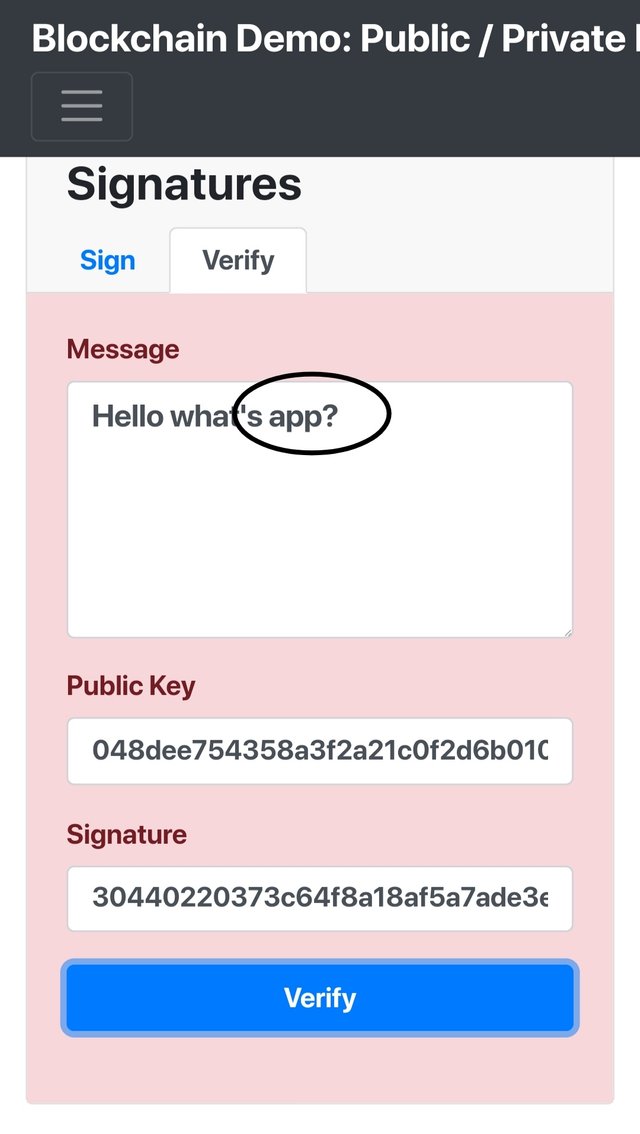
So the impertance of digital signature is emphasized.
Transactions.
Let's try to perform a demo transaction worth 10$ with following details and
Sign the transaction.
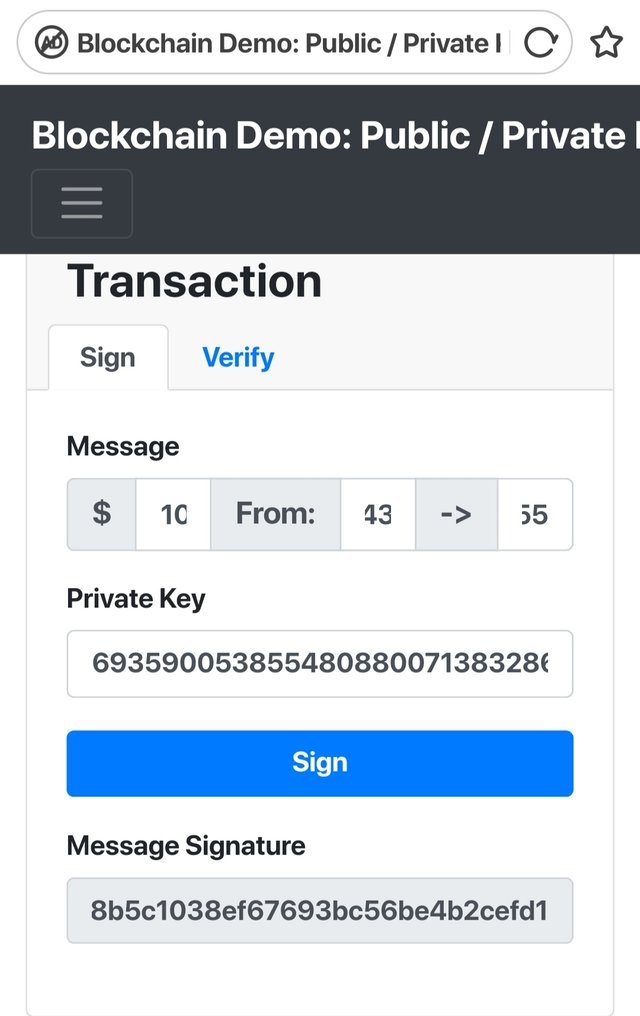
Message
$10
From:
048dee754358a3f2a21c0f2d6b010dc35a2e73b2ec88aa593fda469fb674bf6514f54e77af875374649e8a84a537861daca1ed1aa8e76d960989062104cfbb48d6
->
04cc955bf8e359cc7ebbb66f4c2dc616a93e8ba08e93d27996e20299ba92cba9cbd73c2ff46ed27a3727ba09486ba32b5ac35dd20c0adec020536996ca4d9f3d74
Private Key
69359005385548088007138328680231208316762416321230095749683464695966745804522
Sign
Message Signature
304302202eb589d8a80338bb05d6611ef66190ae2ffeb1fbe623b4c76ca7ed3e88ca05b2021f44edbcac93cbffb1837d2e25a1b7814eb8b5c1038ef67693bc56be4b2cefd1
Let's try to verify the transaction with the valid details and than we will try to forge the transaction and verifify.
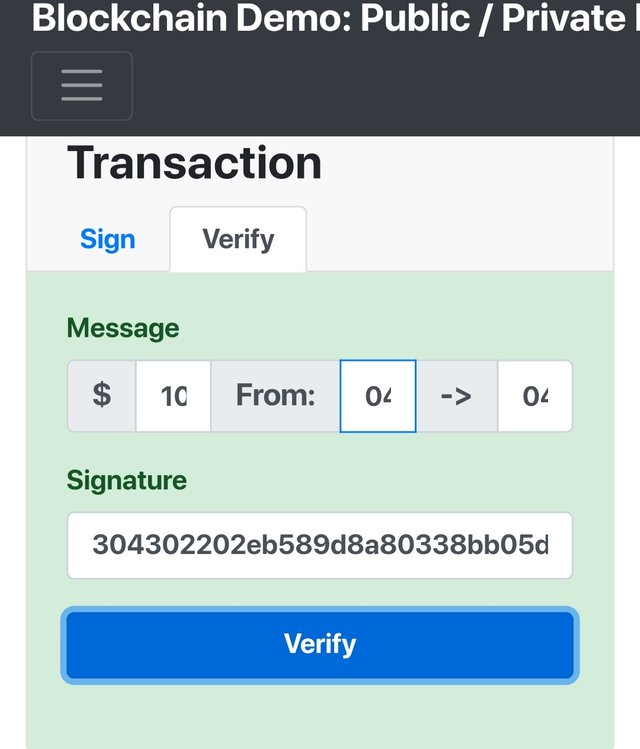
Valid transaction verified
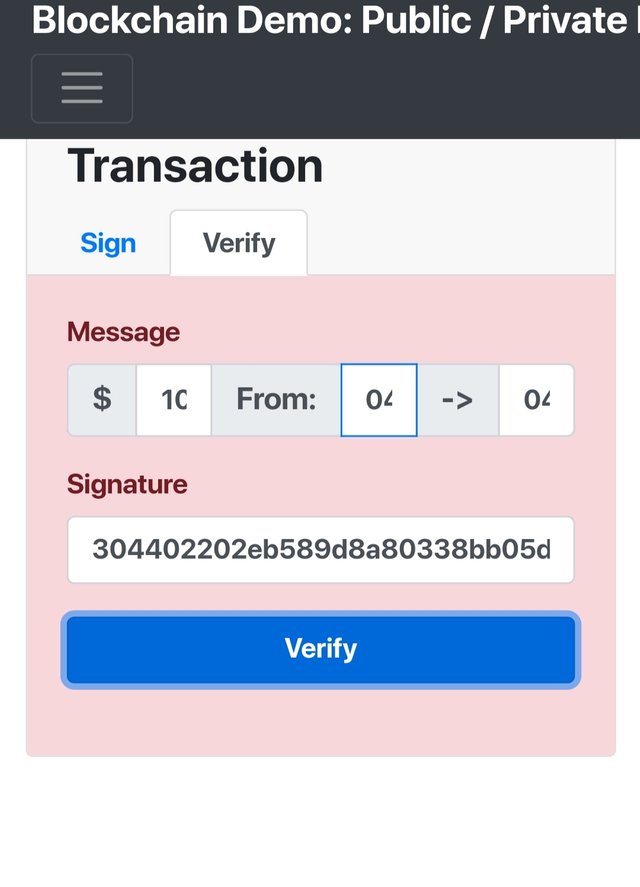
Forge the signature.
On changing signature from 30430 to 30440 , we saw the transaction turned out to be invlid.
Forge the amount from $10 to $20.
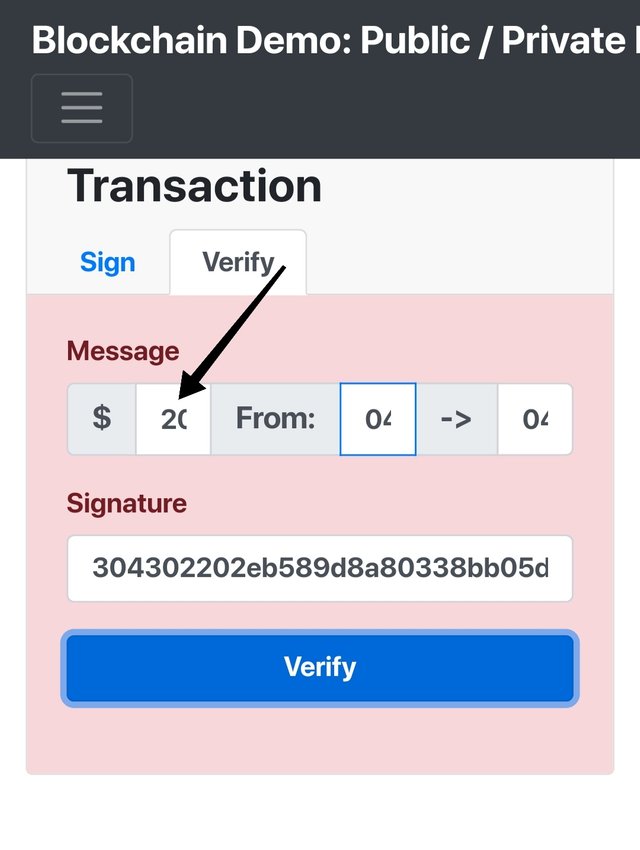
So the Significance of transaction along with details like amount, address, signature is emphasised.
Blockchain
We know the basic framework of blockchain is that transaction details are stored in the for of blocks. Each block has a unique hash and a hash of previous block connects blocks to each other. Each block has a unique number called nonce. Chamge in any details of the block invalidates the transaction.
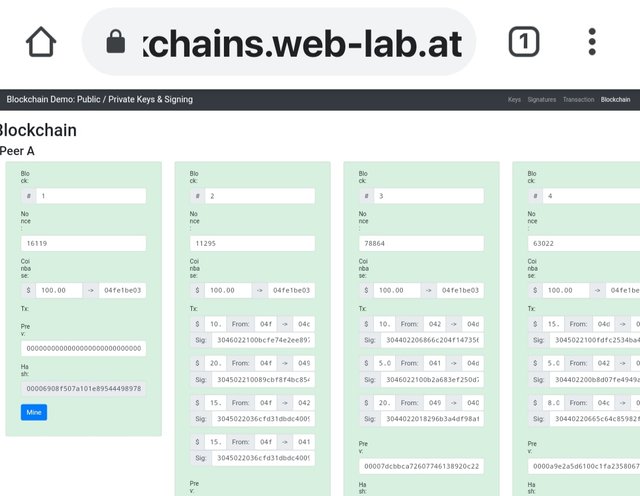
Valid details
Forging nonce.
As i changed nonce of block 2 from 11295 to 11296 , block 2 and subsequent blocks were invalidated.
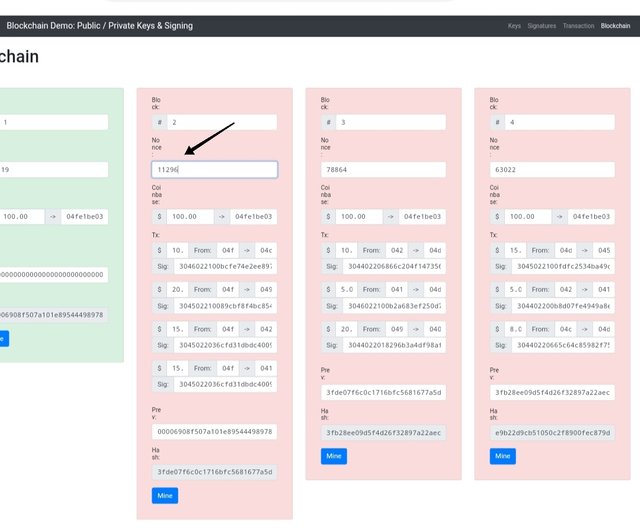
Click on mine and nonce is reset to what it was.
Changing the hash and amount invalidates the blocks similarly and every time we click mine, correct details are refilled im the respective columns. This emphasize the power of blockchain.
Conclusion. (The overall understanding of CryptoGraphy)
Cryptography is a technique of converting a human readable form of text to machine readable text for ensuring secure communication in the world of growing technology and scams side by side. At the core of modern cryptography along with enhanced security other virtues like data integrity , authentication and non repudiation are associated. Cryptography is not just limited to the communication, its growing fame has intercepted other fields like finance, digital currencies,record keeping, military communication etc.
You have been upvoted by @sapwood, a Country Representative from INDIA. We are voting with the Steemit Community Curator @steemcurator07 account to support the newcomers coming into Steemit.
Engagement is essential to foster a sense of community. Therefore we would request our members to visit each other's posts and make insightful comments.
Thank you