Steemit Crypto Academy, Season 3: Week 2 || Hash and Cryptography Homework By @dilchamo

HOMEWORK
1.- Explain what does the resistance to collision mean? And what does resistance to preimage mean?
2.- Use tronscan and etherscan to verify the hash of the last block and the hash of that transaction. Screenshot is required for checking.
3.- Generate the hash using SHA-256 , from the word CryptoAcademy and from cryptoacademy. Screenshot required. Do you see any difference between the two words? Explain.
4.- In your own words explain the difference between hash and cryptography.

1.- Explain what does the resistance to collision mean? And what does resistance to preimage mean?
A hashing algorithm is a computation done to convert an input data to an output of Bit string which has a fixed length. SHA-256 is a hash calculator to covert inputs into bit strings. These hash functions are versatile and are prominent everywhere in software engineering field.
There are three security properties regarding the hash functions. Here I will analyze each of the security purposes in detail.
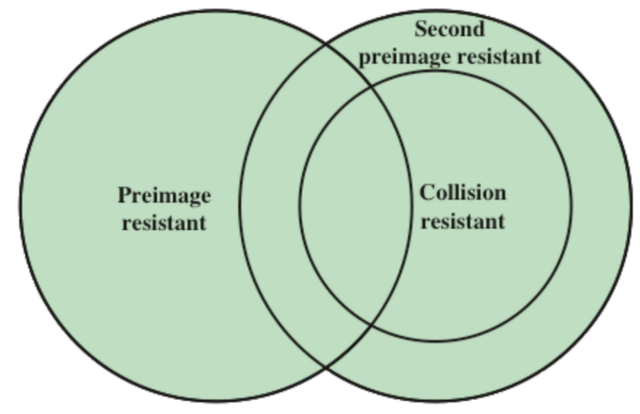
01)Collision Resistance
Collision resistance is also known as “weak collision resistance”. The hash function should have at least 160 bits long to get the collision resistance. Collision resistance is a security property of cryptographic ash function.
Collision resistance is important when a user relies on hash functions that always have two inputs to two different values. We can prove the collision resistance of a hash function using Pigeonhole principle. If the input space is bigger than the output space we know that many inputs can proceed for the same outputs.
02)Preimage Resistance
Preimage resistance is also known as ** One-way Property** is a property of the Hash function that is hard to invert. That is given an element in the range of the Hash it should be infeasible to find input. This property is used for functions with input and output domains of similar size. There should be at least 90 bits to acquire the preimage resistance property.
The direction of a one-way function is straightforward. It is relatively easy to protect a file but if it the computation reverses the direction then it might be difficult. Preimage resistance is different from other security properties.
First, the preimage resistance makes the output value to repeat itself. After selecting the hash function will then ensure that it is uniform. When an attacker is asked to make the selected hash function work, if the attacker finds the preimage value then the attacker is winning. This implies that the preimage hash value should be secure to attackers not being able to obtain the preimage value.
A hash function should consist of security properties to be cryptographically secure. The collision resistance and preimage resistance sometimes show similar characteristics.

2.- Use tronscan and etherscan to verify the hash of the last block and the hash of that transaction. Screenshot is required for checking.
I have visited Tronscan.io to check block details.
First log into Tronscan.io.
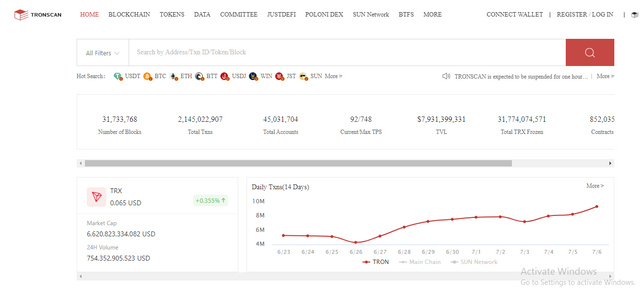
Then click on “Number of Blocks”.
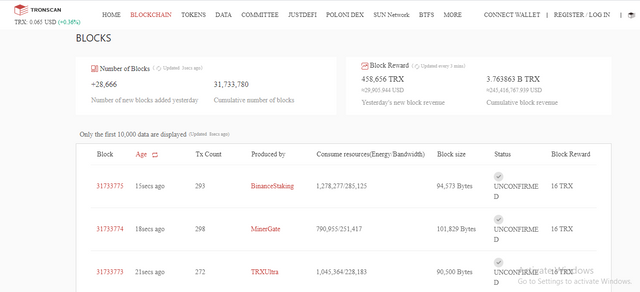
Then click on the last block emerged.
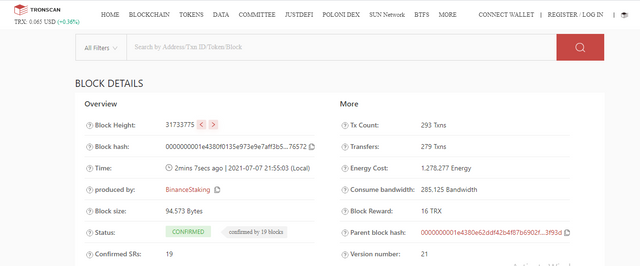
Then you can clearly see the details of the block including Hash, Height , size, status of the block.

3.- Generate the hash using SHA-256 , from the word CryptoAcademy and from cryptoacademy. Screenshot required. Do you see any difference between the two words? Explain.
Below screenshots are taken from theSHA-256
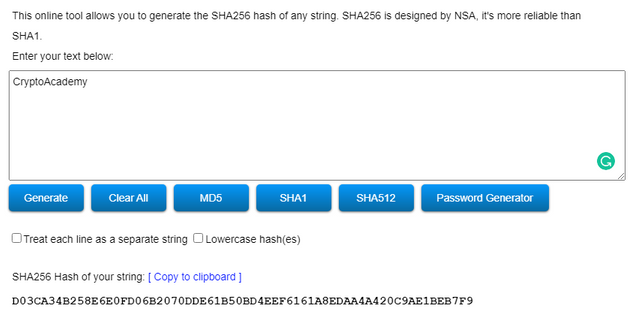
• First I Typed “CryptoAcademy”. The hash function came like this:
• Then I typed “cryptoacademy”. The hash function came like this:
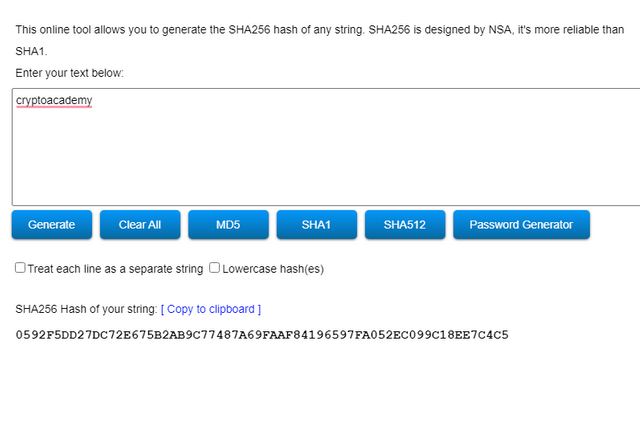
There is a difference between the two Hash functions. In the word with capital letters the hash string has started with an uppercase (D) letter. But in the word with simple letters start with a “0”. The hash strings differ when we use upper case letters, lowercase letters, numbers, symbols or punctuation marks.

4.- In your own words explain the difference between hash and cryptography.
Cryptography is a communication method which is done securely among a sender and a receiver. It is a method of protecting information from attackers. Cryptography can be explained as an encrypted message which the letters are replaced with other characters.
In cryptography of a blockchain there are three ways to perform cryptographic algorithms.
• Symmetric key Cryptography
A single key is taken into application. This is used for both encryption and decryption processes. It can be a problem in securely transferring the key between the sender and receiver.
• Asymmetric key Cryptography
A pair of keys is used in this encryption method.it uses the public key and private key respectively.
• Hash Functions
Hash is also a context of cryptocurrency which generates a hash value from a plain text in the purpose of security. In cryptography every input has a unique output. If an input uses hash function several times then the output will be the same. If the hash function is used for encryption the output can be obtained in a very short time period. In Hash function the reverse engineering cannot be performed. Hash function links the blocks and maintains the data integrity stored in blocks. Slight change of hash function in the input makes totally different outputs.
Key Differences
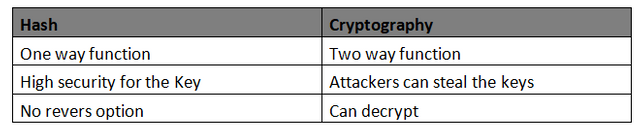
The image created by me in MS Word
Conclusion
Cryptography is a very useful feature in blockchain in order to protect and secure the keys. Hashes aid in cryptocurrencies and mining. This lesson explains the reader about the uses and functions of cryptography and Hash. Thank you Professor @pelon53 for giving us this knowledge about cryptography. Thank you for reading my Homework post.