Crypto Academy / Season 3 / Week 8 - Homework Post for @stream4u | Let's Open the Cryptography by @dilchamo

ENTIRE QUESTION
Homework Task
1.Explain the Blockchain CryptoGraphy and mention few names which are the Blockchain Platforms (Few names of the Blockchain Platforms)?
2.Explain the Public Key CryptoGraphy.
3.Explain the Private Key CryptoGraphy.
4.Explain the Digital Signatures CryptoGraphy and what is Singing Of Transaction/Message?
5.Explain what is Symmetric and Asymmetric cryptography?
6.How Blockchain Wallets CryptoGraphy works and explains the available types of Crypto Wallets.
7.What is the Merkle trees and What its importance in blockchain?
8.Practical + Theory, do some practical research, study on Blockchain Demo: Public / Private Keys & Signing and then explain the functionality of Key, Signature, Transaction, Blockchain with proper screenshots of yours practical. (Do study well for this topic)
9.Conclusion. (The overall understanding of CryptoGraphy)

Explain the Blockchain CryptoGraphy and mention few names which are the Blockchain Platforms
What is Cryptography
Cryptography simply is known as the protocols practice of securing data from third parties. Cryptography develops methods and protocols to prevent third parties gaining knowledge from data in the private messages during the communication process. It is stated that the word “cryptography” was originated from a Greek word called “Kryptos, Graphein” which gives the meaning of “Hidden”. Cryptography is commonly applied in the fields of electronic commerce, chip based payment cards, digital currencies, computer passwords, military communication and many more.

What is Blockchain Cryptography
The cryptography in blockchain technology is used to secure transactions occurring in the blockchain network. Cryptography technology is applied in the process of digital asset and token transfer verification. As a result of the cryptographic protocols built up on a blockchain, third parties won’t be able to access ones private data.
When cryptography is applied to a blockchain network the communication process is encrypted. With this security system only the sender and receiver of the message will be aware of it hidden by the whole world. The sender encrypts the message using keys and algorithms and sends to the receiver. Then the receiver decrypts the message and view. So there won’t be any third parties being able to view the message. The keys and algorithms play the major security role in encryption and decryption. There are key terms that should be aware when learning about cryptography. They are:
Encryption: Transforming a readable text into an unreadable format.
Decryption: Converting unreadable message into a readable format which is the original format.
Cipher: algorithm used to perform encryption and decryption.

Famous Blockchain Platforms
There are many blockchain platforms which use the cryptography. Some of them are:
- Ethereum
It is a decentralized blockchain which supports smart contracts.
- IBM Blockchain
It is a flexible, functional and customizable blockchain platform which is private and decentralized.
- Hyperledger Fabric
It is a set of tools which helps in creating blockchain applications.
- Hyperledger Sawtooth
It is an open source blockchain which supports smart contracts.
- R3 Corda
It is a permissioned blockchain which enables direct transactions with high privacy.

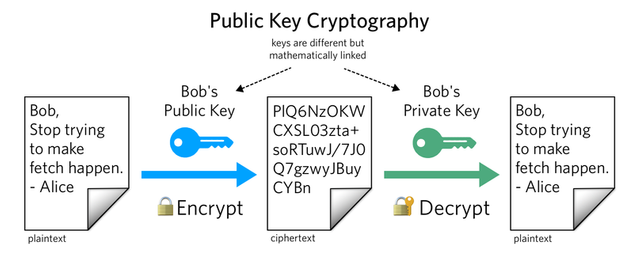
Public key Cryptography
After undergoing many unsecure methods, public key cryptography came into use. As discussed above, cryptography is a method of data security system. Public key cryptography uses more secure methods in data encryption and decryption. In this method the receivers get a unique key in decryption which is the private key and the receiver needs an encryption key known as the public key. Because of the complex encryption algorithm it doesn’t allow hackers to access personal data in the conversation. The public key cryptography has the immense ability to design the relationship between private and public keys.
The users will receive a public and a private key from the certification authority. Public key cryptography is considered as the most secure protocol among all other protocols. The digital signals are also provided by the public key cryptography. As the public key cryptography makes user not to use the private key there is a responsibility with the user to protect the private key. Anyone can use another user public key to encrypt a message but once encrypted only the receiver can decrypt the message using the private key. The public and the private key are generated once the user creates the blockchain wallet.

Advantages
- High security for user data
- No need to reveal the private key to anyone
- Provides digital signatures
- Lesser chance for hacking
Disadvantages
- Less speed for bulk encryptions
- Subject to attacks by the certification authorities.

Private key Cryptography
In the private key cryptography only one secret key is used. That is the private key. The private key encrypts and decrypts information. This is the most suitable encryption for bulk encryptions. The sender and receiver share the same private key. This unique shared key is not shared with other partners.
Advantages
- High encryption/Decryption speed
- Can transfer big file sizes
Disadvantages
- Usage of one Private key
- Key management is not easy

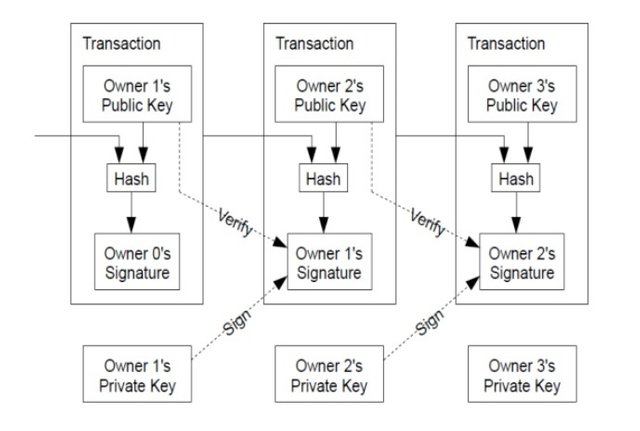
Digital Signatures CryptoGraphy
The word “Signature” is very familiar to us because we use our signature as a proof of secure documents. In the digital world there is a digital signature system which is used to bind a person. Digital signature is not like a handwritten signature. It is a bit long value created with the data and the private key figures.
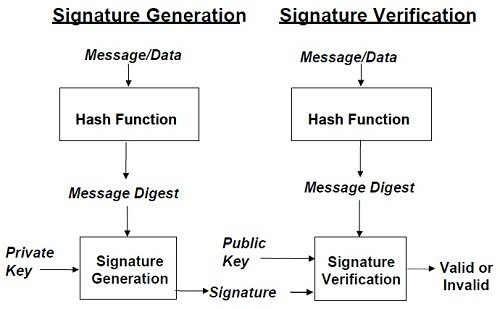
The signature is a hash of data which is ideal for the user so it creates information security as the hash is created with the user private key. The digital signature is verified by the verifier using the public key to make sure the signature actually belongs to the sender. When the hash of data doesn’t match with the verification public key then it can be noticed as an attack by a third party.

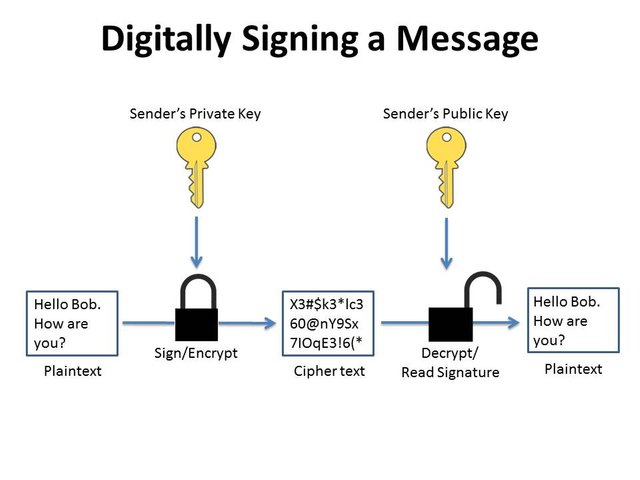
Signing Of Transaction/Message
When signing the message the user private key is used and the user public key is used to read that signature. This process ensures the data integrity. If I want to sign a message to my friend, I will use my private key to sign the message and send to my friend. My public key is used to verify the message signature.

Symmetric and Asymmetric cryptography
Symmetric Cryptography
In Symmetrical Cryptography it uses only one key to encrypt and decrypt messages. The sender should share the key with the receiver. The sender encrypts the message by using the secret key before sending the message. Then the receiver should decrypt the message by using the same secret key.
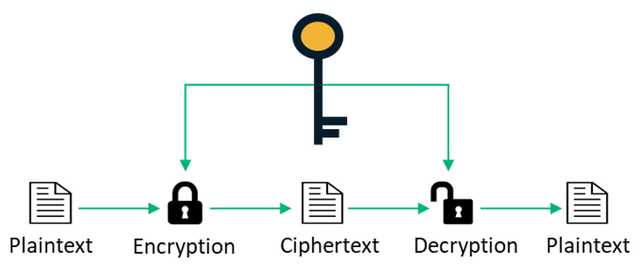
Advantages
- Straight forward
- easy to set up
- Everyone can use it
Disadvantages
- Sharing the secret key may not be secure
- Easy for hackers

Asymmetric Cryptography
Asymmetric encryption works with two keys. The public key is used to encrypt the data and the private key is used to decrypt the data. The sender creates the message and encrypts it with the receiver’s public key and the receiver decrypts the message with the private key of the receiver. The users get this key from a certification authority.
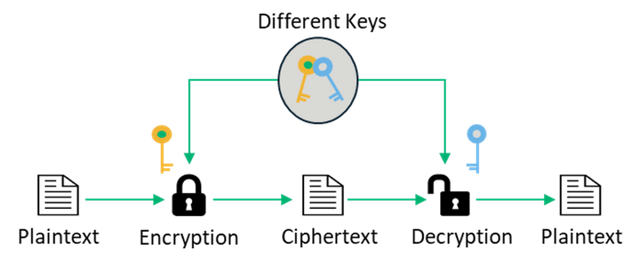
Advantages
- Secure method
- Support digital signing option
Disadvantages
- Complex method
Key Differences Between Symmetric Encryption and Asymmetric Entryption
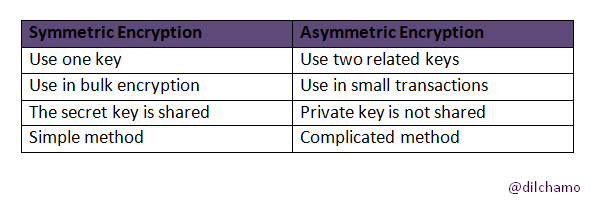
The screenshot was created by me in MS Word

How Blockchain Wallets CryptoGraphy works and explains the available types of Crypto Wallets
Blockchain Wallet Cryptography
Crypto wallets are the place where the private keys are stored which gives access to cryptocurrencies. This allows access to safe cryptocurrency transactions. There are different types of wallets to secure your wallets. By proving the ownership using the private key, users can access the assets stored in the blockchain. The assets are not stored in the crypto wallet. They are stored in the blockchain and the wallet helps to access the assets by securing the keys. This is why users should protect their private keys because they won’t be able to get the assets unless they have the private key.
Types Of Crypto Wallets
- Paper Wallets
Paper wallets are very secure form of storing the keys. The keys are printed on a piece of paper and stored in a safe place. Once the user needs to perform the transaction he can type the characters on the software.
- Hardware Wallets
Hardware wallets seem to be like USB drives. The keys are stored securely in this wallets offline. These are known as offline wallets. To perform the transactions the hardware wallet should be connected to the computer.
- Online Wallets
Online wallets are cloud wallets. The keys are stored in an app or a software.it is easy to use an online wallet. As it is software wallet the keys are stored online which can easily subject to hacking.

Merkle Trees
What is a Merkle Tree
- A merkle tree is a data structure which encodes data more securely. It is also known as Hash trees. It is a kind of a structure which the nodes are labeled in Hash of a data block. To create merkle tree structures the hashing pairs are calculated until a remainder of one Hash. Bottom hashes are leaves, intermediate hashes are branches and the top hash is the root.
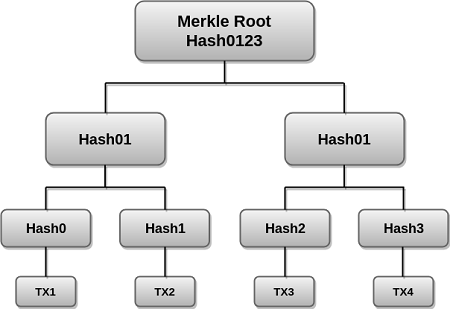
In the above image TX1,TX2,TX3,TX4 are the transactions in the block. The root hash of this merkle tree is Hash0123. The block header where the merkle root is stored is a part of the bitcoin block. This merkle tree holds the wholeness of the data. It saves the memory as proofs.
Importance Of Merkle trees
- Merkle Tree makes the verification process easier by reducing the amount of data to be maintained.
- Proves the integrity and validity of data.
- Small amount of data needs to be transmitted in the proof and management process.
- Transactions can be verified without downloading the entire block. It is known as simplified payment verification.

Practical + Theory, do some practical research, study on Blockchain Demo: Public / Private Keys & Signing and then explain the functionality of Key, Signature, Transaction, Blockchain with proper screenshots of yours practical. (Do study well for this topic)
First I logged into Blockchain Demo. All screenshots of this question are taken from this page.
Key
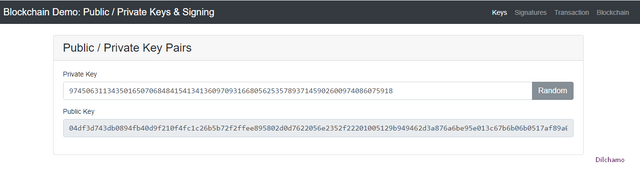
It is well known for us that there are two related keys as a private key and a public key in Asymmetric cryptography. The public key is unique for each private key. The public key and the private key are made of hexadecimal values known as Alpha Numeric values. If we change the private by even a single digit the Public key will differ and produce a unique public key.
The private key in the above screenshot is:
- 97450631134350165070684841541341360970931668056253578937145902600974086075918
The public key in the above screenshot is:
- 04df3d743db0894fb40d9f210f4fc1c26b5b72f2ffee895802d0d7622056e2352f22201005129b949462d3a876a6be95e013c67b6b06b0517af89a0af24c4e1cd0

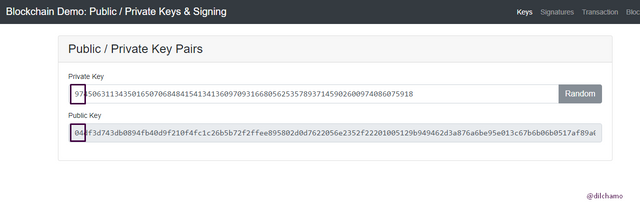
01.I will change the mentioned digits and let’s see how the public key produces a new key. I have changed the first two letters of the private key as “25” and the Public key has also changed its beginning characters.
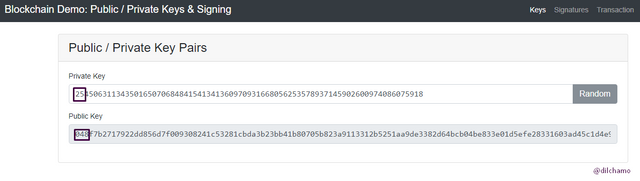
02.Now I will display another example by changing the whole private key and let’s see how the public key changes.
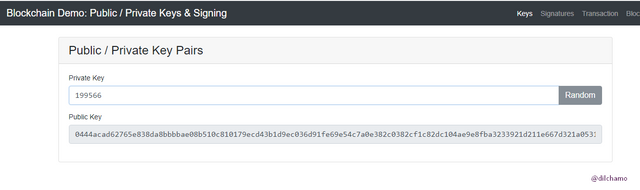
I have used my Private key as “199566” and the Private key was generated as
“0444acad62765e838da8bbbbae08b510c810179ecd43b1d9ec036d91fe69e54c7a0e382c0382cf1c82dc104ae9e8fba3233921d211e667d321a0531b0c0b40fa0a”.
It has produced a unique public key for the given private key.

Signature
Signature is a cryptography performed in connection with the user private key. The user can enter any message here and enter the private key. Then a Digital signature will be designed. As seen in the below screenshot here are my digital signature I got once I click on the “sign” tab and entered the private key and the message.
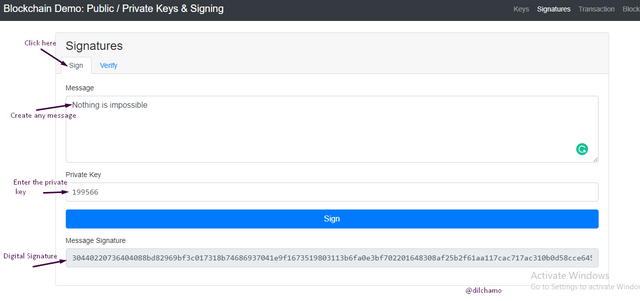
- Message- Nothing is impossible
- Private key- 199566
- Digital signature-
30440220736404088bd82969bf3c017318b74686937041e9f1673519803113b6fa0e3bf702201648308af25b2f61aa117cac717ac310b0d58cce6457456739e94028b9513c5c

Verify
The user can verify the message using the public key. The message created by using the private key is verified by the public key once clicked on the “”verify” button. The background becomes green once the message is verified.
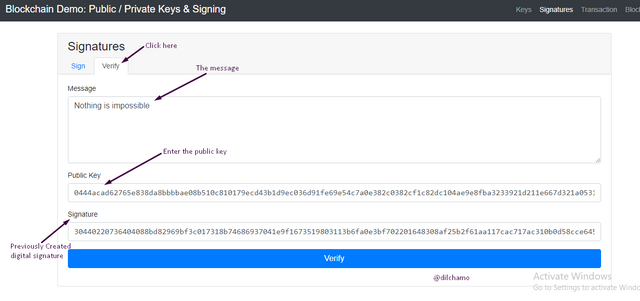

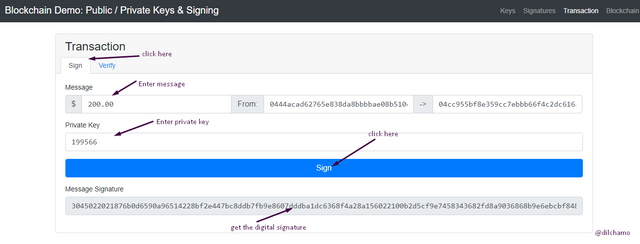
Transaction
After signing in with the private key and verifying with the public key the transaction can be added. Once clicked on the sign button you get to enter the amount and private key. They click “sign”. Then you get the digital sign automatically.

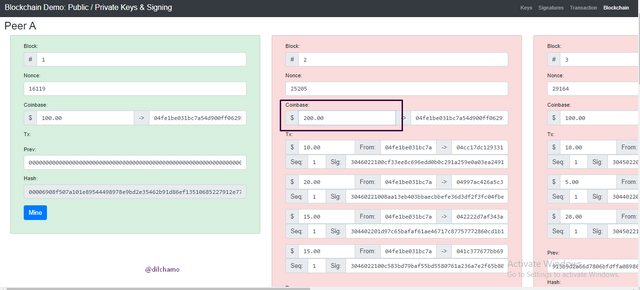
Blockchain
As you can see in the blockchain there are block numbers, nonce, coin base and the Hash. You can see once the coin base is changed, the color of the blocks changed to show the invalidity of the mine. The corresponding blocks will also invalidate if the previous block invalidates. The next block depends on the previous block hash.

CONCLUSION
Cryptography contains different means of securing data during communication and transaction processes. The different structures and cryptography methods like crypto wallets, Symmetric cryptography, Asymmetric cryptography and Merkle trees help users to keep their keys and other information safely. I would like to thank Professor @stream4u for teaching this lesson. Thank you for reading my post. Have a nice day.
