Steemit Crypto Academy – Season 3 - Week 8 - Post for @stream4u

Question 1 - Explain the Blockchain CryptoGraphy and mention few names which are the Blockchain Platforms
Blockchain cryptography is one of the terms that is common as far as blockchain technology is concerned. It is an essential aspect of blockchain that is used to secure user transactions. When the word crypto is mentioned, it is simply means “to hide”. This is one of the core basics in blockchain technology as it is used to ensure the security of transactions on the network. With that, it becomes easier to understand the term cryptography. Blockchain cryptography is basically a type of digital encryption method that is used in blockchain technology to transmit secure messages among the network participants. This encrypted messages can only be decrypted by the receiver.
Simply put, blockchain cryptography is an encryption method that is used by blockchain to secure transactions and private messages between the network participants, and preventing any third party from having access to the information and data during the communication process. In blockchain cryptography, there four main elements namely; the encryption, the key, the decryption and the cipher. The encryption is basically the process of converting or encoding a human readable text or message into an unreadable sequence of bits. The key is very important when it comes to encryption and decryption. It is basically the little amount of information that is required to give rise to the output of the cryptographic algorithm. The decryption is basically the process of reversing encryption. The cipher is basically the mathematical function that enables the conversion of plain text to the ciphertext.
The way this works is that the sender sends an encrypted message to the receiver. This is beneficial for securing the content of the message as the information in the message cannot be viewed by any third party except the receiver who has the key to decrypt and have access to the encrypted message. The receiver would use a special key to decrypt the message. The encryption key and decryption key are two important elements that ensure successful encryption and decryption when it comes to blockchain cryptography. Cryptography is used in blockchain technology in various ways such as cryptography for security, wallets, network transactions, private messages on the network.
Blockchain platforms
- Ethereum blockchain
- Tron blockchain
- NEO blockchain
- Monero blockchain
- Steem blockchain
- EOS blockchain
- Zcash blockchain
Question 2 - Explain the Public Key CryptoGraphy
The public key cryptography is one of the important terms when it comes to blockchain cryptography. It is a type of system or algorithm that makes use of a pair of keys which are; public key and private key. The public key is a type of key that can be made public which means that anyone can have access to the key. The private key is a type of key that is meant to be private and secret which means that only the owner of the private key can have access to it.
Public-key cryptography is a very common way for the encryption of data between the sender and the receiver in a secure way. The public key can be used by anyone for the encryption of private message or data between the sender and receiver, however, the encrypted message can only be decrypted with the private key that corresponds with the public key used to encrypt the message or data.
Public-key cryptography is without a doubt one of the core elements of blockchain technology. The public key cryptography is what is used for the security of wallets and transactions on the network. Each time a user creates a wallet on the blockchain network, the user generates a pair of public and private key. In blokchchain technology, the address is generated from the public key and it is what is used to check the asset on the blockchain and also to receive asset.
Question 3 - Explain the Private Key CryptoGraphy
The private key cryptography is also another important term when it comes to blockchain cryptography. It is a type of algorithm that makes use of the single secret or private key which is then used for both the encryption and the decryption of messages. The private key is a type of cryptography is meant to be private and secret which means that only the owner of the private key should have access to it.
Private-key cryptography is also very common cryptography type, however, for blockchain technology, it is not mainly used as it is considered to be prone to become an issue as in the private key cryptography, only a single private key is used for both the encryption and the decryption of the information, message or data. Making use of a single private key for both encryption and decryption of data can become a problem when it comes to the security of transfer of the key between the sender and receiver because both the sender and receiver must have the same private key to be able to encrypt and decrypt the data.
Question 4 - Explain the Digital Signatures CryptoGraphy and what is Signing of Transaction/Message?
Digital Signatures is also one of the popular terms when it comes to blockchain cryptography. It is one of the core foundation of security in blockchain technology. Digital Signatures are simply a type of proof system that establishes trust in a blockchain network. Like the name digital signature, it basically means a digital stamp of authenticity that proofs that the sent message or data comes from a particular source and not from a malicious actor or hacker. This increases the security of transaction between sender and receiver and reduces the possibility of identity theft.
Digital Signatures is considered as a very secure type of cryptography as it proof the integrity and also the data cannot be altered and can be easily verified. Digital Signatures is used in blockchain technology to ensure that the data is valid, verified and is correct. Digital signatures makes it possible for a valid chain of blocks added to the blockchain. Every data or transaction that is recorded on the blockchain has to go through digital signatures before a new block is securely added to the blockchain. Also, digital signature increases the security of the data that is stored on the blockchain.
Another clear application of digital signatures is in that of cryptocurrencies. It is used for the approval of cryptocurrency transactions on the blockchain network by securely signing the transactions. Also, it is used for digital wallets and multi-signature contracts. The way this works is that it follows a particular previous events of asymmetric cryptography by using a special mathematical links to link two different keys such as the public and private key. Digital signatures has proven to be a very important aspect in blockchain technology as it helps secure transactions in the network. Digital signatures ensures the authenticity of the message or transaction comes from the original sender and not from a malicious actor or hacker. Also, with digital signatures, the receiver would be assured that the message or data received has not been tampered or altered by malicious actors, which increases trust in the blockchain network.
Question 5 - Explain what is Symmetric and Asymmetric cryptography?
Symmetric cryptography
Symmetric cryptography is basically a type of cryptography or encryption that has to do with only a single key being used for both encryption and decryption of digital information or data. The private key used in this type of cryptography is meant to be private and secret which means that only the owner of the private key should have access to it. The parties that are exchange information or data using the symmetric cryptography method must have also exchange the private key that must be used to decrypt the information or data.
Symmetric cryptography is regarded as a more efficient cryptography type when it comes to the encryption and decryption large volumes of information or data. However, for blockchain technology, it is not mainly used in regular circumstances as it can be prone to become an issue because only a single private key is used for both the encryption and the decryption of the information, message or data. The single private key usage for the encryption and decryption of information or data can become a problem when it comes to the security of transfer of the key between the parties because both the sender and receiver must have the same private key to be able to encrypt and decrypt the information or data.
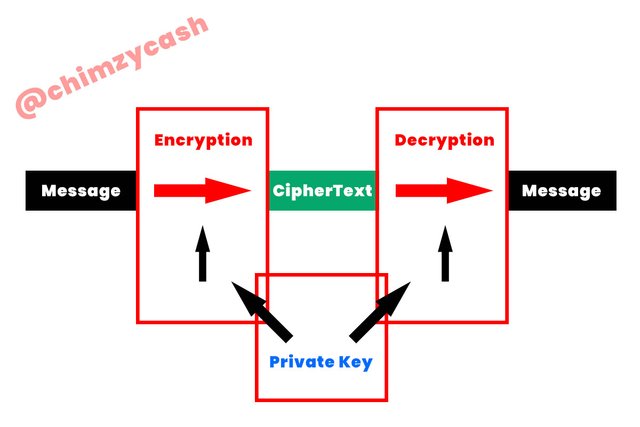
[Design created by me]
Asymmetric cryptography
Asymmetric cryptography is basically a type of cryptography or encryption that has to do with a pair of public and private key that is used for the encryption and decryption of digital information or data. In asymmetric cryptography, the public key can be made public which means that anyone can have access to the key and the private key is meant to be private and secret which means that only the owner of the private key can have access to it.
Asymmetric cryptography is very in blockchain technology when it comes to secure communication between the sender and the receiver. The public key can be used by anyone for the encryption of information or data, however, the encrypted information or data can only be decrypted with the private key that corresponds with the public key used to encrypt the information or data. The way this works is that, when a sender encrypts an information or data in the asymmetric cryptography type using the public key, the receiver of the information or data can only decrypt the information or data using the corresponding private key. This is a great way for secure communication as the parties do not need to worry about the message being intercepted by any third party.
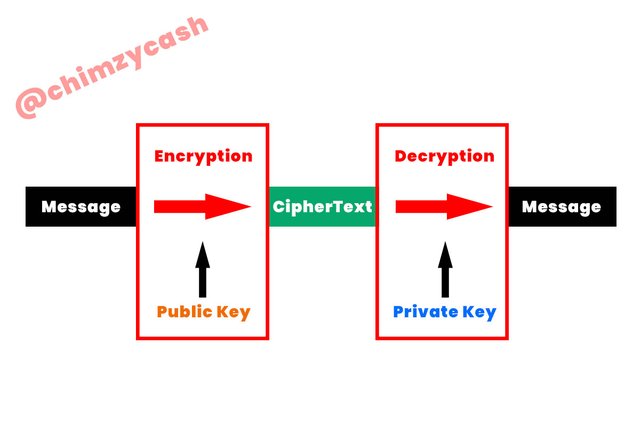
[Design created by me]
Question 6 - How Blockchain Wallets CryptoGraphy works and explains the available types of Crypto Wallets
Blockchain wallets are one of the essential aspects of blockchain and cryptocurrency as it serves as a gateway to store cryptocurrency assets and also interact and make transactions on the blockchain network. A true decentralized blockchain wallet provides the user with both the public key and private key which gives the user full control of the wallet. The private key is very important and must be key secret as that is what gives any user full ownership and control of a blockchain wallet.
The way a blockchain wallet cryptography works is that each blockchain wallet has a unique public and private key. The wallet uses a special algorithm to generate the key pair that consists of public key and private key. This key pair are linked to each other mathematically. In order words, it uses asymmetric cryptography or encryption method. Anyone can produce the public key from the corresponding private key but cannot produce the private key from the corresponding public key. The public key becomes the wallet address that can be used to check wallet balance and also receive cryptocurrency. The private key becomes the proof of ownership of the wallet and is what is used to sign transactions using the wallet. Public key which also serves as the wallet address can be given to anyone or made public without any issue. However, the private key should only be secret and only known by the wallet owner.
Types of crypto wallets
At the moment, there are various types of crypto wallets that can be used to store cryptocurrency, send and receive transactions on the blockchain network. There are four main types of crypto wallets namely; web wallets, software wallets, hardware wallets and paper wallets.
Web Wallets - These type of crypto wallets are very common and popular in the blockchain and crypto space because it is the most easily accessible and anyone can make use of it using any device with a web browser. Web wallets also known as online wallets are wallets that live on the web and requires a user to make use of an internet browser in other to have access the web wallet and interact with the web wallet. A clear example of a web wallet is myetherwallet which is a web wallet for storing and sending and receiving ethereum and ethereum-based tokens.
Software Wallets - These types of wallets does not live on the web, but requires the user to install the software wallets on the supported device which can either be mobile device or computer device. This means that software wallets are both mobile wallets which are installed on mobile devices, and desktop wallets which are installed on computers. Since a software wallet does not live on the web, it does not require internet connect to access them, however, internet connection is needed to process the transactions. A clear example of software wallets are trust wallet (mobile wallet), atomic wallet (both mobile and desktop wallet), exodus wallet (both mobile and desktop wallet), etc.
Paper Wallets - These types of wallets lives offline. It is regarded as one of the safest type of wallet because it does not connect to the internet. Paper wallets are printed on papers with the public and private keys. Cryptocurrency sent to a paper wallet is very secure if the paper wallet is in a secure and safe place.
Hardware Wallets - These types of wallets are very secure because it is a physical crypto wallet and does not by itself connect to the internet, instead, the hardware wallet is used to authenticate the transaction on gateway that is either a web interface or installed software interface on a supported device that connects to the blockchain network through the internet. Since hardware wallets are physical device, they store the keys securely in the chip of the device that is not exposed, and allows the wallet user to access the wallets securely.
Question 7 - What is the Merkle trees and What its importance in blockchain?
Merkle tree which is also known as a hash tree is one of the common terms in blockchain technology. It is basically a tree that makes use of cryptographic hash functions for the storage of hash outputs instead of storing the raw data in each of the nodes. There is a cryptographic hash of the original raw data that is contained in each of the leaf node and the parent node is the hash that is as a result of the combined child node hashes. In the merkle tree, the root is simply the top node of the tree, which means that the combination of both the left and right sub-trees is represented by hash output.
The way this works is that, In blockchain technology, the hash is generated from a block of transactions that is run through an special algorithm. The hash is the string of alphanumeric value. Since the blockchain doesn’t run the entire block of transaction through the hash function in a single time, instead, each transaction sent is hashed, followed by each pair of transactions that is then mathematically linked together and hashed together as well. This would continue until there is one single hash for the entire block in the chain.
To visually demonstrate how a markle tree looks like and works, let’s take for instance a block that contains 4 transactions. The bottom row of the markle tree is the leaves with “Tx” is the transactions. The hashes are the branches and the top of the tree is the root. From the illustration, we can see that there are 4 transactions labelled Tx 0, Tx 1, Tx 2, Tx 3. The transactions are then hashed to generate the hash 0, hash 1, hash 2, hash 3. Hash 0 and hash 1 form a pair to generate hash 0 1, and hash 2 and hash 3 form a pair to generate hash 2 3. In the final stage, hash 0 1 and hash 2 3 pair up in the root hash 0 1 2 3.
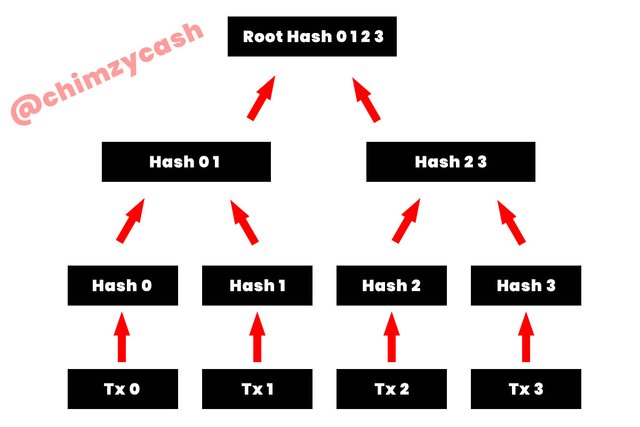
[Design created by me]
The Importance of merkle tree
In blockchain technology, the markle tree structure play a very important role. One of the main importance of the markle tree in blockchain is that it allows a user to verify whether a transaction has been added to a block. This is very useful because without the markle tree structure, a user would have to download the entire blockchain just to verify a single transaction. This increases efficiency in the network.
Also, the Merkle tree structure in a blockchain helps to decrease the amount of data that must be present for verification purposes.
Another importance of the markle tree is that it makes it possible to prove both the validity and integrity of data in the blockchain.
Another benefit of the markle tree in blockchain technology is that it increases efficiency since it helps reduce the memory usage.
Question 8 - Practical + Theory
Keys
Demonstrating the blockchain public and private keys practically, I will be making use of a tool by andersbrownworth https://andersbrownworth.com/blockchain/public-private-keys/keys
From the screenshot, we can clearly see that the blockchain has generated a pair of public-private keys which is what is known as asymmetric cryptography.
.png)
Private key - 87951039812412640276161954906742770828435671519660996219421308480781215647899
Public key - 04aee944780b987ec3572b6be1e21b18a41bc8210668151b9042f4ffacab3038b3c6029a2c730215cb1f145ade1ac88bff7a7400bf6d261b6d2d01637de346e2e6
This is a clear example of asymmetric cryptography because there is a pair of public-private key, and each public key has a corresponding private key and also each private key has a corresponding public key. The private key can be used to generate a public key, however, the public key cannot be used to generate a private key. Each time we randomize the private key, a new public key is generated.
.png)
Newly randomized private key - 234456257972461218393871752070025370277412040873841136242139412644475678
New public key generated from the newly randomized private key - 047a5d8dcd47933155dcc8ebfb36a09a066f226b67b3df4937fce6fcd365e1b086fe352184db85fcd81d84d7bc976c0a0af44acde840fb407c6c16af47db4d1e17
Functionality of the public key
In the asymmetric cryptographic encryption algorithm, the public key is used to encrypt the information or data by the sender. The public key can also be used as the address to receive transaction on the blockchain network.
Functionality of the public key
In the asymmetric cryptographic encryption algorithm, the corresponding private key is used by the receiver to decrypt the information or data that was encrypted using the public key. Also, the private key is used to sign transactions and proof ownership of a blockchain wallet. Private key is also used to generate public key.
Signature
Based on the explanation of the digital signature earlier in this post, I will be demonstrating the digital signature practically by visiting the signatures section here https://andersbrownworth.com/blockchain/public-private-keys/signatures
.png)
.png)
For the message input, I typed in a message and used the corresponding private key to sign the message.
Message - This is super amazing
Private key - 234456257972461218393871752070025370277412040873841136242139412644475678
Message Signature - 304502206c9dee253be5c4b985388ed272d2f71f7cb1347c01df06a829c34222a9a44b9102210086ac2eced3421c7f5d28186cb56f8e6121bd59f0fd3b7d2d6781cb2e03b006c1
From the above, we can see that the message was successfully signed and as a result, there was a corresponding digital signature.
To verify the message, click on the verify section and proceed by clicking verify. We can clearly see that the message was successfully verified because of the green colour which validates the success of the verification and proofs that the message comes from the original sender.
.png)
.png)
Functionality of digital signature
A digital signatures enables the signing of a message so that any changes or modification can be detected and the original source can be verified. This helps to prevent malicious actors from altering the message. It serves as a digital stamp of authenticity that proofs and it increases the security of transaction between sender and receiver and reduces the possibility of identity theft.
Transaction
To demonstrate transaction on blockchain practically, I will visit the transactions section on the site here https://andersbrownworth.com/blockchain/public-private-keys/transaction
Like I explained in the blockchain wallet, this demonstration shows how a transaction is carried out in a blockchain wallet. The core principle of any cryptocurrency transaction is just a message on the blockchain that tells the algorithm to send a certain amount of cryptocurrency from the sender to the receiver. The sender will have to sign the transaction using the private key to approve the message to be sent to the receiver on the blockchain.
.png)
.png)
Message - $120
Sender public key - 047a5d8dcd47933155dcc8ebfb36a09a066f226b67b3df4937fce6fcd365e1b086fe352184db85fcd81d84d7bc976c0a0af44acde840fb407c6c16af47db4d1e17
Receiver public key - 04cc955bf8e359cc7ebbb66f4c2dc616a93e8ba08e93d27996e20299ba92cba9cbd73c2ff46ed27a3727ba09486ba32b5ac35dd20c0adec020536996ca4d9f3d74
The private key - 234456257972461218393871752070025370277412040873841136242139412644475678
Message signature - 304502202e56be23c2d815dbd701f796ed682e27b24ee0297f07559edc89ee71410b9e8a022100c0cc455b2fc9bffaa50e100446d94c253ba005f48642e6e3f6e5c673c8079417
From the above, the private key will be used to sign the transaction on the blockchain. The transaction will be carried out from the sender’s public key/address to the receiver’s public key/address. After signing the transaction, a message signature was generated as a proof of authenticity.
To verify the transaction on the blockchain, click on the verify section and click on verify. This will verify the authenticity of the transaction and ensures that the transaction comes from the original sender.
.png)
.png)
Functionality of transaction
Transactions are key essentials of any blockchain as it is what allows for the creation of new blocks and adds a new block on the chain. Each transaction on the blockchain creates and adds a new block on the chain. Each block on the chain are chronologically linked to each other and each block carries the transactions that is stored on the blockchain.
Blockchain
To demonstrate blockchain practically, I will visit the blockchain section on the site here https://andersbrownworth.com/blockchain/public-private-keys/blockchain
On block 3, we can see the number of transactions that have been carried out in the block. One of the main benefits of blockchain technology is that transactions that are stored on the blockchain is immutable which means that it cannot be changed or altered.
On block 3 we can see that it has a nonce of 29164. The coinbase transaction which is the first transaction in the block is $100. Block 3 has 3 transactions; and a hash.
.png)
Block Hash - 000029942f0286f943ac7e877d7f10c3902aecbb2eebc72a758ab40487b0b8f9
Transaction 1
Amount - 10
Sender public key - 042222d7af343abd780add9dd7a0f554a1d6b127bc6f7ec28c5eef97d25af83028e89011559daa71dfcc7e2175433a1a6ef605715eba07a8a942c7088f8050a714
Receiver public key - 04d4080959e3795bc74a50fe606c1418a0a2a1c2c16e39f5c4a08b363a9c0611fa732be61f13b3f270cc534d3815dacced5d344b86a9aa302390c3399b5238bce6
Signature - 30450220485a5a1c317d5a1b33af90201999909b49e09dc5f0b261048bbee1d09ed1735f02210081eb6d39ab4db5d9f95ec5b103b7a6268bc936c738cb05293e167220fbc3b71e
Transaction 2
Amount - $5
Sender public key - 041c377677bb697329b8dbeb5811b026d532730ad90ad7357fd812183ec01b766d7a4ee33c6a85b84d44fa1c3c59377c660f0076c39c563d9a19005a56ee1d1336
Receiver public key - 04d4080959e3795bc74a50fe606c1418a0a2a1c2c16e39f5c4a08b363a9c0611fa732be61f13b3f270cc534d3815dacced5d344b86a9aa302390c3399b5238bce6
Signature - 3044022002cc3c61bb7cd4573b192d1b61f125545ebc84c5b47dd9ea096b896bf9b335a702204c3252e5f27c8732d4ce52f58efb3493fa733200aba01270f779a3b7fed2e53c
Transaction 3
Amount - $20
Sender public key - 04997ac426a5c3c0ec9b51732435f90ebb4cf06aca4bfdb778865af0110f3931660d8b85297d59382c81eb6c7ae7c100af55800f15dad1fc72122139ba02e5d740
Receiver public key - 040b4c84f02bfec488a8a861267f8221646e1b6f6701504ad39d4ee82248fa7b5152536ea36bf47ee0812186a13311a2c0cfc24f557dfa38b2048139be45d7ac4c
Signature - 3045022100ee33bb3764f5f85f694d1033a66131bc818c188dba4e6392e89c03c06537885202201d92064c5e8804df8864baa30ccbcaca45caac345686768125d0c9a10fad94f4
From the above screenshot, we can see that the block is valid and successfully mined. However, attempting to alter one of the transactions in the block renders the block invalid and all the next block that comes after block 3 becomes invalid since the chain has been broken with an invalid block. every block of transaction on the chain is chronologically linked to each other, which means that once a block is invalid, the chain is broken and all the blocks created after the invalid block becomes invalid as well.
.png)
.png)
Mining block 3 makes the block to become valid and ready for the next block to be mined and added to the chain. However, the transaction that was altered has an invalid signature which is a digital proof that the transaction was altered. The digital signature shows that the transaction is not authentic and it might have been comprised by a malicious actor.
.png)
9 – Conclusion
When it comes to blockchain technology, cryptography is one of the terms that is common and is an essential aspect of blockchain that is used to secure messages and user transactions. This is one of the core basics in blockchain technology as it is used to ensure the security of transactions on the network. Blockchain cryptography is basically a type of digital encryption method that is used in blockchain technology to transmit secure messages among the network participants. This encrypted messages can only be decrypted by the receiver.
Understanding the various types of cryptography such as asymmetric cryptography and symmetric cryptography and also the different types of keys used by each of the cryptography or encryption types is important in order to understand how security in blockchain technology. Blockchain wallets are another key essential as far as blockchain and cryptocurrency is concerned as it is what is used to store cryptocurrency, send and receive transactions on the blockchain network. Web wallets, software wallets, hardware wallets and paper wallets are the four main types of crypto wallets. Finally, blockchain technology has proven to be a very powerful solution in almost all sectors as it offers a lot of benefits with security being one of the main benefits of blockchain technology.