The Steemit Crypto Academy Week 6: All About Blockchain Security 2
•Introduction
Hello steemians Am by name @chidiebere a member of steemit Am very happy to join this great community. I've heard So much about this great community steem Crypto academy am from the eastern part of Nigeria, known as ebonyi state, in afikpo north local government area.
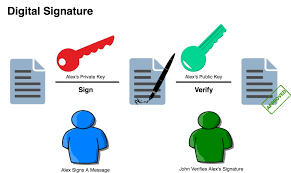
•Digital Signature
•What is Digital Signature
Digital signatures are like electronic “fingerprints.” In the form of a coded message, the digital signature securely associates a signer with a document in a recorded transaction. Digital signatures use a standard, accepted format, called Public Key Infrastructure (PKI), to provide the highest levels of security and universal acceptance. They are a specific signature technology implementation of electronic signature (eSignature).
•Hash Function/Algorithm.
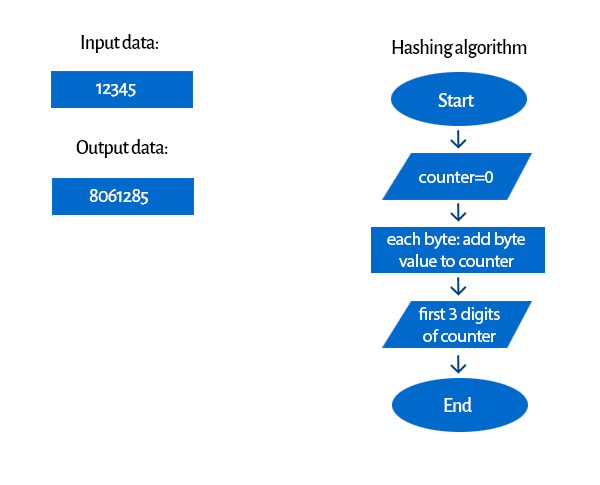
Let’s say you have an important file to send and you want to ensure it will get to the addressee without any changes, in one piece. You could use some trivial methods, like sending it multiple times, contact the addressee and verify the file, and so on... but there’s a much better approach: using a hashing algorithm.
Hashing algorithms are functions that generate a fixed-length result (the hash, or hash value) from a given input. The hash value is a summary of the original data.
For instance, think of a paper document that you keep crumpling to a point where you aren’t even able to read its content anymore. It’s almost (in theory) impossible to restore the original input without knowing what the starting data was.
Let’s look at a hashing algorithm example with a simple hash function:
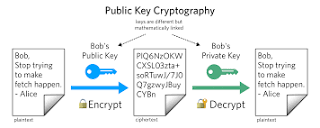
•Public Key
The public key is only used to encrypt data and to decrypt the data, the private key is used and is shared. ... The public key is free to use and the private key is kept secret only.
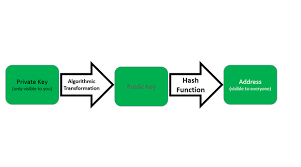
•Private Key
Private Key is used to both encrypt and decrypt the data and is shared between the sender and receiver of encrypted data.
•Public-Key Cryptography (PKC)
A form of cryptography that uses two related keys, a public key and a private key; the two keys have the property that, given the public key, it is computationally infeasible to derive the private key. For key establishment, public-key cryptography allows different parties to communicate securely without havng prior access to a secret key that is shared, by using one or more pairs (public key and private key) of cryptographic keys.
•Hashing
•Secure Hashing Algorithm (SHA)
The Secure Hash Algorithms are a family of cryptographic hash functions published by the National Institute of Standards and Technology as a U.S. Federal Information Processing Standard.
• SHA-1 and SHA-2
The primary difference between SHA-1 and SHA-2 is the length of the hash. While SHA-1 is the more basic version of the hash providing a shorter code with fewer possibilities for unique combinations, SHA-2 or SHA-256 creates a longer, and thus more complex, hash. In 2015, new SSL certificates with SHA-1 were phased out.
• SHA-256 and the Blockchain
One of these concepts that are vital to the blockchain functionality is called SHA256. It is a Secure Hashing Algorithm, commonly used for digital signatures and authentication.
•Conclusion
The conclusion about this lesson is all about security in cryptocurrency how to secure your cryptocurrency wallet from scammers on your mobile phone and laptops . I get to know that Blockchain are very important through the help
Of Hash Function/Algorithm Public Key Private Key Public-Key Cryptography secure Hashing Algorithm (SHA) SHA-256 and the Blockchain.
@gbenga-week6 @cryptoacademy
THANKS ALL
.png)
.png)

.png)
.jpg)
Hello @chidiebere1, I am glad to see you here and you ave done well puting down a long content but then, this isn't the topic of the assignment. Here is the topic to the assignemt:
The Security Benefits of Applying Blockchain Within any Industry, and the impact of cryptocurrency on the industry.
Please you can do well to check through the class and the assignment, I will be expecting to see a new post related to the topic of assignment.
P.S: You should add a profile picture :)
Yours @gbenga