Steemit Cryptoacademy Week 16 Verified Homework Task Re-submitted For Voting To Professor @levycore | The Monero Privacy Coin | By @bukkyi4u
(This is a re-submission of my week 16 homework task which was verified by professor @levycore but was never upvoted by @steemcurator02. Here's the link to the original post Steemit Cryptoacademy Week 16 Homework Task Submitted To Professor @levycore| The Monero Privacy Coin| By @bukkyi4u )
Choose a Privacy Coin and perform a fundamental analysis of the coin in detail.
INTRODUCTION
One of the strong and the major reasons why the Bitcoin was introduced was to act as an alternative to order national fiat currencies that are controlled by the government. However, its use of traceable pseudonyms has led some to argue that it does not offer users the much needed and sufficient privacy they deserve. This is because in authoritarian and dictatorial climes the pseudonyms can actually be traced down by the government to individual users.
As a matter of fact, it can even be argued that Bitcoin actually offers less security than different national or subnational fiat currencies. This is due to the fact that the Bitcoin network uses a public blockchain with this kind of public blockchain transaction details can be traced with the use of chain analysis. This chain analysis can eventually lead to the revelation of the real identities behind whatever transactions an individual with the wherewithal may wish to track.
This ugly development informed the rise and adoption of what are now known as privacy coins. These coins come with the ability to shield the addresses of sending and receiving participants. With these coins value can be anonymously transferred. However, even as a lot of them are sprouting there have been growing concerns over the ability of such digital assets to be used for Terrorism Funding (TF) and Money Laundering (ML). All the same, there are a lot of advantages associated with privacy coins. Consequently, I have decided to examine one of these important privacy coins known as the Monero (XMR).
WHAT IS MONERO?

source:pixabay
XMR Important Statistics
| Metrics | Statistics |
|---|---|
| Monero Price | $278.89 |
| Price Change (24h) | $22.27 (8.68%) |
| 24h Low / 24h High | $254.18 / $279.20 |
| Trading Volume (24h) | $274,503,819.4 |
| Volume / Market Cap | 0.05489 |
| Market Dominance | 0.30% |
| Market Rank | #26 |
| Market Cap | $5,001,296,104.96 |

Monero is a cryptocurrency which is privacy-focused and which was initially released on the 18th of April 2014. Its protocol is open-sourced and is based on an application layer which is known as CryptoNote. The development of this protocol was originally written by Nicolas van Saberhagen. It makes use of a public protocol which is obfuscated. This means that anybody is at liberty to broadcast or send transactions in a manner that the source, destination and even the amount associated with the transaction cannot be known by an outsider.
In the protocol a proof-of-work mechanism is in place. This mechanism uses a hash function known as RandomX. RandomX serves the purpose of issuing new coins. Also, it is used to provide incentives for miners who validate transactions and secure the network. The monero is able to achieve fungibility and anonymity by using a lot of technologies that enhance security. This makes it possible to be used by people who do not want to use cryptocurrencies that are public-monitored. However, this has equally made it a choice for the darknet markets

THE HISTORY OF MONERO?
The history of Monero dates back to 2014 when in a forum called Bitcoin talk a user named thankful_for_today succeeded to fork the Bytecoin codebase and called it BitMonero. The whole idea and concept behind it was to improve upon the Bytecoin and include innovations that would hide block rewards, block time and tail emission. Unfortunately, the introducer of this concept quickly disappeared into thin air and jettisoned the idea which was later taken up by a team led by Johnny Mnemonic. The name was eventually changed to Monero by the team.
In the year 2016 Monero experienced very rapid growth in trading volume and in its market capitalization more than any other cryptocurrency in the market. Actually, this was due to the privacy features that were attached to it. Again, its unprecedented growth came as a result of the adoption of the privacy coin by darknet market users who make use of the coin to purchase a lot of illicit and illegal substances.
The privacy features associated with Monero were further strengthened on the 1st of January 2017 when the protocol adopted the use of Confidential Transactions, an algorithm which had early been developed by Gregory Maxwell, one of the core developers of Bitcoin. This works together with a much improved version of the Ring Signatures to hide the amount in transactions. These privacy features made the funding of projects or acts that would have otherwise been impossible a reality. Such events included:
- The 2017 Unite the Right rally by white nationalists like Andrew Auernheimer and Christopher Cantwell who had been prevented from using other conventional methods of payment
- The 2017 WannaCry global ransomware where proceeds were converted to Monero and The Shadow Brokers group, which leaked the information, received payments from there
- 44% of 2018 cryptocurrency ransomwares used Monero to receive illegal rewards

PRIVACY FEATURES OF MONERO

source:pixabay
Monero uses different technologies that complement one another to produce transactions that are fungible and anonymous. Actually, its core value is to meet two basic criteria of:
- Untraceability which produces a number of possible multiple senders for a particular transaction
- Unlinkability which makes it impossible for it to be proven that a particular address received multiple transactions
With untraceability the sender is protected with what is known as a ring signature. Also, with unlinkability the receiver is protected with stealth addresses. Some of the important Monero privacy features include:
Ring Signatures
Actually, Monero is built on the CryptoNote protocol. In this protocol a one time cryptographic primitive ring signature is generated. This is built on the RandomX that serves to penalize ASIC mining and GPU. This makes transactions anonymous. Another ring signatures variant known as Ring Confidential Transactions (RingCTs) were tested on the 10th of January 2017. RingCTs use two components including:
- Confidential Transactions (CTs) that hide the amount in transactions with the use of Pedersen commitment
- Multilayered Linkable Spontaneous Anonymous Group (MLSAG) ring signatures which obscures the address of the sender
Stealth Addresses
Stealth addresses are generated on a one-time basis and are useful for the hiding of receiver addresses. This is made possible with the use of Dual-Key Stealth Address Protocol (DKSAP). Usually, the sender would use two pieces of information to generate this for the receiver. A shared secret key agreement generated by the elliptic-curve Diffie–Hellman (ECDH). The second information used is the public key. With this public key the intended recipient can scan through the blockchain to determine whether the transaction was meant for him. After that he will use his private key to access the transaction. This public key is meant for one time use.
Bulletproofs
Another privacy feature which the Monero implements makes use of a non-interactive zero-knowledge proof (NIZKP) protocol. These features were first tested in October 2018 and are known as bulletproofs. These were meant to replace the Borromean ring signatures which are range proofs used in RingCT. With the use of Bulletproofs, transaction sizes were greatly reduced and this led to lower fees and faster verification for transactions.
Dandelion++
Monero utilizes a process which propagates transaction broadcast as a way of making the IP addresses of the devices from which transactions are made to appear obscure. This particular method became necessary has a result of the fact that wide-area cryptocurrency markets were coming under serious analysis. Furthermore, botnets could be used for this analysis. In this feature a probabilistic method is used to determine when a completely signed transaction would be transmitted to another node on this peer to peer network. However, it may either be sent to just one node or it could be sent to many nodes at a time through flooding.
Auditing
The way that Monero was developed makes it absolutely impossible for a third-party to either verify or observe transactions that are taking place on the platform. However, the parties involved with the transaction can provide what is known as private view key to a third party. With these private view keys the third-party can observe the amount of funds on the wallet of the owners of the key. Still, the key cannot be used to transfer funds from there. Furthermore, proof-of-payment can be given by a Monero user who can provide a private transaction string key. With this particular key, funds moved in a single transaction can be seen by the authorized third-party.

MINING OF MONERO

source:pixabay
The nature and design of Monero is such that it is made to be resistant to mining with application-specific integrated circuits (ASIC). Actually, this is a technology that is used in the mining of most other cryptocurrencies like Bitcoin itself. However, it can most efficiently be mined on hardware that are consumer grade such as GPUs, x86-64, ARM and x86.
This makes it very prominent among miners who are malware-based. What more, the 2019 November release or introduction of a proof-of-work algorithm known as RandomX even makes mining with ASIC even more difficult.
LINKABILITY OF MONERO TRANSACTIONS
In the year 2017 some group of researchers undertook some studies that pointed out three major user privacy threats of Monero. The first threat relies entirely on the ability to leverage the zero ring signature size. The other lies in the ability to see amounts in outputs. Leveraging Output Merging, which is the second issue raised, Usually functions my practice at least two different transactions that have their outputs traced back to one particular user.
A good example can be taken from when 'churning' occurs in which case they send funds to themselves repeatedly. Furthermore, the use of Temporal Analysis has shown that it can even be possible to forecast the correct output of a transaction whereby amounts can be revealed. In the wake of these stark realities the team behind the development of Monero responded by saying that the introduction of RingCTs addresses the first issue of concern raised. Again, they have equally said that the system mandates ring signatures to be issued in minimum amounts at a time as a precautionary measure.
RESPONSES FROM REGULATORY AUTHORITIES
Authorities that are regulating such illicit activities like money laundering have raised serious concerns over such privacy-oriented coins like the Monero itself. Exchanges that are located in Australia and South Korea have removed Monero from their list due to pressures from regulatory bodies. Sometime in early September in 2020, the IRS Criminal Investigation (IRS-CI) announced a bounty of up to $625,000 to be given to anybody who can provide the kind of statistical data that would make it possible to connect the data of transactions made on Monero or the Bitcoin Lightning Network to particular users. To further consolidate their stand the IRS awarded a one year contract to Chainalysis and Integra FEC, which are data analysis organisations, to trace or track transactions on the Monero network.

Describe the steps in creating a wallet for the Privacy Coin of your choice. (Screenshot required)

The cryptocurrency wallet which is specially designed for the Monero privacy coin and which I will be describing the steps in creating is the Monerujo. This one is quite secure and safe. Also, it has an important feature of being lightweight. This is due to the fact that it makes use of nodes with which it synchronises to Monero blockchain. That is to say it doesn't download it directly. It can:
- Transfer funds between multiple wallets created within it
- Send payments to BTC wallets directly
- Scan QR code
Very importantly, the wallet does not use a server that can be accessed by the public and stores private information on your device alone.
In creating the wallet the first step is to download the Monerujo app from the Play store. To do on Play store:
- Click the 'install' button below the app
- Wait for the app to finish downloading
- Then click 'enable'
- After that click 'open'
- Click 'next' on the welcome page

After downloading and installing the app, once you open it and click next you will see this page:
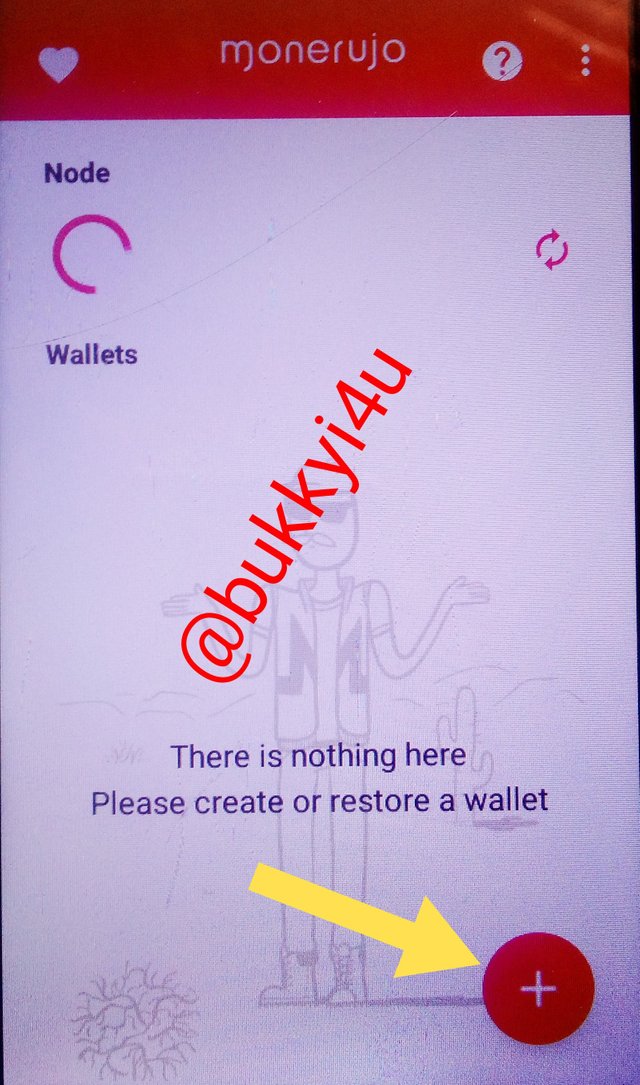
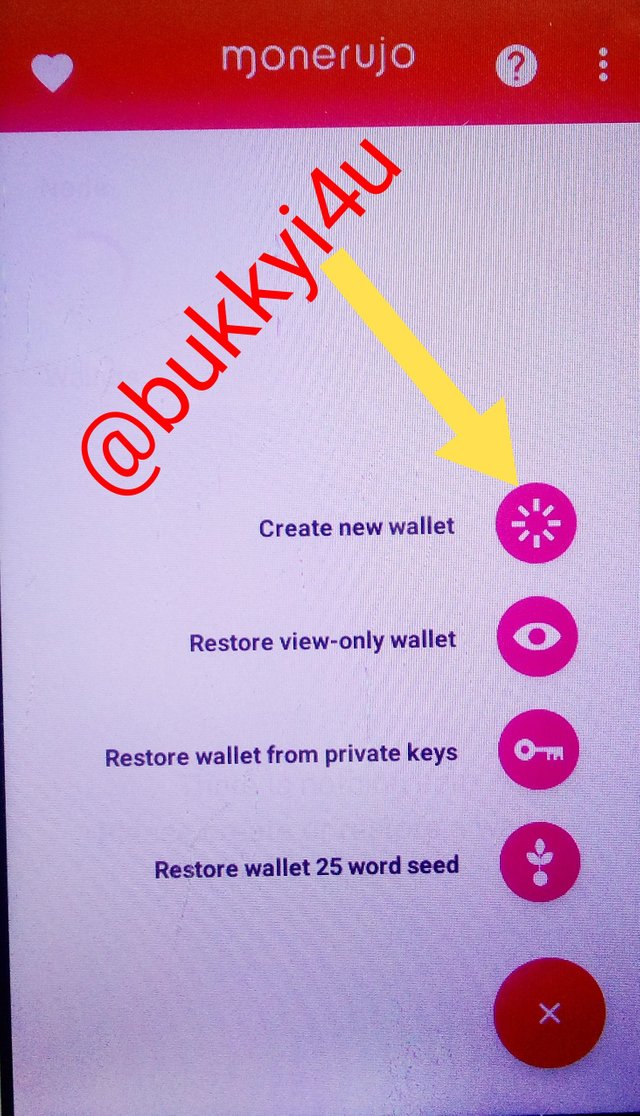
We would click the plus (+) icon to either create a new wallet or restore a previously owned Monero wallet from another source. In this case we would create a new wallet.
To create a new wallet:
- Click on the first icon with that option
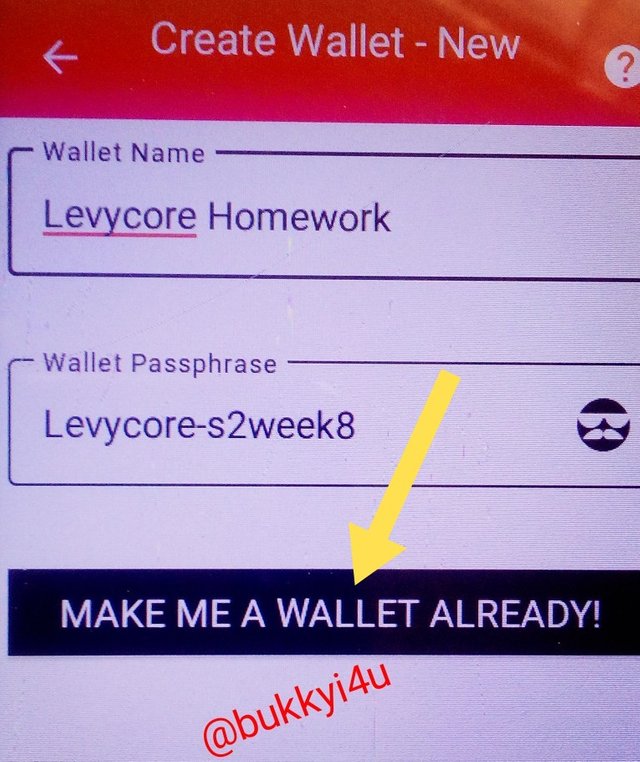
- Input wallet name and wallet passphrase
- Then click 'make me a wallet already'
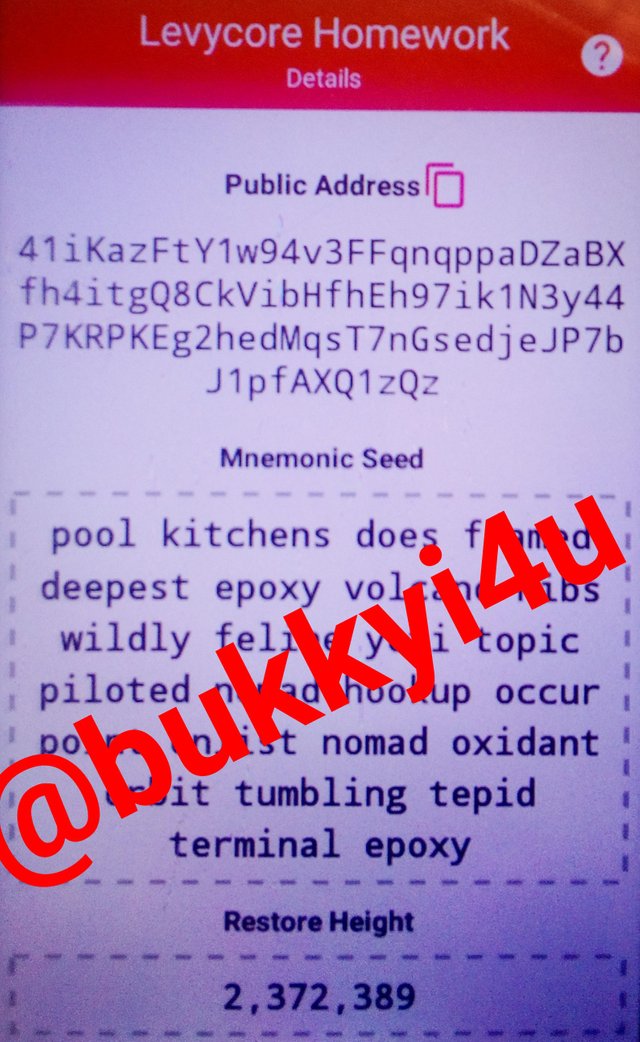
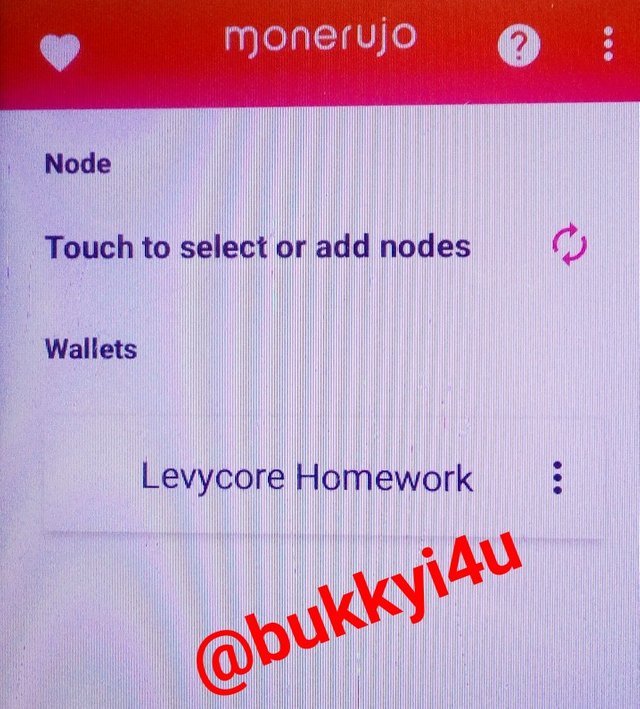
On the next page that opens up you will see your public address displayed. Also, you will see a mnemonic seed phrase which you should note.
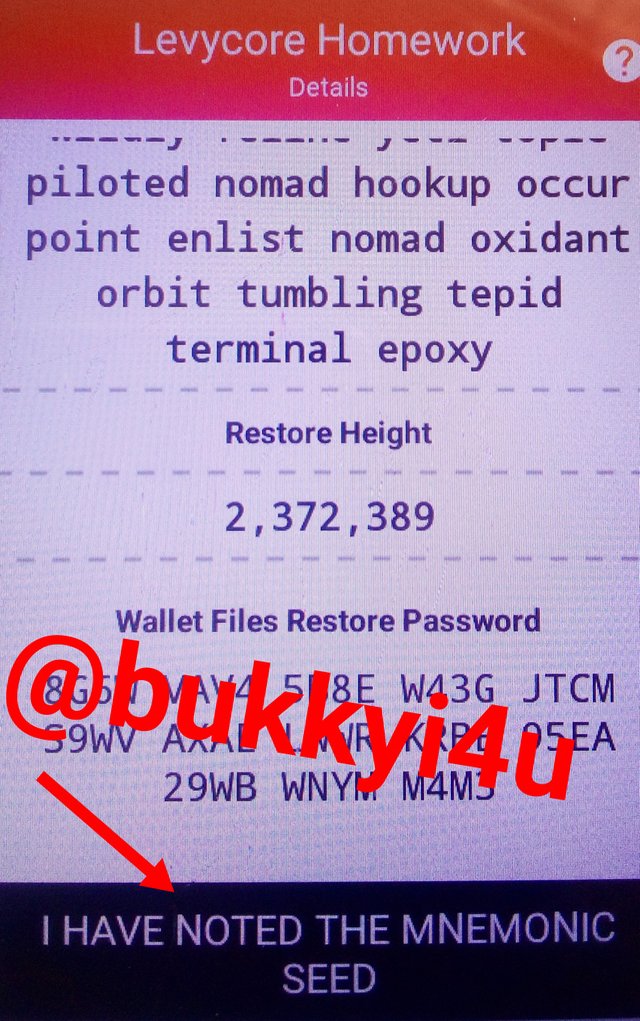
After that, click 'I have noted the mnemonic seed' to finally create the wallet address. From the screenshot below you can see that the Monero wallet address with the address name 'Levycore Homework' has been created.

Explain the reason you chose the Privacy Coin. (State the advantages and disadvantages)

There are a few reasons why I decided to settle for the Monero privacy coin. Even though there are some demerits associated with them, the points I am going to explain in the succeeding lines will show that the benefits far outweigh the perceived shortcomings of it.
Freedom From Unnecessary Capital Control
The Monero privacy coin as a cryptocurrency that is located on a decentralized blockchain gives users full access and rights which shields them from unnecessary governmental capital controls. There have been some cases of unnecessary government interference and capital controls like Greece citizens at some point being restricted to 60 euros expenditure per day, India recently declaring that 86% of all circulating cash would no longer be honoured as legal tender in the near future.
Some other worrisome examples are the proposed Australian government $100 bill ban, Switzerland, Denmark, Sweden and Japan implementing negative interest rates on citizens' account savings. With the Monero privacy coin as a cryptocurrency, all these aforementioned abnormalities can be overcome. This is because with this privacy coin you have full control and right over your capital on a global scale.
It Can Be Useful For Personal Safety
The important features of Monero makes it a great tool and asset in preserving personnel and physical safety. Let's take for instance the situation whereby you reside in an environment where assessing traditional banks may not be feasible and you are left with the option of using cryptocurrency to make payments, it can be seen that in this situation Monero as a privacy coin holds a tremendous advantage over other cryptocurrencies.
This is because in this case you can make payments with Monero without the recipient viewing your account balance as has been seen with other cryptocurrency wallets like bitcoin wallets. In that way you do not risk your safety if anybody sees a huge amount of funds you may have, especially in a criminal-prone area.
It Can Give Some Business And Commerce Advantages Than Other Cryptocurrencies
In cases where cryptocurrencies are to be used for business transactions, the Monero has some advantages over other cryptos. Let us assume a situation whereby you have to make payments to a supplier as a businessman. In doing this with a bitcoin wallet, the supplier would see the balance you have in your wallet. This can affect his sensitivity to price in future trades with you.
Unfortunately, this is not good or profitable for you in running your business. They can even see other payments you have received to that particular Bitcoin address and know how much you are offering other suppliers. This leakage of your commercial information can damage your bargaining power and create losses for you.
It Can Prevent Unpermitted Access To And Usage Of Your Data
It has often been discovered that companies use 'price discrimination' strategies to arrive at what prices they would offer their services to customers. A business may want to offer their services to you at a higher price than they will charge others because they have information on your income.
When you pay with a cryptocurrency wallet that gives people a public view of the transaction histories in your wallet and to see the amount of funds you have in your cryptocurrency wallet, then companies can exploit this open data whenever you make crypto payments to them in overpricing their services to you. However, with Monero such important information is shielded and not sold out cheaply without your permission.
It Prevents You From Unnecessary Criminal Links
The use of the Monero privacy coin can help prevent you from some form of unnecessary links to criminal elements. In a situation whereby you have to accept payment or money from an unverified source or from somebody you are not very sure of then you can accept payment with Monero without risking being linked to a criminal.
In other cryptocurrency payments, funds transferred to you can be monitored and the wallets from where they are transferred are open to the public. In such a situation you risk being associated and linked or back-traced to have transacted with a criminal. Therefore, this can put you at risk of losing your personal freedom in cases of high suspicion scandals.
Monero Has A Mining Algorithm That Is Quite Superior
Actually, mining refers to a situation whereby some form of programs are run on computers as a way of verifying and confirming cryptocurrency transactions that are carried out by users worldwide. It is unfortunate that a lot of mining programs for different cryptocurrencies run better on some custom made chips developed for mining purposes of different cryptocurrencies known as ASIC more than normal computers and laptops.
Equally, the use of ASIC involves a high cost of electricity. However, the mining algorithm used by Monero was designed in such a way that the ASIC as a mining cheap will not have any comparative advantage over other computers and standard laptops. Consequently, the users can choose to run the programs on their computers or laptops and go about their daily business. In this way they could come back to the good news of having mined, and, therefore, earned some amount of Monero from the mining process.
The Adaptive Nature Of Monero Block Size Limit
In cryptocurrencies the transactions that are announced are usually added as blocks. When two or more blocks are added it forms a chain of blocks, hence, the name 'blockchain'. In some cryptocurrencies it can take up to 10 minutes to add a particular block. However, in the case of Monero it takes just two minutes.
Again, some cryptocurrencies have a limit of blocks that can be added at a time. This can potentially cause delay in the speed of transactions. With the Monero, there is a form of adaptive block size limit which would work in making it possible for large-scale transactions to be done at a time. This is because the blocks will adapt to the transactions to ensure that they are completed promptly at all times.

Actually, there have been some arguments that have been offered up as disadvantages of the Monero privacy coin - including all other privacy coins. Most of the argument winds around lack of transparency or the inability to trace transactions as seen in other cryptocurrencies and then, the use of the Monero for illicit transfer of funds during illegal activities.
However, I would like to counter some fallacious lotions that are being propounded by these two major arguments that have emerged against privacy coins and the Monero in particular. When it comes to the issue of transparency and the Monero not being open to public purview it should be understood that making transactions between two different individuals who agree on prices or conditions for funds transfer is entirely up to them on how they decide to go about it.
That is to say that whether the details of their transaction is made open to the public or not should not become a matter of discussion in public cycles, after all. Moreover, individuals who may have agreed that it is best to hide their legitimate business transaction details from the public and decide on the Monero as an efficient, fast and low-cost mode of cash transfer is simply not supposed to be anybody's headache!
The other argument is on the use of the Monero for illicit payments and transactions of illegal businesses including Money Laundering (ML) and Terrorism Funding (TF). Well, I agree to disagree! I agree in the sense that this argument actually holds water. However, I disagree based on the fact that it is not original and not limited to the Monero or any other privacy coin. The use of coins for the Terrorism Funding (TF) and Money Laundering (ML) has become a general issue with cryptocurrencies in one way or the other.
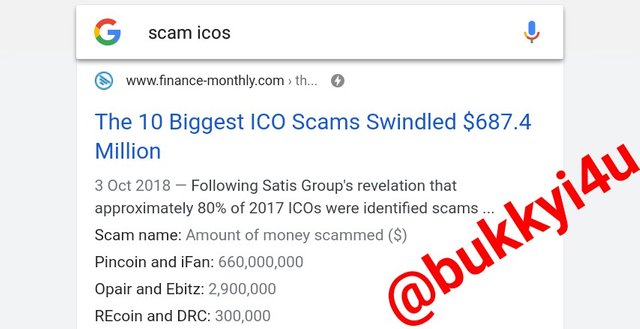
screen from google
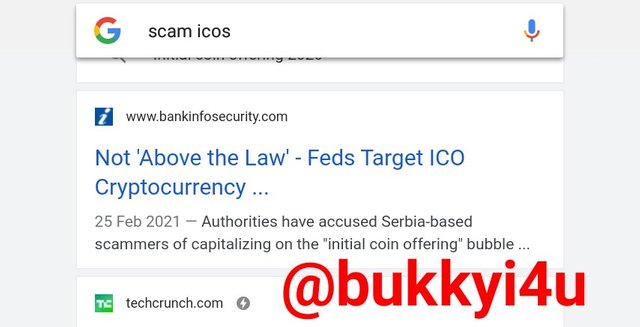
screen from google
From the screenshots I have shown above, it can be seen that all over the news media a lot of cases have been discovered where cryptocurrencies - not necessarily privacy coins - have been used to even scam people with scams in Initial Coin Offerings (ICOs).
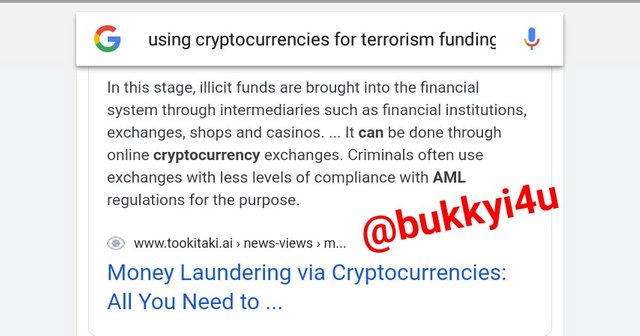
screen from google
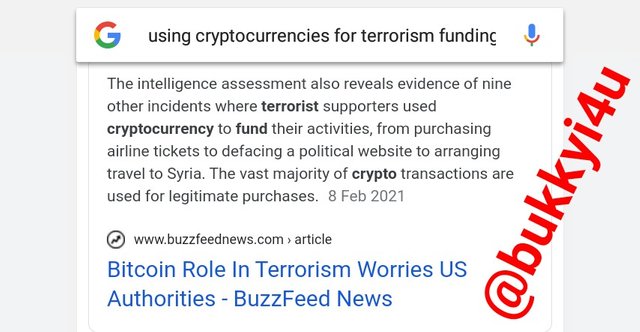
screen from google
It has also been seen how other cryptocurrencies are being used for the funding of terrorism in which case large casinos, corporations and organisations that communicate with terrorists and which have created cryptocurrency wallets, cryptocurrency exchanges and even large worship centres that control a lot of funds have been used to move huge amount of money needed for funding of illicit activities through other cryptocurrencies.

screen from google
Therefore, it is my humble opinion that rather than criticizing privacy coins as possibly being used for these criminal acts, the anti-graft agencies should look for regulations and recommendations that would help cryptocurrencies to generally fight these anomalies. The RATF is already taking the right step by organising and delivering papers on security recommendations for cryptocurrencies, including privacy coins.

CONCLUSION
I have researched and written extensively on the Monero privacy coin, its privacy features, its mining and a few other important information has been included.
Again, I have shown how to create a Monero wallet with the Monerujo and the steps involved in creating it.
Finally, I have discussed why I chose the Monero and also given possible solutions to a few of the shortcomings I have identified with it. Thanks to professor @levycore for an amazing lecture and I hope you had a good reading.
