[Cryptography And The Genesis Block Of Cryptocurrency] - Steemit Crypto Academy Season 5 - Homework Post for Task 3

Edited withCanva

3a) What is a Cryptocurrency?
b) What is Cryptography and how does it make cryptocurrencies secure?
c) Explore the Steem Genesis Block and Sign in as proof of completion.

Cryptocurrency refers to a sort of virtual or digital monetary exchange of value which makes use of the technology of cryptography for its security thereby making it almost impossible to double spend or counterfeit the virtual currency. Most cryptocurrencies operate with a form of decentralized network that is developed on the blockchain technology which functions as a distributed ledger of disparate networks of interconnected nodes, computers or servers. Very importantly, cryptocurrencies are noted for not being issued by any central body, bank or authority. Theoretically, this makes cryptocurrencies immune to the manipulation or interference of any central government.
Cryptocurrency is a word which is derived from the technique employed to secure the network which is a mode or means of encryption called cryptography. The basic structure of cryptocurrencies which gives it the integrity associated with transaction data of cryptocurrency networks is known as blockchain. The blockchain technology is believed by many experts to possess a disruptive tendency for a lot of other traditional industries including the law and finance industries. However, there are still some criticisms faced by cryptocurrencies. Some of these include its volatility in terms of exchange rate and its use for illegal purposes like money laundering and four huge transactions linked to illicit drug trafficking.
Cryptocurrency as a system makes it possible for online secure payments to be carried out in terms of visual tokens that are denominated and represented by entries in the ledger of the particular network or blockchain the underlying particular crypto asset is linked to. Crypto is a term which is used to describe the different encryption algorithms and techniques of cryptography employed to ensure the safety of the entries in the underlying ledger. Such cryptographic techniques can include hashing functions, public-private key pairs and the Elliptical Curve encryption.
Bitcoin became the first cryptocurrency which was based on the Blockchain and remains the most valuable and most popular. However, there are now thousands of other cryptocurrencies called alternate coins that come with various specifications and functions. Some of these alternate coins are forks or clones of Bitcoin and some others are entirely new concepts. Bitcoin was launched by a pseudonym called Satoshi Nakamoto in 2009. As of November 2021, the number of bitcoins in circulation was projected at over 18.8 million and it has a market capitalisation which is about $1.2 trillion. Major planet coins that were spawned by the success recorded by bitcoin include EOS, Ethereum, Litecoin, Solana and Cardano.

What Is Cryptography
Cryptography refers to a methodology employed whereby different protocols and techniques are developed in order to make it impossible for third parties to gain or have knowledge of data which is transmitted in the process of communication in the form of private messages. The term itself is derived from two ancient Greek words "Kryptos" meaning "hidden" and "Graphein" meaning "to write". There are a few words importantly associated to this concept of cryptography, namely:-
Encryption:- This refers to a process whereby normal text or plaintext is converted to a random sequence of bits known as ciphertext.
Decryption:- This refers to the inverse process of converting a ciphertext to plaintext.
Cipher:- This refers to the mathematical function which is actually a cryptographic algorithm that is used in converting plaintext to ciphertext.
Key:- This refers to information which is private and which is required in order to give an output for a cryptographically hashed function or algorithm.
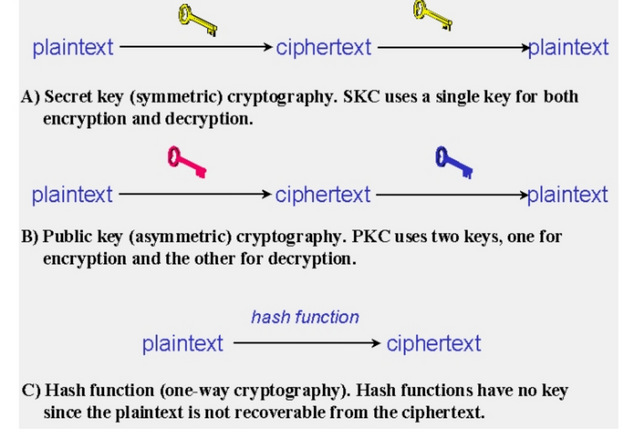
Cryptography can come in three different types. These include:-
Source
1). Symmetric key cryptography- This refers to a method of encryption where a single key is taken into the application. This single or common key can both be used for encryption and decryption purposes.
2). Asymmetric key cryptography- In this type of cryptographic method a pair of keys is utilised. There is the encryption key and another decryption key called public and private keys respectively.
3). Hash Function- This refers to a method of encryption that does not have to rely on the use of keys. Normally, it makes use of a cipher in generating a hash value which comes with a fixed length while having the plaintext as an input. It is almost impossible to recover the contents of the plaintext by using the ciphertext.

How It Makes Cryptocurrencies Secure
What is the relationship between cryptography and the technology called blockchain and how does it make cryptocurrency secure? It should be noted that the technology which underpins cryptocurrency is blockchain. Blockchain functions as a peer-to-peer network which is decentralized and which has no single node controlling the entire network. This requires that the nodes should not have to trust one another. This involves the need for an appropriate safeguard to be put in place to secure information channels and maintain integrity in the transactions. Cryptography has been employed for the safeguarding of transaction information while ensuring consistency in data along with privacy.
Cryptography is primarily applied in blockchain in the area of safeguarding transactions and participants against double-spending and to ensure the absence of central authorities in controlling operations. Equally, it is useful in verifying transfer of assets and the digital tokens between uses. It does this by making use of a concept based on real-world signatures and the encryption of keys. Cryptography employs the use of advanced mathematical codes in storing and transmitting, in secure formats, data values related to blockchain in giving security to cryptocurrencies.
Normally, in employing cryptography as a secure technique for the transmission of private messages between two participants, use is made of keys and algorithms which work by encrypting the message before it is sent out to the intended receiver. The intended receiver on his own makes use of decryption to obtain the original message sent across. This means that cryptography employs the use of encryption keys to secure cryptocurrencies.
Hence, with the use of these encryption keys unauthorised recipients cannot read or decode transactions, data value or messages. Equally, use is made of digital signatures which are basically a mathematical approach that implements digital codes that work to verify if documents or digital messages are legible or not. Consequently, symmetric key cryptography can be employed whereby a similar key is used to both encrypt and decrypt data. Also, the asymmetric key cryptography can be employed whereby two different keys are used to either encrypt or decrypt data.
Furthermore, use can be made of the cryptographic hashing whereby immutability is given to blockchain transactions by making use of cryptographic hashes and not cryptographic keys in this case. The blockchain use cases of cryptographic hashing include:-
Cryptographic hash functions have been proven to be deterministic meaning that for a specific input, the same output would be received at all times and the output would remain of the same length in every case.
Cryptographic hash functions ensure that unique outputs are produced at all times. This means that two different inputs cannot have the same output and this ensures collision resistance in cryptocurrencies, thereby ensuring that crypto functions can be hashed without fear of data tampering.
Cryptographic hash functions are also known to be irreversible and an original input cannot be obtained back with the use of the output. So, transaction outputs in cryptocurrency cannot be used to obtain original data inputs which may have been encrypted by users.
Also, with the use of cryptographic hash functions, hashes are computed in a faster way and this ensures that data cannot be tampered with during processing of cryptocurrency transactions.
Cryptographic hash functions equally make use of the avalanche effect which ensures that a little change in the input would produce a totally different output. So, cryptocurrency inputs for transactions cannot be tampered with without the outputs changing and this can prevent double spending.
These are some of the ways by which cryptography has been employed in securing cryptocurrencies.

Exploring The Steem Genesis Block And Signing In
In order to explore the Steem Genesis block :-
- I visited https://steemworld.org
- Next, I clicked on block explorer
- I clicked OK for block 1
- From the top right-hand corner I clicked sign in
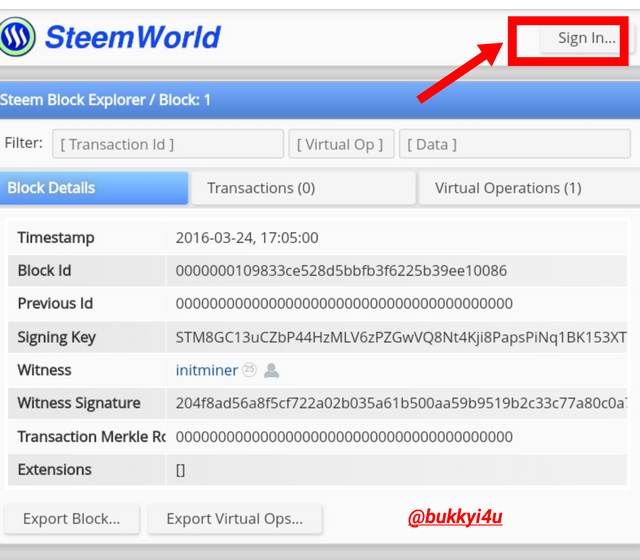
- On the window that opens up I entered my account username and my posting key; then, I clicked ok.
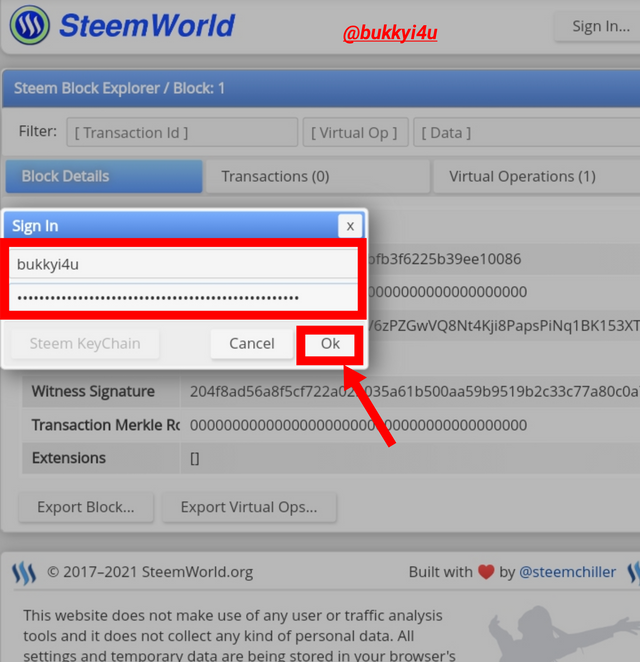
- From the image below you can see at the top right-hand corner that I have been successfully signed in.
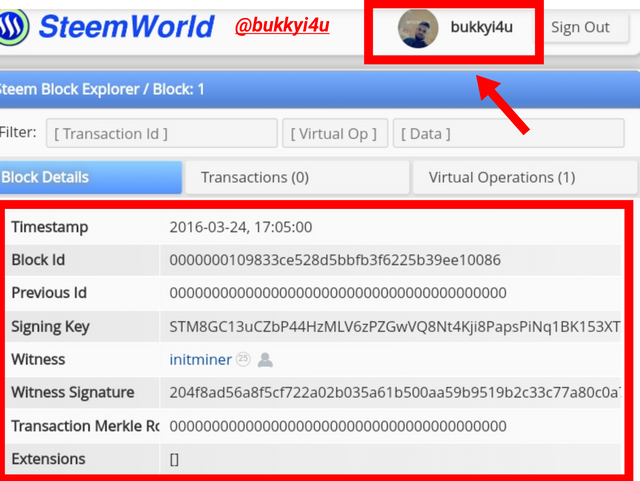
- Again, you can see some information related to the Genesis block of the Steem blockchain; these details are tabulated as shown below.
| Parameter | Statistics |
|---|---|
| Timestamp | 2016-03-24, 17:05:00 |
| Block Id | 0000000109833ce528d5bbfb3f6225b39ee10086 |
| Previous Id | 0000000000000000000000000000000000000000 |
| Signing Key | STM8GC13uCZbP44HzMLV6zPZGwVQ8Nt4Kji8PapsPiNq1BK153XTX |
| Witness | initminer25 |
| Witness Signature | 204f8ad56a8f5cf722a02b035a61b500aa59b9519b2c33c77a80c0a714680a5a5a7a340d909d19996613c5e4ae92146b9add8a7a663eef37d837ef881477313043 |
| Transaction Merkle Root | 0000000000000000000000000000000000000000 |

CONCLUSION

Cryptocurrency as a digital or virtual money that can be used as an exchange of value and which is noted for being highly secure against such anomalies as double spending and counterfeiting has had quite a disruptive effect across the finance world and other modes of doing things since its inception. It can be used as a system for making payments online and relies upon the blockchain technology which is a distributed ledger type system of crypto asset management. Interestingly, cryptocurrency relies on the concept of cryptography to draw much of its security features.
Cryptography makes cryptocurrencies secure in quite an interesting number of ways including the use of symmetric and asymmetric keys as well as hashing functions. This gives the hash functions a deterministic nature that cannot be reversed and for which a particular output would always be generated for each input at all times. The Genesis block is the very first block that was mined on any blockchain. The Steem Genesis block contains quite a good amount of information related to the very first block that was mined on the Steemit ecosystem.

Cc:
@nane15

Thank you for your nice post