Blockchain Trilemma - Crypto Academy / S5W2 - Homework post for nane15.


Explain in your own words what the Blockchain Trilemma is.

A blockchain trilemma is a concept in the blockchain industry that explains the 3 main issues that developers encounter during the developmental stages of a blockchain. It persists even after the blockchains have been created and are up and running. The result of it is that they end up sacrificing one of the issues to allow the other two issues to run smoothly. It is a term coined by Vitalik Buterin, the founder and CEO of Ethereum Blockchain.
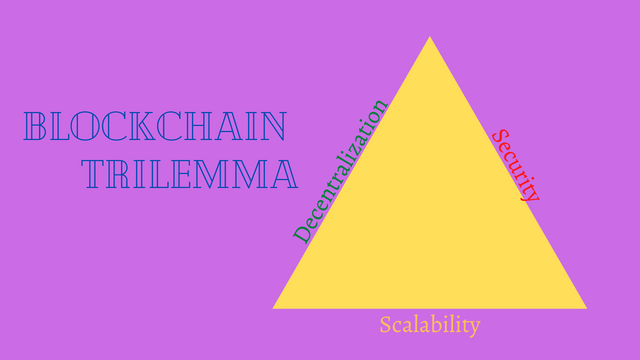
The very nature of blockchain technology is based on Security, Decentralization, and Scalability. These three components are what make blockchain technology attractive to new users. Blockchain enthusiasts believe that blockchain networks can only allow two out of the three main components of the technology. This is true when you consider the existing activities of most blockchain networks.
For instance, the major challenge that the Bitcoin blockchain network is experiencing is Scalability. The transactions that occur on the bitcoin network take a lot of time before getting confirmed and then finalized. The transaction time is 7 transactions per second (tps). This is because of the difficulty level it takes for a block to be mined on the network and record transactions. This makes the activities on the network to be very slow and this depicts a bad omen to a society that is time conscious.
Right now the Bitcoin network is getting more Centralized as node operators who need to mine blocks and get rewarded in BTC have to get the necessary equipment, which is quite expensive. When operations on the Bitcoin network started it was highly decentralized, but as the value of bitcoin increased, only wealthy people can get the types of equipment necessary to mine blocks on the network.
The thing is this, blockchains that are decentralized and secure are less scalable, while blockchains that enterprises run on such as Fabric are secure and can handle a large number of transactions. But the down part is that they are not decentralized as only a limited number of nodes can carry consensus. Finally, some blockchains are highly scalable and decentralized but are not typically secured and this makes them vulnerable to hacks.

Is the Blockchain Trilemma Really a Trilemma?

It should be noted that the term Trilemma is a word that is used to conceptualize the issues surrounding blockchain technology. These issues surround the three core of blockchain technology which are scalability, decentralization, and security. It is something that is inherent in blockchain technology and becomes apparent upon deployment. However, different teams are working on these issues to try and make all three work simultaneously.
So Yes there is a Trilemma. Because blockchain technology gives a sense of security which is fundamental for its existence, and for it to get a higher level of security it needs a consensus mechanism to operate. But the underlying structure that is used in decentralized networks brings up the Trilemma issues. These issues become apparent because a blockchain needs a higher number of network participants or nodes to become decentralized and offer high security, but this feature makes it less scalable.
This Trilemma dates back to the '80s where computer scientists initiated a term called the CAP theorem to give an expression of the major challenges related to decentralized storage. It is the premise where a decentralized storage system can only guarantee two of the three items that make the CAP acronym. As blockchain technology is a modern distributed network, this CAP theorem has now evolved into the Blockchain Trilemma. This cap theorem extends into blockchain technology because it is a high-level iteration of decentralized storage.
The Trilemma persists because blockchain technology is becoming a remarkable utility in different industries of the world such as Finance (which is very common) to Property ownership (which is not so common) because of its characteristics such as peer-2-peer transactions and efficient storage. Although some of these industries have faster transactions times due to them being deployed by centralized entities. For instance, the payment system VISA can have a transaction throughput of 16,000 transactions per second. While others have poor transaction storage which can take a lot of time for previous transactions to be accessed.

Define the following concepts in your own words:
A. Decentralization
B. scalability
C. Blockchain Security

A. Decentralization
Decentralization is one of the three main core components of blockchain technology. Its infrastructure is different from that of centralization. In central networks, the user's data points are given to the control of the entity behind the central network. In decentral networks, the user's data points are in their control. Systems that operate under decentralization provide ownership that is permissionless and anyone can build on the platform. It is the main characteristic of blockchain technology and drives projects that are created using decentralized protocols.
The networks found in decentralization are made up of computers (or nodes) that interact with each other on a direct, peer-2-peer basis without the need for third parties. Each computer (or node) is independent of each others. When data is generated it is distributed to every single computer (or node). Each node gets an updated copy for every data generated and recorded. At the same time, certain as data is distributed certain private information can be stored without the need for a third party.
So instead of following certain instructions as in a centralized network, the nodes interact with each other using some predefined rules, but still keep their sovereign power and can take care of their privacy. This method helps keep a decentralized network secure and at the same time ensures governance that is seen to be democratic.
Decisions and agreements are carried out by a Consensus Mechanism where activities such as transactions and data storage are confirmed and verified by a group of nodes that operate in the network. The consensus mechanism as you know is powered by blockchain technology. A consensus mechanism is a way in which the computers (or nodes) interact with each other in other to ascertain a valid set of generated data before it is stored in a block and put in the blockchain, thus being verified. This means that agreements are crowdsourced and no entity can decide to gain control or censor the data that is generated during operation activities within the network.
Once this verification process has taken place, the data set that is verified cannot be changed. So unlike a centralized network where data can be changed through a centralized database, changing the data in a decentralized network would have to be done by changing all the data of each computer (or node) which is difficult and practically impossible. This makes it that risk and trust are not placed on any one individual.
These decentralized protocols make these projects by-pass intermediaries and third parties such as banks and payments merchants during any operations. For instance, transactions done with decentralized projects are peer-2-peer, and the transactions can be viewed as it occurs in real-time. Also, decentralized financial platforms allow users to stake in liquidity pools where they can earn interest on their stake. This means that intermediaries such as banks are not needed for the raising of loan capital and repayment of loans.
B. Scalability
It is a general term to describe the performance of a blockchain network as the demand for activities on the network grows. It refers to a blockchain's network capacity to support a growing amount of work. It is a non-functional requirement that is used to gauge the readiness of a blockchain network to accept demand as its network grows.
However, it is loosely defined as the ability of a blockchain network to achieve high transactions per second (tps) or transaction times, and the time it takes for those transactions to be validated and stored in each peer node in a way that it cannot be reversed or revoked. It is the ability for a network to support increasing load of transactions, as well as increasing the number of nodes in the network.
A blockchain network is regarded as having poor scalability when instead of having the option of being allocated extra resources such as computing power, servers, or bandwidth, it requires more efforts from the community to improve the network in such a way that it can handle increases in the workload.
The word "Scalable" is a term that has a different meaning in blockchain parlance. So when a blockchain network is considered as "Scalable" it usually means that the network can achieve a higher transaction per second (tps) than some known networks and this is usually achieved by modifying its consensus mechanism to suit the network and or modifying some parameters found in other networks.
C. Blockchain Security
Blockchain Security is a risk mitigation protocol that is comprehensive that involves components of cybersecurity frameworks, assurance services, encryption models, hashing mechanisms, and best practices to reduce risks that become apparent in the form of attacks and frauds.
As a novel technology that proposes to be spectacular, it needs to be highly secure. With all the benefits of blockchain technology, it is underpinned by the strength of the resource code which has to be carefully examined during development. Blockchain technology allows the source code to be transparent, thereby making it a target for hackers as the public network is permissionless and the benefits of a successful hack are lucrative. So while a network being highly scalable focuses on the benefits that blockchain technology provides, security focuses on the risks associated with the technology.
Blockchain networks come in different forms which differentiate the users who can participate and who can have access to data generated in a network. They are usually Public or Private blockchain networks which are used to describe who can participate in the network. Also, there are permissioned or permissionless networks that are used to describe how participants can gain access to data generated on the network. So because anyone can participate in a public permissionless blockchain network, it is susceptible to attacks by hackers and fraudsters. Some of the tactics that these hackers and fraudsters use to attack are phishing, routing, Sybil, and 51% attacks.
Blockchain technology is focused on bringing about trust in an ecosystem that lacks trust. The system infrastructure is decentralized, and the information that is generated on the network is available to members of the network and the public in general. In a blockchain network, all the participants or nodes are tasked with recording, passing along, and viewing any transactional data which is then verified and encrypted onto the blockchain. This process brings about trust and also the integrity of the data generated.
The decentralized storage of data ensures that each block is verified and then added to the chains of block through encryption. This means provides no way whereby the data can be hacked or a point of failure which exposes an entire set of data in a detrimental manner. Also, the use of the consensus mechanism among different nodes which brings about public record-keeping gives each of the nodes an insight into the data that is being stored.

Based on your knowledge, explain at least two viable solutions to the challenges posed in the Blockchain Trilemma.

There are many solutions that have been proposed and also deployed that are being used as a solution to the Blockchain Trilemma. I would do a discussion based on the popular categorization which is: Layer 1 and Layer 2 solutions.
Layer 1 Solutions
These are blockchain networks that develop a means of solving the trilemma through their main blockchain networks. Examples such as Algorand, Polkadot, Solana, and IOTA. I shall be discussing IOTA.
Algorand Blockchain
One blockchain network that tries to solve the blockchain trilemma using its main chain is Algorand. It follows a lottery-like protocol.
They focus on the validators on the network. They do this through a feature known as Randomness where an algorithm automatically picks a new set of nodes that would validate the blocks at different points in time. With this approach, decentralization is maintained as there would not be a 'stable' set of nodes that would be tasked with validating the blocks on the network. It also maintains security as no one knows the next set of validators to be selected. Scalability is achieved as the validators validating the blocks are few which makes validating blocks to be faster. This network system is called a Pure Proof-of-Stake consensus mechanism or PPoS.
Layer 2 Solutions
The other existing solutions are known as layer 2 solutions. These are solutions where a new blockchain network operates as layer 2 to help solve the scalability issues of the main chain (layer 1). A common example is Ethereum which serves as the main chain (layer 1). There are different types of layer 2 solutions but I would be discussing Zero-Knowledge (ZK) Roll-Ups.
Zero-Knowledge (ZK) Roll-Ups
Zero-knowledge rollups are a layer 2 solution protocol where groups of different sets of transactions are batched and taken to the main chain or layer 1 for validation and security through storage. It makes use of ZK-Snark (Zero-Knowledge Succinct Non-Interactive Argument of Knowledge) as the cryptographic proof.
An example of a ZK Roll-up layer 2 solution is Loopring. It is a blockchain system that provides trading and payment solutions.

Conclusion.

Since the invention of blockchain technology in 2009 by Satoshi Nakamoto, it was seen to be a promising solution to the problems associated with centralized systems. Blockchain technology tried to provide a safer avenue where transactions and storage of these transactions are secure and done in a quick manner.
However, as more users started to migrate to projects using blockchain technology, the trilemma effect started to become apparent. This is because most projects couldn't cope with providing a method where all three core of blockchain technology is actively used. In other words, due to the demands on these blockchain projects, two out of the three components of blockchain can be achieved. This has been an issue that dates back to the CAP theorem of decentralized storage.
Today many blockchain projects have been developed to tackle this issue. Some of the projects are the main blockchain itself such as Algorand, Solana, etc. They are called layer 1 solutions. Others are seen as sidechains or fondly called layer 2 solutions. Together these sets of blockchain projects are taking on the trilemma problem that is inherent in blockchain technology. Hopefully, more projects would be available to solve this trilemma problem in the future, thus leading to the widespread adoption of blockchain technology.
