The Genesis Block - Steemit Crypto Academy Season 5 - Homework Post for Task 3
Greetings to you all, Steemians!
Another super fantastic day has come where I’ll be talking about The Genesis Block as my third task, by answering a few questions. These questions actually helped me gain more insight into the subject matter while searching for answers to them. Take a look at the question below.
3a) What is a Cryptocurrency?
b) What is Cryptography and how does it make cryptocurrencies secure?
c) Explore the Steem Genesis Block and Sign in as proof of completion.
In this digital era, the importance of cryptocurrencies cannot be done away. Because, the emergence of a more secured transactional system in this ever-changing world has really helped to bridge the insecurities in our conventional banking systems. Of which cryptocurrencies have been a part of these changes to create a better transactional world for all of us.
These currencies are not being controlled by any central body or account, unlike the conventional banking systems where transactions are being issued, controlled, managed and even verified by a central authority. A very important feature of these virtual currencies is that since they are not issued by any central authority, they are immune and hard for anyone to manipulate.

What is a Cryptocurrency?
The word Cryptocurrency could be broken down into two different words having Crypto as the first, and Currency as the second. The former, being Crypto, is taken from the Greek word Kryptos meaning Secret. And the latter, being Currency, is taken from the Latin word Currere meaning movement or to run, which began to be in use around 1699 to describe the flow of money between people.
In my opinion, bringing these two words together forms the complete word Cryptocurrency which refers to the movement of secret messages from one point to another. These secret messages could either be referred to as a coin or token which is encrypted or made secret with a public key and could only be decrypted with a private key.
As earlier stated, Cryptocurrencies have no central authority that controls them because they work on a pear-to-pear system. As a result, we could say that these currencies can be defined as a digital currency that uses blockchain technology with different levels of Decentralized Applications for transactions and for storage, where crypto owners have full control over their assets without a third-party interference.
Additionally, a cryptocurrency is an encrypted (secret), digital token (or asset) that can be used as a medium of exchange in the real world because of its level of security, which made so many countries to adopt it while some are yet to adopt it into their systems.
More so, in order to make these currencies secured, the technology called Cryptography was adopted, which is the security system of the cryptocurrency blockchain, thereby making cryptocurrencies to be highly dependable in terms of its security. So then, what is Cryptography?

What is Cryptography and how does it make cryptocurrencies secure?
The word CryptoGraphy is coined out of two Greek words. The first is Crypto which as earlier stated, means secret. And the second is Graph which means writing or to write. This, in my opinion, bringing the two words together signifies that, cryptography refers to the system where written messages are being made secret in order to prevent third parties from seeing or accessing it. This implies that, with the use of Cryptography or Secret Writings, no third party could have access to a content that is sent to another party on the blockchain.
Cryptography has really made the cryptocurrency blockchain to be heavily secured, because, it only allows the sender and the intended recipient of a message to view its contents, thereby assuring content security by encrypting the content with a public key. When the message arrives at the recipient’s end, the content will have to be decrypted using the private key, else the message remains encrypted and no one will be able to access the content. In this case, the public key refers to the address of the wallet while the private key is used to authorize transactions.
Additionally, cryptography, which is the act of hiding these messages or tokens into a form known as ciphertext, helps to ensure that messages sent are fully delivered and read by the intended recipient.
In the cryptocurrency blockchain, before a user sends a token or coin to another user, he/she will have to request for the public key of (which in this case refers to the address of) the receiver. While sending the token, the sender encrypts the message with the receiver’s public key. At this point, the message or token is converted into a form known as ciphertext (which is a combination of alphanumeric and special characters). Upon arrival, the receiver could only decrypt the message to view its content by entering his/her private key, else the message remains in its encrypted state.
By this technology, tokens sent in the cryptocurrency blockchain are highly secured, safe and protected as any attempt to view the content without the private key will result futile.
More so, the sender of the message or token as well, cannot backtrack in the future and deny their reasons for sending the message or token as in some other kind of systems where the sender of the message changes his/her mind and retrieves, edits, manipulates or even denies creating such messages, thereby assuring safety and security of tokens.
In trying hard to achieve such levels of security to make transactions in the blockchain secured, different features and terms were used, which I mentioned a few earlier, like encryption, decryption, and even the keys to help make emphasis on this security system of the blockchain. Let’s take a look at them one after the other.
ENCRYPTION
This is the conversion of a text or message that is readable into an unreadable form by the application of keys. This is the phase where we refer the text as being in a ciphertext format, which is a series of randomized letters and numbers that humans cannot make any sense of. Because the text is now in the form of a mixture that includes special characters, alphabets and even numbers. Example is the encrypted text below.
57:65:6c:63:6f:6d:65:20:74:6f:20:74:68:65:20:63:72:79:70:74:6f:20:61:63:61:64:65:6d:79:20:62:65:67:69:6e:6e:65:72:27:73:20:63:6f:75:72:73:65:20:74:61:73:6b:20:33:2e
DECRYPTION
Ciphertext cannot be read until it has been converted into a plaintext. The process whereby these ciphertexts are being converted into a readable form is called decryption. At this stage, a form of key system is sometimes used to decrypt the text into a human understandable form. For example, using http://dolcevie.com/js/converter.html to decrypt the unreadable (or encrypted) text that is written above, we’ll get:
Welcome to the crypto academy beginner's course task 3.
Kudos to the great cryptographers who brought this technology into existence!
THE KEYS
For cryptography to really function properly, there must be a key system that enables all forms of encryption and decryption to work properly and securely. These keys are what help us to achieve a really secured cryptocurrency blockchain. let’s see these keys one after the other.
The Secret or Symmetric Key: This key system uses a single key to encrypt data. This actually implies that both encryption and decryption of a data uses the same key. I refer this to as the easiest form of cryptography key system.
The Public Key or Asymmetric Key: The Asymmetric key uses two keys to encrypt data. One is used for encryption, while the other key is used for decryption. This implies that there must be the Public and the private keys. The public key in this case can be used by anyone on the blockchain to encrypt the data. While the private key is only used by the account owner to decrypt the data being sent to him.
Hash Functions: In this case, data such as passwords could be encrypted by hashing. Examples are SHA-1 and SHA-2. They are irreversible and often a one-way code to protect the data.
Explore the Steem Genesis Block and Sign in as proof of completion.
In order to explore the Steem Genesis Block, you have to follow the steps highlighted below
- Go to https://steemworld.org/
- Click on Block Explorer
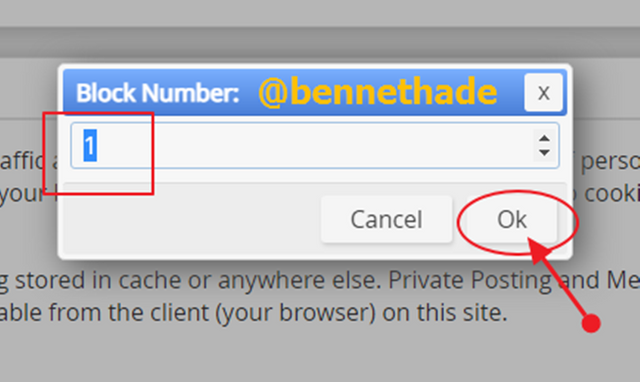
- In the dialog box that appears, input 1 and click on OK
- Then, a display of the Steem Genesis Block will be shown like the one below.
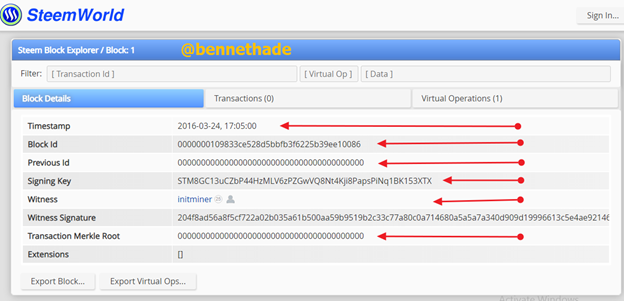
Carefully looking at the above screenshot shows that we have:
- The Timestamp
- The Block Id
- The Previous Id
- Signing Key
- Witness
- Witness Signature
- Transaction Merkle Root and
- The Extensions
In order to sign in to my account, I’ll click on the sign in button at the top-right corner of the screen.
Then I input my steemit username and private posting key and then clicking on the OK button signs me in as shown below.
- https://www.ig.com/en/cryptocurrency-trading/what-is-cryptocurrency-trading-how-does-it-work
- https://steemworld.org/block/1
- https://steemit.com/hive-108451/@awesononso/steemit-crypto-academy-season-4-beginners-course-task-3-the-genesis-block
- https://www.researchgate.net/publication/322456542_A_Short_Introduction_to_the_World_of_Cryptocurrencies
- https://www.kaspersky.com/resource-center/definitions/what-is-cryptography
- https://www.encryptionconsulting.com/education-center/what-is-cryptography/
- https://www.investopedia.com/terms/c/cryptocurrency.asp
- https://steemworld.org/block/1
Thanks for reading through!