Crypto Academy Season 3; Week 2 Homework Post for @pelon53: HASH, CRYPTOGRAPHY.
Explain what does the resistance to collision mean? And what does resistance to preimage mean?

ANSWER
For better understanding of resistance collision, let go a little into the ideology backs it.
What is hash?
A hash is an algorithm that generates a unique length alphanumeric that is associated with a specific file. The resulting hash will be different if the file is changed in any way and you recalculate the value. The hash process is commonly used to encode data or files into a series of alphanumeric values by many organizations, security agencies, and, most notably, the blockchain. Hash plays an important role in the blockchain network's major activities.
Resistance to collision
Collision resistance is a feature of hash functions that ensures its authenticity by making it computationally impossible to detect two colliding inputs. This feature can be thought of as a cryptographic hash function's security term for ensuring efficiency.
A minimum criteria for a hash function to be collision resistant was established in 2014: the length of the generated codes should not be lessers than 160 bits.
When researchers found that the SHA-1 algorithm had been cracked, they suggested SHA-2: Secure Hash Algorithm 2, which was a successor to SHA-1 and is now widely used. SHA-256 is an advanced cryptographic hash function that generates a 256-bit value, and this characteristic ensures nearly 100 % collision resistance using the hash function algorithm.
Preimage resistance
Preimage resistance is a feature of the hash function that ensures that for virtually all prespecified outputs, finding any input that matches that output is computationally impossible, i.e. the input that generated a hash is irreversible and cannot be changed to produce the same result.
Second preimage resistance
Second preimage resistance or weak collision: This dunctiont makes it practically impossible to identify any other input that has the same output as any given input, i.e. The possibility of two different files having the same hash output accidently are extremely minimal.
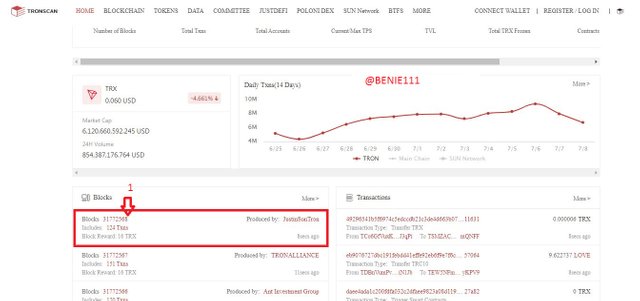
Use tronscan and etherscan to verify the hash of the last block and the hash of that transaction. Screenshot is required for checking.
Answer
To verify the hash of the last block using tronscan, visit the website https://tronscan.org/
Scroll down to where there are list of Blocks
- Click on the last Blocks (The last Block I met: 31772568)
- From the list, under the Block height (31772568), We have the Block hash: 0000000001e4cf98d808b45b06898c090bd0b2d7379102f759f6b47190c794b5
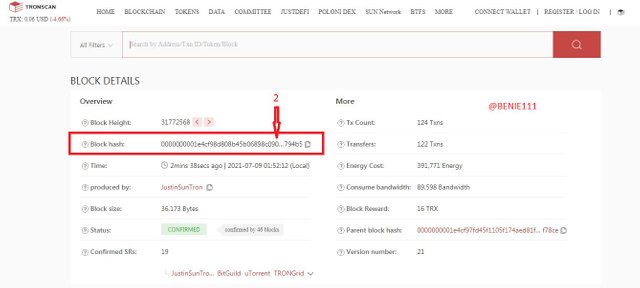
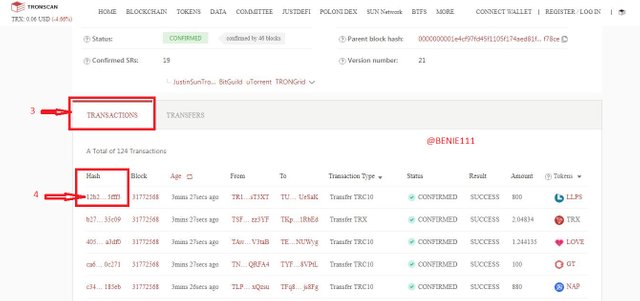
To verify the Hash of the last transaction on the block
From the Block page, scroll down to where we have "Transaction and Transfer" menu
- Ensure you are selecting on the "Transaction"
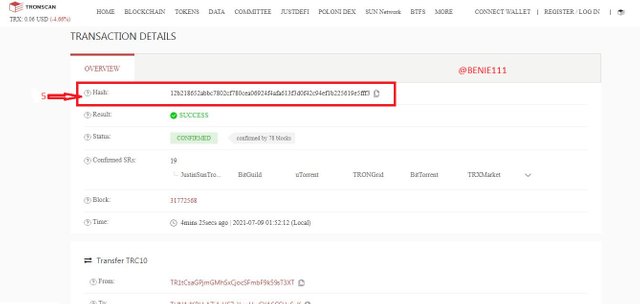
- Click on the last Hash under the Hash list to explore it
And then we have the Hash of the last transaction on the block (31772568) to be: 12b218652abbc7802cf780cea06924f4afa613f3d0f42c94ef1b225619e5fff3
To verify the hash of the last block using Etherscan visit the website https://etherscan.io/
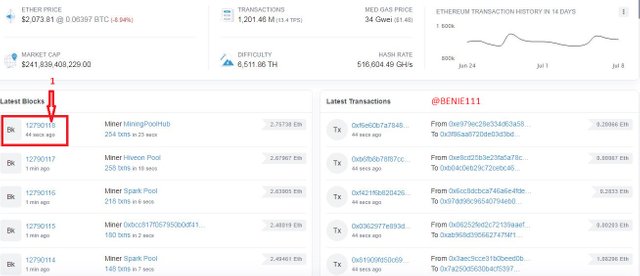
Scroll down to where the list of latest Blocks are
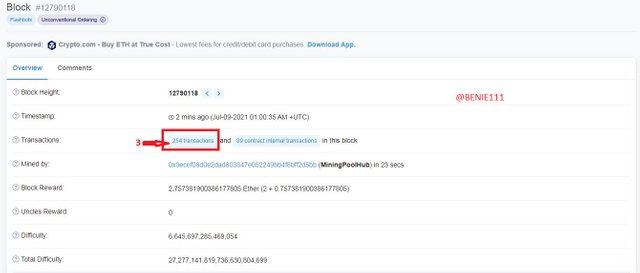
- Click on the last Block (The last Block I met: 12790118)
The next page contains all information about the block
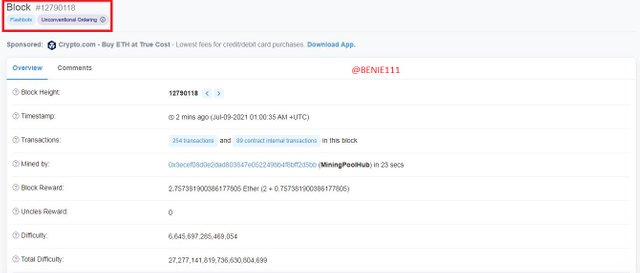
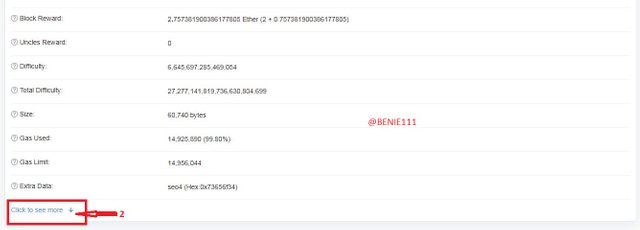
- Scroll down to where we have "Click to see more"
Then we'll see continuation of list of the Block information. There we have the the Block Hash: 0xbbdc5202d50a75026451553baafb4b3837b1c79ceefc5fec6ff976be9269cc0f
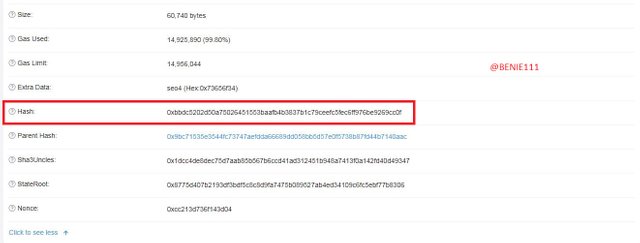
To verify the Hash of the last transaction on the block
From the Block page where we verify the Hash of the last Block, scroll up to the first set of list of the Block's information to where we have "Transaction"
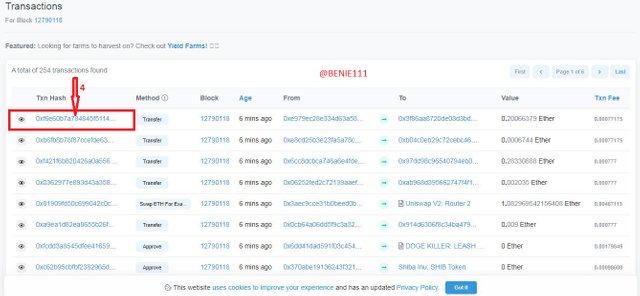
- Click on "Transaction"
The next page will be lists of transactions in the Block - Click on the latest transaction from the list
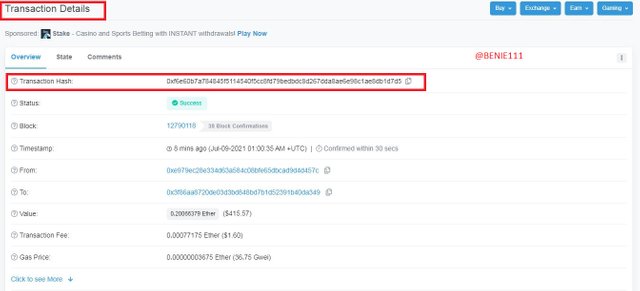
Here we have the list of the last transaction's details overview, and the first on the list is the Transaction Hash which is: 0xf6e60b7a784845f5114540f5cc8fd79bedbdc8d267dda8ae6e98c1ae8db1d7d5

Generate the hash using SHA-256 , from the word CryptoAcademy and from cryptoacademy. Screenshot required. Do you see any difference between the two words? Explain.
Answer
To generate Hash using SHA-256, go to https://passwordsgenerator.net/sha256-hash-generator/
- 1.) Input your desired data into the big space created for text
- 2.) Click on "Generate"
Then you'll have your generated output.
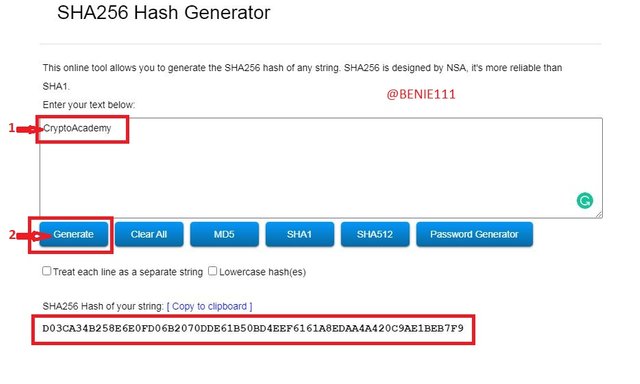
For "CryptoAcademy"
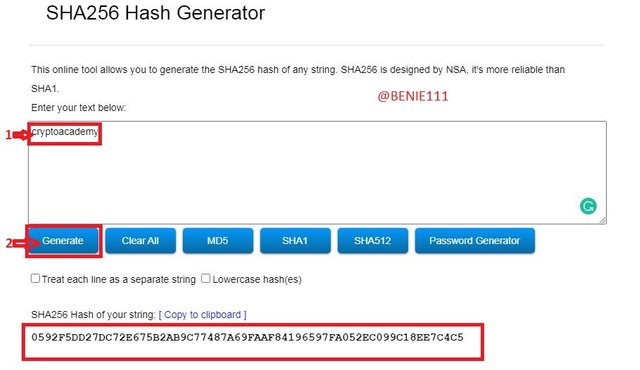
This was the Hash generated: D03CA34B258E6E0FD06B2070DDE61B50BD4EEF6161A8EDAA4A420C9AE1BEB7F9For "cryptoacademy"
This Hash was generated: 0592F5DD27DC72E675B2AB9C77487A69FAAF84196597FA052EC099C18EE7C4C5
Difference between the two words
There is difference between the two words which resulted into different Hash function output.
The words "CryptoAcademy" and "cryptoacademy" meant same things but were written in different forms.
CryptoAcademy has two Uppercase letters (C,A), while cryptoacademy only has lower case letters, which has distinguished the two words from eachother. This is enough for the Hash function generating Hash through SHA-256 to bring different output, and this is as a result of the Resistance of Collision. That is to prove the efficiency of the Hash function algorithm.

In your own words explain the difference between hash and cryptography.
ANSWER
Hash input is inherently irreversible, whereas cryptography input may be reversed and viewed using private keys.
Hash-generated outputs have a predetermined length, whereas cryptography outputs do not (The more the data, the more the output length)
Hashing does not require private or public keys to function, whereas cryptography requires.
Hash functions generate output from a specific file, whereas cryptography encrypts data continuously.
Hash cannot be used to convey private communications, whereas cryptography can be used to do so.

Conclusion
The use of Hash algorithm in the blockchain can not be overemphasized. And advancement has helped this algorithm in enhancing efficiency and security.
The Hash feature of Resistance to collision, is superb to avoid errors and the Pre-image Resistance fosters security. Instead of having loads of files, they can be coded into alphanumeric combinations with the use of Hash functions.
Now, blockchain is doing well and the world of cryptocurrency which was built on the Blockchain network is growing everyday, but the Hash is playing a serious role in it's success.
Thanks to Prof @pelon53 for this week's lecture
Gracias por participar en Steemit Crypto Academy Season 3:
Espero seguir leyendo tus publicaciones.
Me fue imposible ver algunos detalles de las captures de pantalla, muy pequeñas. Todas están así
Buen trabajo, continúe mejorando.
Recomendaciones:
Calificación: 8.8