Crypto Academy / Season 3 / Week 2 - Homework Post for professor @pelon53
Introduction
The arising need for secured communication between two nodes (sender and receiver), led to the development of standard protocols that can achieve this by generating a string of unique codes that can securely transmit the required information such that only the sender and the receiver can have access to the contents of the information. This process is known as Cryptography.
Cryptography consists of two main components, Hash and Encryption. They serve the same purpose of securing data for transmission but they do it using different methods. Hash is more conveniently secured than encryption, hash is widely adopted in the cryptocurrency world for the security of wallets and transactions and because of its irreversible nature.

Image Source
Resistance of Collision
Resistance of collision is a security attribute of a hash function that ensures that no two inputs produce the same output when the hash algorithm is applied to it. Collision is said to occur when two different input values of a hash function the same set of output values, thus compromising the essence of applying the hash function on the information.
The collision resistance of the first hash function SHA-1 was compromised because of the limited output value and thus led to the development of the SHA-256 hash function currently used.
The new has to function SHA-256 makes the chances of collision almost impossible to occur, and this makes the resistance of collision attribute achieved on hash functions in Cryptography since no two different input values can output the same values when the has function is applied.
Resistance of Preimage:
Resistance of preimage is a security attribute of a hash function that ensures that the input of a hash function cannot be determined by the output of the hash function. Resistance of preimage defines the irreversible nature of a hash since the sequence of operation is only forward. When the output of a hash is generated after a hash function is applied it is said to be impossible to get the input from the hashed output.
There are two preimage resistance: Preimage resistance and Second Preimage resistance. The preimage resistance protects the input such that the output can not determine the input.
The second preimage resistance ensures that no other second input can generate the same output as the first input. This is similar to the resistance of collision of a hash function.

Verifying hash using a block explorer
Block explorers are collect, and store data like block ID, hash, timestamp, wallet addresses from transactions in a blockchain. This helps in tracking transactions.
Using Tronscan
To verify the hash of the last block, first, visit the Tronscan Website.
On the home page, scroll down to the block and transaction section, where details of transactions can be seen, this changes very fast due to the volume of transactions performed.
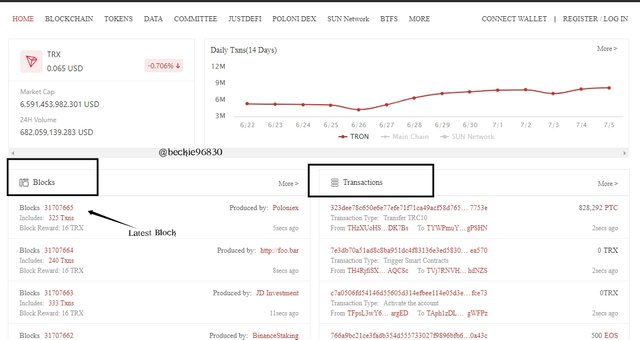
From the above image, the lastest block ID at the time of viewing was 31707665.
I clicked on the block ID to view more details
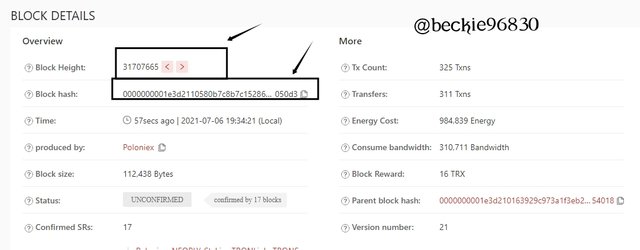
The new page displayed the details of the block showing the Block Height, Block Hash, Time, and other related information about the block.
The block has a hash : 0000000001e3d2110580b7c8b7c15286ad7a149242e72eb57810bb66088
050d3
Hash of the last transaction on the block
To verify the hash of the last transaction using tronscan :
Still, on the block page, scroll down to the transaction section.
Highlighted below is the latest transaction.
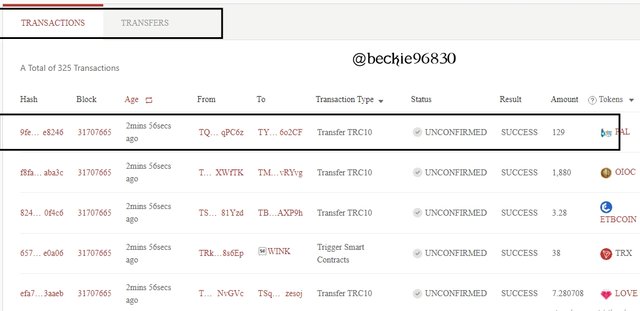
Then click on the hash to view the hash of the transaction.
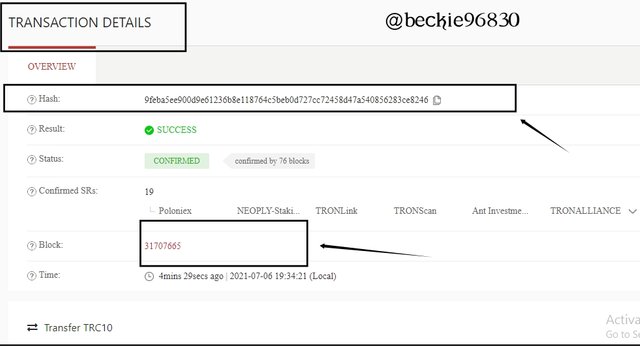
This displayed the details of the transaction and indicating the block.
The hash of the last transaction is : 9feba5ee900d9e61236b8e118764c5beb0d727cc72458d47a540856283ce8246.
Using Etherscan
To verify the hash of the last block, first, visit the Etherscan Website
On the home page, the list of the latest blocks and transactions is displayed.
Next, select the latest Block to view the hash of the block.
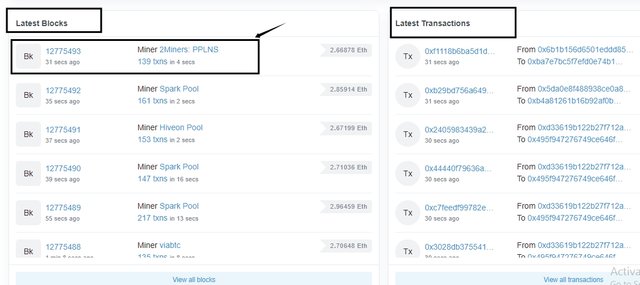
This displays a descriptive page about the block.
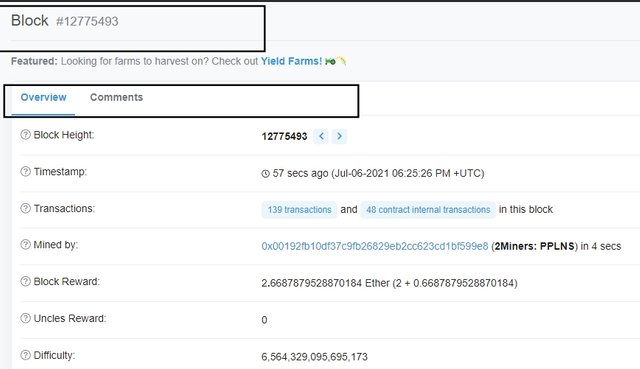
To view the hash of the block, scroll down and click on show more.
On the later section, the hash will be displayed.
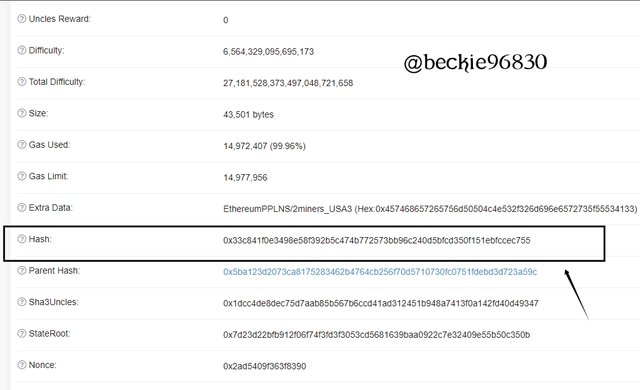
As shown, the hash of the block is: 0x33c841f0e3498e58f392b5c474b772573bb96c240d5bfcd350f151ebfccec755
Hash of the last transaction on the block
To verify the hash of the last transaction using Etherscan :
Scroll up on the block page and click on transactions.
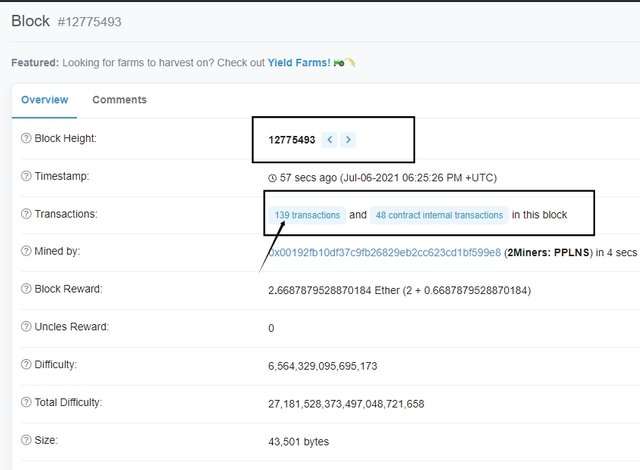
Next, click on the lastest transaction to view the details.
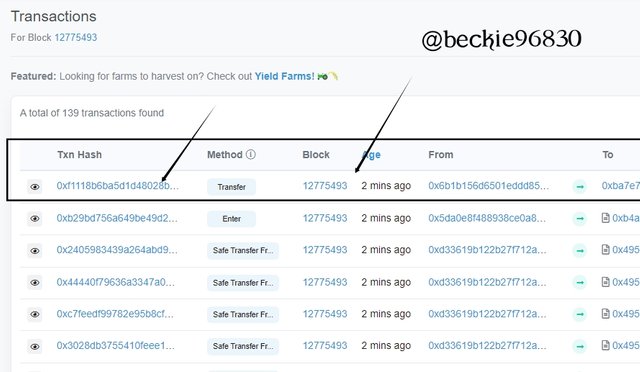
On the new page, the hash of the transaction will be displayed.
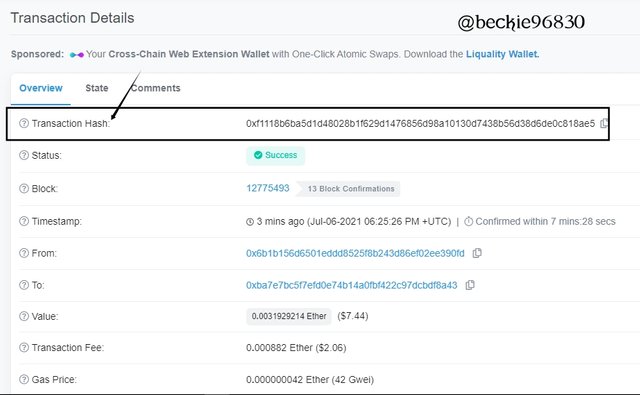
The hash of the last transaction is : 0xf1118b6ba5d1d48028b1f629d1476856d98a10130d7438b56d38d6de0c818ae5.
Generating Hash Using SHA-256
Using the link provided, link.
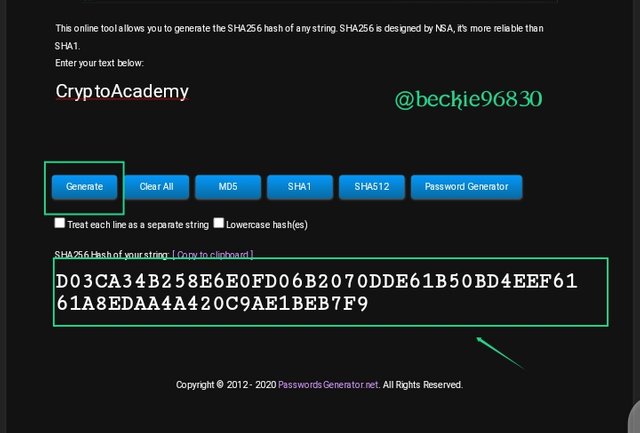
Next, input the words, and click generate. The hash will be displayed.
The first word CryptoAcademy generated a hash : D03CA34B258E6E0FD06B2070DDE61B50BD4EEF6161A8EDAA4A420C9AE1BEB7F9
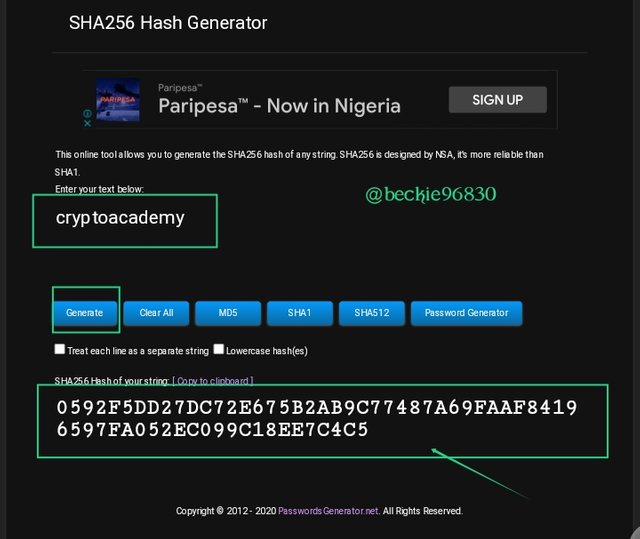
Next input the second word cryptoacademy, it generated a hash : 0592F5DD27DC72E675B2AB9C77487A69FAAF84196597FA052EC099C18EE7C4C5
Difference
The two input values are different which generated different hash values after the hash function was applied.
The first word had two letters in uppercase form C and A, and the rest were lowercase letters.
While the second had all letters in lowercase.
This noted difference in the input caused the generation of different hash values. This shows the uniqueness of hashing.
Difference between Hashing and Cryptography
Hashing and Cryptography perform similar duties, which is to secure the transmission of data. But there are some differences between them.
| Hashing | Cryptography |
|---|---|
| 1) Hashing is irreversible, this makes it impossible to generated input from the hash value | 1) The input can be generated from the ciphertext (encrypted data) using the private keys. |
| 2) Hash is more secured because of its one-way nature. | 2) Depend on how users secure the keys for security. |
| 3) No exchange of keys is required, algorithms calculate to check if the hash value is the same. | 3) Requires the two users involved to has access to keys for decryption, thus transmission of data has to take place first( sending private) |
| 4) Hashing has a fixed value of length | 4) The length of data is limitless. |
Conclusion
Hashing and Cryptography as stated both security feature that protect data for transmission, and are useful to ensure security.
Hashing use the hash function algorithm to parse the input and create a fixed value output that can not be traced or reversed to the input. Cryptography or encryption use private and public keys to turn input to cipher text before transmission and also required the private key to decrypt the information.
Hashing is preferred in crypto as its irreversible feature allows for secured wallet and password safety. This makes it more secured than cryptography.
Thank you professor @pelon53 for this wonderful lesson.
👆 Es casi imposible, pero un atacante puede adivinar el hash y encontrar la entrada.
Pregunta 1: Bien Tu respuesta.
Pregunta 2: Bien explicada y las captures.
Pregunta 3: Muy bien analizada.
Pregunta 4: Bien las diferencias de hash y criptografía.
Muy buen trabajo, felicitaciones y continua así.
Calificación: 9.8