Crypto Academy / Season 3 / Week 8 - Homework Post for @stream4u / Blockchain CryptoGraphy / Symmetric and Asymmetric Cryptography
Greetings dear fellows I hope you will be well and enjoying good health by the grace of Almighty Allah who is most merciful and gracious to everyone.
Today I have attended the lecture of professor @stream4u about CryptoGraphy. And I have learned a lot from this lecture as its working, its benefits, and different types such as asymmetric and Asymmetric cryptography. so if you want to go deep in cryptography then you must join the lecture of the professor.
.jpg)
So let's start learning about the CryptoGraphy and its different features, types as well as the role of the different keys in cryptography.
Explain the Blockchain CryptoGraphy and mention few names which are the Blockchain Platforms?
Cryptography
Before going through the blockchain cryptography I want to define and explain the concept of the CryptoGraphy. Cryptography is the method used to protect the information during the codes by using different specific codes and keys. No doubt it is done by a third-party service but it is 100% secure and the information cannot be hacked. The information can only be seen by the sender and the receiver. The receiver can also do not see the information directly but the receiver has to enter the specific key to see the information.
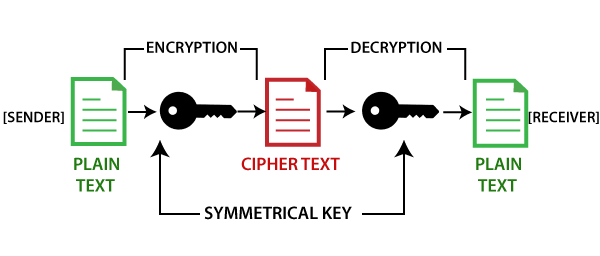
Basically, it works on the basis of the Encrypryption and Decryption. When a sender sends the information, he encrypts the information with certain codes, and to reveal the data receiver has to decrypt the data after applying certain keys. So this is amazing technology due to which we can easily send or receive our information without the chances of being hacked. Even the higher authorities like Govt can also not access our data and it will be transmitted directly without any stealing. So it is a cryptography technology.
Blockchain CryptoGraphy
First of all, I want to explain a little bit the word Blockchain. As it is a combination of two words; one Block and the second is Chain. The block is termed as a collection of data and the chain is termed as a public database of these blocks (collection of data) and in the blockchain, this data is stored in the form of a list. And these lists are simply connected by using cryptography technology.
And the implementation of the cryptography technology in the blockchain database is known as blockchain cryptography. As blockchain is a growing list of records and we know that the blocks are connected to each other by using cryptographic technology.
Blockchain Cryptography is defined as the use of the cryptography technology in the blockchain to secure the transactions, as well as the sending and receiving of the messages between the blockchain users to make them private and the public cannot access these messages and transactions as these are secured by the certain keys and codes.

Brief Overview of Working
Its working is simple firstly the persons who want to secure their transactions and other information by using cryptography blockchain. They should be connected to the same blockchain.
Imaghe Credit Goes to Tutorial and Example
After this, the sender makes a transaction or sends a message by using the encryption key under the influence of a 3rd party but it is secure and no one can access this information without using the specific decryption key. Now the receiver uses a decryption key to reveal the information it is how the cryptography blockchain works and makes the transactions and other messages secure. And all these keys are specific and unique.

Few names which are the Blockchain Platforms
 Image Credit Goes to CoinGeek
Image Credit Goes to CoinGeekDue to the benefits of blockchain technology, there are a lot of platforms that are working and are successful due to the use of blockchain technology. Blockchain technology has become an important thing and its importance can't be denied. There are a lot of blockchain platforms some of them are given below:
Ethereume: It is a leading blockchain platform. It is also known as ETH. It has vast applications and allows its users to build new Ethereume based projects and new cryptocurrencies. It also has its own cryptocurrency. Firstly its speed of transactions was slow. But recently its London hard fork has been implemented due to which its transaction speed has been increased as well as the fees for the transactions has been decreased.
Tron: It is another most wonderful and leading blockchain introduced by Justin sun. Its transaction speed is the fastest and costs a little fee in the form of the Trons (TRX). It is its own cryptocurrency to empower Tron blockchain.
EOS: EOS is another major and distinctive blockchain platform. Like ethereum blockchain it is also used to design and develop new applications. It has another amazing facility of storage as it provides decentralized storage enterprise solutions which help to solve the scalability problems as these scalability problems are faced in the Bitcoin and Ethereum blockchains.
Moreover, IBM, Steller, Tezos, Corda, Multichain, Hyperledger Fabric, Open-chain, Quorum, Hyperledger Sawtooth are all these platforms that are based on blockchain technology but everyone has its own unique technology and working methods, advantages, and disadvantages.

Explain the Public Key CryptoGraphy
Public key cryptography is a unique class of cryptographic protocols and it works on the basis of the algorithms. It is the fundamental of the blockchain and it uses codes to verify the data at different places. As it is a public key so it can be shared with anyone without any hesitation and problem.
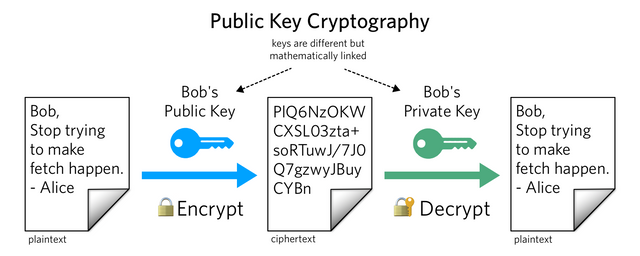
Image Credit Goes to Twilio
In fact, it is created by the private key but by using this key no one can access the private key because these are completely different from each other. It can also be used to send or receive cryptocurrencies to one another.
We can understand this public key as like in the steemit as we use the public keys for the transactions in the steemit wallet. This public key is used for encryption as well as for the decryption of a message. If a user is sending a message to someone else and wants to encrypt that specific message for that specific person. Then the sender will use the public key of the recipient and send the message in the blockchain.
And now the receiver only can decrypt that message to see the information whose public key has been used but for the decryption, the receiver has to use his private key. So we can say that only by that private key this message has been decrypted to which the public key has been linked.
The use of the public key is really very amazing and appreciatable. All the funds sent or received by this process are safe and sound as only a person having a linked private key can access the info and transactions. Moreover, it is an amazing feature of the blockchain cryptography technology than the banking as even the Govt cannot access your money in the blockchain.

Explain the Private Key CryptoGraphy.
This is the most important key which gives you all the control of your wallet. It is a specific key without which you cannot access and use your wallet. It is just like a specific key for a specific lock. When we want to make a transaction of sending a cryptocurrency then it is the key that is used to send the cryptocurrency to others. Without this key, we cannot send our funds anywhere. So we should keep it safe and sound.
These private cryptography keys are unique and are produced by the Asymmetric CryptoGraphy. These private keys are produced by the most complicated method by using mathematical techniques. Humans cannot perform such calculations and cannot make such keys themselves.
No doubt these keys can be repeated but it took hundreds of years to repeat these keys and you can understand that it is impossible for a person to remain in the world for hundreds of years. Sop these private keys cannot be accessed.
There are some specific requirements for the development of the private key. It is composed of almost 64 characters which consist of the numbers as well as on the alphabets.
As well as the private keys have advantages that no one can access except the owner but it has one serious disadvantage that if you lost your private key then you cannot get it back and all of your funds will be stuck in your wallet as without private key you cannot send them or transfer them anywhere.

Explain the Digital Signatures CryptoGraphy and what is Singing Of Transaction/Message?
A digital signature is a cryptographic value and it has the same importance as a handwritten signature has as it is used to access banking documents as well as other important things of daily life. Just like a hard copy signature, a digital signature is used to access digital data and it has an important role in the world of cryptography. A digital signature is just like a transaction that is done by the private key. It confirms that the person has his own private key to access his data.
In all the wallets there is a digital signature system. Whenever a user requests a transaction a digital signature appears and the user has to confirm that by using his private key. And every time for each transaction, there is a unique signature.
For Example, When we use TronLink wallet and linked it to any supported website and want to perform any transaction then a signature window appears to confirm that the user itself is doing a transaction by using his own private key. As we have already logged in to the tronlink wallet with the private key and it is directly linked to that 3rd party website but it is safe and sound.
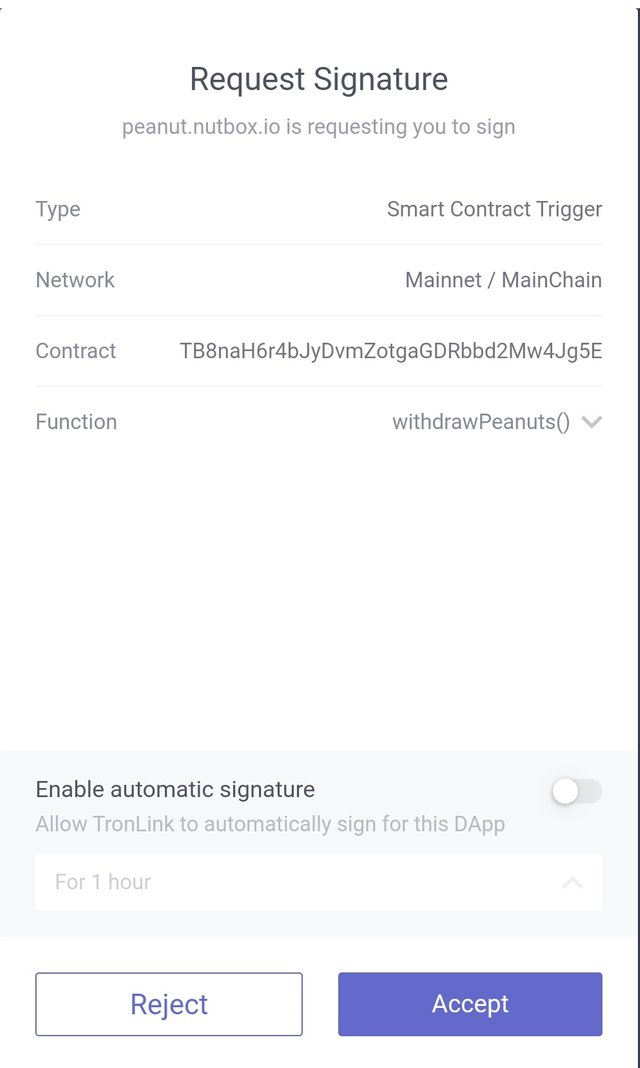
Screenshot Taken By From TronLink - Extenstion
So now we have to do the digital signature to proceed with this transaction.
It is as same as a person prepare a document for any purpose (Legal Purpose) which cannot proceed without the handwritten signature until the specific person gives his handwritten signature. So when the specific gives his handwritten signature the work is proceeding to the next level.
So in the digital signature system, we have to sign by using our private key to proceed with the transaction. It is an amazing feature of cryptography that makes your transactions secure and authentic. Basically, it is the confirmation to read the data correctly before doing any transaction and it is the last step in the transaction to confirm.

Singing Of Transaction/Message
Singing Of Transaction/Message is a process in cryptography in which a sender changes the transaction data into the hashes by using the hashing function. By this process, a digital signature is integrated into the transaction. And this integration of the signature to the transaction, we will learn in the last question in the practical work. For now, I am not going deep.
After this the receiver confirms the data and confirms the signature if it corresponds to his private key then he confirms and converts it top hashes by using a hashing function. It's more information is also available in the last question of practical work.
After the verification, the sender sends it after matching the hashes and if the hashes are obtained become a match then the transaction will be processed but if these do not match then the transaction will be invalid and could not be able to proceed.

Explain what is Symmetric and Asymmetric cryptography?
Cryptography is playing a key role in securing online transactions, messages, and cryptocurrency transfers and giving protection to the online financial system in the blockchain. Cryp[tography has been divided into two different categories:
- Symmetric cryptography
- Asymmetric cryptography
Symmetric Cryptography
Symmetric cryptography is also known as the Single Key Encryption as it uses a single, only one key for the encryption and decryption everywhere. This single key used for the encryption is also known as the secret cryptographic technique.
The main purpose of this key is to encrypt the plain text (Normal Text). The Symmetric Key is the oldest technique that is used for the encryption of the data. This method is as old as it had been using from the Roman Empire. There was a person whose name was Caesar’s cipher and later on, who was given the name of the Julius Caesar, he was an army officer and used the method of symmetric encryption to encrypt the military messages. It is the best practical example of symmetric key encryption.
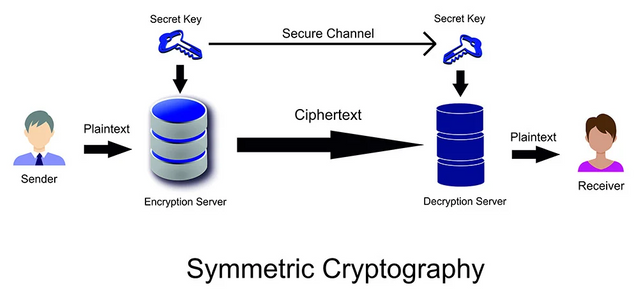
Image Credit Goes to Trenton Systems
The working of symmetric cryptography is simple and can easily be understood as it works by using a stream cipher or block cipher for the encryption and decryption of the data. In the stream cipher, the plain text is converted into the ciphertext (Specially coded text) and a block cipher converts the blocks, of plain text, using a key length. These key lengths are different and can be used accordingly such as 128, 192, or 256 bits.
The important condition for this encryption type is that the sender and the recipient must have the encryption keys to encrypt and decrypt the data. As the sender use keys to encrypt data as well as the recipient use keys to decrypt data.
Advantages of Symmetric Encryption
Symmetric encryption has many advantages but I am going to discuss some main advantages to make the post not so long as this topic is very vast and many posts are required to publish on this topic. So some of them are given below:
It can easily encrypt and decrypt a lot of data quickly in just moments. As its keys are very short and simple than Asymmetric Cryptography encryption.
It is easy to operate because of its simplicity.
AES iteration of the symmetric encryption cryptography is the most secure form of data encryption. it is so much secure that it cannot be cracked. But here I want to mention that it can be cracked but it takes billions of years to crack by using brute-force attacks which are very difficult.
Due to the high security and reliability it has been honored that it has been used for decades in the industries and it has a mass adoption and acceptance.
Disadvantage of Symmetric Encryption
It has one major and serious disadvantage in that it uses only one, private key, secret key, or cryptographic key to operate the transactions. So if unfortunately, it happens that we have lost that single key then we can do nothing except feel sorrow as we cannot recover that key.
The other major issue is its security which has low efficacy than the Asymmetric as Asymmetric is considered to be more secure but Symmetric is fastest and Asymmetric takes more time for the encryption.

Asymmetric Cryptography
Asymmetric cryptography is completely opposite to Symmetric cryptography as in symmetric cryptography only one secret cryptography key is used for the encryption. But in Asymmetric cryptography, a pair of cryptographic keys is used. This pair is of a public key as well as a private key which are linked together and this pair is used to encrypt and decrypt sensitive data sent by the sender and received by the recipient.
In symmetric cryptography, the plaintext is converted into ciphertext and so on but in Asymmetric cryptography, a pair of keys is used for this purpose.
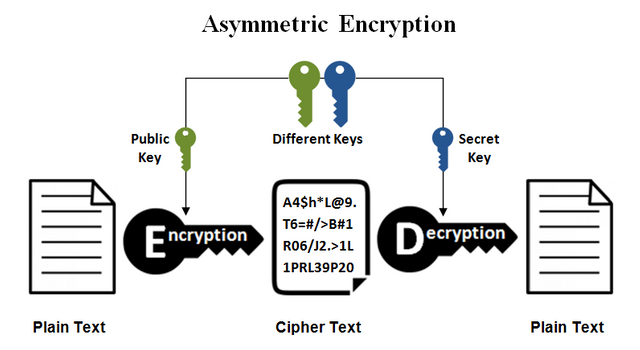
Image Credit Goes to SSL2BUY
Working Explanation
I am going to explain the working of Asymmetric Cryptography encryption. Suppose there are two persons A and B and person A wants to send information to person B then person A will collect the public key of a person B and will encrypt the information and will send it to person B. Now the person B will use his private key to decrypt the data and in this way, it all works. And no one can access this information except person B as the private key of the person B is unique and only B has his private key. It is so much secure even person A also can not access this information as he cannot decrypt this data as he has no private key of B.
So it is the working procedure of Asymmetric cryptography. Asymmetric encryption also offers digital signature authentication which makes it more unique from symmetric encryption.
Advantages of Asymmetric Encryption
The best advantage of Asymmetric encryption and cryptography is that it is more secure than Symmetric cryptography as it uses a pair of linked cryptographic keys.
Another thing in cryptographic encryption is the key distribution channels which are difficult due to the complications. But Asymmetric encryption has eliminated this factor and has made encryption easier.
It is more secure as in this encryption exchange of the private keys is not necessary and the private keys remain at their place. Because in this system public key is used for the encryption and then for the decryption private key is used which always remains to the person who receives data for the decryption.
It has another security benefit that in the Asymmetric encryption for the digital signature private keys are used in which a sender uses his private key to sign a transaction and does not use any untrusted 3rd party.
Disadvantages of Asymmetric Encryption
Indeed Asymmetric cryptography is more secure than Symmetric cryptography but it also has some dark aspects.
The main disadvantage of asymmetric encryption is that it is a slow process. It takes more time for encryption and decryption. Because it uses a pair of linked keys; i.e linked public and private keys.
It is difficult to use as first we need a linked public key to the private key to encrypt a message and then the recipient needs his own linked private key to decrypt the message. And it is not smooth work it is time-taking as well as difficult.

Key Distinctions between Symmetric and Asymmetric Cryptography
Both of the cryptographic types are very useful and have their own unique features. But some of the distinctions between these types are given below:
Security and Speed: The key difference between the symmetric and asymmetric is speed and security. Symmetric cryptography is fast but less secure than Asymmetric cryptography. But Asymmetric cryptography is more secure than Symmetric cryptography but has a low speed.
Usage Feasibility: Symmetric cryptography is simple and easy to use as it is not complicated. Because Symmetric cryptography uses only one secret cryptographic key. But Asymmetric cryptography is difficult to use as it uses a pair of the linked keys, and it is time taking.

How Blockchain Wallets CryptoGraphy works and explains the available types of Crypto Wallets
As we know a wallet is something to store some money. And we use physical pocket wallets as well as handy wallets to store our money. Similarly, blockchain wallets are those wallets that are used to store digital money which is known as cryptocurrency. These are digital wallets and we cannot touch them and cannot feel them. These are the abstract wallets but there are some digital numbers and transactions which we can observe.
Blockchain wallets operate simply with the help of cryptographic keys. When we create any wallet using any 3rd party they provide us unique cryptographic keys to operate our wallet. These keys are unique and without those keys, we cannot access our wallets.
After the creation of a blockchain wallet, we are provided with a specif address of our wallet to receive our funds. This address is just like our bank account number which we use in our traditional banking system. If we want to receive or anyone wants to send us cryptocurrency then we will provide our blockchain wallet address.
Blockchain wallets are highly secured due to the use of private keys. As whenever you want to make a transaction you must have to verify that transaction with the help of the private key.
As we all know that we have a steemit wallet of the steem blockchain. We know that whenever we want to send our assets to others we have to confirm that transaction by entering our cryptographic keys again.

Types of Crypto Wallets
Crypto wallets are playing an important role in blockchain technology as we have need crypto wallets to send, receive or store our assets in the blockchain. Currently, there are different types of wallets that are working and are in demand due to their specific features. So now I am going to explain and tell you about different available crypto wallets:
Nowadays there are three types of wallets that are in operation and in demand and working properly. These three types of wallets are:
- Hardware Wallets
- Software Wallets
- Paper Wallets
Hardware Wallets
From the name, it is clear that it is a wallet that keeps our cryptographic keys in a physical hardware device. These are just like a flash drive and when we want to connect them to pc we can connect them by using a USB drive.
Hardware wallets are also known as the Offline Wallets as these wallets are not connected to the internet. And due to this reason, these are more secure wallets than other software wallets.
It has another major opportunity that if unfortunately we forget the device or lost the device then we can use a seed phrase which we have produced by using the device.
In the hardware wallets, your private key always remains in the device. During the transactions, the hardware wallet device requests the transaction details and then confirms the data itself.
No doubt these hardware wallets are more costly but it is also clear that these are more secure. So if anyone wants to store a lot of cryptocurrencies and wants to hold that then one must use the hardware wallets.
Software Wallets
Software wallets are also known as the Hot Wallets as they are connected to the internet. There are many types of software wallets but some of them which are most common are web wallets, desktop wallets, and mobile wallets.
Web Wallets:
A from the name we can guess that these are those wallets that can be accessed through a browser. These browsers have not any need to download any extra application. They can be easily accessed through a web browser.
For the web wallets, there is no need for any specific browser but the most important condition n is that you must have your password then you can access your wallet anywhere and at any time.
Desktop Wallets:
These are the wallets just like the desktop applications. We have to download a desktop application then we need to enter our login credentials to access our wallet. These are like web wallets but it requires a desktop wallet application like a Atomic wallet which is a desktop wallet. We can easily access our desktop wallet anywhere and at any time but need to have a desktop application and login credentials.
A desktop wallet is more secure than a web wallet as the keys of your wallet are only know you but it is sensitive as well. Because if you lost your wallet keys then you can lose all your data at once. So in order to secure your crypto assets, you should make a backup of your keys and should write in a hardcopy form.
Mobile Wallets:
These wallets are completely the same as desktop wallets but these are mobile wallets. These wallets are mobile applications. These are more flexible and easy to use. Mobile wallet has an important facility that most of the mobile wallets come with the QR code facility and by using this method we can easily sell or buy cryptocurrencies and can easily pay for the things by using our wallet.
But mobile wallets are more sensitive because if anyone knows your personal passwords, can steal your phone and steal your crypto assets from your mobile wallet as well.
You should keep your mobile wallet highly secured and must keep it away from malware and viruses as from these virus attacks people can steal your data and can easily access your mobile wallet.
Paper Wallets
Paper wallets are also knowns as Cold Wallets just like hardware wallets. From the name, it is clear that it is a piece of paper physically. And this is the paper that contains all the data to access your wallet.
No doubt it is a more secure type of wallet as it is offline and all the cryptographic keys are available on the paper, but it has also a great risk warning that if you lose your paper (specific cryptographic document) then you have already lost all of your cryptocurrency.
Another dark aspect of the paper wallet is that we cannot send or receive partial funds. So due to these dark aspects and insecurities, paper wallets are discouraged to use.

What is the Merkle trees and What its importance in blockchain?
This technology was firstly introduced by Ralph Merkle in 1979 due to which this technology is named Merkle trees. It is a fundamental part of blockchain technology. By using this technology the data of the blockchain is encoded in the form of a tree that is why it is known as a Merkle Trees.
Basically, it is a mathematical data structure that is composed of hashes of the different blocks which summarize all the data of the transactions in a blockchain.
It is used for the quick verification of blockchain data. And it can also be used for the quick transfer of the data from one node to the other node due to the peer-to-peer blockchain network. Bitcoin and Ethereume also use Merkle Trees technology. This Merkle tree is also known as the Hash Tree.
Working of Merkle Trees
All the transactions occurring in the blockchain network have their own unique hash. But these hashes are not in symmetry. But these are arranged in such a way that each hash is placed under the parent hash and they form a tree-like structure. And due to a lot of transactions, all the transaction hashes in a block are also hashed. This combination of small hashes into large hash results in a Merkle Root.
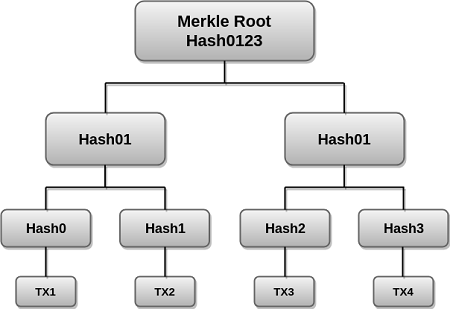
Image Credit Goes To Javatpoint
Here in this diagram, you can see the formation of a Merkle Tree. Here Merkle root or a Root hash is a complete block and we can see that this block is consists of four transactions. And each transaction is hashed again and again and stored into a leaf node due to which we obtain Hash 0, 1, 2, 3. Now all the leaf nodes are then summarized into a parent node by hashing Hash0 and Hash1 which gives us a Hash01. Hash01 is a combined effect of the Hash0 and Hash1.
Similarly when the hashes Hash2 and Hash3 are hashed into a single has then the resulting hash is Hash23 which is a combined effect of those hashes from which it is obtained. In the diagram, there is a mistake as there should be Hash23 instead of the Hash01.
Now at last the resulting hashes Hash01 and Hash23 are again hashed to get a Merkle Root as you can see at the top Merkle Root has obtained after hashing different transactions and hashing them again and again. And now the Merkle roots are hashed into a Header Block and produce a Merkle tree.
Importance of Merkle Trees in Blockchain
Merkle trees play an important role in the blockchain. Some of the important features of the Merkle trees are given below:
Merkle trees play an important role in maintaining the integrity as well as the validity of the blockchain data.
Merkle trees save the disk space as the proofs are numerically easy and fast.
Merkle trees require a small amount of information to be transmitted to the network.
Merkle Tree enables us to find the transaction data and any error in the blockchain easily as in the blockchain there are a lot of blocks. And without the Merkle tree, it can become difficult.

Practical + Theory
Functionality of Key
No doubt all the keys have their own purpose and benefits but In the blockchain cryptography Private key as well as Public key are most important as these keys are of great use. We know that these two types of keys are used in cryptography for the encryption and decryption of information.
As we know that all the private, as well as public keys, are different and unique but we also know that the public key is related to the private key and they are linked to each other. Now I am going to prove it by some practical work with the help of the Andersbrownworth which provides all the demo things about the blockchain.
Screenshot taken from Andersbrownworth
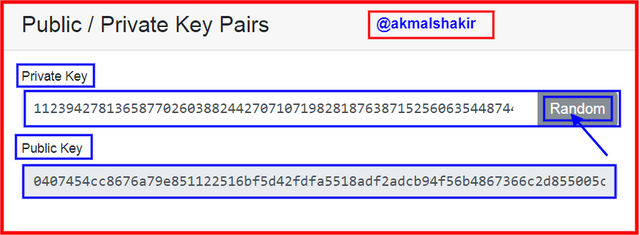
Here you can see the private as well as the public keys. Both these keys are completely different from each other but these are linked together. If we encrypt a message using this public key then that will only be decrypted by using this linked private key.
Private Key: 112394278136587702603882442707107198281876387152560635448744005023761652700997
Public Key:
0407454cc8676a79e851122516bf5d42fdfa5518adf2adcb94f56b4867366c2d855005c5fca1ce96cacc84b2955216801c076af2197f1f90f27c3ebac49583f6c3
Now let's see if the next private key comes the same as it is.
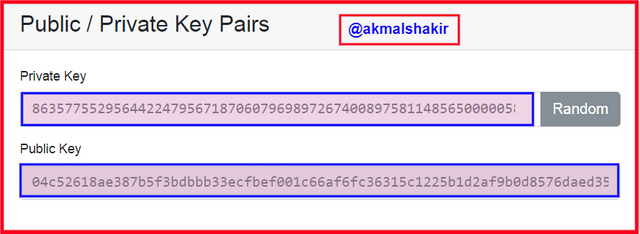
Screenshot taken from Andersbrownworth
Private Key: 86357755295644224795671870607969897267400897581148565000005860021391038015449
Public Key:
04c52618ae387b5f3bdbbb33ecfbef001c66af6fc36315c1225b1d2af9b0d8576daed35fd647a77f50ff12fdc4547e7b4017eb26d3b3d64d0564610d8bab26bab0
Here you can see that all the private, as well as public keys, are different from each and Private key is made up of only numbers and the public key is made up of numbers as well as of alphabets.
Here I want to mention for the security concerns that we can share our public key to others to receive funds correctly but please always remember we have not to share our private key. And if we share our private key then we have lost everything.
Signature
As we have already discussed that signatures are very important and play an important role in the transactions as by the signatures we confirm the message. But many users do not know how it works? So now i am going to explain that how it works.
 Screenshot taken from Andersbrownworth
Screenshot taken from AndersbrownworthTo see the working procedure of the signature please click on the Signature button as i have highlighted.
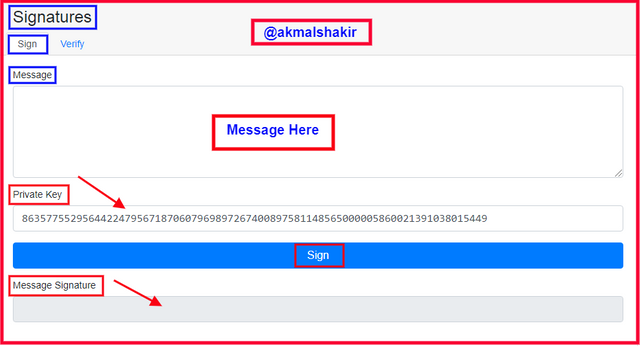 Screenshot taken from Andersbrownworth
Screenshot taken from AndersbrownworthAfter clicking there we will see a new window like this. Here you can see different options and fields which are required to be filled to sign a message.
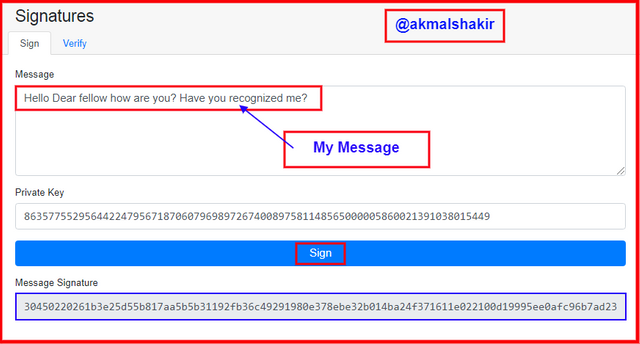 Screenshot taken from Andersbrownworth
Screenshot taken from AndersbrownworthAfter typing the message I have clicked Sign and you can see that our message has been signed with a unique code. And it means we have successfully signed a message.
I have obtained this signature
30450220261b3e25d55b817aa5b5b31192fb36c49291980e378ebe32b014ba24f371611e022100d19995ee0afc96b7ad23659b8a428e918a3eb5661ec82216a26b1f1a3ab9fcef
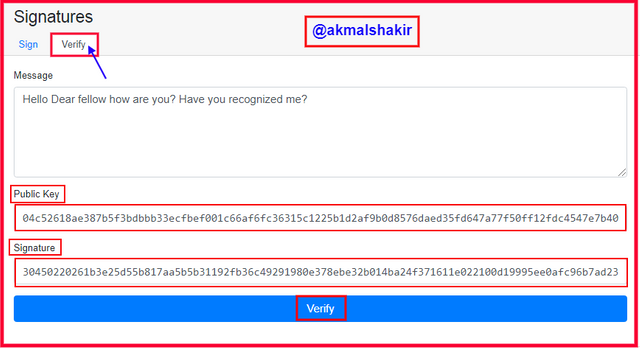 Screenshot taken from Andersbrownworth
Screenshot taken from AndersbrownworthHere you can see that when I went to verify the signature and message then we can see that my public key has been shared with the recipient so that he can verify that this message is from me.
And for the verification when we click Verify then the complete box becomes Green and tells us that the message has not been modified before the signature you can see in the below picture.
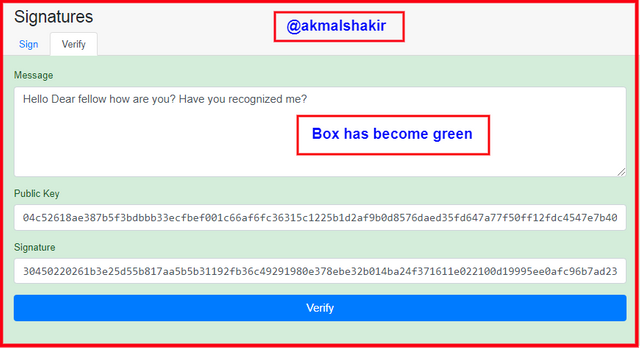 Screenshot taken from Andersbrownworth
Screenshot taken from AndersbrownworthHere you can see that the message has been signed successfully as it has been verified.
Now we will check if we change the/modify the message then what happens?
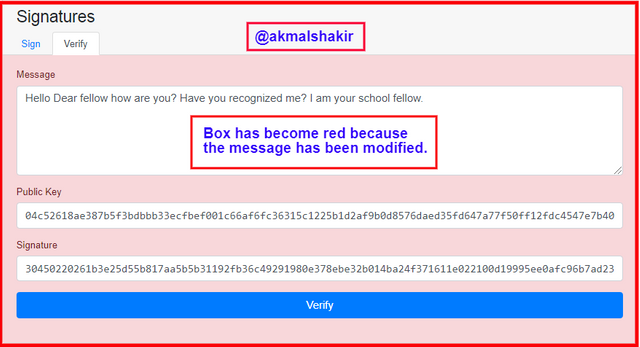 Screenshot taken from Andersbrownworth
Screenshot taken from AndersbrownworthHere you can see that I have modified the message and then when I clicked the Verify then the box became red showing that the message has been modified. Due to which this transaction has become invalid and if we want to make the transaction valid after modifying the message then we must have to sign the message again to get a new signature of the modified message.
Now i have signed this message again and now i can see that the new signature code is different which is given below:
3044022022f92a57a61203d46fe5e0de93b8ab1c77dd8d8e905ad2436363a8372300ed5402207604fc19fe48c27ecb2f088eca2b625fb15addfdcefa7241f80de17e3127df33
Now if I go and click on the verify then I will get verification successfully and all the boxes will turn green.
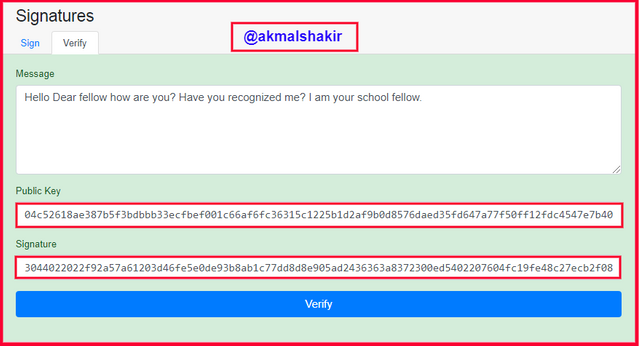 Screenshot taken from Andersbrownworth
Screenshot taken from AndersbrownworthHere you can see that the Signature has been changed from the first signature which we obtained before the change in the message but the public key is the same all the time.
Now you can see that the validation has become successful after signing the message again after the modification in the message.
Transaction
As we have already discussed that the cryptography transactions are encrypted and decrypted with the pair of keys linked with each other; i.e Private key and Public key and with the signature
 Screenshot taken from Andersbrownworth
Screenshot taken from AndersbrownworthTo see the procedure of a transaction we have to click on the Transaction button after clicking there we will see a new window as you can see below:
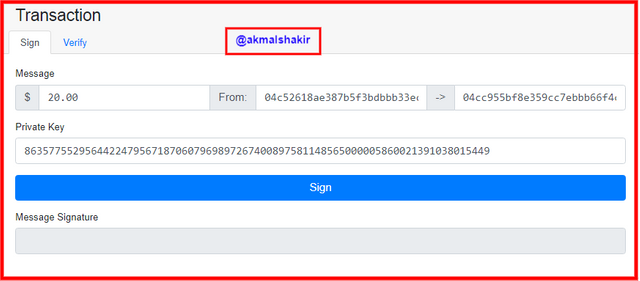 Screenshot taken from Andersbrownworth
Screenshot taken from AndersbrownworthHere we can see the message with the private key. And in the message, there is a sender's address and the receiver's address for the destination. As you can see as I have highlighted it in the below picture.
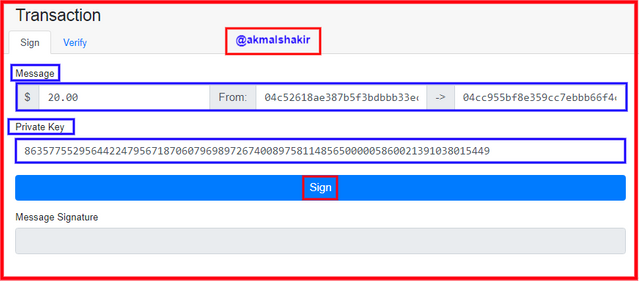.png) Screenshot taken from Andersbrownworth
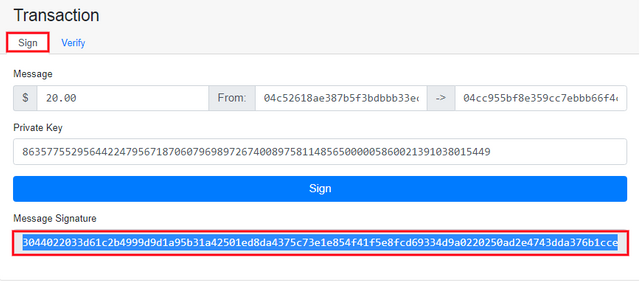
Screenshot taken from AndersbrownworthI have signed the transaction and I have obtained the message signature which is
3044022033d61c2b4999d9d1a95b31a42501ed8da4375c73e1e854f41f5e8fcd69334d9a0220250ad2e4743dda376b1cce21babb2c1af3f12d2ee7c10d201f841520d696a8d4.
 Screenshot taken from Andersbrownworth
Screenshot taken from AndersbrownworthNow I have to confirm this message signature and the private key of the recipient. For this purpose, I will validate the data by clicking on the sig in. And if the transaction is valid and the signature corresponds to the private key of the recipient then the transaction data is valid.
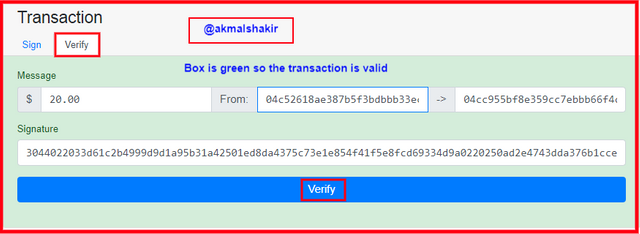.png) Screenshot taken from Andersbrownworth
Screenshot taken from AndersbrownworthYou can see that this transaction is valid as the green color in the box has appeared.
But if any error occurs in the signature and in the private key then the box will show a false result and the color of the box will be red.
Now in order to test I have changed the last three digits of the private key and let's see what happens.
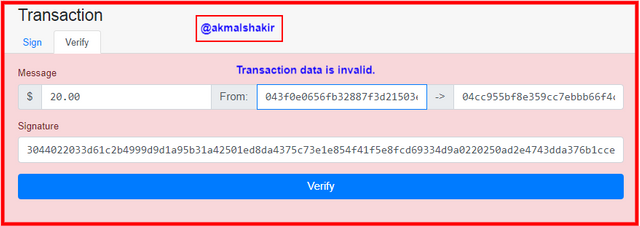 Screenshot taken from Andersbrownworth
Screenshot taken from AndersbrownworthYou can see that the result is invalid as I changed the last three words of the private key. So if we want to validate this message then we have to sign the transaction with the changed private key to get matched the private key of the recipients to the signature.
Blockchain Understanding
 Screenshot taken from Andersbrownworth
Screenshot taken from AndersbrownworthIn order to understand the blockchain validation we have to go to the Blockchain Section
 Screenshot taken from Andersbrownworth
Screenshot taken from AndersbrownworthHere we can see that in all the Peers Peer A, Peer B, and Peer C the blocks are validated and the data is correct within the chain.
Now I am going to do a test if change anything in the block then what happens.
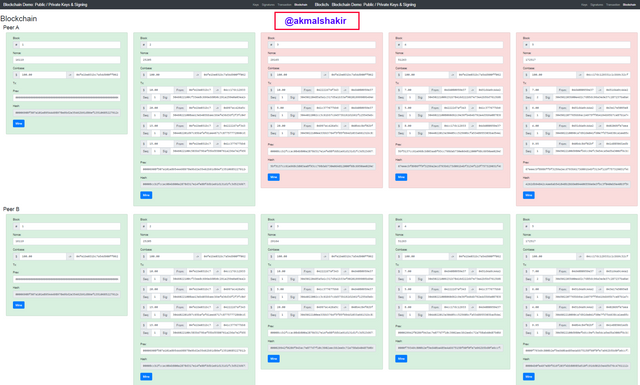 Screenshot taken from Andersbrownworth
Screenshot taken from AndersbrownworthHere you can see that I have modified the block 3 by changing the Nonce in then block 3, due to which all the remaining blocks have become invalid in the Peer A. As you can see in the picture that the only invalidation has occurred in the Peer A and all the remaining Peers are working properly.
We can make it validate by putting the correct Nonce and in this way, all the blocks will become validate in Peer A.
Her is an important point to be noted that all the blocks in a peer are connected to each other and every next block is connected to the previous one. That is the reason that the change has occurred in block 3 but invalidation has occurred in all the remaining next blocks including block 3.
So it is all about the keys, signature, transactions, and blockchain work. It is really an amazing thing to do again. I like this practice and doing again and understanding the new critical things.
Conclusion
Today blockchain cryptography is working everywhere and it is an amazing thing for secure transactions and due to its many benefits, there are a lot of platforms that are using blockchain technology such as Bitcoin, Ethereum, IBM, Stellar ...etc.
In blockchain cryptography all the keys are important but Public key and Private keys are most important and these cryptographic keys have their own working. But if we lose our private cryp[tographic key then we can do nothing except to bear and weep because we will lose all our crypto assets.
A digital signature is also very important in the world of cryptography as it confirms the message and authenticates that the message has not been modified before the signature.
There are two methods for cryptography; i.e Symmetric Cryptography, and Asymmetric Cryptography. Both these types are very useful but different from each other as symmetric cryptography uses only one secret key for the encryption and decryption of the data and it is fastest than asymmetric.
While Asymmetric cryptographic keys use a pair of the linked keys. But it is time taking process and it is more secure than symmetric cryptography.
Blockchain wallets are important digital wallets where we can store our digital currency. And these are secured by the use of the keys. And there is a specific address of a wallet just like the bank account number.
There are different types of blockchain wallets such as Hardware wallets, Software Wallets, and Paper wallets. and all these wallets have their own importance and features but hardware wallets are considered more secure because they are not connected to the internet.
Merkle trees are fundamentals of the blockchain as they manage the transactions by hashing them to blocks and then hashing them to Merkle Root. Then Merkle roots are directed to the header and make Merkle Trees. They play an important role to maintain the integrity and the validity of the data.
Moreover, the practical demo work is very amazing and I have learned many things myself by doing the practice. I want to thank professor @stream4u for adding all these tasks to the homework especially adding the practical work.
