Proof of Keys | Steemit Crypto Academy S4W7 | Homework post for @awesononso
Introduction
Hello to everyone,
In this post, there are the assignments of Professor @awsononso's 7th week lesson. This week the professor talked about Proof of Keys in general and talked about keys and wallets so we can get a clear understanding of this topic. In the light of the information he has provided, I will fulfill his assignments. I don't want to prolong it too much, I want to start the assignments directly. Let's start!

Question 1
Explain private and public Keys in relation to custodial and non-custodial wallets.
In order to understand this issue more clearly, I would like to talk about Private and Public Keys first.
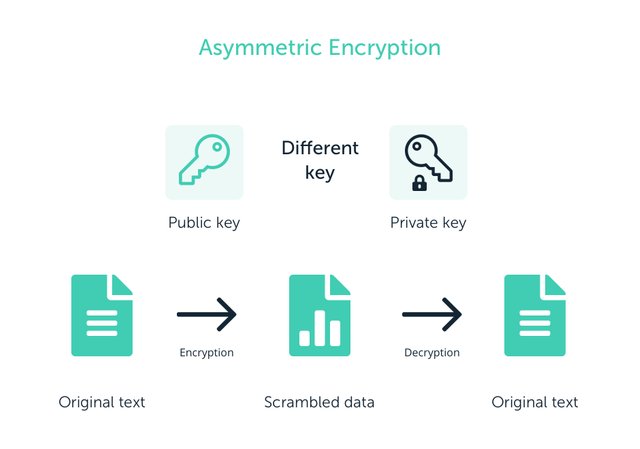
Private And Public Keys
Private and Public Keys are products of an asymmetric key encryption. We can say that asymmetric key encryption has been developed to eliminate the shortcomings or disadvantages of symmetric key encryption (Single key encryption method) and it is performed with the use of a pair of keys.
Public Key
Our first key type, as the name suggests, is the key type that we can easily share and make public, and it is called Public Key. When we want to send the coins to a wallet, we can easily encrypt this transaction with the Public key and share it with others. Because these keys only serve for encryption, not for decryption. As his professor said in his lecture, this key only serves to lock the coins, they are not used to unlock the coins.
Private Key
Our second key, Private Key, is the key among these keys. Because these keys are private keys and they are the keys that allow us to sign our transactions, show that we own the property rights, and they are keys that should not be shared with anyone. This type of key can be considered a kind of decryptor or unlocker, and anyone with access to this key can unlock your coins. That's why we shouldn't share this key with anyone and we must make sure we keep it safe.
Now that we fully understand what Public and Private Keys are, we can now move on to Custodial and Non-Custodial Wallets.
Custodial and Non-Custodial Wallets
If we make the distinction of Custodial and Non-Custodial Wallets in the simplest way, we can make the use of Private Key as ours and belongs to people or organizations other than us.
Custodial Wallet
In this type of wallet, Private Key control does not belong to us alone. In short, they are wallets where we do not have full control over our wallet and our key, which should be private to us, is managed by someone else or another organization. If we give an example of these wallets from real life, we can say that we entrust our money to banks. Banks have the authority to process or use their users' money until the users demand it back. This means that the control of our money does not actually belong to us 100%. Likewise, to give an example in the crypto world, our accounts on centralized exchanges will be the best example. We can use our assets on centralized exchanges as we wish, or we can transfer them from one exchange to another or to a decentralized wallet on an exchange. However, the issue that escapes attention is that the private keys of these wallets belong to the central exchanges. They have the same rights over our money in centralized exchanges, just like a bank's method on our money. Therefore, there is always risk in such wallets. Our assets can suddenly disappear when the stock market or bank is hacked or declared bankrupt. Therefore, such wallets are always risky.
Non-Custodial Wallet
As we can understand from the definition we made at the beginning, such wallets are wallets where we have all the control and the Private Key is only found in the wallet owner. For this reason, the only risk that these wallets face is the loss or seizure of the Private Key. As long as we keep our private key securely, we eliminate all risks to our assets.

Question 2
What do you think about the Proof of Keys Day? What precautions would you take when participating?
Proof of Keys Day
The day that first started to be celebrated as the 10th anniversary of Bitcoin's first Block (Genesis Block) on January 3, 2019 is called Proof of Keys Day and is celebrated on January 3 every year. But nowadays this day does not only include the creation of the Genesis Block. After a while, this day was also called A Crypto Bank Run as a day when almost all investors withdraw their funds from Centralized exchanges and transfer them to decentralized wallets.
As a result, Proof of Keys Day has become a very important day for investors and centralized exchanges. Because in this way, investors both confirm whether their funds are secure and test whether many centralized exchanges really have enough funds. In this way, the white sheep and black sheep emerge and it can be understood which exchange is reliable or not.
Precautions to be Taken on Proof of Key Day
First of all, it is very important in which decentralized wallet we keep our assets. Because a decentralized wallet with a low security level is no different from centralized exchanges.
Secondly, we need to pay attention to ensure that we fully ensure the security of our keys. Because today, hungry wolves will be waiting for you and at the slightest mistake they will make you their bait.
Thirdly, we should pay attention to our wallet addresses. Because we may be pulling our assets from more than one blockchain from one or more exchanges, we must be careful with the wallet addresses and the blockchain network we use. Also, we should not forget that this day is a special day. Assuming that everyone is processing many transactions at the same time, we should be prepared for a possible congestion in blockchain networks.

Question 3
Do you prefer Centralized exchanges or Decentralized wallets for storing your cryptocurrencies? Why?
I can say unequivocally that the only address I will use to store my assets is decentralized wallets. Because centralized exchanges are constantly at risk and are automatically at risk in our funds. For this reason, it is more logical to keep only our capital, which we will trade, in central exchanges. Because the usage rights of our funds in centralized exchanges are in the exchanges before us, so even when there is no risk of attack, the managers of the exchange can hijack our assets.
Decentralized wallets are always better because we are the only ones in control of our assets in these wallets and our assets are not at risk unless we make a mistake.
Traders trading cryptocurrencies should always trade with amounts they can lose as capital. For this reason, since your capital is the amount you will lose, we can keep our trading capital in central exchanges. But of course it would be wise to use trusted exchanges. However, it would be better to always keep our assets, which we consider as an investment, in a decentralized wallet.

Question 4
Let us assume it is Proof of Keys Day:
a.)Transfer at least 20 Steem from your Binance wallet to your Steemit wallet.
b.) Transfer at least 50 TRX from your Binance wallet to your TronLink wallet.
(Provide Screenshots and make sure you have your Keys).
a.)Transfer at least 20 Steem from your Binance wallet to your Steemit wallet.
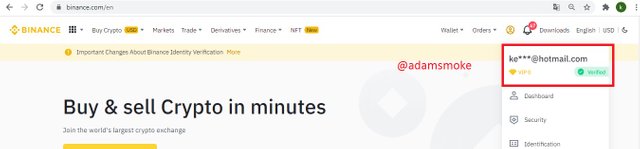
- First, we go to the Binance platform. We then log into our verified Binance account.
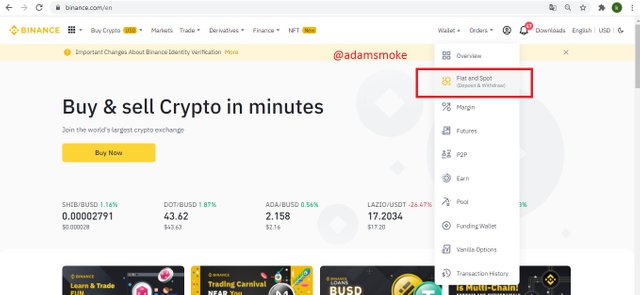
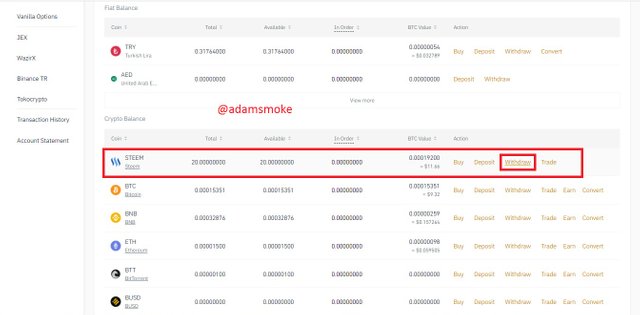
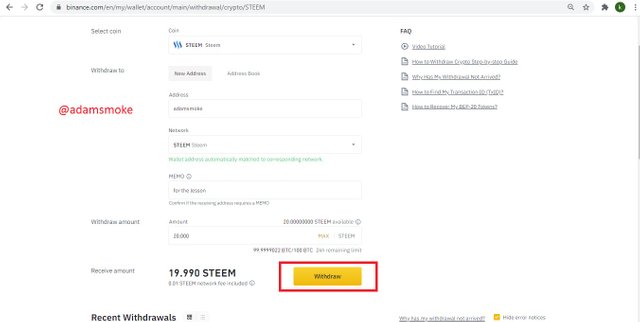
- Then we come to the Wallet section and click on the “Spot wallet” button. In the section that appears, we find Steem and click on the "Withdrawal" option.
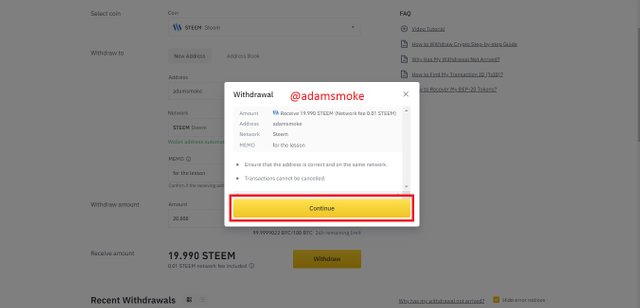
- Then on the screen that appears, we fill in the network, adress and memo sections correctly and press the withdraw button.
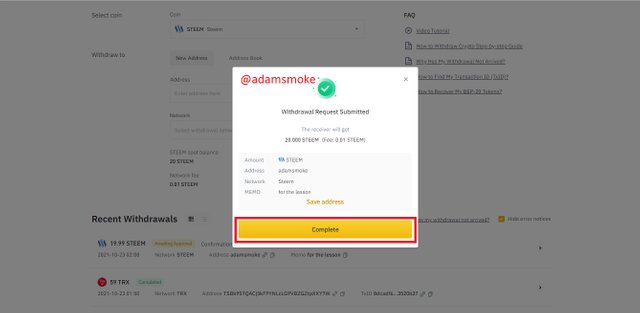
- After giving the necessary approvals, our transaction is successful.
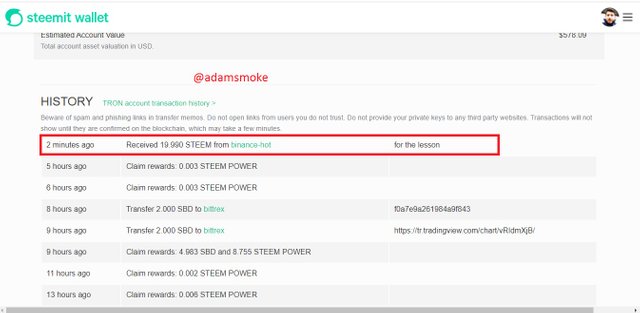
- Then we check our Steem wallet to make sure that the amount of Steem is in our account.
b.) Transfer at least 50 TRX from your Binance wallet to your TronLink wallet.(Provide Screenshots and make sure you have your Keys).
- We go back to the Binance platform and log in to our verified account.
- Then we click on Spot Wallet section and find TRX and click on the withdrawal button.
- Then we enter the network, address and amount information. Let's make sure we enter the correct information.
- Then we click the Withdrawal button and give the necessary approvals. After that, our process is successful.
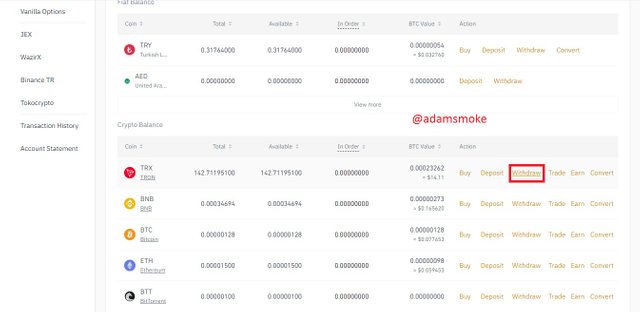
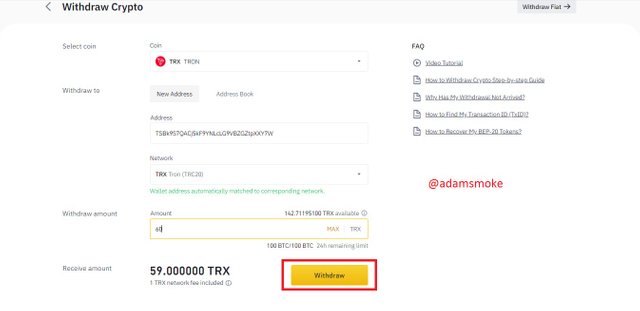
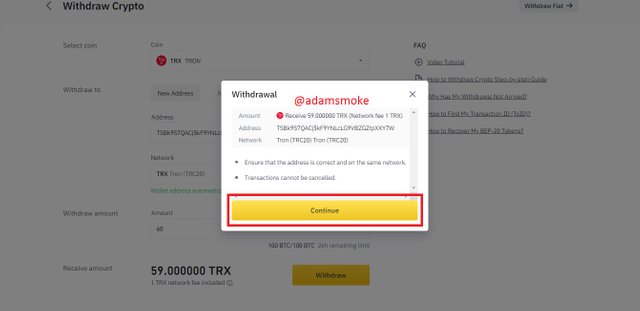
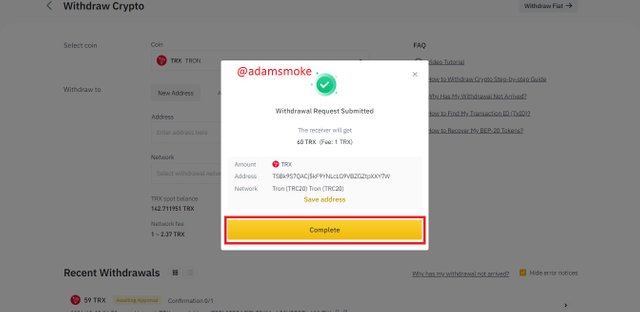
Screenshots not specified in this section are taken by me from Binance and Steemit.

Question 5
In one statement, what is the major significance of the transfers in question 4.
By performing these transfers, I have proven that I have full control of my funds and that I am the sole owner of my assets.
Of course, considering we're on Proof of Keys Day

Conclusion
In this lesson, we learned once again what asymmetric encryption keys do and why they are important. In addition, we have practiced how to control our wallets and how to use them effectively. Above all, it was a very enjoyable and instructive lesson. Thank you professor @awesononso for this nice lesson and everyone who read my post. I wish you all a healthy and beautiful day.
CC: @awesononso


Hello @adamsmoke,
Thank you for taking interest in this class. Your grades are as follows:
Feedback and Suggestions
Your paragraph arrangement can be improved a bit.
Your answer in question 3 needs work in expression and clarity.
Thanks again as we anticipate your participation in the next class.