Homework post for @pelon53 || Hash Cryptography Etherscan tronscan by @abu78
Greetings to all and sundry, it is my pleasure to be here once again to write and submit my homework post for this week's task assigned by prof @pelon53. I would like to say a very big thank you to prof @pelon53 for lecturing on such a wonderful topic for this week. The lesson was simply taught and understandable to a beginner in cryptocurrencies. Without much ado, I would like to commence with the task assigned.

Hash
Hash is a cryptography function that aids users in generating codes in an alphanumeric code format from a summarised given data. Hash converts given data into sensitive 64 alphanumeric character codes after the summarized data is being produced. In doing so, the data becomes secured and safe as well as unique for the user. Hashes can be simply defined in the following sentences;
Hash codes are not reversible and also cannot be regenerated for other data.
Hashes contain 64 unique characters case-sensitive codes
Hashes consume much time to develop from the MD2 to SHA-256.
Hashes provide a secured environment for its users by securing the data.
Uses of Hashes
- Hashes are used in generating crypto addresses and wallets.
- They are also used in mining cryptocurrencies.
Cryptography
Cryptography is the process of securing a given data by protecting and securing the data from the world. It aids users by securing their transactions performed within the platform. Cryptography is in three types and below are the types.
- Symmetric cryptography: This is the type of cryptography that involves only a one-key.
- Asymmetric cryptography: this type of cryptography involves two keys. i.e. Public key and private key cryptography.
- Hybrid cryptography: this type involves the use of both symmetric and asymmetric cryptography.
Question 1:-
Explain what does the resistance to Collision mean and what does the resistance to Preimage mean?
Resistance to Collision
Resistance to collision is the property of the hash technology which is in a picture format when Rabin in 1978 discovered it. Resistance to collision property implies that when there exists a difficulty in finding two inputs for the same output, then this implies that a collision property in a hash function exists.
For instance, considering two inputs i.e. M and N, the hash function would be H(M) and H(N) respectively. The two hash functions would exhibit a hash collision property when the two hashes are not equal to any value of the inputs M, and N.
Collision of resistance property aids in securing data from hackers.
Resistance to Preimage
Resistance to preimage is a property of the hash technology which aids in suppressing and protecting preimage attacks on a hash. Preimage attack is the attack of fraudsters on a hash code with the main purpose of acquiring a unique hash code of a secured hash data. Hash data are supposed to be secured from the preimage attacks of fraudsters which helps to improve the user-friendly environment.
There are two types of preimage resistance and they are;
- Preimage resistance
- Second preimage resistance
Preimage Resistance
This property helps in securing data that is very difficult in finding information from the hash code, an example is taking B as input and D as output and taking both the hash and input as the same. This property would imply that H(B) and D are the same but it is very difficult to attack and decode them. H(B)=D.
This property of hash states that it is very difficult in finding out two inputs for the same output regardless of any means or method used. An example is considering the two inputs as C and V where C is not equal to V, then this property states that there would be no output of Z.
Question 2:-
Use tronscan and etherscan to verify the hash of the last block and the hash of that transaction. Screenshots are required for checking.
I would be demonstrating the process of verifying the hash of blocks and that of transactions using tronscan and etherscan below;
- Visit the tronscan website by searching on google. tronscan.org
- It portrays two options is Latest blocks and Latest transactions as indicated below.
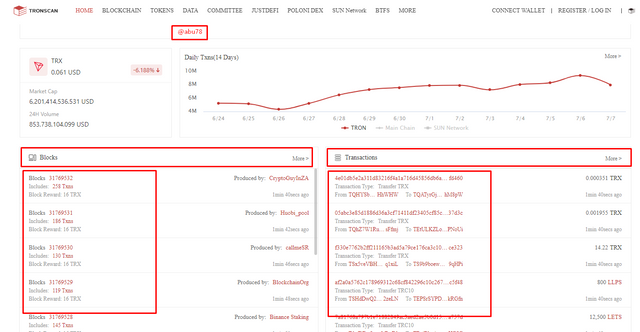
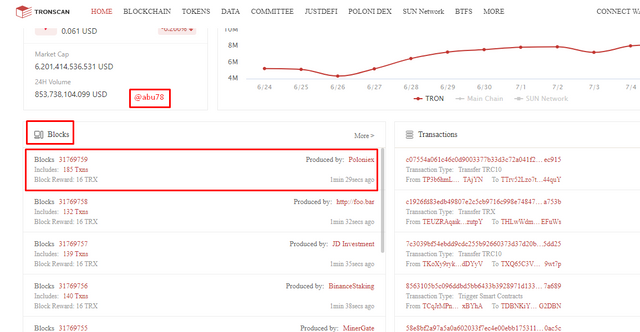
- I then clicked on the first block from the latest blocks list as shown below to access the details of the block.
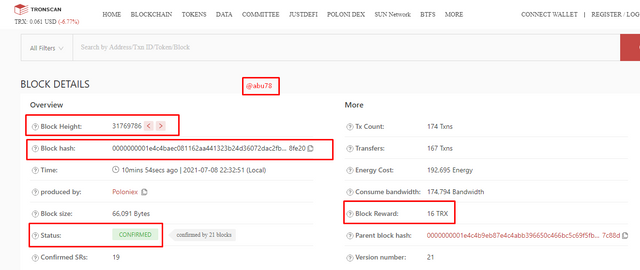
- Block Height: 31769786
- Block Hash: 0000000001e4c4baec081162aa441323b24d36072dac2fb1c2b72c5af9a8fe20
- Block Rewards: 16 TRX
- Status: Confirmed
- Then I clicked on transactions to have access to a numerous list of transactions and then select a single transaction to view details of that transaction.
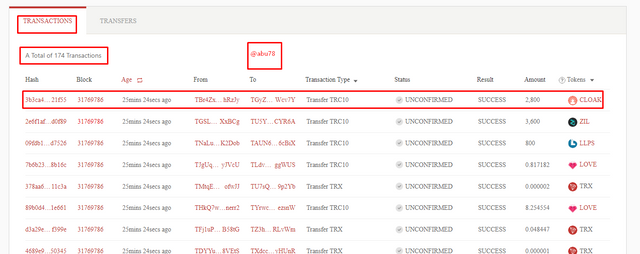
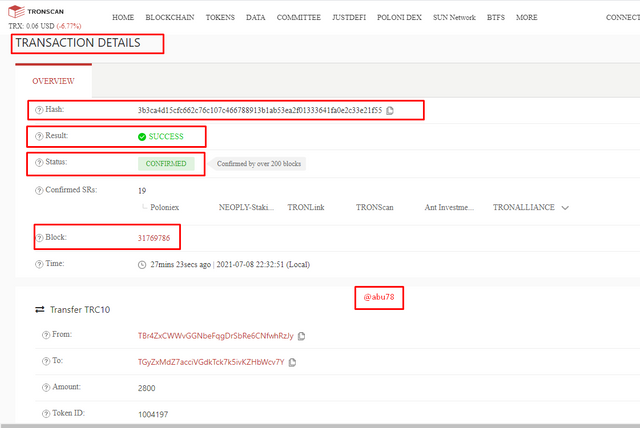
Hash code: 3b3ca4d15cfc662c76c107c466788913b1ab53ea2f01333641fa0e2c33e21f55
Block: 31769786
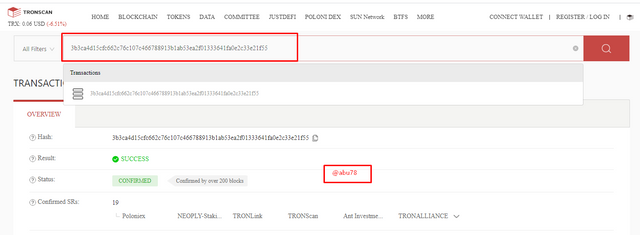
- I copied the transaction hash and searched for it from the search bar just to confirm it and it was the same as before.
Etherscan
- Visit the etherscan website by searching on google. etherscan.org
- It portrays two options that are Latest blocks and Latest transactions just as in the case of the tronscan.
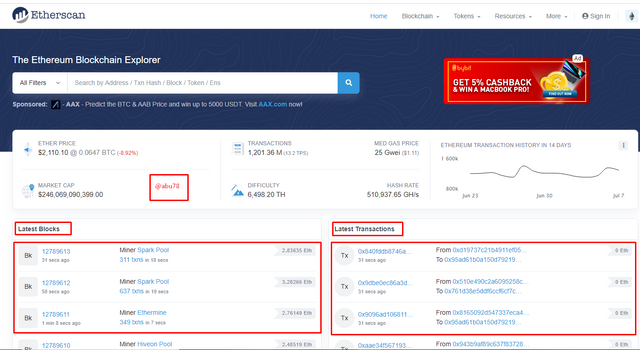
- I then clicked on one of the latest blocks to view its details.
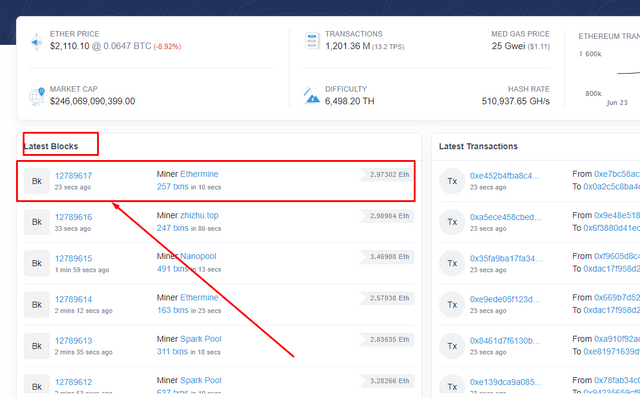
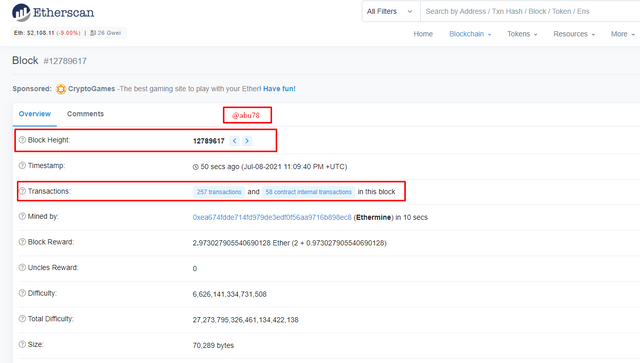
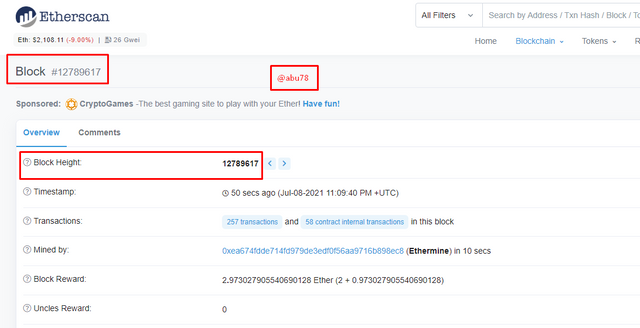
- Block Height: 12789617
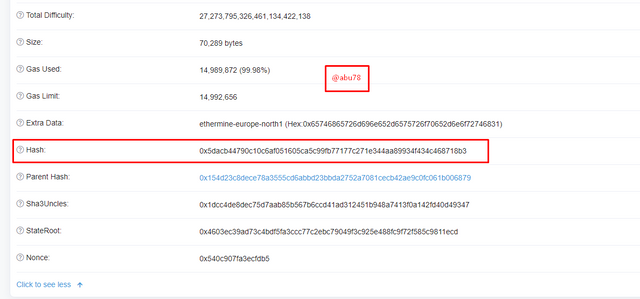
- Block Hash: 0x5dacb44790c10c6af051605ca5c99fb77177c271e344aa89934f434c468718b3
- Block Rewards: 2.973027905540690128 Ether
- I then clicked on 257 transactions to view the transactions list then selects one transaction and then view the details of it.
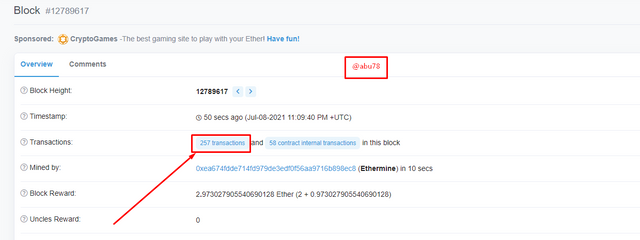
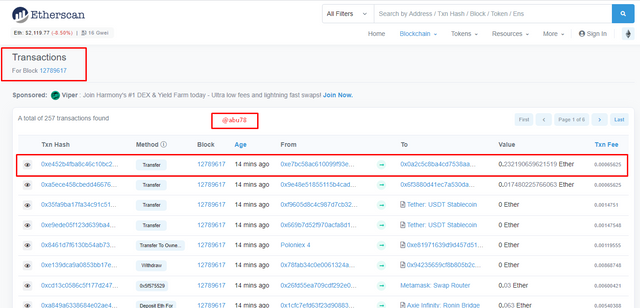
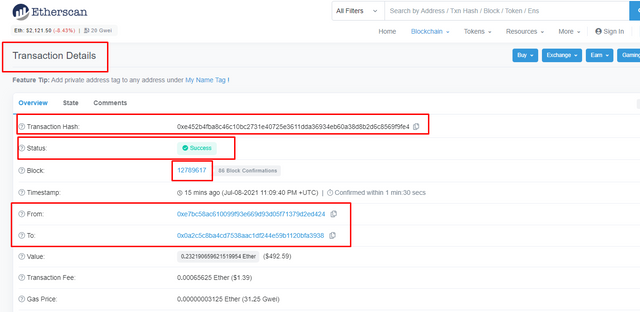
- Block: 12789617
- Transaction Hash: 0xe452b4fba8c46c10bc2731e40725e3611dda36934eb60a38d8b2d6c8569f9fe4
- Status: Success
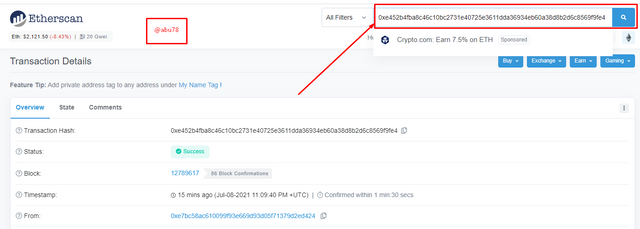
I confirmed my transaction details by copying the hash code and searching it from the search bar and it was confirmed.
Question 3 :-
Generate a HASH using SHA-256, From the word CryptoAcademy and from cryptoacademy. Screenshot required. Do you see any difference between the two words? Explain.
The steps below would help guide us on how to generate a Hash code for two given words using SHA-256.
- First I visited the SHA-256 website by searching from google. SHA-256 website.
- I then entered my first data as (CryptoAcademy) and then generated the hash code for that.
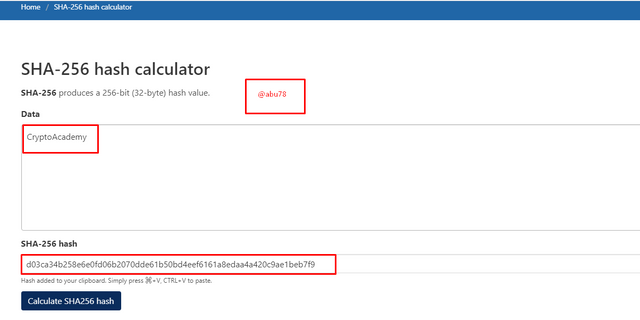
Hash code generated: d03ca34b258e6e0fd06b2070dde61b50bd4eef6161a8edaa4a420c9ae1beb7f9
- Next I entered the data as (cryptoacademy), i.e. in small cases, and then clicked on calculate SHA256 hash.
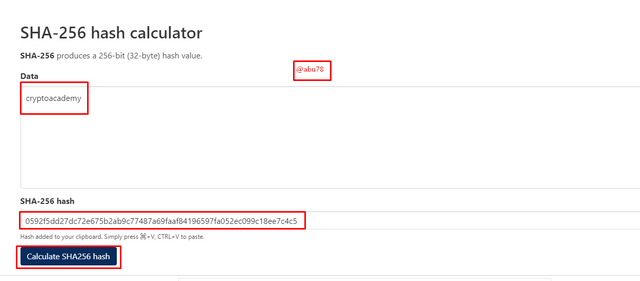
Hash code generated: 0592f5dd27dc72e675b2ab9c77487a69faaf84196597fa052ec099c18ee7c4c5
I have generated the hash codes for the two words and we can now explain the difference between them. The computer works in only binary language and it is the reason why the computer generates codes using specific numbers for particular commands. The difference in hash codes between the two words comes from the "a" and the "A" and the same for the "c" and "C" because those letters are very sensitive to case. If the case of both letters was to be the same then the hash code would have been similar. On the other hand, the case is different in this situation and this accounts for the different hash codes for the same word.
Question 4:-
Explain in your own words the difference between Hash and cryptography.
I would be differentiating them separately below;
Hash
Hash is the process of getting secret code for a given day input in an alphanumeric code format.
The calculation or process is easy to operate.
Hashes are more secured and it does not involve the use of keys
The alphanumeric hashes codes are not editable.
Hashes sends secured passwords from one user to another without the knowledge of the password by any third party.
They verify input data and also secure them with the use of codes.
There is no reverse hashing in a designed algorithm.
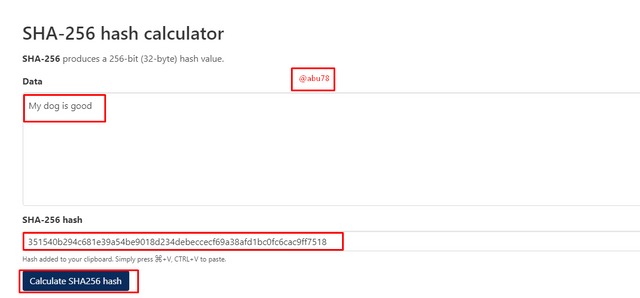
An example is illustrated below;
Input: My dog is good
Hash code: 351540b294c681e39a54be9018d234debeccecf69a38afd1bc0fc6cac9ff7518
Cryptography
Cryptography on the other hand is the process or method of encrypting information with the use of software known as cryptography. They are used in storing data.
There is the involvement of encrypting and decrypting processes.
Cryptography is purposely for securing the process of the transfer of data by giving the maximum security needed by the data.
When decryption is done the original input can be retrieved.
It contains huge information in an extensive amount.
There is the involvement of Key requirement in decryption but no key requirement for encryption.
An example is illustrated below,
Input: My dog is good
Output encryption:
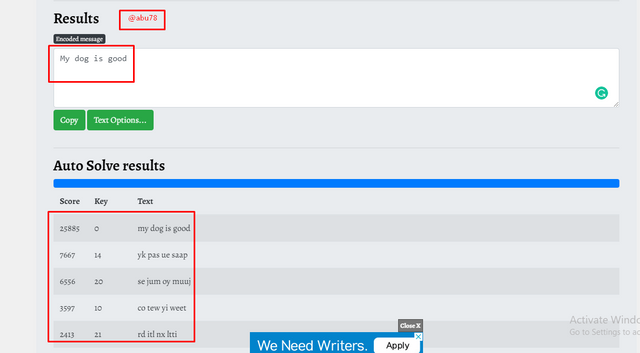
Conclusion
We discussed hash and cryptography after which we also discussed how to use the etherscan and the tronscan to see details of blocks and transaction hashes. We also discussed the properties of hash including, resistance to collision and resistance to preimage. We also watched the process of how to generate a hash code using SHA-256 hash code then we finally discussed the differences between hash and cryptography. It is my pleasure to have participated in this lesson. The lesson was easy to understand and also a neat presentation as well.
I say a very big thank you to professor @pelon53 for such a wonderful lesson taught. I wish for your convenience in your work.
Thanks to you all for reading and passing by my post
Gracias por participar en Steemit Crypto Academy Season 3:
Espero seguir leyendo tus publicaciones.
La resistencia a la colisión y resistencia a la preimagen, están explicadas de una forma confusa, no clara.
Recomendaciones:
Explicar los conceptos que se soliciten de forma sencilla y clara que cualquier peona pueda entenderlo.
Es necesario justificar el texto.
Calificación: 8.2
Hi, @abu78,
Your post has been supported by @heriadi from the Steem Greeter Team.
This is a catch-up vote for the Achievement 5.4 and Achievement 6 post
Thank you