Panama Papers hacked through PHP CMS WordPress

Panama Cards PHP CMS Hacked Through WordPress
Panama-hacks-hack
The violation of the data of Panama letters, known as The Mosek Fonseka (MF), is the biggest violation in history and contains 4.8 million emails. The Panama law company was hacked through a WordPress module called Revolution Slider. This plugin is used on more than 2 million websites because it is very popular, there are so many hacks that have the targer revolution slider
What is the Panama Papers?
The Panama Papers scandal is among the other famous public figures, with the controversy surrounding the Prime Minister of Iceland and President Putin of Russia and British Prime Minister David Cameron.
Data violation consists of 2.6 terabytes and 11.5 million documents. The #Pamma Papers database contains information about more than 200 000 offshore institutions from around the world. There were violations of email accounts, passport copies, invoices, banking documents and of course, thousands of offshore registration acts.
This document presents details about the secret business of 128 politicians around the world. More than 11 million documents show how a global industry sells secrets to politicians, fraudsters and narcotic smugglers, made up of law firms and large banks, but also sell billionaires and some celebrities.
How did this cyber attack?
The Mosek Fonseca website is running WordPress and is currently running a version of the Revolution Slider, which is weak to attack and will give a shell to the remote attacker on the web server. After checking home page source code, we realized that current MF website uses the old version of the Revolution Slider, they were using it: 2.1.7. Up to 3.0.95, all versions of Revolution Slider is weak for hacking attacks. For more details, see the image below:
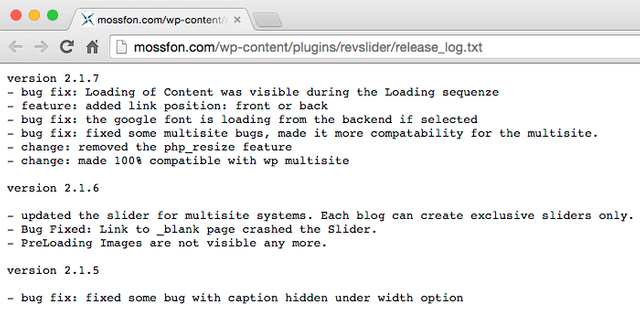
In addition, according to their DNS results, web servers and mail servers were hosted on the same machine. More importantly, they were hosting private and confidential information on their WordPress database. They were not using firewalls, and nowadays there are so many security companies.
Therefore, using a previous version of plugins, a WordPress website has heavy security risks. But I think that the Mozoss Fonseca website administrator was not thinking that something like this could happen.
Conclusion
What should everyone learn from violating this data is that:
- - You should always update your CMS (it is not important that the CMS you use, WordPress, Drupal or Joomla, it is important to be up-to-date)
- - If you host confidential data on your website, then you should use an SSL certificate and you must have firewalls and DDOS protected (there are services like cloudflayer and succession)
- - Check your website from time to time against new or changed files (if someone has changed your index or header / footer files, then it does not matter how the programming language is used, 99.9 % Opportunities are hiked)
- - Check your database from time to time (there is a database table used to store the user account, for example admin, if your website was disconnected, there are possibilities to find new administrator accounts )

img credz: pixabay.com
Nice, you got a 10.0% @ew-and-patterns upgoat, thanks to @zahidsun
It consists of $0.11 vote and $0.0 curation
Want a boost? Minnowbooster's got your back!
The @OriginalWorks bot has determined this post by @zahidsun to be original material and upvoted(1.5%) it!
To call @OriginalWorks, simply reply to any post with @originalworks or !originalworks in your message!
grt
This post has received a 18.38 % upvote from @aksdwi thanks to: @zahidsun.
great