Air-Gapped Computers – The next big hack of computers
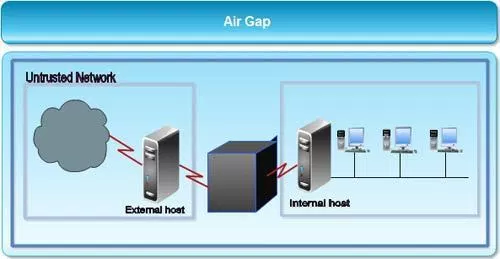
Air gapping is a security measure that involves isolating a computer or network and preventing it from establishing an external connection. An air gapped computer is physically segregated and incapable of connecting wirelessly or physically with other computers or network devices. To prevent unauthorized data extrusion through electromagnetic or electronic exploits, there is often a specified amount of space between the air gapped system and outside walls and between its wires and the wires for other technical equipment. Air-gapping is used in the military, government and financial systems like stock exchanges. The measures are also used by reporters, activists and human rights organizations working with sensitive information. Air gapping can also be used to maintain a stable software environment for sensitive application development.
Penetrating an isolated computer can be difficult but not impossible. Some of the ways to infiltrate an isolated computer are mentioned below:
Establishing a covert channel that can be used to steal information from computers in air-gapped networks by detecting the heat from one computer to a near machine.
Using GSM frequencies to extract data.
Acoustic Data Exfiltration from (Speakerless) Air-Gapped Computers
Two Israel Scientist also came up with an idea to use flatbed scanners and smart light bulbs as a relay point to control a malware infected air gapped computer
Domains where Air-gapped computers are mostly used:
- Large Enterprises (Accenture providing employees a personal laptop – Specially SAP users)
- Stock Markets (BSE)
- Government/Military (US Navy)
Isolation:
Isolating a computer requires various phases as well as a secure/filtered web gateway. Isolation is based on the concept of creating an “air-gap” between the web and users, to eliminate the possibility of threats reaching devices.
Gartner estimates that by 2021, 50% of enterprises will leverage isolation to reduce the impact of attacks, up from less than 5% in 2016.
Infecting an isolated network:
Infecting an isolated computer would also require physically affecting the network by means of social engineering techniques or phishing links.
Some of the safety measures that can be taken are:
- Secure that machine either offsite or in a safeguarded room;
- Make sure all cables to the machine are properly shielded (don’t cut corners on cables here);
- Plug unused USB slots with the USB Port Blocker;
- Turn the machine off when it is not in use (and unplug it from power);
- Replace standard drives with SSD; and
- Encrypt your data.
Congratulations @chiranjeev, you have decided to take the next big step with your first post! The Steem Network Team wishes you a great time among this awesome community.
The proven road to boost your personal success in this amazing Steem Network
Do you already know that awesome content will get great profits by following these simple steps, that have been worked out by experts?
Congratulations @chiranjeev! You received a personal award!
Click here to view your Board
Congratulations @chiranjeev! You received a personal award!
You can view your badges on your Steem Board and compare to others on the Steem Ranking
Vote for @Steemitboard as a witness to get one more award and increased upvotes!