10 Most Powerful (Known) Active Hacking Groups
There are youthful, trick programmers like Lizard Squad. Reptile Squad scandalously utilized a DDOS assault to bring down Playstation and Xbox systems amid Christmas (it's an entirely evil trick to target kids that way). A few programmers are more seasoned, and regularly fill in as "PC security specialists" who prompt organizations on the most proficient method to ensure themselves. A few programmers are in it for fiscal pick up, while others are in it for the lulz and the power.
More there are state-supported gatherings that have Hollywood-style capacities. The best known case of this is Stuxnet, an Israeli (and in addition presumably American) worm that contaminated Iran atomic offices. Stuxnet made the atomic axes go haywire while the control framework shows for those rotators would read typically. It had the ability to make an overwhelming blast while observing stations seemed typical. The scariest part is that it could be refitted effortlessly for pretty much any modern activity.
Since an infection like Stuxnet is substantially harder to pull off than a DDOS assault, the vast majority of the gatherings on this rundown are state-supported. Disclaimer: I don't have remarkable specialized learning regarding the matter, don't hesitate to evaluate in the remarks.
10 - Chaos Computer Club
Confusion Computer Club (CCC) is likely just a single of two gatherings on this rundown with any kind of good code. It likewise is presumably the most seasoned it was established by a little gathering of Germans in 1981.
Today it is an extensive relationship of generally German-talking programmers. CCC has made various hacks where they initially counseled legitimate specialists to ensure that what they were doing was lawful. In spite of the fact that they for all time dwell in or around lawful hazy area, this ability to work inside legitimate limits has permitted their survival. Have they made due, as well as they've been acknowledged, perceived, and some of the time celebrated by the press. Since it is an extensive disrupted relationship of individuals with outstanding PC security specialized information, not every person has dependably carried on as indicated by law.
CCC picked up reputation in the 80's the point at which they informed the Deutsche Bundespost of defects in their online framework. Deutsche Bundespost was to some degree a perfect focus for an early hacktivist gathering, since they effectively attempted to shield all the more mechanically propelled new businesses from contending. Deutsche Bundespost's framework supplier reacted by guaranteeing everybody that the framework was secure. Obviously, CCC still hacked the framework and stole DM 134,000. They restored the cash the following day.
9 - Bureau 121
Albeit most innovation in North Korea is greatly obsolete, their administration still has indicated enthusiasm for hacking. As indicated by deserters, military programmers live lavish lives in North Korea. Top understudies are handpicked from straight out of their "College of Automation" school. The essential wing of this hacking bunch is known as Bureau 121. It includes around 1,800 individuals that work far and wide (in light of the fact that web framework in NK is really horrible).
The majority of the Bureau's action has been centered around South Korea. Assaults have extended from pernicious gaming applications focused at South Korea, hacking the site of the South Korean President, and wrecking information of banks and broadcasting organizations. Watchmen of Peace, the gathering behind the well known Sony hack may have been a Bureau 121 intermediary. That specific hack cost Sony about $15 million.
8 - Syrian Electronic Army
The Syrian Electronic Army (SEA) is a hacker group with Syrian sympathies as well as connections to Iran and Hezbollah. They've show a wide array of attack capabilities. Most famously, they've defaced many major Western news outlets, but they have also managed to locate opposition rebels using malware. Also, if you're a fan of The Onion, you should read the Onion's response to a SEA hack.
The SEA is unique because of its varied tone and style. For example, it tweeted from AP's account that Obama had been injured in explosions at the White House. This one simple tweet sparked a dramatic temporary fall in the DOW Jones Index. On the lighter side, they've tweeted from BBC Weather that "Saudi weather station down due to head on-collision with camel". Their familiarity with English colloquialism and humor raises questions about the SEA's identity, but the NYT has stated that the SEA is probably Iranian.
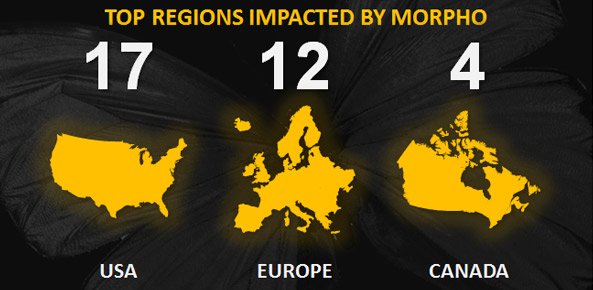
7 - Morpho
Morpho, a.k.a. Wild Neutron, is an all around financed gather that has executed many prominent hacks since 2011 on tech, pharmaceutical, and venture organizations. They're likely not state-supported in light of the fact that their hacks more often than not take insider data for fiscal pick up. They've hit Microsoft, Apple, Facebook, and Twitter by means of zero-day misuses. Since zero-day misuses are obscure to the product seller as long as they are unfamiliar, they give ground-breaking access to the programmer. This is a differentiation to something basic like a DDOS that just over-burdens server movement for a timeframe.
Morpho is especially intriguing in light of the fact that they are likely a modern little gathering. A portion of their marks incorporate multi-stage malware, all around recorded code, bitcoins to pay facilitating suppliers, and multi-organized order and control systems with scrambled virtual machines. They are English-talking and are great at covering their tracks.
6 - Anonymous
Anonymous is presumably the most conspicuous programmer gathering to in any event the American overall population. They started in 2003 on 4chan, and have become a huge power on the web. Anonymous draws some power from being amazingly decentralized, and they accordingly can keep activities running regardless of whether somebody is captured (the same number of have been). The greater part of their hacks verifiably have been of the liberal hacktivist assortment, despite the fact that others have been amazingly genuine or to a great degree carefree in nature.
A portion of their more engaged crusades have been the Occupy Movement, hostile to kid explicit entertainment, and against Church of Scientology (some of which included physical nearness and in addition a web one). Despite the fact that they have certain aggregate images, for example, Guy Fawkes covers and slogans, there is no single individual giving summons. In the event that a man turns out to be excessively narcissistic and begins, making it impossible to utilize his or her own name for things, that individual will be chastised and urged to clear out. Mysterious is a thought, and it is a thought with exceptional resilience
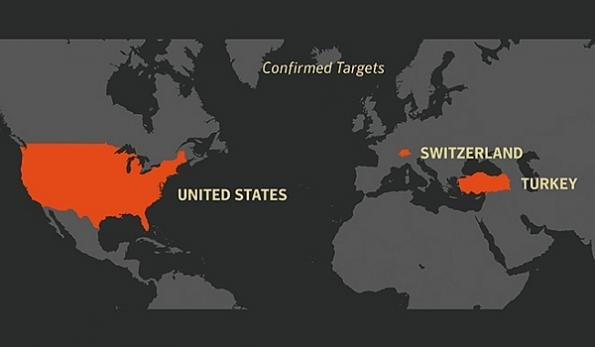
5 - Tarh Andishan/Ajax
Justifiably, Iran was not satisfied with Stuxnet. It risked the nation's atomic power (and in case you're all the more negatively slanted, additionally atomic bomb) desire. Iran chose it was best to forcefully update their digital abilities. They did this in no less than two different ways: make a free state-supported gathering, Tarh Andishan, and counsel and contract existing Iranian hackivist gatherings (like Ajax).
Ajax was better known for site destruction, however after Stuxnet it's reasonable they were counseled for enthusiastic reconnaissance (spearheaded by the Chinese). Ajax is most renowned for "Activity Saffron Rose" in which they endeavored to pick up data on U.S. guard industry authorities with cutting edge phishing assaults.
Tarh Andishan is quite minimal scarier for the normal regular citizen since they've accessed air terminal entryway control frameworks in South Korea, Saudi Arabia, and Pakistan. Such access would enable them to parody security accreditations in an air terminal. They've likewise hacked modern targets like oil, gas, and media communications organizations.
4 - Dragonfly
Another feasible state-supported gathering, this time out of Eastern Europe and Russia, is Dragonfly. Dragonfly is likely state-supported because of its objectives: electric frameworks, vitality industry, and other control frameworks in U.S. furthermore, Europe. They're assigned as an APT (Advanced Persistent Threat).
Their most regular assaults are stick phishing and watering opening assaults. This isn't surprising for APT gatherings. They've likewise exhibited capacities to implant trojans in real programming for modern control frameworks. This is extremely reminiscent Stuxnet. At the point when Stuxnet was first discovered, it was perceived to be all inclusive for some ventures. It may be that we are beginning to see Stuxnet-like worm abilities for associations other than the United States and Israel.
3 - APT28
APT28 (named by FireEye) is obviously an Advanced Persistent Threat gathering. They're Russian, and might impart financing sources to Dragonfly (in spite of the fact that I don't know so I didn't gather them together). The majority of their objectives are focuses on that the Russian government is occupied with, they communicate in Russian, and they've been followed back to an administration support in Moscow.
APT28 utilizes quite surely understood hacking strategies, and utilizations them effectively and regularly. They've hacked NATO, Polish government sites, Georgia services, and OSCE. They're exceptional in that they've been discovered encircling the Cyber Caliphate (ISIS) for their assaults. Much the same as different associations on this rundown, they work in regions with no removal settlement to the U.S. - so they are insusceptible to legitimate repercussions.
2 - Elderwood Group and 20 other Chinese APTs
Elderwood Group, Axiom, Unit 61398, Comment Crew, Putter Panda, Hidden Lynx, and some more. China spearheaded the state-supported hacking gathering, and they've kept on culminating the training. Frequently it is hard to tell whether the Chinese government is pulling the strings, financing, or even has connection with a gathering. I'm doing whatever it takes not to be foreboding, but rather the rundown of hacks and zero-day adventures of these gatherings are somewhat long.
One of the more celebrated assaults came in 2010 under the name "Activity Aurora". We to a limited extent think about Operation Aurora since Google approached and declared it had been hacked. Basic targets included resistance businesses, human rights crusades, and production network firms. Elderwood gather is a sweeping term for every one of the gatherings included. Sub-bunches incorporate Hidden Lynx (directed guard industry and Japanese clients), Linfo (producing firms), Sakurel (aviation organizations), and Vidgrab (Uyghur protesters). Such a planned, propelled, all around supported assault must be arranged by the Chinese government. It is indistinct what precautionary measures will be taken to secure against progressively modern and constant assaults later on.
On the off chance that that wasn't sufficient, the Chinese have immense troves of individual privileged insights of United States government workers.
1 - Tailored Access Operations, NSA
If not for Edward Snowden, we presumably wouldn't think about Tailored Access Operations (TAO). TAO has a portion of the best abilities on the planet, and has gathered about all the American phone information you can envision. When uncovered, an ever increasing number of points of interest have turned out about them.
We currently know they have 600 workers in the primary NSA complex in Fort Mead, Maryland. There are likewise branches in Hawaii, Georgia, Texas, and Denver. They have modern one of a kind capacities that are hard to try and devise. One of those abilities is QUANTUMSQUIRREL, which enables them to show up on the web anyplace as anybody. They've additionally traded off extremely normal PC frameworks frequently with physical access or collaboration with system or equipment organizations. They are known to drive organizations to embed vulnerabilities into their own frameworks for TAO to misuse.
Pretty much every one of the subtle elements of the association are Orwellian. Take, for instance, WARRIOR PRIDE. It's IPhone and Android programming that can turn on a telephone remotely, turn the amplifier of the telephone on and tune in, track utilizing geolocation, and its own sealing and stealth programming. That is only one that we think about.