More than just a Data Breach: a Democratic Fundraising Firm Exposure
On October 17, a member of Hacken cyber risk security team found an unprotected instance in Buffalo TeraStation NAS.
NAS (Network Attached Storage) — a portable data storage server that provides access to the client base. These devices are quite popular and are easily manageable via HTTP / HTTPS web interface. Buffalo TeraStation NASs are password-protected by default and are ‘the most secure NAS solutions’ on the market (according to the manufacturer’s site).
However, nobody can protect your digital assets if you disable authentication and, as a result, NAS web interface is indexed by Shodan or any other IoT search engine (Google in IoT world). In lay terms, a misconfiguration had happened what resulted in NAS becoming public.
Who Owns Data?
The NAS in question appeared to be managed by Rice Consulting, a Maryland-based Democratic fundraising firm. According to their site, over 2017 fundraising season Rice Consulting teamed with Democrats to raise $4.32 million.
Storage contained detailed information on each of the Rice Consulting client (past, current, and potential), e-mail databases with details on thousands of fundraisers (phones, names, emails, addresses, companies), contracts, meeting notes, desktop backups, employee details, etc.
As per Shodan search results, there are more than 700 unprotected Buffalo TeraStation NAS across the US only.
Significance of Data Breach Discovery
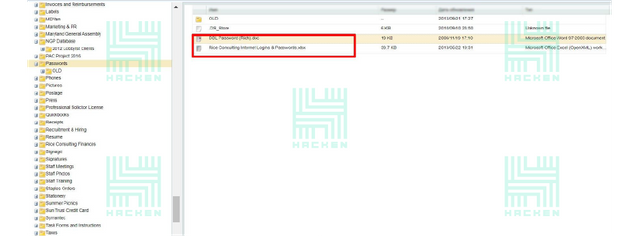
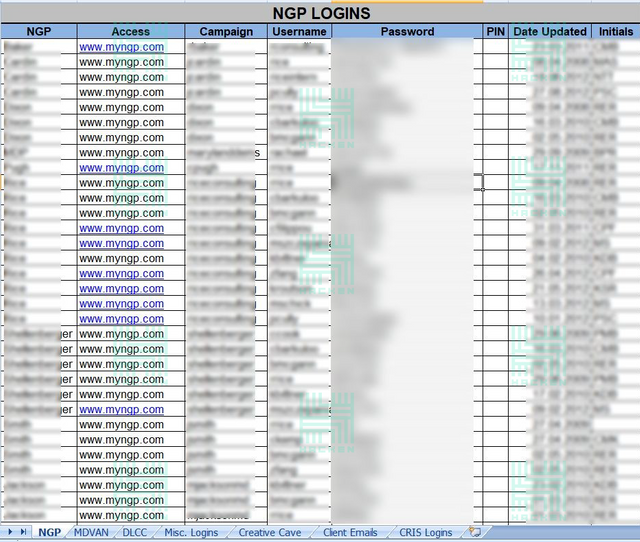
The most significant asset available for public was passwords to database resources, including access details to NGP — a privately owned voter database and web hosting service provider used by the American Democratic Party, Democratic campaigns, and other non-profit organizations authorized by the Democratic Party, MDVAN —Maryland Voter Activation Network, DLCC —Democratic Legislative Campaign Committee, and DNC — Democratic National Committee) email accounts. All of those were stored in an Excel file non-encrypted.
Access log (also available among other files in storage) shows first connections made to the NAS on February 22. It includes IPs from Turkey, South Korea, Thailand among others: scanning engines IPs, like Greynoise, are also there. We suppose that NAS information could have been accessed by non-authorized and even malicious actors.
Responsible Disclosure Issues
Immediately upon discovery, we sent email notifications directly to the Rice Consulting management team (luckily, their email was also in one of the files). However, no response was received within 24 hours, so taking into account the sensitivity of data, we called Rice Consulting office next day. A person responding to calls simply hung up.One of Twitter followers who agreed to help me reach Rice Consulting also had the same issue with communication: “The first person thought I had a marketing call and said "No thank you" and hung up. The second one acted like she was doing me a favor taking down the info”.Finally, on October 18, public access to NAS device and sensitive files has been disabled and we received a ‘thank you’ note from Rice Consulting. We will update this article if/when we receive answers to our questions.
Lessons Learned
- With so many unreliable emails floating around, sometimes it is difficult to discern what is legitimate and what is not. Nevertheless, it's not so hard to at least answer a call.
- Follow cyber hygiene rules on each and every level within your organization:
- use passwords;
- do not re-use same passwords on multiple accounts;
- constantly check your IP environment from the public internet area;
- When outsourcing your IT tasks, make sure you work with a provider you can trust. A regular independent security audit won’t hurt at all just like the services provided by Hacken specialists.