Email Spoofing with Python Tools
Greetings to all,
Email spoofing is a very old technique. It’s still widely used in the schemes Spear Phishing or Spear Apps to trick a user into believing they’re receiving an email from a specific person. That is, a user impersonates another and try to make a credible message as possible. In many processes of ethical hacking, email spoofing must be performed to verify several things. For example, a set of employees are aware and don’t fall to this kind of practice. Although, sometimes, it’s very difficult not to fall.
At the same time, you can verify the correct configuration of attenuation mechanisms as SPF (Sender Policy Framework) / SenderID, DKIM (Domain Keys Idetified Mail) or DMARC (Domain-based Message Authentication, Reporting and Conformance). The only effective solution is that all employees use digital signature systems as SMIME or PGP.
Today, I’ll talk about a couple of tools written in Python that can be used in our processes of Ethical Hacking. They show if a domain is spoofeable and could be used to send a fake email that deceives the victim.
A tool that’s really been more useful, perhaps because of its simplicity, is the SpoofCheck. This tool allows you to check a series of conditions to show whether a domain is spoofeable or not. The tool will tell you if the domain you want to replace is probably spoofeable or not.
Additionally, the SimpleEmailSpoofer tool is a script written in Python that handles connections to a local SMTP server Postfix. It carries out sending e-mail with the parameters and attributes that you indicate to the application.
Installation or download of these applications is very simple. They can be obtained directly from their Github repositories. Once you’ve downloaded both tools with the git clone command, you must install the dependencies ith the execution of the command pip install –r requirements.txt
SpoofCheck
When is a domain spoofeable?
The SpoofCheck tool handles checking a number of conditions. Here, we can see the conditions are evaluated and determine if a domain is spoofeable or not:
- Absence of SPF record or DMARC.
- The domain DNS SPF record does not specify ~ all or -all.
- The DMARC policy is set to p = none or does not exist.
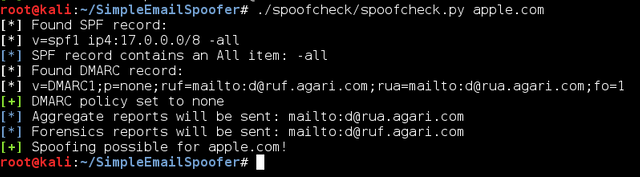
Seeing these conditions, we’ll perform some tests with known domains. In the first example, we’ll analyze apple.com. As you can see in the picture below, Apple has an SPF record enabled and with -all policy. However, although there are DMARC records, the policy is not specific, so that domain is potentially spoofeable.
Apple has improved its policy, as happened when Celebgate, the domain had the policy ~ all, made it even easier to replace.
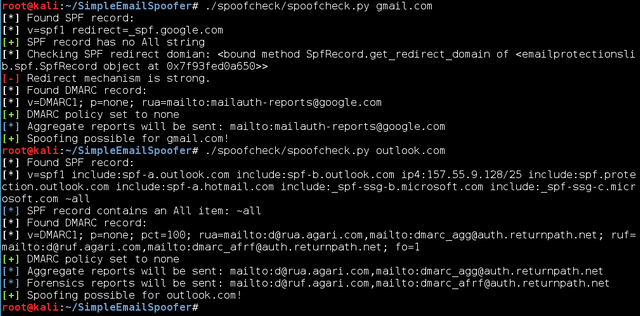
As a second example, we’ll perform an analysis of Gmail and Outlook – free email providers most used in the world. As you can see in the picture both have SPF record, where the IP addresses or domains used by authorized mail servers are included. Both have applied DMARC, but the policy is not specific. The application SpoofCheck returns that both are potentially spoofeables domains.
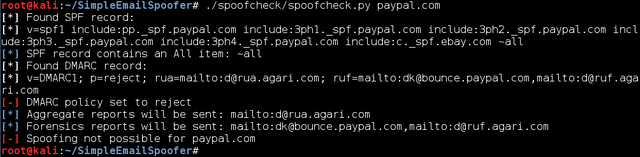
In the case of PayPal, we observe a welcome difference. It’s not spoofeable because the SPF record has a specified IP addresses, DMARC and enabled policy rejection.
Remember that PayPal has other small errors or weaknesses, such as the ability to steal accounts and user failure to register a non-real email when creating a PayPal account
SimpleEmailSpoofer
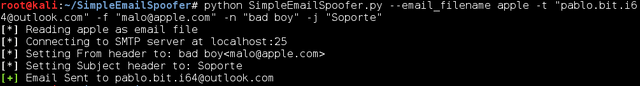
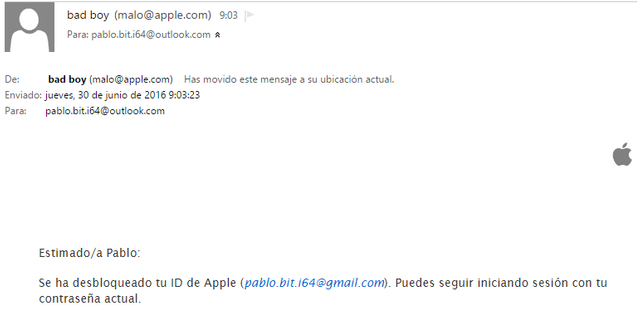
The SimpleEmailSpoofer tool is very simple to set up and run. The first thing is to have a file in which we include the HTML code body. Shown below, there’s a small example of an email from Apple. In the body, you can see the loading an image, which is the apple of Apple.
The file generated should use a number of parameters to send email. Before you can use SimpleEmailSpoofer, you need to be sure that Postfix is installed on the system. If not installed, you must run the command apt-get install postfix, and later service postfix start.
Different parameters are used to indicate the file with the body of the message, the email address to send the email, the sender address you want to spoof and name of the user who sent the email. Finally, the parameter -j allows us to indicate the subject with which the mail is sent. If we review the email that’s been set up, we see how it could easily pass for a real mail.
The above tools are useful to have in our backpack for our audits and ethical hacking. The SpoofCheck tool is especially important, as it allows us to infer if a domain is spoofeable and see whether we’ll succeed or not with the manipulation and creation of a false email on our audit.
Download Tools
Thanks for sharing a helpful post to prevent spoofing. Nowadays, email is the quickest way to use your brand name. We all know hackers can use our email addresses to steal our data, money, etc. You have shared amazing tools that will help us to avoid malicious attacks. After reading your post, I'll prefer DMARC that is an online security tool that provides you DMARC record that uses DNS to allow, do nothing, or quarantine message. It's a great tool to become more secure. I'll try the trial version first.