Nintendo Switch definitely hacked ?
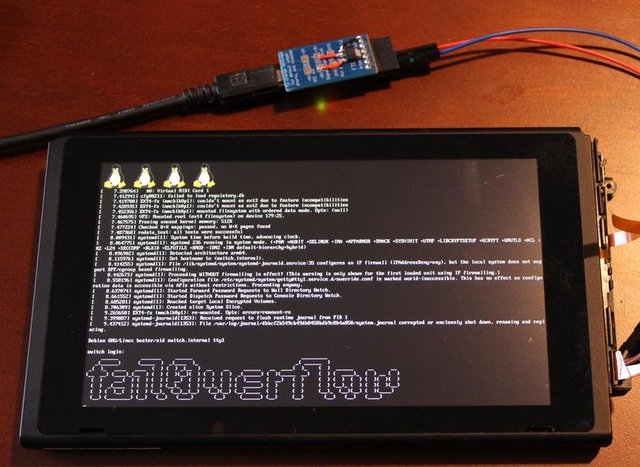
A sensational news in the summer of 2017, with websites specialized in computers and all kinds of technologies, the latest one from Nintendo would have been the price of a hacking made by the no less famous Fail0verFlow team. The press in a surge of enthusiasm and opportunity not hidden, with the sole aim of generating clicks from particularly gullible Internet users, it is advanced in a long logorrhea that would hint at the possibility of throwing unsigned iso images of games available in the market. The truth is that this is not the case. Although photos, proving the truthfulness of the team that made this exploit, circulate in the articles in question, the hack about the intrusion into the kernel of the console was only at an early stage.
A little history of things
Obviously, one could then be delighted with such an announcement, allowing us to see the possibility of developing tools and software for the machine, in favour of the homebrew scene. However, the method used must be analyzed to determine whether the hack in question can be decided. On this subject, we already have an element of answer: the question of firmware. According to the statements of Fail0verflow, firmware 3.0.0 would be more than recommended to take advantage of this intrusion. The gap being closed since the recent appearance of the firmware 3.0.1, the question arises then of the use of an outdated software. The answer is quite simple: It was an intentional by-pass, coming from Nvidia, with the sole intention of accessing the heart of the Tegra x1 chip. This action was a command from the Kyoto firm to insert code without going through the "official" channel. For example, a NES emulator has been inserted into the chip's firmware. Since then, the patch has overturned this principle and removed, at the same time, this vulnerability concern "caused" by the manufacturer...
A simple question of determination
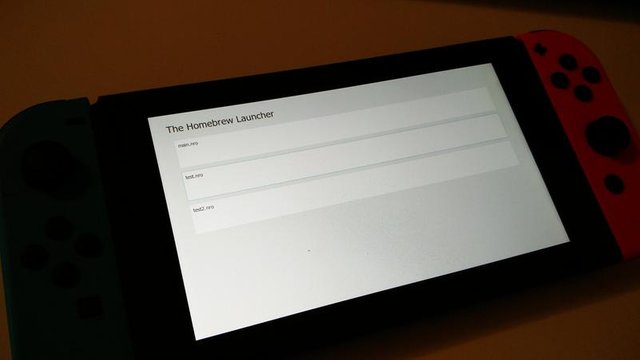
It is not without counting on the determination of the hackers, programmers and other folks who have embarked on a frantic race, in search of any backdoor... On February 6th, Fail0verflow announces an unprecedented news: The hack is operational again and would use the Rom boot of the famous Tegra X1! In other words, boot ROM, or boot memory, is an unmodifiable sequence of instructions written directly into the chip. This implies that the console's hardware has this vulnerability, without the possibility of modifying it, except to re-produce a revision of the whole! In the meantime, Xecuter, a group specializing in the exploitation and production of "pirate"chips, promises a new product for sale, capable of launching any non-proprietary code on the Switch. Certainly, Nvidia and Nintendo have a lot to worry about, given the first images of the launcher in question!
Will the switch be the new playground for crazy developers? Only the future will tell us that. However, we can see that this remains a financial blow to both manufacturers!