synthetic fraud uses faux or fraudulent INFO synthetic identity important classifiable info getting post address nurtured listed on online archivesin person
Skrevet av KIMTERJE83
What is it? synthetic fraud uses faux or fraudulent INFO synthetic identity nurtured in a person getting post address and other important classifiable info also getting your synthetic listed on online archives like white pages.(PII)how to form new credit profiles, learn how this has been done and exploited
And refined since early sixties, then called poor man’s Credit or sometimes fly by night Credit and how the mafia took over his exploits starting selling cpn numbers Reddit profile numbers This must be the earliest type synthetic identity fraud, make big business selling cpn numbers used to pump up credit scores and use them to induce product and services. Post forwarding service online can be used to make a new synthetic identity and have This as a gateway where you can collect real products and register payment gateways and services used as address starting any kind of online webshop selling any product or service.
There are several faces to the current curriculum
Make it portent following the lectures in the right order. There will be time to follow the instructions during the.lectures. , however, it started off originally as a tool to assist out anonymous individuals who is protecting the real identity ssn from identity theft. The use of a synthetic identity is the perfect way to safeguard you and your family especially children and any family member using online service without the knowledge of security and safe internet usage. synthetic identity fraud began in poor communities within the U.S. wherever individuals with terrible credit couldn’t afford to buy product and services they required. first and still it absolutely is marketed as a credit profile number (CPN). They were told they may lawfully use a CPN instead of their Social Security number (SSN) using DOB forwarding post address, opas.com also a phone number is/was also needed, sometimes even supplied by the same Criminal syndicate supplying the CPN.al the parts used together and applying for credit.
synthetic identity fraud began in poor communities within the U.S. wherever individuals with terrible credit couldn’t afford to buy product and services they required. first and still it absolutely is marketed as a credit profile number (CPN). They were told they may lawfully use a CPN instead of their Social Security number (SSN) using DOB forwarding post address, opas.com also a phone number is/was also needed, sometimes even supplied by the same Criminal syndicate supplying the CPN.al the parts used together and applying for credit.
Popularity growing Once fashionable in those areas,
When it absolutely was noticed by fly-by-night credit repair firms that began commerce CPNs and tradelines as a method for individuals to repair their credit. Well tried out and working using the method provided by the provider or salesperson, it worked and still works even modified using synthetic identities non existing online citizen with address and phone controlled by the anonymous user for safety and as identity theft prevention for all the family. Maybe a second chance for a poor family having bad credit. also, a save for abused spouses on the run or hiding from violent persons.
solely a matter of your time before organized criminal components noticed the potential. They co-opted synthetic identity fraud, refined it, Associate in Nursing brought a potency and criminal experience thereto that hadn’t been seen before. Today, an individual partaking in synthetic identity fraud should still be somebody with lousy credit making an attempt for a new chance a second chance.
during this case, they’ll use their real name with a unique SSN, address, and signaling. However, way more common are skilled crooks employing a form of ways to form cash exploiting the general weaknesses of the U.S. system. it should be a crook stealing a child’s real identity Associate in Nursing applying for a leader positive identification (EIN). Then, the crook builds a synthetic credit profile with the victim’s real name, completely different SSN, same date of birth (DOB), completely different address and different signaling. Once done, the crook uses the $64000 EIN with the synthetic profile and applies for business credit. or even the fraudster simply needs some fast money. He will build a credit profile with a faux name, fake SSN, pumps the credit score up to 760 in thirty days, then apply for private loans and walk off with profit hand. Social Security numbers are key There are several variations, however, it forever starts with the SSN. a brand new credit file should be created within the agency system to commit synthetic identity fraud which needs an SSN not antecedently in the system. however, will a fraudster simply get an SSN? They take a child’s inactive SSN and substitute a true adult’s name to use for credit. they will additionally produce a very faux SSN and a fake name to travel with it. In 2011, the Social Security Administration created making synthetic identities an entire heap easier once it randomized the issue of SSNs to combat fraud. This call to disarrange new numbers meant somebody might now not verify from the amount what year the SSN was issued or from what state. That additionally meant that fraudsters might currently use a baby’s SSN while not it being flagged as happiness to a child.
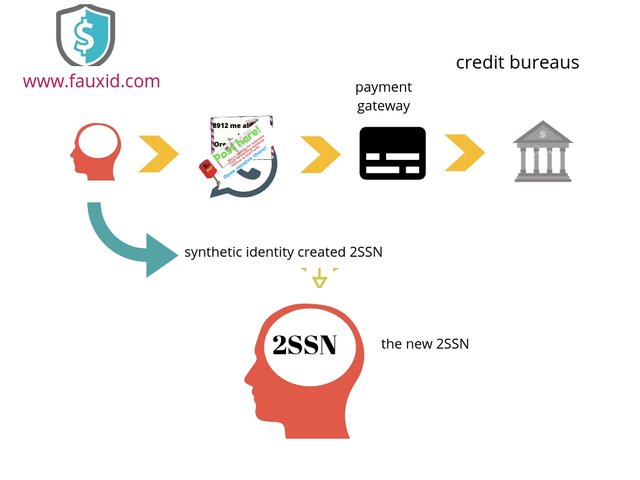
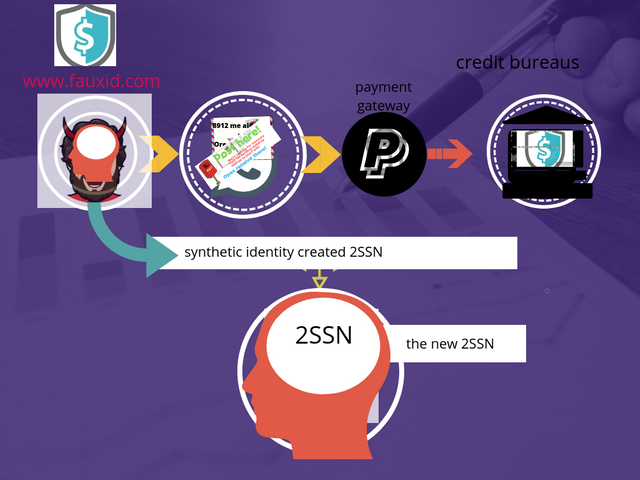
As this course us additional method consumer victimless no persons are made suffering, no one is exploited or harmed no personal loss to anyone. The additionally might produce an SSN out of void and credit and loan suppliers wouldn’t be able to tell it absolutely was a faux. As long because the SSN wasn’t already issued to a different adult, a fraudster might use it. on the far side the SSN can be obtained exploiting the ssn verifier locate a verified SSN with the right origin state and the birth Time.
synthetic fraud works by exploiting a range of alternative systems, together with the credit bureaus, open supply intelligence (OSINT) gathering, application systems, grasp your client (KYC) filters and additional.
Is typical synthetic fraud however straightforward is it to induce done? Let’s practice how this crime is usually committed therefore you’ll be able to see wherever the gaps are within the system and the way fraudsters exploit them: produce a SSN following the rules, being careful that the prefix doesn’t begin with a non-SS variety. Verify the amount through a SSN validator simply found through a Google search.
SSN has ne’er been seen by the agency system, permitting the crook to create a brand new profile at the most important credit bureaus. Add a name, DOB, address and signaling to the dishonest SSN. Apply for credit through mortgage refinancing or an auto loan – one thing that pulls the report from all 3 major U.S. credit bureaus (Experian, Equifax and TransUnion). the appliance is going to be denied, however, the process of reviewing it’ll produce a brand new credit profile in the least 3 bureaus (also called “tri-merging”) with the synthetic information. Wait 24-48 hours.
attend creditkarma.com and pull the free credit report. Security queries are going to be asked. The fraudster has the answers to those queries as a result of the created profile. If the credit report is on the market, proceed to the following step.
Manipulate OSINT to fool fraud hindrance tools.
Make the information about your new available for anyone to find. Get listed on the different public archive start using listyourself.net and input the synthetic information contained in the new idvmhost.txt and the identity information is used to get the identity from a text file and validated by the online website and owner of a new postal address phone number all-in USA.
The profile can seem in White Pages’ directories and spam are going to be sent to the address within the synthetic profile’s name. Apply for varied rewards cards from airlines, grocery chains, and pharmacies.
contemplate building a Facebook page. If a human search for identity info mistreatment OSINT tools the synthetic identity can have a web history.
Wait seventy-two hours. attend Capital One and apply for a secured MasterCard.
A $49 deposit can provide you with a $200 credit limit. The profile is already creating cash. develop a paid revolving credit and register it within the name of the synthetic identity. Use the banking routing and account numbers to fund the secured Capital One card. The secured card provides you a primary line of credit, however, it will very little for the credit score.
Time for approved user (AU) tradelines.
In the U.S., changing into Associate in Nursing AU on someone’s MasterCard leads to the particular credit history of that card becoming the credit history of the approved user.
It’s fully legal and prices anyplace from $300 to over $3,000 per card counting on the kind of card, obtainable credit balance, age of card and debt magnitude relation.
Doing this with a synthetic profile suggests that a credit score will go from zero to the high 700s in precisely over thirty days.

Another profit is that the age of the account being employed affects the age of the synthetic identity profile,
creating the synthetic profile look older than it very is.
Once the faux profile is constructed, then apply for brand spanking new loans and credit cards. counting on however they need to proceed, they will live from $20,000 all the thanks to $200,000 during a matter of some months.
Please note that a human seldom really appear at the credit report. Instead, they depend upon automatic systems to see whether or not credit is granted to candidates. If the appliance falls among a given set of parameters, credit is granted while not a question. This reveals one in every one of the hazards of automatic provisioning of credit.
on condition that an application falls so much enough outside of these parameters will a person finally pulls the credit report. synthetic profiles are designed to forever fall among those automatic parameters: High credit score, age, Associate in Nursing ASCII text file online presence, time at address and leader, higher average regular payment, etc. It becomes without delay apparent Associate in Nursing identity is synthetic if a credit report is really examined. synthetic fraud as Gangnam practiced fraudsters loves synthetic fraud. The profits are giant, the crime is straightforward, and it’s laborious to induce caught. nobody complains as a result of the identity is either faux or belongs to a baby WHO has no reason to participate within the system. If the identity belongs to a baby, they won’t understand they’re a victim of fraud for years. the opposite victims are creditors, however, creditors sometimes don’t acknowledge it as a fraud. it’s additional like somebody WHO didn’t pay their bill and is usually classified as a foul debt. practiced fraudsters take this method to create it economically and scale it up into real gangdom. They use taken MasterCard logins to feature approved users. They use virtual and drop addresses, mail forwarding services, faux driver licenses and complicated hiding techniques to line up profiles, receive mail and live. They founded dozens or many synthetic profiles without delay and infrequently layer the profiles by adding approved users onto credit cards of aged synthetic profiles, leading to profiles with intensive credit histories. skilled fraudsters even use proxies or remote desktops to spoof informatics addresses and locations, therefore every synthetic profile seems completely different.
SYhttps://ssn2ssncpn.wordpress.com/2019/05/10/11/NTHETIC IDENTITY THE PERFECT CRIME