FORTIGATE HA AND VIRTUAL CLUSTER CONFIGURATION
FORTIGATE HA AND VIRTUAL CLUSTER CONFIGURATION
In this document we describe how to cluster two Fortigate devices and then make virtualization in this cluster with VDOMS and then making virtual cluster to load balance traffic between two deferent instances of devices.
In this scenario we use FG-300C as Fortigate firewall and cisco 3750X as switches.
In fortigates we will define to deferent VDOMs. EXRTRANET and INTRANET.
Please note to the following diagram:
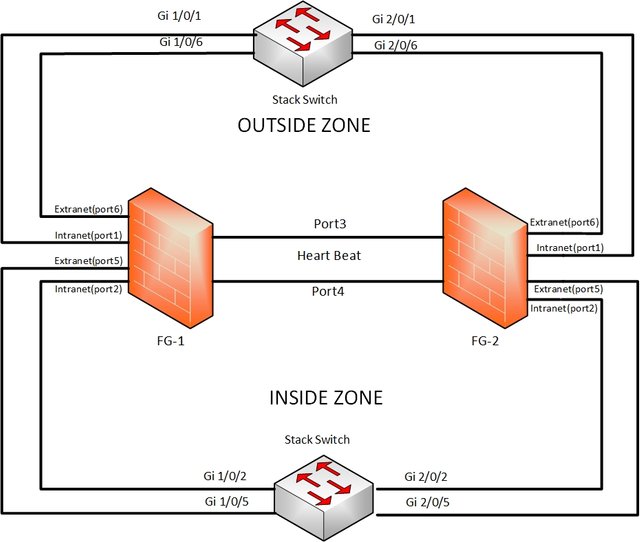
As you can see in this scenario we have a stack switch in our network. The concept of connectivity in our scenario is that interfaces in firewall 1 are connected to interfaces in Switch member 1 and so on interfaces on firewall 2 are connected to interfaces in switch member 2.
In this scenario we will use VLAN plan as follow
VLAN20 for EXTRANET-INSIDE zone.
VLAN21 for EXTRANET-OUTSIDE zone.
VLAN22 for INTRANET-INSIDE zone.
VLAN23 for INTRANET-OUTSIDE zone.
Let’s start to configuring switches:
The first step is VLAN configuration.
Now we should assign VLANs to interfaces.
!
interface GigabitEthernet1/0/5
description <<FG1- EXTRANET-INSIDE -INTERFACE>>
switchport access vlan 20
switchport mode access
end
!
interface GigabitEthernet1/0/6
description <<FG1 EXTRANET-OUTSIDE -INTERFACE>>
switchport access vlan 21
switchport mode access
end
!
interface GigabitEthernet1/0/2
description <<FG1- INTRANET-INSIDE -INTERFACE>>
switchport access vlan 22
switchport mode access
end
!
interface GigabitEthernet1/0/6
description <<FG1 INTRANET-OUTSIDE -INTERFACE>>
switchport access vlan 23
switchport mode access
end
!
And like this method we should configure interfaces for second firewall:
!
interface GigabitEthernet2/0/5
description <<FG1- EXTRANET-INSIDE -INTERFACE>>
switchport access vlan 20
switchport mode access
end
!
interface GigabitEthernet2/0/6
description <<FG1 EXTRANET-OUTSIDE -INTERFACE>>
switchport access vlan 21
switchport mode access
end
!
interface GigabitEthernet2/0/2
description <<FG1- INTRANET-INSIDE -INTERFACE>>
switchport access vlan 22
switchport mode access
end
!
interface GigabitEthernet2/0/6
description <<FG1 INTRANET-OUTSIDE -INTERFACE>>
switchport access vlan 23
switchport mode access
end
!
Now it is time to configure HA in firewalls. As you can see in following image we use default heartbeat links. (Port3 and port4). For security reasons I masked some information.
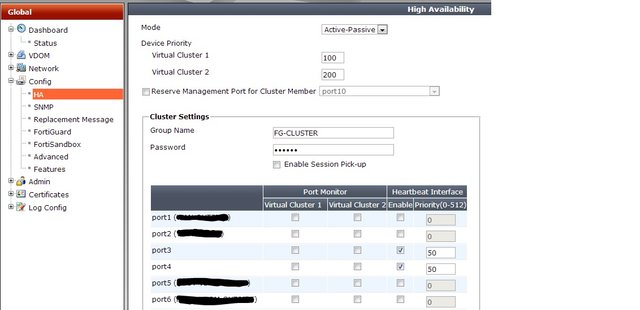
Follow these configuration on both devices:
FG-1 # config global
FG-1 (global) # config system ha
FG-1 (ha) # show
config system ha
set group-id 1
set group-name "FG-CLUSTER"
set mode a-p
set password ENC 4Lye/lPUw1UNn/O1unxY3hmO+
set vcluster2 enable
set override enable
set priority 100
config secondary-vcluster
set override enable
set priority 200
set vdom "INTRANET"
end
end
And make mirror of this configuration on 2ND device:
FG-2 #
FG-2 # config global
FG-2 (global) # config system ha
FG-2 (ha) # show
config system ha
set group-id 1
set group-name "FG-CLUSTER"
set mode a-p
set password ENC WMDvKIyun1ryvO5EPnIiuPendu7zeruS7
set vcluster2 enable
set override enable
set priority 200
config secondary-vcluster
set override enable
set priority 100
set vdom "EXTRANET"
end
end
As you can see I enable Virtual clustering in my HA. This feature help me to load balance traffics of various VDOMs in deferent cluster members.
Glad to see Iranians at Steemit :)
me too
great post...i made a special thanking post including you as special ..please check in my blog