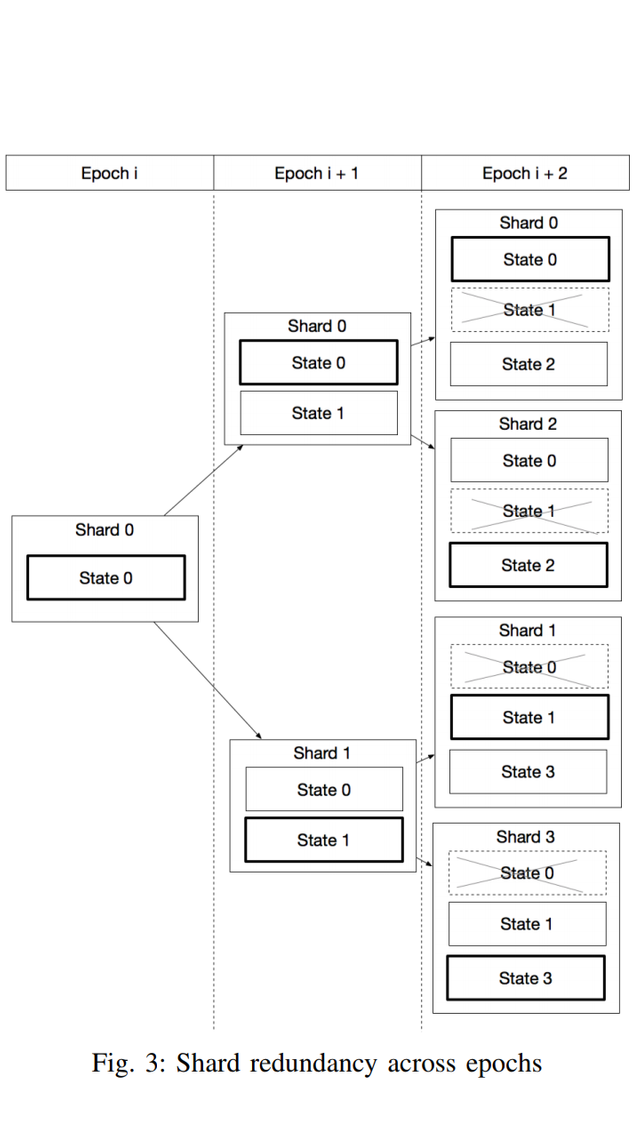
| By @Jully3722 [Lnk] After reading your other articles about elrond,my question here is what if a shard fails to come up or there are some majority of the nodes are offline, would that affect the entire system? | This in particular is resolved through a method termed Shard Redundancy (ie a part of the shards, etc., that has the same function as another shard and that exists so that the entire system, will not fail if the main part fails). A pattern of Sharding called State Sharding attributable to Blockchain is prone to failure. That is, where exist an insufficient nodes in shards online to reach consensus (ie where more than 1/3 of nodes are non-responsive). There, is possibility of high risk that the whole design depends majorly on super-full nodes that download in full every block of all shards in existence and verify everything. See as depicted in image below. Considering all of this, Elrond protocol comes with a protection mechanism that introduces a barter in the state holding structure by enforcing the shards from the last tree level to also hold the state from their siblings. By this, there is reduction in the communication flow and thus eliminating the bootstrapping when sibling shards are merging since they already have the data. |
| Question 2. Is there possibility of members of the consensus to form a malicious set and launch an attack compromising the system? And what is the way out if this happens? | This, although rare, may happen. To soften it, a system was introduced to preserve security in sharded permissionless blockchains (public blockchains) which reshuffles and reallocations active nodes between shards at a fixed time interval using a designed random criteria. This approach is termed context switching which is an improvement in the security state. As good as it is, it poses complexity in structure required to maintain consistency between multiple states. The state transition has the biggest footprint on performance since the movement of active nodes requires to resync the state, blockchain and transactions along-side the eligible nodes in the new shard. Beginning of each epoch, only less than one-third of these nodes will be uniformly re-distributed across shards. This happens to maintain liveness of nodes in Shards. And is proven to effectively form a shield against malicious formation. |
I got it right now. Actually I haven't tot of perusing the white paper. Tnk u for sharing..
I'm glad that you do. More to come. Please share with your friends.
Bob I love this. Many thanks.
Thank you Jay