Smart Home, but Secure as Well?
There can never be too many IoT gadgets -- that Is what people usually think when buying yet another connected device with advanced functionality. From our standpoint, we also believe there cannot be too many IoT investigations. So, we've continued our experiments into checking and uncovering how vulnerable they are, and followed up our study focusing on smart home devices.
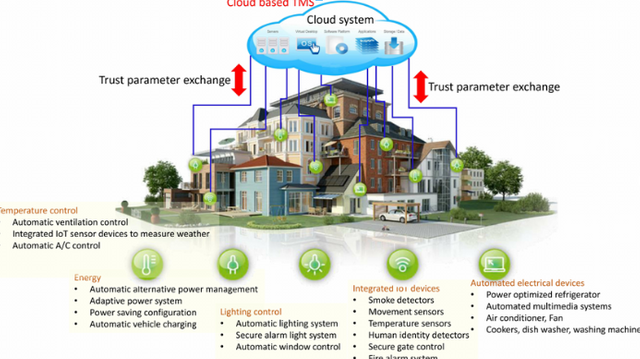
Our Latest research has once again confirmed that ‘smart home' does not mean ‘secure home'. Several logical vulnerabilities (combined with an unconsciously published serial number) can literally open doors to your home and welcome in cybercriminals. Besides this, remote access and control over your smart hub can lead to a wide assortment of sabotage actions, which could cost you via high electricity bills, a flood or, even more importantly, your mental health.
But Even if your smart hub is secure, remember that the devil is in the details: a tiny thing such as a light bulb could serve as an entry-point for hackers also, providing them with access to a local community.
Always instead use a strict and complicated one. Do not forget to update it regularly .Don't discuss serial numbers, IP addresses and other sensitive information regarding your smart devices on social networks.
No Less important is that sellers should improve and increase their security approach to make sure their devices are adequately protected and, because of this, their users. In addition to a cyber-security check, which is just as vital as analyzing other features before releasing a product, it's necessary to follow IoT cyber security standards. Kaspersky Lab has contributed into the ITU-T (International Telecommunication Union -- Telecommunication sector) Recommendation, created to help maintain the proper protection of IoT systems, such as smart cities, wearable and standalone medical devices and lots of others.
Our Latest study has once again confirmed that ‘smart home' doesn't mean ‘secure home'. Other than this, remote access and control over your smart heartbeat can lead to a wide assortment of sabotage actions, which could cost you via high electricity bills, a flood or, even more importantly, your mental health.
But Even if your smart hub is protected, never forget that the devil is in the details: a very small thing like a light bulb could function as entry-point for hackers as well, providing them with access to a local community.
That's why it's highly important for users to follow these cyber hygiene rules:
Always instead use a strict and complicated one. Don't forget to update it regularly. Be aware and always check the latest information on found IoT vulnerabilities.
No Less important is that vendors should improve and enhance their security approach to make sure their devices are adequately protected and, as a result, their users. In addition to some cyber security check, which is just as vital as analyzing other features before releasing a product, it is necessary to follow IoT cyber security standards. These programs were created to help maintain the proper security of IoT systems, including smart cities, wearable and standalone medical devices and lots of others.
An attacker breaches, interrupts or spoofs communications between two systems. Similarly, an attacker can disable vulnerable HVAC systems during a heat wave, making a catastrophic scenario for service providers with versions that are affected. Data created by unprotected wearables and smart appliances provide cyber attackers with an ample amount of targeted personal information that could potentially be exploited for fraudulent transactions and identify theft. The attacker hijacks and effectively assumes control of a device. These attacks are quite difficult to detect because the attacker does not change the basic functionality of the device. What's more, it only takes one device to possibly re-infect all smart devices in the house. For instance, an attacker who initially simplifies a thermostat can theoretically gain access to an entire system and remotely unlock a door or adjust the keypad PIN code to restrict entry. A denial-of-service assault (Do’s attack) attempts to leave a machine or network resource unavailable to the intended users by temporarily or indefinitely disrupting services of a host connected to the Internet. In the case of a distributed denial-of-service attack (DDoS), incoming traffic flooding a target originates from multiple sources, making it hard to stop the cyber offensive by simply blocking a single source. This isn't surprising, particularly as a single compromised smart sensor on a network can infect similar devices running the identical software. These infected devices are then forced to join vast botnet armies that execute crippling DDoS attacks. Permanent denial-of-service strikes (PDoS), also referred to as phlashing, and is an attack that damages the apparatus so badly that it requires replacement or reinstallation of hardware. Bots can be coded to exploit hard-coded passwords in IoT devices and cause permanent denial of service, is one such example. Another example could see fake data fed to thermostats in an attempt to cause irreparable harm via extreme overheating.
Best short answer in controlling these Issues is having a protocol that decentralizes the data to start with such as Dxchain.
Therefore, the few steps involved in generating and sending the Right requests to the server can provide remote attackers with the possibility Of downloading data to access the user's web interface accounts, which doesn't Lights or water, or, even worse, open the doors. So, one day, somebody's smart Life could be turned into a total nightmare. We reported all the information concerning the discovered vulnerabilities to the seller, which are currently being fixed.
Referral Link : https://t.me/DxChainBot?start=rk1k3n-rk1k3n
https://www.dxchain.com/
✅ @stantheman613, I gave you an upvote on your post! Please give me a follow and I will give you a follow in return and possible future votes!
Thank you in advance!
Congratulations @stantheman613! You received a personal award!
You can view your badges on your Steem Board and compare to others on the Steem Ranking
Vote for @Steemitboard as a witness to get one more award and increased upvotes!