Diro(Decentralized identity & access platform)
Diro is a Decentralized Identity & Access Management (dIAM) platform. Today’s digital world lacks a credible identity system that is universally consumable and can be trusted by counter parties across industries. Further, all crowd sourcing based solutions lack credibility and verification that is needed to address regulatory requirements. Getting, all the industries, governments and consumers across hundreds of jurisdictions to agree on a framework is a challenge. A great deal has already been written on challenges in creating universal identity (Vinay Gupta, 2017). The problem has been part technical and part political.
Owning identity itself is hard for individuals
Verifying real identities requires mass consensus and adoption
Centralized systems are unreliable in long term due security and political risks
Identities need to constantly remain validated and updated
Limitations of mass adoption by different stakeholders
As diro rapidly adopt digital technologies with smartphone penetration slated to reach 4 billion by 2022 and new technologies like IOT, blockchain, AR/VR and digital currencies getting ready for mainstream adoption, the need for cyber-security has never been greater.
The identity theft losses are reaching $16b1 annually in USA alone. The cost of KYC & AML is $15bn in the financial industry only. The latest forecast from Gartner Inc. says worldwide information security (a subset of the broader cyber security market) spending will grow 7 percent to reach $86.4 billion (USD) in 2017 and will climb to $93 billion in 2018. Global spending on cyber security will exceed $1 trillion cumulatively over the next five years, according to Cyber security Ventures.2 [Cyber crime attacks are expected to cost us $6 trillion a year by 2021. In a single year, cyber terrorism could cost us three times more than the entire U.S. housing and real estate industry is currently worth.
NB: Government and Industry are desperately looking for a solution.
“More than 100 developing countries lack functional civil registration and vital statist cs. Some countries like Malawi and Ethiopia have registration rates in the single digits. Experts estimate that there are 1.5 billion people without a legal identity. That’s the equivalent of all of China going untracked.
Governments are now holding businesses and banks responsible for AML and KYC. Europe has recently witnessed a complete overhaul of data privacy under GDPR that is going live in May 2018 putting steep penalties on breaches. All countries are likely to follow suite.
Owning Identity is hard
An average consumer is not technologically inclined. Besides having technological and cryptographic challenges, owning identity without proper safety and recovery is dangerous. Permanent loss of control or hacking can lead to severe consequences. Owning an identity today is a technological challenge for an individual as it requires:[Comment: Are the below supposed to be desired features?]
• Associating public keys with Identity — a public ledger is needed for identity lookups and making sure each identity is uniquely represented by a person. The ledger would typically contain the public key and would be located on a public blockchain.
• Modify and control identity attributes — a privately owned profile or profiles containing a list of attributes and values that can be added, modified or revoked.
• Regaining lost control of Identity — owners need to have unrestricted access and right to regain control or reset keys in case of a compromise without the need for centralized authority.
• Selective sharing of attributes — a way to share signed copies of identity attributes with third parties. The third parties should be notified when such attributes become invalid or expire.
• Collect third party claims and authorizations — a method to collect & further share third party certificates containing claims or authorizations.
Verifying identity requires mass consensus
Digital identities have had two broad concerns.
Synthetic Identities — wherein the actual person does not exist and the identity is digitally constructed.
Identity theft — where the attacker is masquerading as someone else. The digital identity is hijacked. This person may or may not be known to the real owner. In these cases, you need mass consensus or organizations to validate if the real person actually exists. These both can not be solved by biometrics. It’s often misunderstood as a means to protect against Identity theft. Unlike a password, once a biometric is compromised, it is permanent.4 The problem with biometrics on the internet is if you transmit the biometric id or its hash to third parties then the chances of permanent compromise remain extremely high.
Cyber-security can no longer be a walled garden
• Tens of specialized cloud services being consumed as technology stacks
• Multi devices including smartphones are now a norm
• Remote working and work from home is more common
• Bring your own device
• Authorization information embedded along with digital assets
• Cloud collaboration is replacing Virtual networks
Many companies with 250 or fewer employees have learned the hard way that if they wait until after being hacked to deal with it — it may be too late. Nearly half of all cyber attacks are committed against small businesses, and the percentage is expected to rise next year.
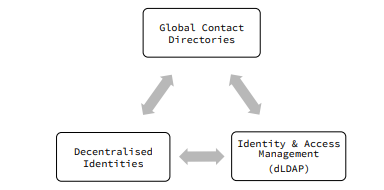
Designing — Decentralized IAM infrastructure
The world is rapidly shifting to cloud services and the demand for single-sign-on is rising. SMEs are consuming multiple cloud services across departments and the need for a shared directory of employees and maintaining frictionless secure access is felt even more. In this new paradigm, the authorization information now sits in respective cloud service providers while employees use multiple devices and roam freely. The complexity of network admission control and authorization information needs to be simplified mobile first employee directories that match the working styles of today. A very useful and broad architectural layering requirements were recently proposed as Semantic Identification Layers (Reed, Architectural Layering for Decentralized Identification, 2017).
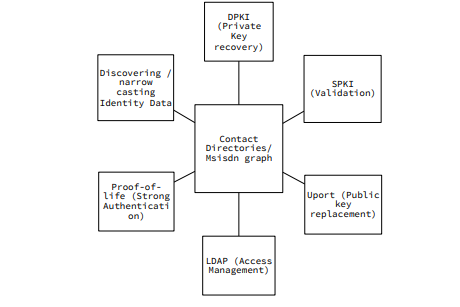
To create a dIAM — MSISDNs offer a good universal baseline to begin processing data of live identities. It can be combined with other factors like names and connections to determine unique identities. Further, existing contact lists offer a raw dump of contact information to start building graphs universally.
Global Contact Directories
(Diro platform under-the-hood)
A multi-directory platform wherein users can tag their existing contacts on smartphones into one or more directories shared in closed user groups. When a user tags an existing contact into a directory then it also tags on other phones having the same directory and also containing matching contacts automatically.
Aggregate unverified identity data (contacts)
The system allows every user to upload all their existing contacts to the platform as private directories. Many caller id apps aggregate data of users to create public databases. An average user has about 650 contacts and therefore it should be possible to get all contact data mapped within about 1% signups of the total population.
Identity attributes discovery & auto-correct
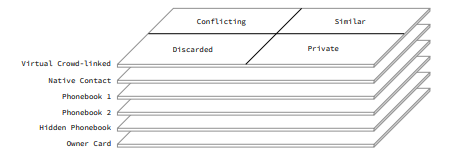
It is not necessary to make the aggregated database public and can be given to the respective owners of the MSDINs. It anonymously discovers all information matching the MSISDNs in the global database of contacts. It discovers all information related to an identity containing complete crowd data including all obsolete information to the newest data available. It helps the individual take control of the information and ability to mark all information as discarded or with most appropriate labels. (IN Patent No.
PCT/IB2017/051056, 2016)
Auto-correction — then propagates the correct labels and restricts/hides the zombie data lying in all other directories and phones of other users without sharing any additional info. This is done without actually deleting any data in other directories by simply applying appropriate labels.
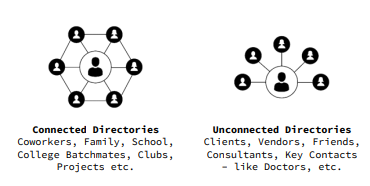
Creating shared directories
The directories that can be create are basically of two types. Connected Directories (groups) — wherein the directory is shared or made accessible to all its listed members automatically whenever they sign up. Unconnected Directories (contact lists) — wherein the directory is a private contact list only shared with specific contacts that may or may not be listed in the directory itself.
Crowd-linked contact layers
The platform virtually combines contacts based on context on different user nodes to generate virtual contact profiles across directories. A user may have multiple contacts of a person in different directories containing with different pieces of information shared. The platform virtually combines these matching contacts for a single view to the user. The linking algorithm further calculates priority and state of different labels attached to each piece of the information while respecting privacy of the contact
Using distributed database to decentralize contact directorie
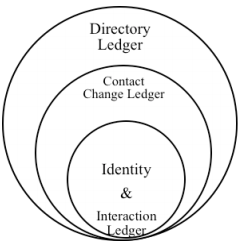
For decentralizing the directories, it is important to use record chaining using hashes to manage conflicts across devices while decentralizing the control. Further lazy consensus may be used to support offline transactions.
Directory Ledger — Contains changes to members roles, permissions for block distribution with other identities.
Contact Ledger — Changes to Identity related attributes, certificates, claims, authorizations, change log etc.
Identity Ledger — Change log of MSISDN, devices, keys, claims, certificates, invalid claims, privacy stings, profile etc.
Decentralized LDAP and Multi Factor Authentication (MFA)
Enabling contact directories as dLDAP:
Lightweight Directory Access Protocol (LDAP) version 3 is now the most widely used and accepted open standard under RFC 4510. It is adopted by over 90% fortune 500 companies (using AD). Most IAM vendors support the protocol and open source having multiple projects having production grade servers in use. The primary benefit of LDAP is the provide user directories with common authentication for organizations across different applications. Offering LDAP on contact directories reduces redundancies and eliminates provisioning workflows, admin and group management. Further LDAP servers being critical for access to all company applications pose a central point of failure. Building redundancy and backups itself is a chore that small companies avoid at the cost of data security.
Using Mobiles for password less MFA experience
A study by research firm Gartner shows that 95 percent of Web app attacks make use of stolen passwords. The LDAP system may further redirect the authentication to mobile with simple confirmation. The mobile notification may be configured to further require signing with private key and manual user acceptance to validate a login request on cloud services. OpenID Connect for exchanging identity information SSO is important but needs to bridge across SSOs. OpenID Connect (OIDC) (OpenID Foundation, 2017) is a simple identity layer built on top of the OAuth 2.0 protocol, which allows clients to verify the identity of an end user based on the authentication performed by an authorization server or identity provider (IdP), as well as to obtain basic profile information about the end user in an interoperable and REST-like manner. This could easily be added on top of dLDAP. OpenID Connect is increasingly the common authentication protocol. When an app prompts you to authenticate using your Facebook or Google+ credentials, the app is probably using OpenID Connect. It is easier to integrate than SAML, and it can work with a wider variety of apps. LDAP and MFA are protocols that can be implemented on top of contact directories using mobile devices as mobile authenticators. The contact directories can act as Virtual Directories and user store for other LDAP based authentication and authorization.
Using cryptography and blockchain to decentralize Identity
Federated Identity and entitlement is a key part of distributed architecture. As the world is gradually moving towards ambient computing, the physical world will seamlessly merge with the digital world to create next-gen UX based on augmented reality, virtual reality & IoT devices. Trustless identities are needed for security & context for enabling this next gen digital engagement & smart contracts (Active Contacts- dApps). Further, universally reliable identities provide accountability in the digital world while making regulatory oversight possible. By having accountability across the ecosystem through reliable identities, Diro solves multiple issues like theft, corruption, tax evasion or fraud.
By definition a digital identity is
“a globally unique identity ; non-synthetic ; singularly representing a living person; having irrevocable ownership ; and control over one such identifier.”
a) a globally unique identity;
- Must not change and associated with a public set of keys.
b) non-synthetic;
Should be globally unique based on social graphs and human confirmation.
Impossible to create without daily human interactions.
c) singularly representing a living person;
The identity must be used regularly.
Must not be ghost used and have live human confirmation.
d) having irrevocable ownership;
Impossible to loose ownership or access.
Possible to regain control of identity in all circumstances.
e) and control over one such identifier.
recycle /revoke public keys or devices.
Needs to be almost unhackable and even then recoverable
Digital Identity has three aspects:
Proof of global unique identity8
Consensus driven latent identities
Social contacts grid based on consensus
Non-duplicate and global
Proof of aliveness
Continuous chain of social interaction
Human confirmation (through deep interaction like audio / video)
Fault tolerance
Manage identity theft/attack using consensus of social interaction
Key management and recovery
Managing decentralized consensus between nodes
Further decentralizing the identities has four key challenges
Managing and securing the Keys
Changing the Public Key in case of compromise
Safely recovering the Private key when lost
Validating and authenticating the identity
3.Validating if the identity is not synthetic
4.Validating if the digital identity is being used by the right person
Public blockchain
Contains immutable decentralized Identity data replicated across n nodes with public keys. A DID is maintained for every Identity created based on the MSISDN. (W3C community group, 2017)
Private blockchain
Contains encrypted backup of all digitally signed blocks generated on mobile devices having distribution permissions. It’s the sync layer between multiple Identity linked devices for distribution of blocks or JSONs that may contain smart contracts.
Transaction layer
The nodes may also be identity hubs containing Identity data. Each node can generate blocks that are then independently verified by other nodes based on the distribution of the block. The multiple verifying nodes may together revoke the public key of the originating device if a block is found to be malicious or a device is found to be compromised. The master key is directly sharded and encrypted at the local device with PGP key of other trusted devices. Can use Shamir’s secret sharing (SSS) or threshold signatures to generate and later combine the shards of master key
Validating authentic digital identity owner with proof-of-life
Smartphones offer a unique opportunity in validating identities using live social interactions. These live human voice and video interaction give us a passive way to eliminate synthetic identities and defend against Sybil attacks. An identity trust score can be easily built for privilege access using such human validations that are more secure than any biometric systems. When users have a live conversation with other members in their social groups and across different groups it generates proof-of-real person owning the device and thus acts as a real bridge between physical and digital identities.
Authentication levels
User identified with one-time password
User authenticated with social fingerprint using directories
User previously confirmed by having live conversations
User transaction confirmed by subsequent live conversations
Any private and public key changes or retrievals could be limited to Level 4 authentication. These authentications would ideally be done on a smartphone dialer app that supports live conversations with other devices to obtain a mesh of such confirmations from them. The confirmations could be explicit or implicit. The implicit confirmations may be based on length of the conversation using voice or video. The user, on sign up, may select a list of individuals to validate his/her own identity based on interactions. On specific interactions, the trusted members would then digitally sign the device as authentic for a short period. The user may then declare authorization level before signing transactions based on collected signatures and share with trusted devices. In case of incorrect declaration, the trusted devices could revoke the signing key of the user.
Conclusion
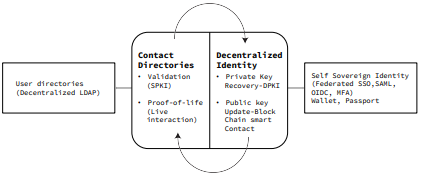
Contact directories offer a rapid method to validate digital identities using SPKI to do social KYC. It further offers a possibility of strong identity authentication through live interactions with human confirmations over voice and video calls. Voice and video conversations offer a continuous stream of strong authentication to digital identities. Further, a decentralized identity platform requires a safe public & private key management and recovery process to make owning identities possible. The DPKI and uPort based architectures also require social proof for key management and recovery.
Therefore, social KYC is a critical factor for authentication across different aspects of creating a decentralized identity structure including key management, identifying non synthetic identities and generating proof-of-life authentication from other devices.
Contact directories based on MSDINs open up a new realm of decentralized identity and access management infrastructure across multiple domains like web, apps, blockchain, AR/VR & all other industries as user directories for context and security (LDAP). Crowd sourced contact data containing MSDINs offer a rapid source of building a universal decentralized identity system that is a holy grail for delivering public benefits.
Scaling trust with block chain
Identity and security for establishing trust are critical building blocks on blockchain. Contact directories or social graphs are a central component in decentralizing the identity and access management. Without using social confirmation building a reliable decentralized identity and security architecture is not possible.
for more information on this project, check out the link below
Website: http://www.diro.io/
Witepaper: https://docs.wixstatic.com/ugd/fae167_26798553a540495d9c8189932e9c088f.pdf
Ann Thread: https://bitcointalk.org/index.php?topic=3266144.msg34032664#msg34032664
facebook: https://www.facebook.com/DiroBlockchain
Twitter: https://twitter.com/DiroLabs
Reddit: http://www.reddit.com/r/dirolabs
Telegram: https://t.me/DiroToken
BitcoinTalk profile: https://bitcointalk.org/index.php?action=profile;u=2205745