Avoid Detection Using Proxychains
Hi Computer Security Enthusiasts,In this tutorial, I’m going to explain how to stay anonymous and keep your internet traffic private. Before starting, you know that every hacker needs to hide his tracks. We need to make it difficult for system administrators, investigators and others to track our moves or to spy on us. I believe we have the right to uncensored communication.
What are Proxychains?
A proxychain is a tool that combines many proxies to assure a higher levels of anonymity.
If you are using Kali Linux distribution, just type locate proxychains in your terminal:
root@Ghost:~# locate proxychains
/etc/proxychains.conf
/root/.config/google-chrome/Default/Local Storage/http_proxychains.sourceforge.net_0.localstorage
/root/.config/google-chrome/Default/Local Storage/http_proxychains.sourceforge.net_0.localstorage-journal
etc…
As you can see, proxychains are built in Kali linux and we can use the command from any
directory (simply because it’s in the /usr/bin directory.)
To use proxychains, for example, to anonymously scan a website, just type:
root@ghost:~# proxychains nmap sS <IP address>
Proxychains Configuration
If you want to configure your proxychains, you need to open the configuration file /etc/proxychains.conf using a text editor like Vim or leafpad etc…
root@ghost:~# vi /etc/proxychains.conf
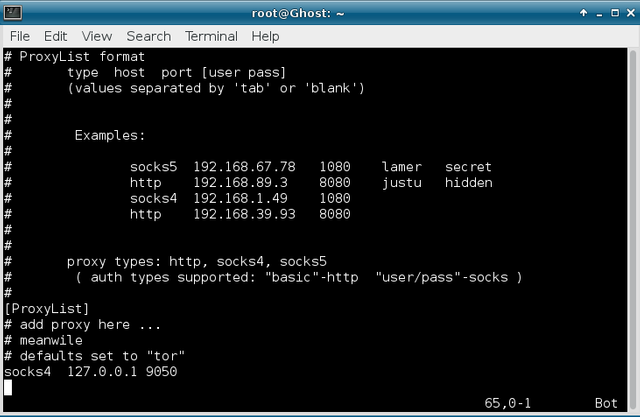
To add IP addresses for new proxies, you just need to replace “ #add proxy here… “ by your IP address list. As you can see, proxychains use the default Tor configuration 127.0.0.1 on port 9050. So, if you’re using it, leave it (else comment that line).