DeepOnion and TOR network, an excellent combination.
DeepOnion has many interesting details to offer us, and among them is its security and anonymity, something to highlight is the native use of TOR networks increasing the privacy by reducing the possibility of hacking or intervention of any entity in our transactions.
If you are an experienced user, you will already have an idea of what I’m talking about, but if you are someone new and you still can’t understand the meaning of the TOR network, I will explain it in this article.
The primary use of the TOR network is to remain anonymous in the network, whose data that is sent through this network are encrypted from point to point so that no intermediate entity can obtain access to the data.
In the same way, the IP address is modified similarly to other private data, so that it would be extremely difficult to find the origin of the data.
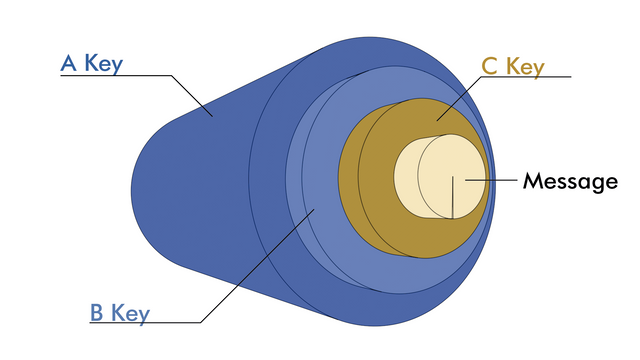
This is achieved by using a technique called Onion Routing, calculating a random path to its destination, passing through several intermediate nodes until public keys are obtained using a directory of nodes.
This method uses an asymmetric encryption, encrypting the data by layers (like an onion) the first thing that is done is to encrypt the message with the public key of the last node of the route, so that only can decipher it. Besides the message, it includes (also encrypted) instructions to reach the destination.
This whole package, together with the instructions to reach the last node of the list, is encrypted again so that it can only be deciphered by the second last node of the route.
The package sent is in the center, protected by several layers of encryption for each of the nodes.
This process is repeated until all the nodes of the route are finished, we will have the data package ready to be sent.
The sender connects to the first node of the router and sends the packet to it. This node will decrypt it to follow the instructions it has deciphered to send the rest of the packet to the next node. This new node will decrypt again and re-send the packet to the next node and so on until the data reaches the exit node that will send the data to its destination.
To avoid that the data sent is intercepted, the nodes of the TOR connection are changed every 10 minutes, choosing new nodes randomly.
In this way, much more security and privacy is provided in each of the transactions, no one knows where the information we send comes from or where it goes. The message is encapsulated in many encrypted layers.
This is one of the qualities that DeepOnion has to profile as one of the safest and most anonymous coins that exist, being practically impossible to be hacked or intercepted, so if you want security in your transactions this is one of the best alternatives there is.