History Of TOR ("The Onion Router")
The "TOR" network (The Onion Router) sits at the heart of the new "DeepOnion" "crypto" offering, allowing users to transact with others anonymously. Whilst the system has been created to facilitate private transactions, there are wider implications in the realms of virtual private networks and similar setups.
The most important thing you need to understand is that if you're looking at the "crypto" market from the perspective of trying to profit from the price of the various "coins" that are available, you'll have to come to grips with the potential for TOR's growth and its application in the "crypto" space.
The other thing you need to realize is that TOR has often been associated with what's known as the "Dark Web" - an area of the Internet which has been designed to evade the majority of investigation and public access. Whilst the Dark Web is entirely legal, many of its uses have been illegal, most notably the "silk road" marketplace, which ended up being closed by the US federal government. Due to TOR's association with this system, it has long been seen as an "illegal" entity, despite receiving the majority of its funding from the US government.
Ultimately, when considering whether "DeepOnion" can provide effective "crypto" management, you're really looking at whether its integration with the TOR network, and relative privacy technology, would be able to provide users with the ability to create effective transactions without their details being shown publicly. This tutorial is going to examine the way in which "TOR" plays an important role in the new "DeepOnion" coin.
TOR was established in 2002 to provide users with the ability to anonymously access web-based services through a layered "virtual private network". The main benefit to TOR was that it would route traffic through a huge network of random systems - allowing for an "onion" router that would obscure the majority of data that each connection would provide . The system was actually developed in the mid-1990s by United States Naval Research Laboratory employees, mathematician Paul Syverson, and computer scientists Michael G. Reed and David Goldschla. They were tasked with creating a system which would protect US naval traffic on the Internet.
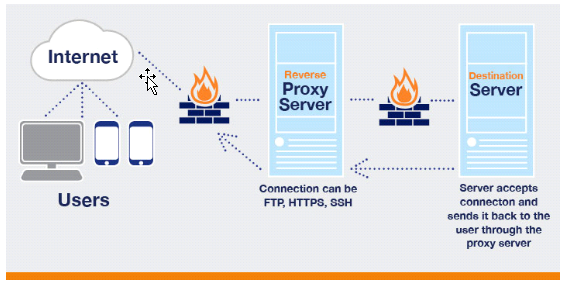
Beyond the obvious reasons of wanting to maintain security for US Navy personell & their employer's intentions, the system also had another purpose in that it would give anyone the ability to access information online through a globally accessible "proxy" network (VPN) which would basically remove any trace of their identity from searches etc. To understand how it works on a fundamental level - every time you "browse" the Internet, what you're really doing is using your computer to access new IP addresses. These IP addresses belong to servers, each of which have public Internet connections.
Any time that you use your computer access said server, what's happening is a "request" is being sent to the server with your IP address attached to it. This is then handled by the server and a "response" is generated in the form of an HTML document. This document is then shown by your web browser.
The problem for many people is that either their government has blocked a particular website, or maybe they don't want their information tracked online. To this, you're able to use what's known as a "VPN" (Virtual Private Network) (often termed "proxy") to act as an intermediary system through which you're able to access websites without having your own digital footprint at risk.
This is important, as it basically how TOR works (except TOR adds several extra "layers" -- hence the name) to the mix. After the test in the mid 90's, it wasn't until 2002 that the "TOR" project was released as a public entity. During this time, it underwent a number of developments - with the Naval Research Laboratory eventually releasing its code entirely open source.
The second version of TOR was introduced in 2006, with a project funded by the EEF (Electronic Frontier Foundation) providing the majority of funding, along with a number of commercial partners. After this time, the US government took to funding the project directly, and thus is responsible for the massive growth of the network and its relatively high adoption on a global basis (the US government funding allowed the team to extend the network's reach and effectiveness).
Despite a number of board changes, the system is still primarily funded by the US government, and has been used by the likes of the NSA to conduct intelligence gathering operations.
Hope you liked the article, Please feel free to leave your comments below, Thanks!