Can DeepOnion be Hacked?
A lot of people have been asking the question about whether a privacy based cryptocurrency like DeepOnion, that puts so much emphasis on anonymity and privacy can be subject to being hacked. We are going to attempt to find out, but first we need to understand what DeepOnion is and how it was developed. DeepOnion is a new form of cryptocurrency that has put the privacy of its users before anything else. It works a lot like other cryptocurrencies except it has a little more to offer. DeepOnion’s most important feature is how it is linked with the Tor network, which hides the user’s IP address so when they send and receive transactions they are provided with clear safeguards against revealing the identities of the traders by decrypting the IP locations.
Firstly DeepOnion is 100% anonymous and no one can identify where you are located and therefore no one can monitor your activity or financial transactions. The Tor network offers a high level of protection on your connection, making impossible for anyone to surveil and monitor your virtual life.
But does having total anonymity and privacy protect you from cyber attacks and hacks? Hacking is the unauthorised intrusion into a computer or network and there are many different methods that can be used to gain access to a computer or network. Firstly, there is the obvious method of password cracking, which by all accounts is the process of recovering passwords from the data stored or transmitted by computer systems. The next method is one that is known as packet sniffing, in which applications are used to capture data packets in order to view data and passwords in transit over networks. This method is particularly common amongst the hacking community, and is relatively easy to carry out.

Another common way for hackers to gain access to a computer system or network, is to use spoofing attacks. This involves websites that falsify data by mimicking actual websites, and are often treated as legitimate websites by unsuspecting targets. In addition to spoofing attacks, something called a Root Kit might often be used as a way to gain entry. It represents a set of programs which work to subvert control of an operating system from legitimate operators, and this is also a common way for people to gain entry to a system.
Probably the most well known way for a hacker to gain entry to a computer or network is via a computer virus. These viruses are self-replicating programs that spread by inserting copies of itself into other executable code files or documents.
Although attempting to hack DeepOnion would by no means be an easy thing to do, But there is clear evidence that with the right leverage and the right combination of software, there is every possible way that a hacker could gain entry to DeepOnion. Just by social engineering alone, someone could manipulate an unsuspecting victim to willingly give their private keys to a person they have never met pretending to be from DeepOnion. So not all ‘hacking’ is down with viruses, malware and clever typing. The real issue is dealing with the social engineering and how to find a way to make sure people don’t fall victims to this style of hacking.
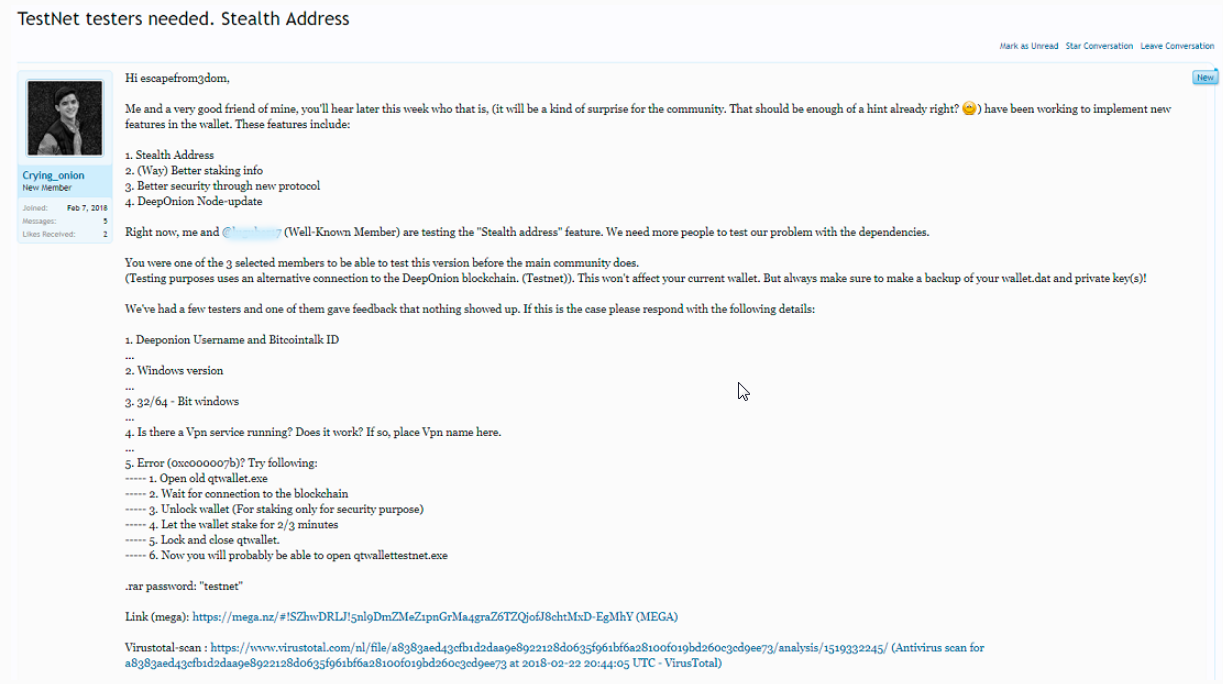
I'm not done yet, take a look at the recent post from Impressive, this is what I'm talking about!
Here is the link to the actual thread in DeepOnion Community.
So stay safe, and going forward, be more cautious with such PM's and while logging into Desktop wallets.
Hope you liked the article, Please feel free to leave your comments below, Thank you!
Images Courtesy: DeepOnion Community