Your Guide to Secure Software Development Practices, Products & Projects
![]()
![]()
Credit: Atif Arshad, The Noun Project
January 9, 2018
Secure code is critical to the software industry, every organization on the internet and anyone who leads a digital life.
This explains why we started publishing the BugHeist Beacon, an e-newsletter dedicated to secure software development practices and products, privacy initiatives that help safeguard your data and security software and cybersecurity events.
Secure code also motivated Sean Auriti to launch BugHeist https://www.bugheist.com in July 2016 after he grew frustrated with companies that failed to fix the software bugs weeks or months after he identified and shared these flaws with them.
BugHeist helps organizations sponsor BugHeist Bug Hunts that award cash to individuals who find and share software and hardware vulnerabilities on their websites. They range from software security issues, such as cross-site scripting and expired SSL certificates, to design and performance issues.
“Think Your Apps are Secure in the Cloud?” https://www.ibm.com/developerworks/library/se-think-apps-are-secure/index.html explains why Sean chose the Django software framework for BugHeist. Written for IBM’s software developer community, the post also shares tips on how developers can amp up their application security development skills.
Have a story idea, concern or comment? Please contact us at [email protected].
Thank you for joining us and best regards!
Sean & Tara
—————————————————————————————————————————
Secure Software Developer Tools
Sean chose Django as the foundation for BugHeist because the software framework features embedded code that protects data from common hacking problems, like cross-site request forgery (CSRF), cross-site scripting (XSS), SQL injection, click-jacking, insecure SSL and HTTPS protocols and unprotected header validation.
Here are other software frameworks and platforms designed to help developers create secure code. (Full Disclosure: Sean and Tara have no known financial stake in any of these products. Really smart people shared these with us or we used and/or found them through the internet.)
CA Technologies/Veracode
The company’s cloud-based secure web application development https://www.veracode.com/solutions/by-need/secure-development offering scans and monitors your code for vulnerabilities in the pre-production and production stages of development.
It implements Static Application Security Testing (SAST), web application discovery and monitoring, Dynamic Application Security Testing (DAST), behavioral analysis and penetration testing to scan your code for problems.
The company also prioritizes your risk by cross-referencing your flaws with the OWASP Top 10-2017, a compilation of the most common and critical software vulnerabilities and recommended solutions to remediate them, CWE/SANS Top 25 and PCI compliance mandates.
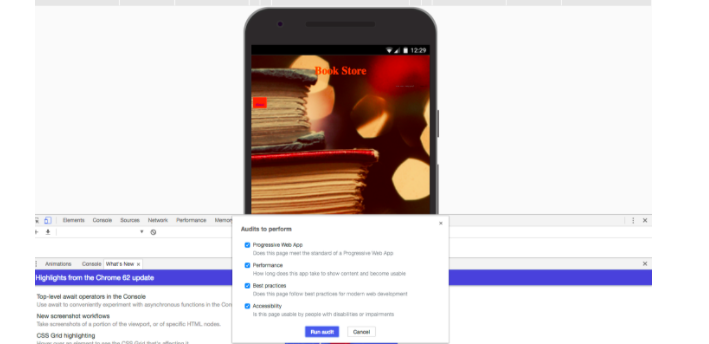
Google Chrome
As a front-end web developer who is on the eternal quest to perfect her code, Tara uses Google’s Chrome Developer tool to audit her software for errors, level of responsiveness on various devices, performance issues and insecure HTTPS connections.
Insomnia
Insomnia https://support.insomnia.rest/article/11-getting-started is a cross-platform application that enables developers to install HTTP authentication standards, including Basic, NTLM, API keys, OAuth and HAWK, in their APIs through a user-friendly interface.
Secure Code Warrior
Integrated with Micro Focus Fortify’s software security testing solution, Secure Code Warrior https://new-www.securecodewarrior.com/ provides coders with on-demand vulnerability training modules aimed at showing them the sources of their issues, how to fix them and prevent future mistakes.
UK-based Micro Focus https://www.microfocus.com/about/press-room/article/2017/micro-focus-completes-merger-with-hpe-software/ completed the acquisition of HP’s Enterprise’s software division, which included the company’s Fortify portfolio of security products and services, in September 2017.
Synopsys
A “Static Application Security Leader,” according to The Forrester Wave 2017 Q4 Report, Synopsys https://news.synopsys.com/2017-12-11-Synopsys-Completes-Acquisition-of-Black-Duck-Software https://www.blackducksoftware.com/ expanded its secure coding product line when it acquired Black Duck Software for around $547 million on December 11, 2017.
Through its acquisition, the Mountain View, California-based company offers products that identify the open source code in your software environment, map it to known open source vulnerabilities, flag policy violations/track the remediation process and alert you when they detect new vulnerabilities.
Developers might be familiar with the company’s Coverty Static Analysis platform. It scans software for vulnerabilities included on the OWASP Top Ten and CWE (common weakness enumeration) List during the software development lifecycle. It also notifies developers about Payment Card Industry Data Security Standard (PCI DSS) compliance issues.
—————————————————————————————————————————
Protect Your Privacy
Our digital identities seem more realistic than our physical ones when we consider the amount of transactions and communication we conduct on our computers, laptops and mobile devices.
Our IP addresses can be traced by advertisers. Our passwords and email addresses can get hijacked by hackers. Our mobile devices use GPS chips to find our geographic location.
Do we reconcile ourselves with the fact that we have no privacy on the internet, or do we take control of our digital destinies by using encryption, two-factor authentication and other security methods?
Here is information on how we can enhance our digital safety from a few organizations.
The Electronic Frontier Foundation (EFF) https://sec.eff.org/ created the “Security Education Companion” training materials for people interested in educating others about digital security. Its “Surveillance Self-Defense Guide” explains encryption, HTTPS Everywhere, a browser plug-in “that tells websites to use encryption,” and PGP or Pretty Good Privacy encryption keys to individuals who want to secure their communications—academic researchers, activists, journalists, online security veterans—everyone.
Created by The Tactical Technology Collective, Tactical Tech’s Me and My Shadow Project https://myshadow.org/about details how mobile device users are tracked through GPS, Wi-Fi, cell towers and location logs. It also shares a menu https://myshadow.org/resources of open source tools, messaging and video applications, search engines, trackers and guides dedicated to securing your privacy.
GitHub now offers Security Alerts https://github.com/blog/2470-introducing-security-alerts-on-github that notify you when a vulnerability is detected in your Javascript and Ruby code and whether it is a publicly disclosed vulnerability listed in the National Vulnerability Database https://nvd.nist.gov/. GitHub shares recommended solutions that are available and “suggests known fixes from the GitHub community.”
The Engine Room https://www.theengineroom.org/about/ is staffed with an international team dedicated to using technology and data to “push for social change around the world.” The team created LevelUP https://level-up.cc/, a website with training modules focused on malware protection, mobile safety, data protection, safer browsing, GPG/PGP encryption and social media safety.
Through its Matchbox program https://www.theengineroom.org/matchbox-program/, the Engine Room partners with organizations to create projects focused on transparency and accountability. It helped Mexican journalists create ¿Quién Compró?, a platform that tracks the receipts of Mexican congressmen and women in an effort to bring transparency to government spending.
It has also partnered with Uganda’s Anti Corruption Coalition http://accu.or.ug/ to develop “a safe channel” where public officials can access and address corruption and transparency violations reported by citizens.
—————————————————————————————————
Software Security Events
OWASP BugHeist Bug Hunt
We are excited to announce that OWASP https://www.owasp.org/index.php/Main_Page is sponsoring the first BugHeist Bug Hunt in 2018.
Hunters who find the most bugs on OWASP’s site will win 3 Steem Power tokens.
Your Steem Power tokens build equity in the platform. They also help Steemit (further) develop a sustainable platform that rewards users and contributors who share their time, knowledge and content on the site. Depending on your level of interest in investing in Steemit, you can maintain your Steemit Power with the site or convert it into U.S. dollars.
OWASP AppSec California 2018 https://2018.appseccalifornia.org/
If you are interested in advancing your application security development skills you should know about OWASP or the Open Web Application Security Project.
OWASP is at the heart of the cybersecurity community, a population of international software security professionals, white hat hackers and pen testers who use their skills and knowledge to create open source software security initiatives for everyone.
The non-profit organizes secure software training events and conferences to help underwrite these initiatives.
We will shamelessly promote OWASP’s U.S. and European conferences because they are the main revenue generators for the OWASP Foundation.
Plus—full disclosure—Sean is the leading developer of OWASP’s Bug Logging Tool (BLT), the open source project he helped create and commercialize as BugHeist. Tara attends OWASP events because she loves software and security.
The first major OWASP conference in 2018 is OWASP AppSec California 2018 from January 28-31 at the Annenberg Community Beach House in Santa Monica, CA.
Training classes will cover:
*An Introduction to Web Hacking using OWASP’s Zap tool
*Advanced Web Hacking and Secure Coding
*OWASP’s Top Ten Exploitation and Effective Safeguards
*Open Source Defensive Security
*Running a Secure Service on AWS
Keynoters are Eric Baize, chairman, SAFECode; Dr. Christian Dameff, doctor, hacker and researcher; Richard Seiersen, Twillo’s CISO and vice president of trust, and Cory Doctorow, science fiction author, activist and journalist.
HACK NYC 2018 https://q22018.hacknyc.com/en/
Websites and mobile applications are common targets for hacking attacks.
But nuclear facilities, water treatment plants, train stations, airports and the electric grid are also susceptible to malicious activity.
Security experts from the private, governmental, non-profit and academic sectors will converge at Hack NYC 2018 to discuss the challenges with protecting these structures, along with solutions.
Scheduled from May 7-10, 2018 at Microsoft’s Technology Center at 11 Times Square in New York City, the event will include OWASP, All Day DevOps, Amazon, Intuit, NetSPI, Dragos, Whiteside Security, TrapX Security, the U.S. Department of Homeland Security, the FBI, NIST, New York University, Pace University, NJIT, Goldman Sachs, Pershing and SAFECode.
On May 9, GORUCK https://www.goruck.com/constellation/ will conduct a Custom Constellation exercise that will teach people how to survive a disaster that destroys elements that define society--government, infrastructure and civility.
With only a backpack or rucksack of supplies, attendees will learn how to navigate New York City as “survivors.”
——————————————————————————————————————————-
Sponsor a BugHeist Bug Hunt to Find the Flaws that Expose Your Data!

Contact Sean at [email protected].
Congratulations @bugheist, you have decided to take the next big step with your first post! The Steem Network Team wishes you a great time among this awesome community.
The proven road to boost your personal success in this amazing Steem Network
Do you already know that awesome content will get great profits by following these simple steps, that have been worked out by experts?