Your Guide to Secure Software Development Practices, Products & Projects
Credit: Atif Arshad, The Noun Project
March 7, 2018
Dear Steemians:
Like you, Sean and I are reading the stories about how our U.S. election data might have been accessed by the Russian government and we’re not happy about it.
Following is information about the reasons why our electronic voting machines could be compromised. We also share some possible solutions about how to secure the digital transmission of voting data and better design the voting machines themselves.
Best regards,
Sean & Tara
————————————————————————————————----------------
Electronic Voting is Insecure
What can we do to maintain the integrity of our election votes and ensure democracy stays alive?
The revelation about the Russian government accessing voters’ data in U.S. election backend systems before the 2016 U.S. presidential election scares many of us who believe voting is imperative to preserving democracy.
This assertion follows years of discussions about the software and hardware issues with U.S. voting machines from computer scientists, security professionals, security researchers, academics and U.S. election officials.
At the 2017 DEFCON conference, computer scientist and board member David Jefferson and chairperson Barbara Simons of the Verified Voting Foundation outlined the reasons why U.S. electronic voting machines are vulnerable to hacking attacks.
Why are U.S. Electronic Voting Systems So Weak?
In 2002, Congress passed the Help America Vote Act, which gave U.S. state election officials about $3 billion to replace voting machines after the Florida ballot recount controversy in the 2000 U.S. presidential election. “One of the unfortunate conclusions that a number of people reached from Florida 2000 was that paper was bad. Paper is bad. Paperless is good,” said Simons, author of Broken Ballots: Will Your Vote Count?
Election officials had a “Gold Rush” mentality with the funds, wanted the “newest and greatest shiny object” from electronic voting machine vendors who claimed their equipment was secure, federally certified, automated and eliminated the need for manual recounts, explained Simons.
These machines were badly engineered due to inadequate calibration, produced questionable testing results that were proprietary to vendors like Diebold and unavailable to election officials who wanted to verify voting machines’ security. The voter-verified paper audit trail process that was implemented to validate electronic information in some voting machines has been rarely used and challenging to read, stated Jefferson and Simons.
Add insecure proprietary software that was developed by 5 to 6 vendors who built (or contracted the building of) the electronic voting machines and wrote the software for the voting machines and the computers that tally the voting ballots and produce the final results for thousands of jurisdictions throughout the United States, you have the perfect attack vectors for nation-states and other evil actors who want to advance their or others’ agendas.
“A lot of the software in voting and canvas machines (election management computers) are commercial off the shelf stuff, mostly operating systems stuff. Some of these systems are so old, they are running Windows XP, Windows CE, some of them run Windows 2000,” said Jefferson.
“The reason that they are so old is because once they are certified, you can’t change a voting system without going through the complete recertification process, which is long, slow and expensive,” he continued.
Specific software problems include weak software update and installation processes and password and key management, cryptography and randomization. The physical ports and seals on electronic voting machines, which could be up to 15 years old, are also vulnerable.
How Can We Better Secure our Voting Data?
Simons recommended paper ballots and manual post-election paper ballot audits serve as possible solutions to address the issues with electronic voting machines. These methods are also recommended in The State and Local Election Cybersecurity Playbook, which was published in February 2018 by Harvard University’s Belfer Center for Science and International Affairs.
At an OWASP NYC chapter meeting on February 13, 2018, Andy Liverman, director of sales and marketing, DISPEL, issued his call to action for volunteers to get involved with local and state officials to address issues with U.S. elections systems. He also encouraged people to visit
donthackthevote.org, a clearinghouse for information about U.S. elections systems and security.
Liverman talked about DISPEL’s software offering for elections, which addresses the “most networked” and vulnerable areas for possible hacking attacks--the voter registration rolls and the transmission of votes from local election officials to state election officials--during a demo on February 28, 2018.
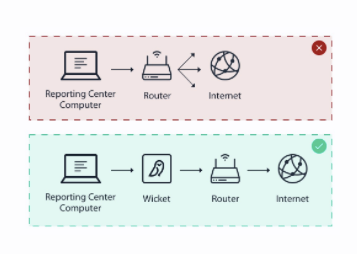
In its Handbook for Elections Infrastructure Security, the Center for Internet Security also states“...one of the largest sources of vulnerability and most common methods of attack is in the transmission of data between systems.”
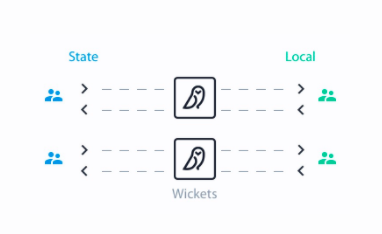
DISPEL provides users with a DISPEL Wicket, a device that “sets up a highly secure fully controlled virtual private network” between the election workers’ local computer that contains voters’ data at the local polling location and the centralized database used by the administrator, like a CIO or secretary of state. Since DISPEL’s software gets installed on the local and state computers responsible for voting registration and tabulation data and does not get installed on the voting machines themselves, it would not need to get certified by state and or federal authorities.
DISPEL Wicket. Courtesy: DISPEL
According to Liverman:
“...What’s different with DISPEL’s VPN network versus others, (is that) you fully control all the nodes in that network and you fully control all the connections. And all the nodes are new and fresh, typically daily. When you go through another VPN network, you don’t necessarily know where those servers are that are brokering that traffic. You might also be sharing that network with other individuals, and so if you are a sophisticated adversary you can start to understand what that network looks like and potentially find ways into it…. Every single day, the architecture of your network changes and shifts, which makes it incredibly difficult for someone who’s attacking you or even studying you to find out what’s going on.”
And instead of logging in to an actual computer laptop or computer connected to a network that could allow hackers into this environment, users log in to a laptop or desktop that features a virtual registration system housed in the cloud through a browser.
DISPEL’s data transmission process. Courtesy: DISPEL
Liverman continued:
“Now it makes it very difficult for an adversary to jump from the local machine to that virtual machine that’s accessed through the web browser. There is no backend process running between that virtual machine and the browser. It will only accept typed in data, like to CSV file, depending how the system is architected.”
The authorized administrator uses multi-factor authentication and log viewing to further control and secure access to the encrypted information. “It’s a much simpler system in some ways. Your whole system is just these virtual machines and your servers and all they do is take CSV files...It’s simplicity in terms of how it’s built. The complexity is in that it’s moving.”
Possible Hardware Solutions to Fix the Voting Machines
In January 2018, Galois, a computer science research and development organization, announced it will receive up to $4.5 million from DARPA “to develop tools and methodologies that enable provable security for hardware used in a broad range of business, consumer and government projects.”
“Spectre and Meltdown, the vulnerabilities found in Intel’s chips, spotlighted hardware design issues in computers,” says Sean Auriti. “When we talk about U.S. voting machines, we are talking about aging legacy equipment with microprocessors, modems and routers that could be around 10 to 15 years old. I think DARPA’s funding will help organizations like Galois develop solutions that will safeguard voting machines through better hardware and microprocessor design architecture.”
Sean also thinks blockchain technology could be used for voting at some point.
“The foundation of blockchain is transparency and accountability. With the recent developments in hardware, blockchain could use SHA 256 cryptographic hash functions to match voters’ and officials’ keys and replicate a unique chain of blocks with unique signatures that would be impossible to reverse. This process would allow anyone to trace and verify voting information.”
How Do We Pay for More Secure Voting Equipment?
In Assessing the Vulnerability State of America’s Voting Machines, author Kate Rabinowtiz stated that money needed to replace or update today’s voting systems comes from the states and counties. She also mentioned the Secure Elections Act. Submitted in late 2017 by six senators, the bill would “make $386 million in unspent HAVA (Help America Vote Act) grants available to states to replace paperless voting machines.”
————————————————————————————————
How You Can Learn about Cybersecurity
When Tara attended her first OWASP Meet-Up in New Jersey, she was clueless about cybersecurity, hacking and social engineering. Dumb, dumb, dumb.
The book she bought about front-end web development contained 5 pages on how to strip out or escape malicious code that creates cross-site scripting (XSS).
For a secure coding fan like Tara, the journey to learn how to prevent evil people from stealing social security numbers, passwords and bank account numbers has been a long and challenging one.
Penetration Testing: A Hands-On Introduction to Hacking by Georgia Weidman helped her understand IP addresses, virtualization (simulated software operating systems), Kali Linux’s operating system, shell scripts, syn scans, subnet masks, SSL, routers, ports, hubs and switches.
Cybrary’s free videos introduced her to tutorials about specific hacking topics, such as external footprinting, hash functions, HTTP recon, spoofing, session highjacking, distributed denial of service (DDOS) and steganography (hiding information in photos and videos and other types of files.)
She also subscribed to the EHT (Ethical Hacking Tutorial) Newsletter where she found a list of “legal (web)sites” on which people can practice their hacking skills.
If you are serious about becoming a cybersecurity “professional,” you might know about NYU Tandon School of Engineering’s NYU Cyber Fellows program, an online cybersecurity master’s degree program.
With a price tag of about $15,000, this initiative integrates real-world experiences from the business community and expertise from New York City agencies like New York Cyber Command (NYC3) with the academic world (NYU).
——————————————————————————————-
BugHeist Welcomes New Employee
BugHeist creator Sean Auriti is excited to welcome Sourav Badami to the BugHeist team!
As a student intern who managed 3 students at the OWASP CodeSprint 2017, Sourav helped develop the OWASP BLT project, the open-source project that served as BugHeist’s foundation. He also maintained Google’s Oppia project and contributed patches to Oppia, Dropbox’s Zulip, DuckDuckGo, OWASP and other commercial and open-source organizations.
Sourav will contribute his programming skills to BugHeist while he pursues his bachelor of engineering degree in computer science and engineering at the Haldia Institute of Technology in India.
Get a 10 percent discount off your HACKNYC General Admission ticket by using the BugHeist Beacon’s code: BUGHNYC.
——————————————————————————————————-
Sponsor a BugHeist Bug Hunt to Find the Flaws that Expose Your Data!
The leaderboard prize is $25 for anyone who reports the most bugs. Or simply report one bug!
Contact Sean at [email protected] for details.