RSA ALGORITHM CONCEPT AND EXAMPLE
Source: Skill Gurukul
Breaking News ! |
Cipher Suites: Ciphers, Algorithms and Negotiating Security Settings - Hashed Out by The SSL Store™ (blog)
Largest known prime number discovered: Why it matters - The Conversation CA
Microsoft makes play for next wave of computing with quantum computing toolkit - Ars Technica
News - Largest prime number discovered: Why that matters - The ... - The Weather Network
We need to talk about mathematical backdoors in encryption algorithms - The Register
The Register: “This is the reason why this kind of research is essentially done in R&D lab of intelligence agencies (GCHQ, NSA...) and [is designed] more for designing backdoors than detecting them.” Revelations from papers leaked by former NSA sysadmin Edward ...StealthCrypto Launches Privacy for Mobile Phones Worldwide - SYS-CON Media (press release)
SYS-CON Media (press release): DALLAS, Dec. 23, 2017 /PRNewswire/ -- Privacy and mobile phones have never been a very good combination until now. Stealth Grid has developed, tested and manufactured the first totally encrypted mobile phone in the industry and will soon launch an ICO ...and more ...Rent Stabilization Association of NYC and Rhino Announce Partnership to Bring Security Deposit Alternative to Members - SYS-CON Media (press release)
SYS-CON Media (press release): The Rent Stabilization Association of NYC and Rhino announced today a partnership to bring ... security deposit alternative to the ... 25,000 members. The RSA already provides a wide assortment of products and services to its members, ranging ...and more ...Q# Is for Quantum Computing: A New Programming Language from Microsoft - All About Circuits
'Mr. Robot' Rewind: Rewinding the '5/9' hack in a stunning season finale - GeekWire
Hackers Show Proofs of Concept to Beat Hardware-Based 2FA - Motherboard
Follow our Community for More ! |
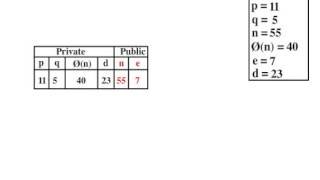
HOW THE RSA ALGORITHM WORKS, INCLUDING HOW TO SELECT D, E, N, P, Q, AND φ (PHI)
RSA ALGORITHM WITH SOLVED EXAMPLE USING EXTENDED EUCLIDEAN ALGORITHM | CSS SERIES #7

RSA ALGORITHM
THE RSA ENCRYPTION ALGORITHM (1 OF 2: COMPUTING AN EXAMPLE)

PUBLIC KEY CRYPTOGRAPHY: RSA ENCRYPTION ALGORITHM

Latest posts from our Team ! |
- BTC DEBIT CARDS DISABLED BY VISA / JAPANESE POP IDOLS / BITCONNECT TARGETED BY TEXAS / MUCH MORE
- Last Hour Price Changes: STEEM:-5.00 BTC:-3.14 ETH:-4.04 XRP:-4.17 BCH:-1.84 ADA:-3.63 LTC:-2.75 XEM:-2.48 XLM:-2.62 MIOTA:-3.75 DASH:-2.80
- WHY I BOUGHT 50,000 TRON TRX TOKENS! $1 MOONSHOT PRICE PREDICTION?
- Last Hour Price Changes: STEEM:0.72 BTC:-0.25 ETH:0.16 XRP:-2.52 BCH:-1.93 ADA:-1.19 LTC:0.33 XEM:-0.65 XLM:1.48 MIOTA:-0.39 DASH:0.21
- Last Hour Price Changes: STEEM:-1.27 BTC:-1.06 ETH:-0.58 XRP:-4.22 BCH:-2.05 ADA:-0.05 LTC:-2.08 XEM:-1.37 XLM:1.86 MIOTA:-1.80 DASH:-1.51
- Bitcoin Cash vs. NEM ( January 4th - January 10th )
- ICO TUTORIAL - HOW TO BUY ICO'S ON ETHEREUM
- 10GB HOME NETWORK (P2) - PEER TO PEER
- Last Hour Price Changes: STEEM:3.43 BTC:2.01 ETH:0.22 XRP:0.94 BCH:2.38 ADA:0.95 LTC:1.61 XEM:0.90 MIOTA:2.82 XLM:1.48 DASH:1.66
- DISTRIBUTED DENIAL OF SERVICE (DDOS) - LIGHTNING NETWORK - COLD STORAGE - BITCOIN - KYC - QR CODE - SOLIDITY - LIGHT NODE - INITIAL COIN OFFERING (ICO) - MINING POOL -
Note for @steemcleaners / @cheetah:
The agreement of our Team:
The following authors decided to create a Team in order to collaborate and share formats and content in our posts. Any copy of content between this Team does not constitute a plagiarism.
waht a concepts you share and also its algo <3 you made my day man <3.... i think crypto will future <3 whats your opinion ?? byt the way thanks for sharing this informatical stuff