Huge Ransomware Attack Worldwide, Demands BitCoin Payments
The BBC and others report that a huge international ransomware attack has occurred against computers in 99 countries. The attack exploits a Microsoft Windows vulnerability called EternalBlue, identified by the National Security Agency. The NSA's tools to exploit the vulnerability were stolen and then published online by the hacker group The Shadow Brokers, who made it freely available as a protest against the presidency of Donald Trump in early April.
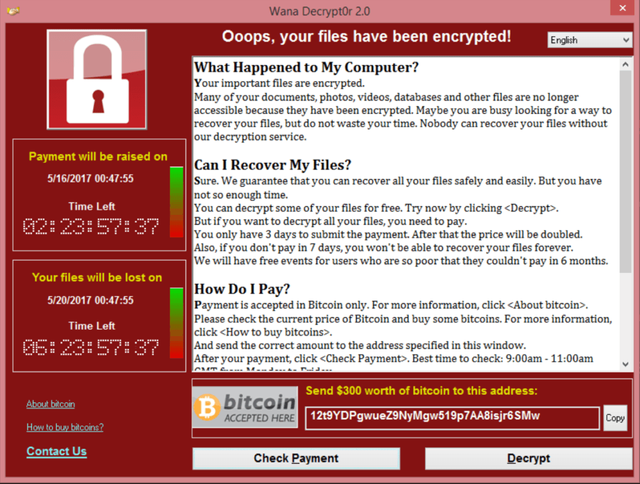
The ransomware, called WannaCry, encrypts data on affected computers (with the .wcry extension added to files) and demands payment of the equivalent of $300 USD in Bitcoin (0.171 BTC at the time of writing) to decrypt it. The ransomware further threatens that failure to pay in time will result in the amount demanded increasing and, eventually, the complete loss of victims' files. Kaspersky have published a more detailed initial analysis, including the bitcoin wallets to which payments are requested.
The worm on which the ransomware is based spreads by identifying and infecting other vulnerable computers on the network. Microsoft has earlier issued a patch against the vulnerability, but it seems many computers have not been updated. Spain's Computer Emergency Response team has recommended the immediate installation of updates in the Microsoft March 2017 Security Bulletin as a way of limiting the attack from spreading.
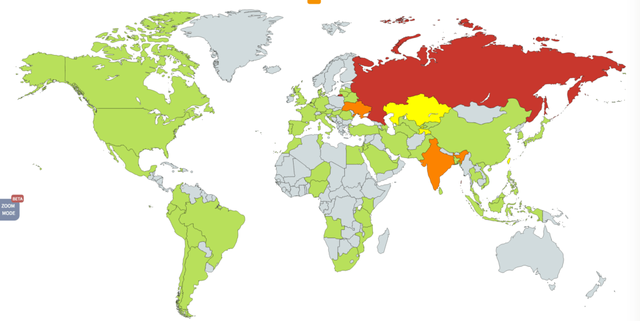
It seems that Russia was the most targeted country during the early hours of the attack, although computers belonging to state institutions and private companies in US, UK, China, India, Ukraine, Italy, Spain, Taiwan, Sweden, Portugal and others were also affected. The ransomware's interface is written in several languages.
The most tragic news so far is that patient data held by the UK's National Health Service has been affected, meaning that many vulnerable patients could not be treated. The NHS has offered updates on the situation, and are advising emergency cases to visit Accident and Emergency (A&E) as normal. For more details, see this dedicated BBC article.
UK Home secretary Amber Rudd has announced that "lessons must be learned" from the ransomware attack. The NHS, incredibly, still uses Windows XP on its systems, which has not received security updates from Microsoft since April 2014. This means NHS computers are 3 years out of date.
This attack will and should intensify the scrutiny of security practices relied on by large corporations and state institutions and the innevitable vulnerability of "Internet of Things". It should also inspire an urgent debate about the culpability of state level organizations like the NSA and CIA in such attacks. Both intentionally undermined the security of millions of people's computers and then lost control of the tools with which mass exploits, such as this one, could be executed.