The Rise of the Privacy Token
It's hard to imagine our lives these days focused on privacy considering the mass amount of information being divulged about ourselves every second through the various social media platforms available to us. One would argue that social media and privacy are an oxymoron; however, just recently a data breach was discovered on the popular online social media platform Facebook. Over a two year period, a third party company, named Cambridge Analytica, harvested profile data from millions of Facebooks users without their consent (Romano, 2018). Users compelled to share their personal information publically are now feeling violated as a result of the data breach.
Although some might believe that users should not expect any privacy when engaging in online social media and like platforms, one thing is true; users are still focused on privacy when it comes to their everyday lives, especially when it comes to the area of money.
Enter the discussion, cryptocurrency, which, for the longest time, was linked exclusively with anonymity. Consider that three years ago, virtually anyone at any time could buy or sell anything with the well-known cryptocurrency Bitcoin and never be tracked, or caught if breaking the law (Bohannon, 2016). Fast forward and you will quickly learn that Bitcoin is not as anonymous as once thought. In light of Bitcoin’s privacy shortcomings, financial privacy will continue to be the focus for many. “I don’t feel people have the right to know, unless disclosed, how much cash is in my wallet, just like I don’t feel anyone should know what conversations I’m having with anyone else,” says Ryno Matthee, a software developer based in Somerset, South Africa (Bohannon, 2016).
Understanding that financial privacy is a top priority for a lot of people, the current cryptocurrency sector offers several anonymous currencies promising to provide 100% transaction anonymity. One particular token stands out from the rest, and that is DeepOnion. DeepOnion is an entirely anonymous cryptocurrency that utilizes the TOR network to provide increased levels of transaction privacy. Below is a diagram illustrating how this is accomplished.
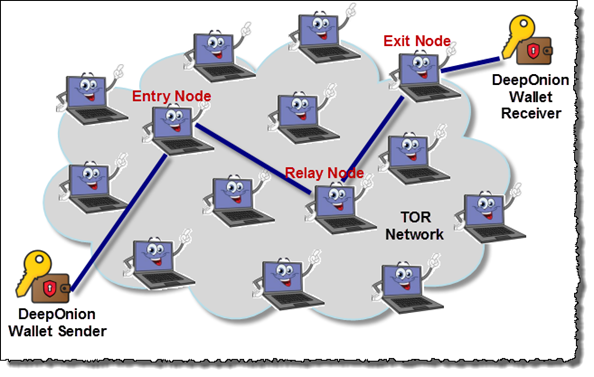
The transaction starts with the sender, making its way through DeepOnion relay nodes on the TOR network and making a final destination in the recipient’s DeepOnion wallet. As the transaction makes its way through the various relays, it is done so completely encrypted.
So if financial privacy is critical to you and you don’t want others knowing your transaction business, then consider using DeepOnion which guarantees complete anonymity.
References
Bohannon, J. (2016, March 9). Why criminals can't hide behind Bitcoin. Retrieved from http://www.sciencemag.org/news/2016/03/why-criminals-cant-hide-behind-bitcoin
Romano, A. (2018, March 20). The Facebook data breach wasn’t a hack. It was a wake-up call. [Blog post]. Retrieved from https://www.vox.com/2018/3/20/17138756/facebook-data-breach-cambridge-analytica-explained