All you need to know about distributed denial of service (DDos) attack

A distributed denial of service (DDoS) attack is one in which a large number of compromised systems connect to a single target (like a website), thereby causing denial of service for genuine users of the targeted system. The flood of incoming messages to the target system essentially forces it to shut down, rendering it unable to service legitimate users.
Historically, DDoS attacks have proven to be one of the most devastating hacks a company can face. To put it into perspective, Google’s net income in 2015 was $16.3 billion; If a DDoS attack shuts down Google.com even for an hour, it would cost them $1.86 million. There’s your perspective. Now let’s see how it works.
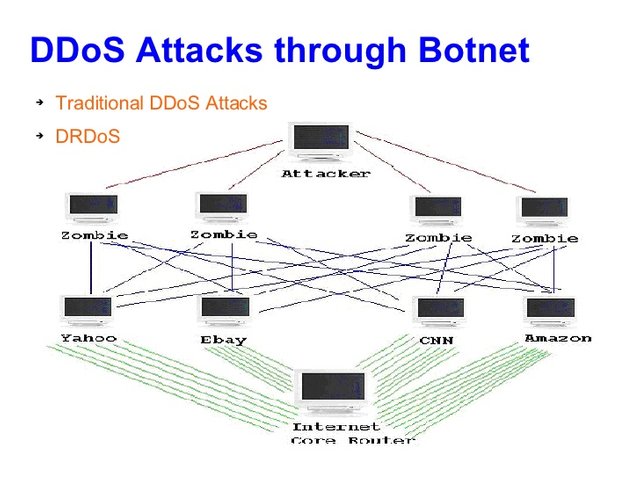
A computer under the control of an intruder is known as a zombie or a bot. A group of co-opted computers (infected by the same malware for the same purpose) is known as a botnet or a zombie army. Note that a bot generally implies a completely compromised system. Computers in a botnet are typically infected with a backdoor that allows the attacker to carry out any commands (such as pummeling requests at a website).
A typical DDoS attack has two steps:
• Create a botnet
• Unleash the botnet
The hackers of today don’t care about formatting your hard drive just for fun. In 2017, breaking into even pedestrian computers is no easy task. Nearly all publicly known vulnerabilities get patched up within days, sometimes hours. Most major security holes in popular software are only made public after being fixed. Hacking is hard work. Blackhats can no longer afford to expend so much time and effort just for screwing with random strangers. And so today’s hacks are more ransomware or botnets and less Albanian viruses.
Maybe blackhats should try being more polite
Any half decent DDoS attack requires thousands of infected systems. Some botnets are millions of machines strong and can deliver an attack so big that it can max out a country’s international cable capacity and even affect normal internet users (See: The DDoS That Almost Broke the Internet). No wonder this type of attack can be so harmful.
If your aim is to make a botnet, to begin with you’ll likely have to create a custom exploit to a vulnerability that has not yet been publicly exposed. The payload must also contain instructions for coordinating the bots or simply a time and a target. Now you have to figure out a way to actually spread the exploit to thousands of systems and only then can you carry out an attack on a target.
Of course, things are made easier by people who use old and outdated operating systems and software. In fact, most of the malware that is found in the wild (including the ones used to create botnets) exploits vulnerabilities that have been known for a long time and depends on the fact that most people don’t care about security. You can add “not being zombified” to the list of reasons to keep all your software updated. Remember, security is a cat and mouse game and the only way to win is to stay ahead.
So, I’m afraid we’ll have to amend our two step DDoS process mentioned above to the following:
• Find a vulnerability
• It may be some old vulnerability that still hasn’t been fixed.
• If it’s brand new (not yet publicly known), your botnet will grow faster and and bigger and remain in your control for longer.
• Implement the exploit: The exploit is what you’re going to spread. Not only must the exploit itself be well implemented (otherwise it’d be flagged by antiviruses) but it must also be packaged up in a way that makes spreading easier. This depends on your infection strategy.
• Decide the payload
• First of all, we need to figure out what kind of DDoS do we want to perform (more on this in the next tutorial).
• For DDoSing, at the very least the payload must have instructions of the time and target (IP addresses) to attack.
• But most hackers don’t just give up on the chance of creating a long term bot. So the payload usually includes a backdoor, one that can make the compromised system do the attacker’s bidding for a long time.
• The most successful payloads are those that interfere the least with the victim’s activity. If a DDoSing payload hogs all of the bandwidth, the victim is going to know something’s up. If a bitcoin miner makes the computer grind to a halt, they’re going to know something’s up. And you just lost a bot.
• Spread your germs Various ways you can spread your malware are:
• Email
• Social media
• Torrents
• Bonus points if you bundle it with a crappy toolbar.
Ahh the good old days
Oh and there’s also an implied zeroth step:
• You better have a hell of a good reason to DDoS someone because it is a lot of work to pull it off and if you get caught pulling it off, you should know that DDoSing is considered a criminal offense punishable by imprisonment.
And with that we come to the end of introduction to DDoS. Next up we’re going to see how to launch our own DDoS attacks.
How to Launch a DDoS attack
Now that we’ve got a good understanding on the what DDoS is, let’s take a look at how it’s practically done.
Most servers are built to handle a fairly large bandwidth and even the smaller ones can give maximum speeds to several hundreds of clients. Keeping this in mind, it is very difficult and for the most part impossible to actually bring down a website using DOS from a single computer. Where your internet speed might be 1Mbps, your target server might have several 100Mbps. This is the reason that most DOS attacks are actually DDOS,that is Distributed-Denial of Service.
DDOS attacks can easily bring down majority of websites. In DDOS, Botnets are used which are just a bunch of compromised systems who have been infected with a virus or trojan. A simple trojan can be sent out as a public download, and if the unsuspecting victims download it the trojan may silently settle down somewhere deep in the system and start up in the background without the user or the system ever knowing. When enough systems have been compromised in this way the master of the Botnet, the hacker who wants to DDOS a website may send out a message to the dormant trojans on several systems around the world, which may then indivisually begin attacking a server. This can be very harmful to the website, which due to lack of resources, may shut down for a long time and even get corrupted due to overloading. Further, since the requests for transactions are coming from seemingly random IP addresses all at once(the botnet), the victim may never find out the identity of the mastermind.
Although I won’t get into the technical details, here is an example of a fairly popular DOS tool – HULK. Hulk is just a simple python script that continuously sends out large packets from randomly generated IDs so as to fool the server. Again, using it from just one computer may not actually do anything to any big websites, but it may be able to bring down a small website, for example your school’s website in about a minute.
To perform this attack you need two things:
- The python Engine (v2.x) – To run and compile the hulk script. You can get it here : http://www.python.org/getit/
NOTE : Download the 2nd version only (for example the current one is 2.7.13), this script does not work with the 3.x version of python. - Hulk.py script – This will run like a normal cmd.exe window. It’s a small zip file,Get it here :
For technical details, The official website is :
HULK, Web Server DoS Tool
When all is done, you should have python installed, and hulk.py file extracted. It would be easier if you installed Python to a root directory, for example :
C:\PYTHON27.
Also, put the hulk.py file which you just extracted in the same root directory alongside the PYTHON27 folder(In my case, I put the hulk.py file in the C:\ directory).Again, both python folder and the hulk.py file are now in the C:\ ). With all that done, let’s launch our DOS attack ! - Open Run, type cmd to start cmd.exe window.
- Change directory to where you installed PYTHON and put hulk.py , Type ‘cd’ then the directory (Case sensitive) (cd= change directory)
cd C:\PYTHON27 - Now start up the hulk.py script as follows :
C:\hulk.py http://www.google.com
(Write the directory of the hulk.py file followed by a space followed by the website you want to attack (Don’t actually try this with google, since they tend to block IPs with weird requests like the ones we are sending. You may be blocked from google for some time. If you want to try it out, consider setting up a small website on your own, or ask someone’s permission.)
You should now see something like:
HULK ATTACK STARTED
Give it a few seconds then it will show how many requests it has sent. A few more seconds and if the attack was succesfull you will see something like: ‘Response Code 500’
As soon as you spot this, try opening the website which may say : ‘Resource Limit Reached’ or ‘Service Unavailable’ meaning you have successfully brought down the website.
Technically, most servers may temporarily deny all requests from your ISP (internet service provider) and hence your IP address meaning that you’ve not actually brought down the website for the world but only for yourself(The website banned you). This is why DOS isn’t as effective as DDOS. When the server has to repeatedly deny several IP addresses, it truly runs out of resources for anyone wanting to open the website.
Protecting Against DDos
The goal of any DDoS attack is to overwhelm a service to the point where it no longer works. While DDoS has historically been just an annoyance, there is usually a financial impact, such as lost sales or a spike in bandwidth costs. Cloud-hosted services, which charge by usage, are especially financially vulnerable to an onslaught of traffic.
DDoS attacks use large numbers of computers simultaneously targeting a single service. The attack often comes from botnets, which are composed of PCs infected by a virus. Recently, DDoS has been used by political protesters, who crowdsource attackers through downloadable software.
Older DoS attacks like SYN floods used limited numbers of attackers, so it was possible to use automatic per-client rate-limiting, or to block the IPs. Modern DDoS techniques try to avoid large amounts of traffic per attacker, and rely purely on large numbers.
Many sites may think they’re too small to attract attention. However, DDoS isn’t a hard attack to perform. Ironically, DDoS is even available as a service. If your site is big enough to attract any business, it’s big enough to attract a potential attacker.
Reducing the cost of an attack starts with early detection. There are simple techniques you can use to alert yourself to an attack. Run a script on your server that sends a message periodically with the recent traffic count: You’ll get a warning either if the count jumps significantly, or the message doesn’t arrive. Additionally, use a remote monitoring program that periodically checks the service’s availability.
A large DDoS attack may block your management access if the site is remote. Try to make sure there’s a cost-effective out-of-band management solution.
Once you detect a DDoS attack, the first step is to identify its unique characteristics. Despite the availability of cleverer techniques, DDoS usually relies on brute force – which means that the traffic from all of the attackers will have unique similarities. Because large numbers of attackers will be involved, scattered across the Internet, blocking the IP addresses will be nearly impossible.
Instead, do a quick packet capture of the attack. Finding examples will be relatively easy, since most of the traffic will be DDoS traffic. Commonalities can often be found in the URI, user agent, or referrer. What you’re looking for is a pattern that you can block with your firewall, router ACL, IDS, etc. It will often be an ASCII or hex pattern at an offset. Become familiar with the capabilities of your equipment, and try some tests in preparation.
Once you have identified the attack fingerprint, it is time to set up a block within your firewall or router to drop the majority of packets. However, a high-bandwidth attack may simply exhaust your WAN link: You’ll have a clean LAN, but your service will still be unreachable. Contact your carrier now to figure out how to work with them during a DDoS attack, in case they need to do the blocking for you.
Some service providers offer “clean pipe” hosting with automatic DDoS squelching. There are also companies who offer products and services to detect and prevent DDoS. Depending on the specifics of your service, it may make financial sense to pay for one of these solutions. Don’t forget the option of simply hosting the service somewhere large enough to absorb the attack – but remember that DDoS against sites that charge by bandwidth can result in unexpectedly high bills.
During and after a DDoS attack, ask for help. Your regional CSIRT (Computer Security Incident Response Team) should be alerted, as they have expertise and contacts that can not only help you during the attack, but also start the process of figuring out who did it and how. A global list is available here:
As cyber crimes get more sophisticated, businesses must be able to constantly adapt to these new security threats. While there are no methods or tools that can completely prevent DDoS attacks from happening, having a security “insurance policy” in place is the first step in ensuring that you are completely prepared. The ability to quickly suspend this new level of attack is tantamount to protecting company data as well as your business as a whole.
Practicing for DDoS
What we’ll attempt to do in this article is similar to testing a nuclear bomb (okay, not really). But still, there’s no way to tell exactly what will happen, other than to blast the damn thing because more often than not that’s just the way it is with DDOSing.
To refresh your memory, DDOS Attacks involve saturating the target machine with external communications requests (packets) so much so that it cannot respond to legitimate traffic. In most cases, this presents an obvious obstacle – Where to get massive amounts of bandwidth? By definition, servers are designed to handle huge quantities of traffic and when we are trying to attack it with traffic, it’s going to be very difficult (or is it?).
The usual way to DDOS is to slowly build up a botnet for example, by spreading a trojan (or RAT) that installs the DDOSing software and sets up a backdoor listener. When the infection has spread to thousands of systems, the hacker then activates the trojan and the DDOSing begins. Clearly, breaking into several thousand systems is not very legal or ethical, so even if some genuine website administrator wants to perform a dummy DDOS just to see what will happen and what’s the best way to handle it, they won’t be able to do it. This is another reason why small websites particularly are very vulnerable to attack – they don’t practice because apparently the only way to practice is illegal. So, when they are hit by an actual DDOS they simply don’t stand a chance. So, below we take a look at a possible solution that works for both good and bad guys. An alternative practice methods for website admins and a shortcut for DDOSing for hackers.
The method described below is quite unpopular. In a sentence, we use online services to DDOS for us. These are called “stressers” or “booters” and are simply services which provide large internet bandwidth for the purposes of simulating a DDOS attack. Before moving on, some of the websites mentioned below do offer trials but most of them are fully unlocked only after a payment. So, these may be useful mainly for serious networking administrators or website owners only.
Clearly, doing an actual BlackHat DDOS using this is very much possible if done correctly. But that would require using a VPN or TOR browser to hide your identity. Even with that, since you would have to make a payment, it could potentially lead back to you making this a very dangerous alternative if not done exactly right. Hence, I recommend using this method only for what it’s meant for, as simply fooling around can get you into very serious legal trouble.
You can search yourself for “website stressers” to find a few good ones.
For some reasons, the majority of these websites appear quite dull on first look. Perhaps they don’t want to attract a lot of attention. Anyways, In most of the above websites you’ll simply see a login page with a “Register” option. So, pretty much the only way to get inside is to make an account. Pick anyone and create an account. (Again, this tutorial is mainly for online service/website owners who want to make sure their website is well protected) Once you’ve registered for the first time. You will see several packages of boot time and strength. Whether you’re trying to DDOS someone else (which you shouldn’t) or your own online website or service, I recommend having several (2-3) booters or Stressers with moderate time instead of just 1 large DDOSer.
On The websites you will see a control panel-like window, where you can initiate your DDOS Attacks after selecting a package. To DDOS a home connection or a server, you will first need the (host) IP address. Many Booters Contain a built in Skype resolver and Domain Resolver. For “Port” option, the usual choice is Port 80 (Directed at home modems).
You will then be able to set your Boot time anywhere from 0 to the maximum time you paid for. Generally, UDP(User Datagram Protocol) is used for targeting a PC. For website and larger servers, SSYN attack is usually used which is considerably more powerful. You can think of these as DDOS attacks in which different types of optimal requests are sent for different situations and targets. Anything more than this will get a bit too technical than required here.
So that’s that for configuring and optimizing the DDOS attack. After this you will be able to start your DDOS attack as and when you please. Below you will find some useful relevant information that is frequently required for DDOSing using stressers and/or booters:
Skype Beta Resolver – http://www.iSkypeResolve.com
Other Ports:
(Home Connections)
53 – DNS Port
80 – Default Internet Port
(Xbox Connections)
80 – Default Internet Port
88 – Authentication Port
3074 – Xbox Default Port
(Web Servers)
21 – FTP Port
25 – SMTP/Mail
53 – DNS Port/Nameserver
80 – Default Internet Port
3306 – MySQL Port
Credit
Interesting information
upvote banjo
upvote banjo