Hackers using Facebook Messanger to spreads Cryptocurrency mining virus
A virus that turns users computers into a cryptocurrency miner without their knowledge is spreading across Facebook Messenger, which many security experts have warned for alert.
The virus, named "Digmine", affects desktop versions of the app when running on a Google Chrome browser, according to researchers.
If the user’s Facebook account is set to log in automatically, Digmine will manipulate Facebook Messenger to send a link to the file to the account’s friends, they wrote in a blogpost to victimize.
Crypto-mining virus works by hijacking a computer's processing power to help generate coins and confirm transactions for digital crypto exchanges. Effectively, it is tracking the blockchain, the digital ledger that keeps record of cryptocurrency like Bitcoin and other coins.
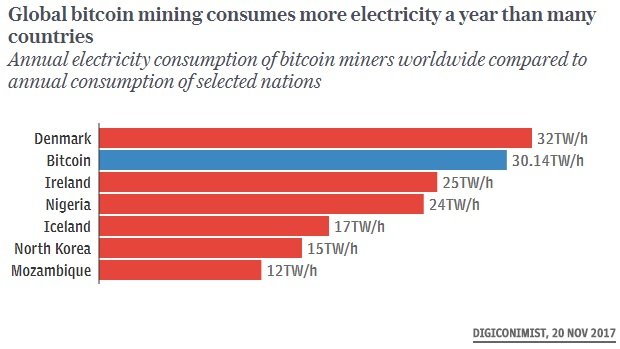
Mining a Bitcoin eats up a lot of power and so it has become lucrative for hackers gangs to affect computers en masses to do the job, earning them cryptocurrency including Bitcoin in return.
With a finite supply of 21 million Bitcoins, as many of opportunistic individuals and organisations are making use of high power computers to hoard as much of the supply as possible. The increasing popularity of cryptocurrency mining is drawing attackers back to the mining botnet business.
And like many cyber criminal schemes, numbers are crucial—bigger victim pools makes to potentially bigger profits. The real fact that they’re piggybacking on many popular platforms such as social media to spread their malware."
The malware appears to have originated in South Korea and has spread across Vietnam, Philippines, Thailand , Azerbaijan, Ukraine and Venezuela. And as it expected it to spread further, "given the way it propagates".
Facebook said: We maintain a number of automated systems to help stop files and harmful links from appearing on Facebook and in Messenger.
If we suspect your computer is infected with malware, we will provide you with a free anti-virus scan from our trusted partners.
We share tips on how to stay secure and links to these scanners on facebook.com/help.
Facebook users are advised to make sure they do not click on links they do not recognise. Some of the examples included the phrase "thisaworkstation.space", "mybigthink.space" and "thisdayfunnyday.space.
Please leave your thoughts and feedback below!
Thanks for reading.
@errajesh payed 16.7 SBD to @minnowbooster to buy a stealth upvote.

transaction-id e61536e08d62fd9ce635f2253cf98327dc78c02d
@stealthgoat
Thanks for sharing this information
@errajesh payed 28.3 SBD to @minnowbooster to buy a stealth upvote.

transaction-id df149d45e97fec21b0d2a22453e2222006937079
@stealthgoat
@errajesh payed 29.84 SBD to @minnowbooster to buy a stealth upvote.

transaction-id 5a9d9130dc01243fe97c21364db174bf4adc766b
@stealthgoat
@errajesh payed 29.93 SBD to @minnowbooster to buy a stealth upvote.

transaction-id 1d780be2856d6d5cd9671e9bd13f3c11c8808268
@stealthgoat
@errajesh payed 34.5 SBD to @minnowbooster to buy a stealth upvote.

transaction-id f87e084c3e831e0508fe05179417bf7d6c2a26d8
@stealthgoat
@errajesh payed 13.33 SBD to @minnowbooster to buy a stealth upvote.

transaction-id 7a6dc985f28c7965dcd2396ac4fa5121e6d0ad64
@stealthgoat
@errajesh payed 10.61 SBD to @minnowbooster to buy a stealth upvote.

transaction-id 152c2eb171e12a3a0f4bec143741db250fff0e3b
@stealthgoat
@errajesh payed 16.1 SBD to @minnowbooster to buy a stealth upvote.

transaction-id 1e89a96177a289b18feab85830f6f44b3726199d
@stealthgoat
@errajesh payed 16.2 SBD to @minnowbooster to buy a stealth upvote.

transaction-id 8b6bce4b8fbd730f278154f237201dd12c5430d1
@stealthgoat