DAPS privacy features in a nutshell
In my previous article named “A look at privacy coins and why DAPS will be different”, I compared DAPS with the rest of the well-known privacy coins. Here, I want to explain its privacy features.
Blockchain privacy (Obfuscated addresses/balances)
Blockchain privacy refers to capabilities that opaque the blockchain data (addresses and balances). This is the most important part to provide privacy without which users can be identified relatively easily. In this regard, DAPS uses Mandatory stealth address/public address system and Ring CT to hide addresses and balances.
Note: DAPS will have a mandatory stealth address system, with private being the default option. Users will be able to send a “public key” at any time, which will reveal the sender and amount sent. The public-key function will enable non-private payments and transparency on the fast and secure DAPS network.
Network Privacy (Obfuscated IPs)
Network privacy refers to capabilities like the TOR and I2P networks. These capabilities aim to anonymize users’ activity on the network by obfuscating information such as IP addresses. In this regard, DAPS uses the Mandatory TOR/OBFS4 relays for all nodes. This feature hides all node/Masternode IP addresses, which can be used as attack vectors. If TOR traffic is blocked, OBFS4 will activate and mask the TOR layer, allowing normal function. This will allow the DAPS wallet to run anywhere, anytime. One trade-off of this technology is slower wallet synchronization times on launch, which is acceptable in order to achieve wholly-obfuscated and protected nodes.
Default on privacy
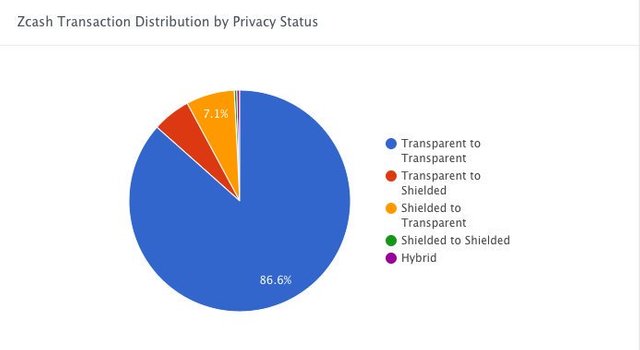
Privacy capabilities can either be optional or mandatory. If privacy is not the default option on original running, then the user is exposed for that original usage. For example, not all Zcash transactions are private by default. As of September 19, 2018, 86.6% of transactions on Zcash were sent publicly.
[image source: Blockspur]
DAPS is private on default.
Provable transactions
Obfuscated transactions are excellent, but sometimes you need to be able to prove to someone that the transaction was sent. In this regard, DAPS is equipped with a block explorer. The person who holds the wallet and initiates the transaction will get a key. With that key, the person (and everyone who owns it) can view the transaction on the blockchain explorer.
No message on the blockchain
Unlike bitcoin and many other projects with messages on the blockchain, DAPS does not allow storing of data-holding strings, preventing “spoiled well” attacks and making all transactions smaller.
Trustless
“Trustless” is the concept that you, as an end user of a network, do not need to “trust” any operator of the network to confirm or verify your usage as legitimate or illegitimate. A trusted network has a central authority or authorities which determine the fate of the entire network. An example of a “trusted” network in real life is Visa payments. You, as an end user, have no way to verify if your fiat dollars have actually transferred to the person you’ve sent them to outside of the banking or financial institution itself confirming said transaction. How do you check if your fiat is transferred properly on the SWIFT network? What is the equivalent to the block explorer for this system?
On the other hand, Bitcoin is a trustless network. Trustless is the idea that you can utilize this network without having to trust that the central authority or authorities are being honest in their actions. You, as an end user, can personally check to see where your coins are, where they’ve gone, and the user who got them. The block explorer is a public third party system where you can view the network any time, making it so you do not rely on node operators or any other authority to relay this data to you.
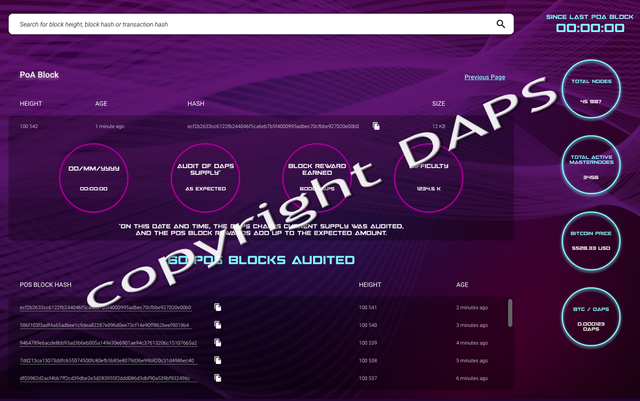
In privacy coins, Trust is hard to maintain while also approaching full obfuscation. How do you verify the supply of a fully private chain? In the case of masternodes, a fully private Masternode-enabled chain can be exploited by nodes colluding off-chain to enact changes. In current implementations of zero-knowledge proofs this issue appears as well, as there is no way to ensure node operators and minters are acting in an honest manner. The only way to ensure these fully private networks are not exploited is to introduce a third party check on these networks’ supply and other factors. This is where our unique Proof-Of-Audit (called Harpocrates) comes into play.
With proof of audit, masternodes and staking securing the DAPS network, it will be resistant to most hacks on private networks and solve the trust issue of Ring CT implementation. The only tracking in DAPS will be the total supply and block height via the Proof-Of-Audit block.

Congratulations @cryptoloving! You have completed the following achievement on the Steem blockchain and have been rewarded with new badge(s) :
Click here to view your Board
If you no longer want to receive notifications, reply to this comment with the word
STOP