Cryptography 101 (post #1)
What We're Learning and Purpose Of This Series
In this series, we're going to be looking at the basics of cryptography, how cryptographic primitives work, how to implement them correctly, and also reason about cryptographic constructions, and break ones that haven't been implemented correctly.
This series is just as much for me as it is for you. I'm learning about cryptography, and by sharing what I learn from various resources, I better internalize the concepts. Plus, you get to learn something. I'm in no way claiming that this is all my original material. I'm literally just going to be taking what I learn from courses and trying to post about it in my own words. Hope you enjoy!
Why should I care?
Well, it's no secret that cryptography is used in many many places. The most popular place you see cryptography is the internet. It's a way of keeping things a little more private. For example, the users of Steemit are protected by using a protocol call HTTPS. The wi-fi that you're using to hop onto the internet to then hop on this website is protected using the WPA2 protocol which is part of 802.11i (another topic for another post). Cellphones use mechanisms in GSM, bluetooth is another popular one using cryptography. You encrypt files on disk with EFS or TrueCrypt. DVD and Blue-ray disks use content scrambling system (CSS) and AACS respectively. The point is we use this cryptography stuff allllllll the time.
This series is mainly dedicated to cryptography as it relates to the internet so I'm mainly going to focus on that. Later on I may talk about how you easily break the CSS on a DVD or something just to keep things interesting.
Back to cryptography in the internet context! Here we have two actors. We'll call them Bob and Jane. Let's say Jane is the client and Bob is the server. I'm not going to go into huge detail about the ins and outs of how these two communicate, but the point is that Jane (the client) needs to communicate with Bob (the server). The problem is that someone might be able to eavesdrop on this conversation or worse yet, tamper with the data we're passing back in forth
In other words, we need a way to have secure communication between these two entities, such that they can understand what one another says without unauthorized third parties being able to do unsavory things. Enter HTTP protocol!

In fact, the actual protocol is called SSL or TLS, but that's beside the point. These protocols insure an attacker can't eavesdrop on data or tamper with data in the network.
Secure Sockets Layer/ Transport Layer Security
It consists of two main parts
Part 1: The Handshake protocol
This consists of Jane (the client) and Bob (the server) "talking" to each other and at the end of this initial contact or handshake a shared secret key has been created. Jane and Bob know what the secret key is, but no one else does. Wait! How do you make the key? How do you do the handshake? You use what's called pubic-key cryptography (covered later in the series)
Part 2: The Record Layers
Once the secret key has been established, Jane and Bob can begin transmitting data and before transmission they crypt and decrypt this data to ensure it's confidentiality and integrity.
Symmetric Encryption
Symmetric encryption is one of the fundamentals of securing traffic and data transmission on the web.
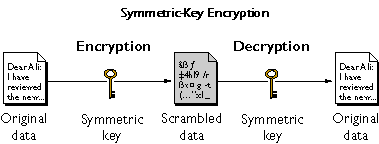
What makes a symmetric encryption a symmetric encryption system? Basically, that key that we talked about that's created during the handshake protocol. Well the client (Jane) and the server (Bob) are using the same key to both crypt and decrypt the data being transmitted. In order for all this to work you basically need three things. A cipher, a message, and a key.
Cipher - consists of an encryption and decryption algorithm
The cipher takes the message, in this case Hello World, and the key as input, and uses that to produce ciphertext that Bob receives. Then the opposite happens. Bob uses the cipher text and the key as input into the decryption algorithm and produces the message as output.
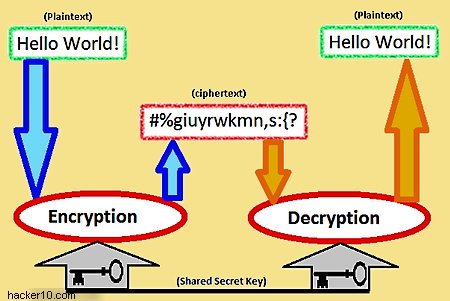
Something worth pointing out here is that everything here is public. The encryption and decryption algorithm are public. The only thing that should be unknown to adversaries is the secret key.
Keys, keys, keys, I got the keys, keys, keys
That was for my Royce da 5'9 fans out there. Anyway, keys can be divided into two main categories. Those being,
Single use keys
- A key used to encrypt only one message
- ex. Encrypting emails:A new key is generated for every email
Multi-use Keys
- A key used to encrypt multiple messages
- encrypted file systems: same key used to encrypt many files
In Short
Cryptography is obviously a great tool. There's clearly a lot to it, but it's a fantastic way of keeping data secure. However, it is only a tool, one of many. It is not the solution to all security problems. It is merely one tool in the world of protecting information.
I'm super excited for what I've got lined up next. We're going to be diving into algorithms and actually doing some practical projects and implementing the things we learn. So, thanks for reading and I'll see you in the next one!