Security Lessons Learned from @JewKorean
Note: I am not a security expert nor computer professional. The following is meant for educational purposes only and is not security advice. If you feel that your computer has been compromised, please seek out a qualified computer security specialist in your area.
In a recent interview, @jewkorean, BigEasyShiller, and Chris talked with a user named Cain to discuss the circumstances around his recent crypto hack. Not only did Cain lose a substantial amount of money in the hack, but his bank info, credit card information, and email address were also compromised.
As someone who used to put together computers and run tech support for friends, I believed I had a decent background in cyber security, enough to protect myself from similar attacks. After viewing this interview several times I know that I was mistaken. I have since implemented several of the suggestions from the video above.
The purpose of this article to is summarize the security measures discussed in the interview and break them down into actionable steps everyone can take in order to secure their cryptos and computers. These steps will be categorized as Easy, Medium, and Hard. I have omitted several suggestions made in the video i.e. locking down computer ports, because I was unable to find easy to follow directions.
Easy - Do Now
Change your router default password
Most people never change the login and password after setting up their router. This is a mistake that can leave your home network compromised and vulnerable to bad actors. Once a hacker has access to your network, they can see all data that flows to and from your computer.: your emails, attachments, and IP address are all viewable. All routers from certain manufactures have the same login and password when they leave the factory.
As an example, Netgear's defaults are "admin" and "password". Here is a link that shows how to change the login, other routers have similar configurations.
https://kb.netgear.com/20026/How-do-I-change-the-admin-password-on-my-NETGEAR-router.
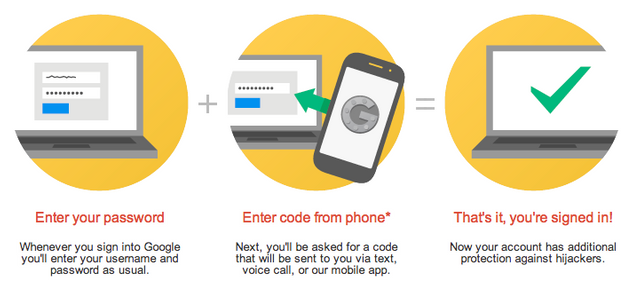
Use Two Factor Authentication
Two Factor Authentication (2FA) is a secondary layer of security, useful when accessing email and crypto exchanges. 2FA requires that a user enter a one-time code into a website before gaining access to it, this code is generated on your iPhone or Android device. If a hacker is able to get your login and password, they would still need your iPhone or Android in order to get the code to access your exchange. Using an exchange WITHOUT 2FA is risky and not recommended. The most popular are Google Authenticator and Authy.
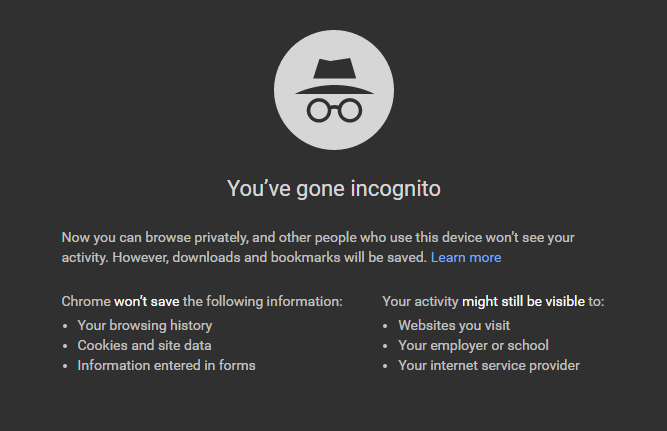
Disable Chrome synching across devices
Chrome's syncing feature is convenient, but greatly increases your exposure for attack. The sync saves data and bookmarks across multiple devices: PC, Mac, iPhone, etc . More importantly, all autofill data is synced across your devices, this includes your Credit Card data, Passwords, Logins, etc.
If one of your synced devices is compromised, both devices can now be compromised. Allowing data to sync across devices increases your exposure to risk.
If your computer is compromised, your browser history will allow a hacker to see the exchanges that you use. Using Incognito Mode eliminates website history, trading websites, and tracking cookies. A workaround is the delete all your trading after every session on your computer, but Incognito Mode saves a step.
Medium - Requires Continuous Attention
Be Suspicious
It should go without saying, but in crypto, do not trust blindly. While crypto groups in Discord, Telegram, or even Meetups can be exciting and useful, there is always a chance that someone will try to separate you from your hard-earned coins. One should always assume a certain level of paranoia around crypto assets and personal data. If you go to a meetup do not bring your wallet. Do not help someone else with their wallet. Do not allow people to have access to your wallet.
The interview gives an example of someone being followed after talking about Monero in public. While it may seem absurd, if you are planning to talk about cryptos in public make sure you are aware of your surroundings. You may want to find a more private space to talk about your holdings.
Verify websites to avoid getting phished
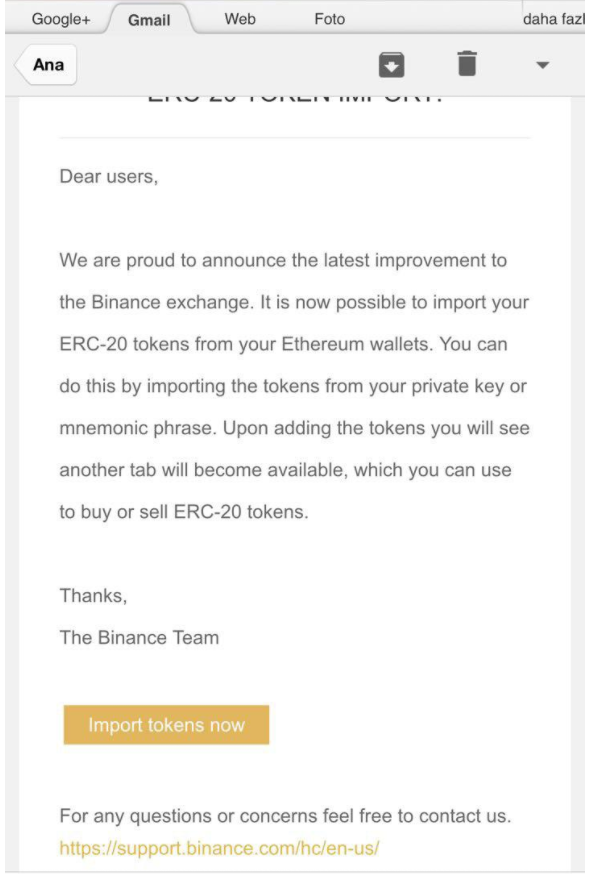
Investigate all "official" emails from service providers, cable company, bank, credit card company, Coinbase, etc. If in doubt, do a google search for the suspicious email and "scam" or "phishing". Recently, emails from an individual masquerading as Binance were flagged as a phishing attempt. Binance was quick to respond, as the email was enticing users to send in their private Ethereum keys.
https://support.binance.com/hc/en-us/articles/360002070252-Types-of-Phishing-Email
If you sent your private keys to this website, your money is gone. NEVER send your private keys to anyone. I go more into phishing attempts in my previous Steemit article.
Use a VPN
A VPN (Virtual Private Network) creates a layer of obfuscation between your computer and your ISP. Without a VPN, your ISP is able to see your browsing history and all data that is sent or received from your computer. A VPN hides your location, encrypts your data, and keeps your ISP from viewing your browsing habits. If you use public Wi-Fi in coffee shops, airports, or libraries, you absolutely need a VPN as the data on those networks is public. Anyone with the right software and knowledge can see what you are doing on a public Wi-Fi channel.
There is a diverse range of VPN's to choose from, ranging from free to expensive. If you are comfortable creating your own VPN, by all means please do so. For those less inclined to compile binaries, my choice for VPN is Private Internet Access: https://www.privateinternetaccess.com/.
PIA is less than $5.00 a month and has been positively reviewed by PCMag.com, TechRadar.com, and IGN.com. Additionally their VPN does NOT store your data on their servers.
Create new email for each exchange
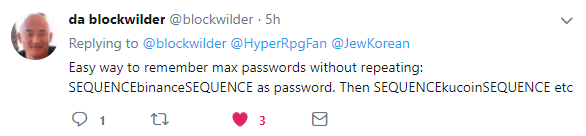
Users should use a unique login and password for each exchange they use. Re-using either of these greatly increases the chance that your account could be accessed if your system is compromised. Logins should be semi-random and not immediately traceable to you. Similarly, passwords should be equally difficult. One suggestion I've received is to sandwich your login with the exchange name, i.e. BittrexLOGINBittrex.
If you feel that remembering these logins and passwords are too complicated, there are password managers available that will handle these tasks for you. These programs allow you to generate random passwords quickly and log into your services without the need to remember each password individually. Keeper has been recommended to me in the past https://keepersecurity.com/
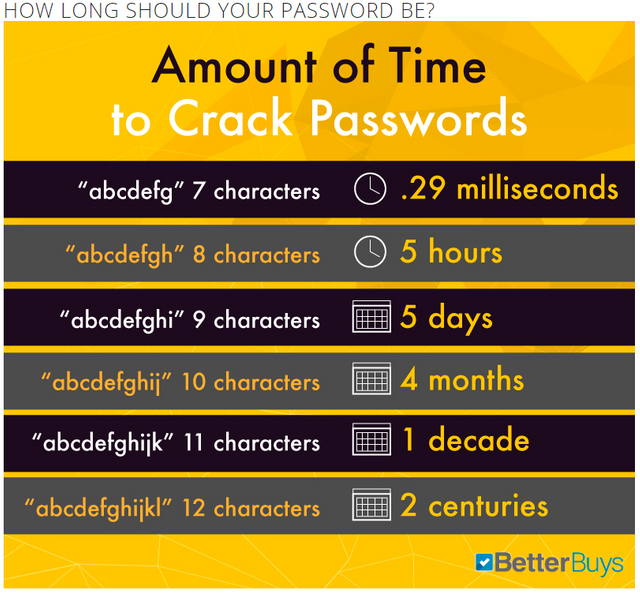
Max out password character count
Longer passwords are more difficult to crack, and the more difficult it is to crack, the more likely a hacker will become frustrated and move on to an easier target. A popular method of password hacking is to run a program that goes through every combination of letters and numbers until the password is guessed. The following link gives you an idea how secure your password actually is.
Note: While the site claims it does NOT save your data, please use a dummy password to be safe.
Password Hacking times (brute force attack): https://www.betterbuys.com/estimating-password-cracking-times/
"Lengthy passwords are often associated with an increase in password entropy, which basically is the measure of how much uncertainty there is in a key. An increase in entropy is seen as directly proportional to password strength. Therefore, a lengthy list of easy-to-remember words or a passphrase could be actually more secure than a shorter list of random characters."
http://resources.infosecinstitute.com/password-security-complexity-vs-length/
Hard - Defcon 1
Layer your security protocols
Layering security protocols is a combination of all possible steps you can take to keep your data safe. It involves using as many steps as possible to separate you from your exchange. Two factor authentication, separate email account of every exchange, erasing internet history, these are all steps that should be taken before you access your coins. It is a pain, but if you want the security of sovereign bank you need to think like sovereign bank. Crypto ownership requires that users take precautions that would frustrate and deter a malicious entity.
Dedicated trading computer
Designating a computer for the sole purpose of trading greatly reduces your risk of inadvertently downloading malware/corrupt java script code on to your system. In the interview, it is hypothesized that a roge java script from an ad was how the hacker was able to get into Cain's computer. Setting up a new computer for trading, implementing the aforementioned security protocols, and disabling java script may reduce your threat risk.
Social Engineering
Quite possibly the most nefarious of security exploits is Social Engineering. In recent times, this term has come to encompass the psychological manipulation of individuals in order the receive private user information. People with your personal data can call up your service providers to reset phone numbers, logins, or passwords. This includes Google, your Bank, Post Office, etc. The personal information needed to fool the customer service representatives for these institutions can be bought online.
Your Bank has the option of creating additional layers of security at your request, aside from the normal questions like your Social Security number and Mothers Maiden name. These can all be found from an online search. Call them and ask if you can create specific security questions:
"What is the best kind of cake?"
"Pie"
"Who is your favorite recording artist?"
"Potato"
In Closing
I hope you have found these suggestions useful. I know not everyone will follow them but raising awareness is the first step in making yourself a smaller target for would-be hackers. Remember that we are in a new age of financial freedom, and the price of that freedom is eternal vigilance.
If I have missed anything that you do to make yourself more secure online (or if I am mistaken in my explanations) please let me know in the comments.


Awesome post. The only way to do great work is to love what you do. You have achieved that.
Thanks my man. As we grow closer to mainstream crypto adoption, this kind of material will become more necessary. Let me know if there's anything you'd like to see in the next crypto article.
Absolutely! Thank you because you mentioned a step I need to do. If you are your own bank you can never be paranoid enough. That point about Monero reminds me: When Bitcoin was trading at a much lower price, I used to wear Bitcoin t shirts around the community. It is how I was able to buy Bitcoin on the street. But when it became a status symbol I stopped wearing those shirts. It’s saying “I got money.” So my advice is to always blend in wherever you are. Next, store most of your cryptocurrency in offline wallets. Cold wallets or a hardware wallet. Keep hard copies of the seeds on a burnable CD ROM. Store it in a safe deposit box. I own a Trezor. I rarely do firmware updates because my 24 word cards are needed in case the update fails. I keep my cards in a safe. The amount of cryptocurrency I buy these days is small anyway so I buy it on a central exchange (using 2FA of course).
Congratulations @kaltoro! You have completed some achievement on Steemit and have been rewarded with new badge(s) :
Click on any badge to view your own Board of Honor on SteemitBoard.
For more information about SteemitBoard, click here
If you no longer want to receive notifications, reply to this comment with the word
STOP