GOLDLOCK | NOT THE COLD STORAGE. NOT THE HOT STORAGE. JUST THE RIGHT STORAGE.
INTRODUCTION
Every wallet on blockchain have two core components:
Private key:
This is takes the form of a long string of alphanumeric digits. They are to be kept as private as possible because they can be used to verify for the legitimacy of every transaction carried out in your wallet. The private key is like your PIN code to your wallet as in the case of bank accounts. For this reason, it should be stored properly, as a lost private key will result in the irreversible loss of funds in that wallet. This is blockchain, there is no bank to give you another PIN code .Public key:
WHAT IS GOLDIBLOCK?

CURRENT STORAGE METHODS FOR DIGITAL ASSSETS
It is understood that storing large amounts of cryptocoins on any exchange exposes them to the risk of loss or hack, So, instead of keeping your cryptocoins on an exchange, consider setting up a safe wallet which you own the private keys to. We recommend you ether setup an offline paper wallet or make the small investment in a hardware wallet. Now your cryptocoins are safe at the wallet level. You are now left with the task of securing your private keys as this is now the only access to your assets. Currently, there are basically two distinct ways of securing digital assets and private keys, and they are:
HOT STORAGE:
COLD STORAGE:
THE GOLDIBLOCK SOLUTION
Goldiblock is built based on three main ideas, and these ideas are:
How does goldilock achieve the three premises?
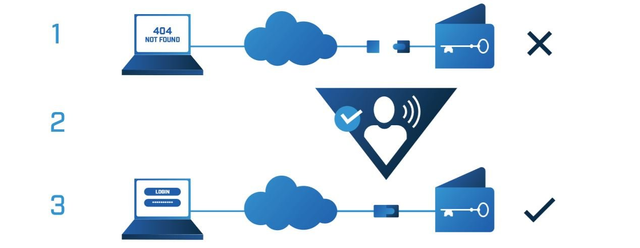
Goldilock makes sure that the wallets are stored offline through a physical airgap mechanism (1), and this makes it isolated and unaccessible to the internet and thus to the hackers. However, the user can access their data and wallet over the internet whenever and wherever they want to, and in a highly secured way as goldilock utilizes a non-IP mechanism for internet access(2). Users are provided with a dedicated URL and also access credentials such that wallets are accessed over a highly encrypted connection(3).
You would agree with me that a hacker will require enough time working on ways through which he would be able to access your secured data online. He would have to break alot of encrytion codes before he will finally get access to it. Well with the way goldiblock is designed, it is 100% unlikely that a hacker will allowed that much time in decrypting your stuff online. Goldiblock allows that you will be online for just the shortwhile during which you will be needing your data. With this i do not see any possibility of a hack scenerio.
HOW DOES GOLDIBLOCK ENCOURAGE MASS ADOPTION?
Since the major reason why most institutions display sluggishness when it comes to crypto-adoption and crypto-investment is because of the issue of insecurity in key storage. Now that goldilock has come to provide a lasting solution to this problem, these institutions can start running back to blockchains and cryptocurency as they no longer have to dread that their keys will be compromised by hackers, stolen, misplaced, confiscated or even destroyed.
Since the major reason why most institutions display sluggishness when it comes to crypto-adoption and crypto-investment is because of the issue of insecurity in key storage. Now that goldilock has come to provide a lasting solution to this problem, these institutions can start running back to blockchains and cryptocurency as they no longer have to dread that their keys will be compromised by hackers, stolen, misplaced, confiscated or even destroyed.
WHY IS NEO THE PLATFORM CHOICE FOR GOLDIBLOCK?
Goldilock choose NEOas its choice platform because NEO is a non-profit, community-based blockchain project that uses blockchain technology and digital
identity to Digitize assets, Automate the management of digital assets using smart contracts, and Realize a “smart economy” with a distributed network. With these combined, NEO will build a highly secured blockchain that will be recognized by enterprises and governments. These are the exact guiding premises of goldiblock.
NEO is distinguished from its fellow blockchain smart contract competitors because it is endowed with the following features:
Aims for Regulatory Compliance
we all know that in large companies and government settings, all physical transactions and assets are subject to auditing. Reason along that same angle too, if there large companies and governments are going to operate on the blockchain, these institutions will also require the ability to audit digital assets and transactions. Digital identities will need to be known and verifiable. This is exactly what NEO is committed to to achieving. NEO make use of the Public Key Infrastructure (PKI) X.509 standard for identity, which means that NEO will have the ability to issue and confirm digital identities. NEO is building this digital identity mechanism into their ecosystem.Utilizes a Superior Consensus Mechanism
NEO utilizes an improved form of the Proof of Work (e.g. Bitcoin) and Proof of Stake (e.g. NXT) consensus mechanisms entitled “Delegated Byzantine Fault Tolerance” (dBFT). This dBFT is a modification of the Proof of Stake protocol whereby holders of NEO tokens vote for delegates, and the delegates must reach a consensus on acceptable transactions.Processes Transactions Faster
Since NEO makes use of the “Delegated Byzantine Fault Tolerance”, it therefore means that it would not be requiring thosands of mining machines in order to complete a resource-expensive algorithm to verify transactions. With this dBFT consensus mechanism, the blockchain can process more than 10,000 transactions per second without any accompanying fees for transaction.These features automatically qualifies NEO to be the ideal platform for a secure wallet utility token. These features are in total alignment with Goldilock’s mission to ensure that consumers are transacting business on the blockchain in the most secure and efficient way possible.
HOW CAN INSURANCE COMPANIES BENEFIT FROM GOLDIBLOCK?
HOW WILL BANKS BENEFIT FROM GOLDILOCK?
During the course of a negotiation between goldilock team and the representatives of one of the three largest banks in the United States, they were informed of the banks' opinion that the application Goldilock solution will allow them to provide “a safer and more convenient” wire transfer process than they currently offer their clients. Goldilock will provide a secured backend solution for bank account and transfer management.
GOLDILOCK TOKEN
The LOCK token is registered as in NEP-5 token on the NEO Blockchain. It governs and audits all operations or transactions performed on the Goldilock ecosystem. The auditing mechnanism formed by the LOCK token in combo with the smart contract logic and the audit information is written on Goldilock's own private blockchain.
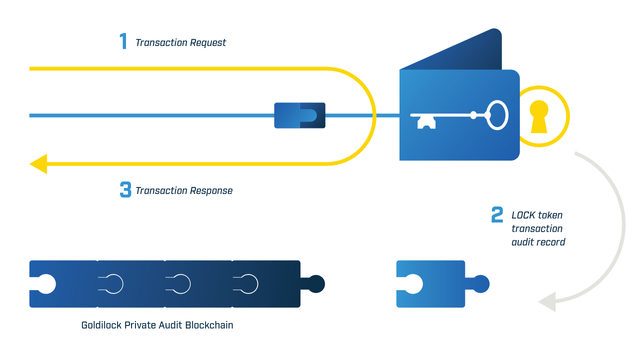
The LOCK token is also needed to access a Goldilock wallet. With the LOCK token, activities of users' nodes can be recorded and provided when needed, while encrypting and LOCKing away user-owned data from everyone including the Goldilock team. The LOCK token is also to be accepted means of subscription payment for individual users.
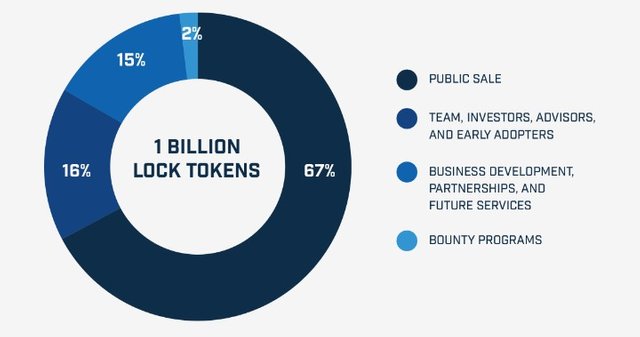
There are 1 billion LOCK tokens, out of which 670 million has been offered for sale to the Public by Q3 2018 and the others distributed as shown in the image below.
Goldilock Team
GOLDILOCK ADVISERS

GOLDILOCKS PARTNERS

GOLDILOCK MENTIONS
Goldilock Roadmap

Additional Information and Resources
See Video below for more information and Clarity;




This kind of game is very exciting. https://goo.gl/Dd9394