BEAM: IN THE BLOCKCHAIN CONFIDENTIALITY IS SECURITY
The arrival of cryptographic currencies brought with it innumerable commercial and financial applications have influenced even sectors related to the real economy such as industry and medicine. However, the storage of money and transactions without a centralized authority are also common use cases for these new trading tools. That is one of the reasons for the recent success of Bitcoin in recent years.
The blockchain serves to demonstrate the validity of the statement that transactions do not depend on a central entity, such as banks and the current system of FIAT currencies. Since all the participants of the system must reach consensus regarding these validation criteria, in the Bitcoin Network each transaction is public. We can see the input and output values and we can verify that the transaction is valid if they are summed (the sum of the inputs is the sum of the outputs.), although the usage of public and private keys in the process, transactions can be tracked and owners identities can be inferred.
Recent blockchain investigations and analyzes have shown that there are always data leaks, which can be easily extracted through the OTC agreements and grouping the blockchain data. This is done with the purpose of revealing the identity of users since the amounts of the transactions are open in a public accounting book. Once the identity of the users is known it is possible to see all their past transactions and their balance. This situation is a serious security failure for people and organizations who prefer that their transactions and balance are confidential and can only be seen by someone authorized by them. In fact, it is highly likely that this disclosure of data has made possible major theft of cryptocurrencies as evidenced by the following emblematic cases:
NiceHash: In December 2017 the platform for Slovenian miners lost approximately 4,736 BTC, equivalent to 64 million USD. Back then the thieves located the wallet where the cryptocurrencies were stored. To accomplish their objectives, the thieves first had to identify the users on the public ledger and track the transactions back to the address which had all the funds.
Coincheck: This exchange was considered the main cryptocurrency market in Asia, it was hacked by the order of 530 million USD affecting 260,000 investors, which is the biggest theft of this type in the history. An action of this type is not executed by inexperienced pickpockets, surely highly qualified professionals were the ones that identified the users and the dynamics of their wallets transactions.
Mt. Gox: In February 2014, hackers stole from Mt. Gox about 750,000 BTC from its customers and 100,000 BTC from the company. The lost was equivalent of 473 million USD as a result of a compromised computer of the company. In 2013 Mt. Gox was the largest BTC exchange in the world and concentrated 80% of the transactions of this cryptocurrency. This situation affected thousands of BTC holders and generated an institutional criminal action against the company by authorities in the USA and Japan.
To avoid such situations, it is required to limit the visibility of transaction details such as transferred amounts and participant identities. Only the required information to prove that the system functions properly should be public to avoid future security leaks and potential disclosures that compromise the funds of the crypto investors.
WHAT IS BEAM?
It's a scalable and anonymous confidential cryptocurrency based on MibleWimble protocol. In addition to maintaining the benefits of an incorruptible blockchain as Bitcoin, Beam has been designed with scalability and confidentiality in mind. Beam allows users to control the transaction data that will be displayed on the blockchain. Also, thanks to the MimbleWimble protocol, Beam has smaller blocks than any other blockchains, which allows greater scalability, more speed, and more efficiency. This concept is formulated to initially work as a store of value.
What makes BEAM special? - MiblewimbleBeam applied the MimbleWimble protocol to achieve the following features:
• Users decide what and to whom the information will be available.
• Confidential transactions do not cause a computational overload of the Beam's Blockchain, nor there is a tradeoff on performance and scalability.
• Trust configuration is not required.
• The blocks are extracted using the Equihash consensus algorithm.
• Limited emissions using a periodic division in half with a total amount of coin ~ 210 million.
• There is no information about the sender or receiver of a transaction in the Blockchain.
• The Beam Blockchain has orders of magnitude smaller than any other blockchain implementation.
• Support many types of transactions, such as escrow transactions, atomic swaps transactions and more.
• It is issued from each block during the first 5 years without ICO and backed by physical assets.
• It is implemented from scratch in C ++ by a team of professional developers.
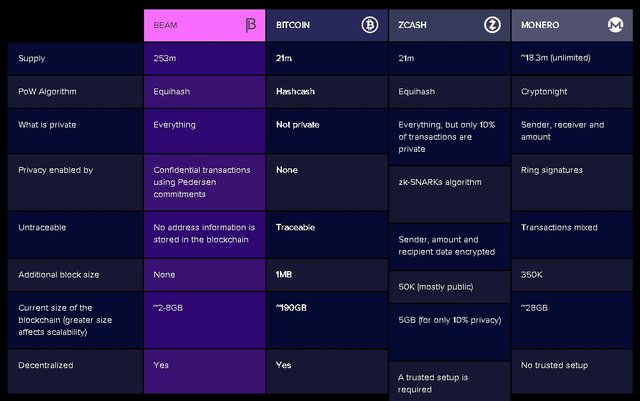
Beam Comparison
TECHNOLOGY: MIBLEWIMBLE
In August 2016, an anonymous author published a new protocol (like the Bitcoin disruptive innovation) called MimbleWimble that has an elegant design of efficient confidential blockchain. Its name refers to the spell of “Tongue-Tying Curse” of Harry Potter books, based on two concepts proposed by Greg Maxwell, which are: Confidential Transactions and signature data optimization.
Confidential transactions are implemented using a cryptographic commitment scheme that has two basic properties: hiding and binding. MimbleWimble uses a compromise scheme known as Pedersen Commitment that accomplishes this using elliptic curve cryptography and is of the same form
C = r * G + v * H
Where r is a blinding factor, a secret key that hides the real value v and G and H are generators of a specific elliptic curve.
Each entry and exit of a transaction is a linear combination of two factors: a real value of the transaction and a blinding factor. To transfer ownership of a UTXO (Unspent Transaction Output), due to the linearity property of the Pedersen Commitments, if we have two identical transactions: from A to B, and then from B to C, we can cut the intermediate transaction, which results in a merged transaction from A to C, which is a valid transaction in the system.
This scheme of "cutting" the intermediates extends to the entire chain and we obtain a system that only needs to store the current state UTXO, instead of the whole transaction history. The validity of the history can be confirmed by storing only the headers of the previous blocks that contain the validity test of previous states (using a structure called Merkle tree) and Proof of Work allows to reach a consensus on which of the header chains it must be considered the correct one.
Since what is needed to prove ownership of the UTXO is the value and the blinding factor, there is no need to store addresses in the blockchain. After making the transaction between two wallets, only the commitment in the blockchain is recorded. This means that no matter the resources of the attacker, personal information can't be extracted from the blockchain.
In addition to Inputs, Outputs, Tests, and rates, each MimbleWimble transaction includes the transaction kernel which contains the difference between the emitter and receiver blinding factors. Each transaction must also contain a zero-knowledge non-interactive rank test to ensure that the transaction value is positive without disclosing the actual value. It is important since allowing the user to create transactions with a negative value would result in the ability to arbitrarily create new currencies that should be prohibited by the system. For this purpose, Beam uses Bulletproofs a compact and highly computational efficient implementation of zero knowledge range tests that are attached to each transaction and verified by the system during the validation of the transaction.
Scalability performance and MibleWimble
Like any another blockchain, BEAM ledger is immutable, the compact architecture is granted because of the information needed to validate the entire blockchain is much smaller than the complete list of transactions. The user's wallet, a new node connected to the system, or an existing one that does not want to store all the information should only download block headers and current status to verify the entire blockchain.
Today there are roughly 423,000 blocks on the Bitcoin Blockchain, 80 GB or more of data that validating nodes should process in order to keep the system ongoing. This data is approximately 150 million transactions and 5 million non-confidential non-spent assets. While on a Mimblewimble blockchain, this exact scenario will be handled as follows:
• Each unspent output is around 3Kb for the range test and Merkle.
• Each transaction also adds about 100 bytes: a value of k * G and a signature.
• Block headers and explicit quantities are negligible.
• Adding up all barely reaches 30 Gb o data. This significantly lightens and improves the performance of the blockchain and facilitates its scalability.
Benefits of Beam - What does it offer?
• Confidentiality: All transactions are private, no personal information about the participants on a transaction is stored in the blockchain.
• Versatility: Beam's technology allows a wide variety of transactions such as atomic exchange, escrow, and time-locked transactions.
• Scalability: The "cut-through" feature of Mimblewimble makes the BEAM Blockchain smaller, which helps avoid computational overload.
• Sustainability: Open source implemented from scratch, governed by the community and supported by Beam Growth Pool: 20% of the block mining rewards go to this group to encourage the development and promotion of BEAM.
• Usability: A wallet for desktop computers and mobile devices designed for individual users and small businesses. The integrated panel makes administration easier, with actionable expenses and valuable information. Compatibility: An Equihash algorithm was selected to ensure widespread adoption by the GPU miners. BEAM comes with an extensive set of tools for mining nodes.
USE CASES
Albert is a miner who lives in Colombia, a country with high levels of crime. He is concerned that the large volumes of Bitcoin transactions he handles could help local hackers determine his identity and his location. Since Bitcoin Blockchain allows them to visualize all the data of the transactions and deduct Albert's balance. Eduardo, a friend from Venezuela recommended him to use BEAM, which is completely confidential and a perfect option for him to keep investing in mining. He chooses to fully adopt Beam and now he can rest assured with the MibleWimble technology third parties of transaction can only see that a transaction existed but it doesn't allow to know the identity of the parties or the amounts transferred, BEAM gives Albert the security he needs.
Mary is a cryptographer who has her own brokerage firm, in addition to the daily exchange transactions she prefers to have some cryptocurrencies as a store of value. She already has bought BEAM some time ago, she wants to negotiate a deal to make investments in one of her companies. She is negotiating with Karl, a man who lives on the other side of the world, thus she has to prove that she owns the asset in order to start negotiating. With BEAM these conditions are readily handled, Mary can select the levels of privacy so that only her future customer can check the ownership of the asset, and VOILA!!! Karl knows that he can trust his counterparty and he makes the transaction. Now Mary and Karl are partners in a new company.
Oil Mining Integrated INC. is an international oil drilling company and is evaluating opening a retirement fund for its employees backed in crypto. But its managers know that although Bitcoin and Ethereum are the most quoted in the market they have a disadvantage, all their transactions are public and you can determine the identity of the parties and the transaction amounts. An executive loves to blog in his leisure time and finds about BEAM thanks to a great contest held on Steemit, his preferred platform. Now the problem is solved, they decided to open an important fraction of the fund with this crypto because of the safety of their employees being a top priority. With BEAM, the transactions do not reveal the identity nor the amounts transferred.
CONCLUSION
BEAM offers the possibility of taking a step forward to the current blockchain, based on privacy-security and better performance by a lighter and shorter chain, LIKE Bitcoin achieved at the time can now be done by BEAM with a disruptive technology. innovative that will redefine the operation of the most sought-after cryptocurrencies in the market. With BEAM it will be possible to increase your money's performance substantially while allowing a saving of memory and data storage, until now unused or underutilized.
Here is my Tweet about the contest
This is my entry for @originalworks
https://steemit.com/crypto/@douglasflo/beam-in-the-blockchain-confidentiality-is-security
beam2018
beamtwitter


%205171661.jpg)





This post has been submitted for the @OriginalWorks Sponsored Writing Contest!
You can also follow @contestbot to be notified of future contests!
@douglasflo