Information security: Data Protection... Part I
This is a series of articles that cover some basic InfoSec (information security) and OpSec (operational security) tips for private home/mobile or small business use.
I'm an IT security guy that came around quite a bit from small business settings to big corporations in FinTech and other industries.
I'm trying to cover much in - hopefully - simple words with some simple approaches, methods, processes and hands on recommendations for you to assess and maybe up your InfoSec (information security) game if you want. Please understand that I will have to be pretty generic in some parts of these articles...
...but if you got questions go ahead and drop them in the comments and I'll try to help out!
IMPORTANT! If you're insecure with some of the recommendations please hire an professional before getting into trouble with your systems and possibly blaming me for that!
A general advice! Please only "touch" (change) things/configurations that you are familiar with and that you can undo if needed!
Lastly, why do I do this? To raise awareness and to hopefully help you to raise your personal information security & data protection bar!
I will cover the following topics in this series of articles
- 190513 Assessment & general thoughts
- 190514 Passwords
- 190515 Prerequisites for secure patching of systems, Part I
- 190516 Prerequisites for secure patching of systems, Part II
- This article here: Data protection... Part I
- "Right sized" processes for Risk management/InfoSec/OpSec
- Automation?
A quick recap of points we touched in previous articles...
Assessment...
First article in series Here I’ve suggested that you make an assessment of your internet connected devices or better of all devices in your own network including mobile devices! This includes collecting information on serviceability of these devices.
This is the groundwork for the next steps.
Passwords...
The Password article touched on some general aspects of password handling like defining an password policy and the use of some help by using password managers.
Prerequisites for secure patching of systems, Part I...
With Prerequisites for secure patching of systems, Part I I've introduced you to some of the frameworks (ITIL) and methods (ITSM) to understand what you're dealing with, how to collect and store information of your environment (CMDB) and how to make an first estimation of the criticality of your systems (BCM, BIA).
Prerequisites for secure patching of systems, Part II...
With Prerequisites for secure patching of systems, Part II we dove a little deeper into the justification for putting time, effort and money on the table to protect our environment. We looked at IT risk management and resulting prioritization of systems/apps to gain knowledge about what is it all worth to us. At last we had a glimpse of a possible cyclic process to handle service improvement and vulnerability handling.
Data protection...
When words really matter!
Data protection is used to describe backup of data as well as protecting data against unauthorized access. To make things worse there's often a mix up with data privacy.
But it's not sooooo complicated after all it's just a little confusing...
Data protection is backup of data but data protection can as well be technical means to prevent unauthorized access while data privacy addresses legal issues.
You will encounter much more confusion in this regard when you see that the overlaps go on and on for example different policy names for "the management of personal information" as in the US "privacy policy" is used and in the EU (and almost everywhere else) you'll find "protection policy" to describe the same thing more or less.
To make things more clear I will use data protection in the context of backing up data while trying to make sure that unauthorized access is prevented.
So let's look at data protection in the context of backup & recovery.
As already stressed in the previous articles to ensure a safe method to service (patch, security patch) your environment we extended our understanding of what we are handling here and how much it is worth to us. The next step is to make sure that we can return to the starting point before patching, in case something goes wrong, for those systems we found worthy enough.
In our assessment list we've added therefor a prioritization of our systems.
Backup and recovery
We will have to find fitting methods for each and every device on our list that has to be backed up. We will have to decide if a subset of all data on each system is a sufficient protection or if we have to backup all data and system files to make a complete recovery possible.
Example 1 mobile device:
If you have a mobile device of which all data is automatically synchronized (backed up), to a local storage or cloud service, you could decide that this is enough to recover the device as a whole, since a reset or default reinstall would cover the basic operation of the system and the synched data can be re-synched back to the device again once it is running again. For some manufacturers these synchronization tasks cover also the installed apps on the mobile device or they offer even a complete backup & recovery solution for mobiles for example Apple with the iTunes desktop app.
Example 2 Windows desktop or notebook:
Windows desktop system. It could be sufficient for some installations to just backup the data of the system and to reinstall the OS if something goes wrong with your patch or update. In Windows you also got the choice to use so called system restore points where a rollback to a created restore point is possible if needed. Windows also has an on board backup & recovery solution that you can use. Please see this Article here "Recovery options in Windows 10" for more details.
Example 3 Linux system
Here more or less the same like with Windows systems just a little more challenging for the average user. There is a whole array of different backup and recovery solutions that come with the most Linux distributions that can be easily set up and be used. In a simple "out of the box" installation a simple data backup of certain files/folders could be enough to get you up and running again after a from scratch installation but don't underestimate all that you've possibly have customized and adjusted in your specific system configuration!
Routers/managed switches/Printers
These can be very tricky in certain problem constellations. One typical problem is being left with a "bricked" device (hanging device typically after broken firmware update) after a firmware update malfunctioned (flawed code or power disruption, network disruption). Some manufacturers have implemented so called hard resets were you can restart/resinstall a system into a initial firmware level others don't have these options and you could be left with a inoperative device that only the manufacturer can fix after you send it in or that is a case for the trash because it cannot be saved once "bricked". Here you have to carefully investigate the options for your device and make sure that you understand what to do if needed. Most of them offer sufficient integrated solutions to backup/restore your configuration data at least.
So we have two general groups of backup/recovery solutions. On board in different sophistication and functionality levels and other so called proprietary alternatives. Each solution requires effort to get accustomed with and when it comes to different operating systems you'll end up with a lot of work to handle them effectively. On the plus side of proprietary solutions they in some cases offer the same "look and feel" regardless of platform, at least for Windows, Mac and Linux. But you will see that this comes at cost. The free proprietary backup and recovery solutions are often function limited or sometimes to slow to backup bigger capacities effectively. When it comes to one fits all you wont find a solution that covers PC operating systems, mobiles and other devices.
What do I recommend?
Look what best fits your needs and try to cover as much as possible with one solution. Maybe even look beyond free backup & recovery software and spend some time and money on it.
When it comes to your mobiles, managed switches and routers you'll have to check with each and every manufacturer what their backup & recovery solution offers for the specific devices. There's no way around this. Since this category varies so much I cant go into further detail on those devices.
Let's look into the requirement specifications and target specification for a local backup & recovery solution.
For this we'll check back with our system assessment list and more specific let's look at the RPO (recovery point objective) and the RTO (recovery time objective) for our systems.
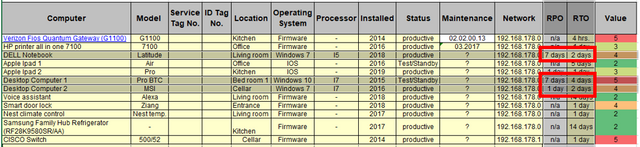
- Our minimum requirement in terms of RPO for the backup & recovery solution is a backup every 7 days for the "DELL Notebook" and the "Desktop computer 1" and a daily backup for the "Desktop computer 2".
- The minimum RTO requirement is 48 hours (2 days).
Next let's look at the backup media we want or have to use to meet these requirements.
Let's say the "DELL Notebook" has a 240 GB SSD Disk, the "Desktop computer 1/2" have each a 120 GB SDD for the OS installation and temporary files and another 500 GB SATA drive for programs and data.
So we'll have to make sure that our backup is performant enough to get consistent backups done in a acceptable time frame and that a recovery is possible in the RTO time frame.
For example this means for "Desktop computer 2" with 620 GB a minimum restore speed of 3,7 Mbps (mega bit per second) to get the system recovered in 2 days. The backup speed should be significantly higher to get the system backed up in a consistent state.
3.7 Mbps doesn't seem much but you'll find that many backup solutions, especially when they use compression are quite a bit slower than you would expect.
If you want to use cloud backup solutions you'll have to take into account your uplink speed as well as concurrency on the line with backup potentially impacting other web services used.
With local backup media you should be significantly faster. Here some numbers to play around with (theoretical maximums):
In bits per second:
USB 1.1 = 12 Mbit/s
Fast Ethernet (100BASE-X) 100 Mbit/s
Firefire 400 = 400 Mbit/s
USB 2.0 = 480 Mbit/s
FireWire 800 = 800 Mbit/s
USB 3.0 = 5 Gbit/s
USB 3.1 = 10 Gbit/s
eSATA = Up to 6 Gbit/s (750 MB/s) right now as it depend on the internal SATA chip.
Thunderbolt = 10 Gbit/s × 2 (2 channels)
Thunderbolt 2 = 20 Gbit/s
Thunderbolt 3 = 40 Gbit/s
In Bytes per second:
USB 1.1 = 1.5 MB/s
Fast Ethernet (100BASE-X) 12.5 MB/s
Firefire 400 = 50 MB/s
USB 2.0 = 60 MB/s
FireWire 800 = 100 MB/s
USB 3.0 = 625 MB/s
USB 3.1 = 1.21 GB/s
eSATA = 750 MB/s
Thunderbolt = 1.25 GB/s × 2 (2 channels)
Thunderbolt 2 = 2.5 GB/s
Thunderbolt 3 = 5 GB/s
Also let's not forget that these are the theoretical maximum interface speeds but your backup media can be significantly slower! The actual speed of a hard drive can be slower because of mechanical limitations and overheads. So you will have to live with a wide variety of different DTR's (data transmission rates).
If you're unsure what your data storage is capable of I recommend testing it!
For instance with "Crystal Disk Mark" (https://crystalmark.info/en/software/crystaldiskmark/).
Here a test run I ran against my local disk (SSD):
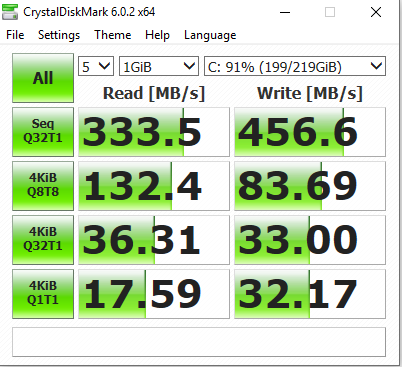
You will see that the DTR is always limited by the bottleneck in your environment... and there's always a bottleneck!
For instance if you backup a Wifi connected system to a network device in your environment you have the local disk, the local disk interface, the network interface, the network itself, the network interface of the target system, the disk interface of the target system, the disk itself on the target system and potentially lag coming from multiuse of any of these possibly limiting interfaces/components.
Here such a constellation again from the system that I've used before with it's local disk. Now testing a network target reached via the local Wifi adapter going through the Wifi access point to the cable bound GB Ethernet, through a network switch to the target system (a Windows PC with local SATA drives):
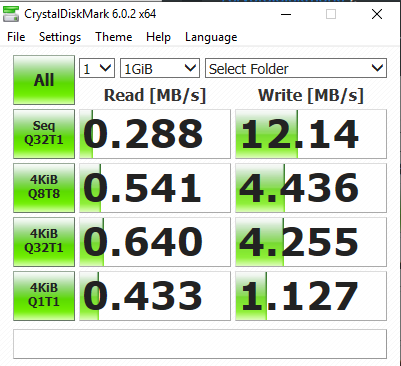
And that's before anything else like a backup software with possibly file indexing and compression comes into play!
I highly recommend that you check out your possibilities in your existing environment in terms of free capacity, performance (DTR) and eventually thinkable interference with other needed services while a backup is running!
Part of your considerations should also be the kind of security needs you want to see realized for your backups.
A local "in same system" backup is in most impacting cases invalid because you possibly cannot access your backup data if an issue strikes on this system.
Removable (storage cards) or mobile data storage (USB sticks, drives) is in most cases very cost effective but has limitations in regard to DTR and security. If something else than a patch, let's say fire, water or a electrical surge cripples your system this might also impact your backup media.
So you'll have to think about safe storage for your backup media after backups.
Using a secondary system/server in your environment with some distance to the backup origin can be way to go if placed somewhere safe. Consumer grade network attached storage is also worth a consideration since these boxes, if battle proven manufacturers are selected, are reliable and give the "biggest bang for the buck".
If you're capacity and performance needs can be covered by a cloud backup service these can be very attractive too but are highly dependent on your internet access speed. On the other hand the requirements of backup target distance to backup origin should be sufficiently covered by using such a service and if they aren't lacking in encryption and access control they are probably one of the better options to get off the ground with backup/recovery with relatively low skills and low effort.
Here an example of a mapped cloud folder that I've tested:
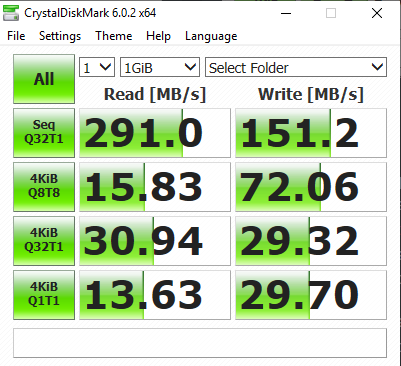
Here I'll drop you some links for free backup tools/utilities:
Linux:
https://help.ubuntu.com/community/BackupYourSystem
Windows:
https://www.lifewire.com/free-backup-software-tools-2617964
https://support.microsoft.com/en-us/help/17085/windows-8-restore-refresh-reset-pc
... and online backup services:
https://www.pcmag.com/roundup/226992/the-best-online-backup-services
https://www.lifewire.com/free-online-backup-plans-2625187
I recommend that you look through the linked articles/resources and that you let this all simmer with you for a while.
Think about your requirements compared to cost and effort for the different solutions.
I don't want to jump the gun on this but there's some reason's for cloud based backup services being very popular. Especially if you're not very tech savvy or have an IT department handy to take care of this.
But please also always have in mind too that "cloud" is just a word for someone else's computer or computers!
Are you're privacy and protection needs covered with a data storage that you don't control?
As I wrote before your questions and suggestions are very welcome!
Please drop a comment if you like!

Gif from my friend @smilinglllama!
