- Guaranteed Future With ~ GOLDILOCK-

GOLDILOCK Since the beginning of cryptocurrencies, the issue of keeping the wallet secure is the priority of individual or institutional investors. To this day, the means of keeping private keys and password is a kind of mundane and inefficient security measures.
It is a new type of storage system, which acts as a cold storage until such time as the user needs to access their funds / data.
When a user needs access to their private data, the physical device that stores their information is connected to the Internet and the user is granted limited time access through non-IP technology with secure authentication layers.
Goldilock is revolutionizing the way data is stored on the Internet by creating an ecosystem to protect cryptocurrencies and digital assets for individuals and institutions.
We base Goldilock on the premise that your data should not be physically connected to the Internet when you are not using it, but that it should be available to you from anywhere immediately when you want to access it.
A digital asset management system, we can also say that it is responsible for storing, managing, organizing, processing and distributing digital assets. Its objective is to simplify the management of digital assets and provide authorized users with the search and recovery of the asset that they need. The value of the managed asset is materialized only if it is accessible by authorized users at the time they need it.
We base Goldilock on the premise that your data should not be physically connected to the Internet when you are not using it, but that it should be available to you from anywhere immediately when you want to access it.
A digital asset management system, we can also say that it is responsible for storing, managing, organizing, processing and distributing digital assets. Its objective is to simplify the management of digital assets and provide authorized users with the search and recovery of the asset that they need. The value of the managed asset is materialized only if it is accessible by authorized users at the time they need it.
This type of platform provides security among digital asset issuers, developers' applications and consumers. In addition, tasks related to asset management are decoupled, such as issuance, transaction processing, the deletion of user funds and the establishment of user identities.
It is usual for these systems to associate each digital asset with metadata for, for example, describing the asset itself, indicating who owns the property, categorizing etc.
The chain block technology is especially useful for this type of systems because they act as accounting books of assets and take advantage of the security properties of block chains: Impossibility of falsifications, immutability, disintermediation, easy transfer, transparency, ease of audit, no overload related to transaction processing and network effect produced by having a unified infrastructure for multiple types of tokens.
For example you can use the block chain and the GOLDILOCK platform to perform any type of management without problem
-Recording of creation test to obtain the property.
-Implementation of intelligent contracts.
-blockchain security
For works that have not been created from the principles on a system based on a chain of blocks it is fundamental to determine a criterion to accept the registration of ownership of a certain digital asset Your digital files are the backbone of the production, distribution and sale of your products.
Your digital files are the backbone of the production, distribution and sale of your products.

Our digital asset management system is more than text documents, images and presentations, it also allows you to collaborate in those files that give life to your fashion products. In the digital world there are millions of people working every day to carry out malicious attacks and get your information to modify or destroy it, no matter how big or small your company, there will always be a person with your eyes on your website.
Cryptocurrency investors and confidential digital asset managers are now forced to choose between personal hardware cold storage solutions, which can be stolen, pirated, lost, destroyed or confiscated; and attractive online wallets, which are vulnerable to piracy, denial of service and custody and collapse companies. Without a secure, scalable and secure Cryptographic Key Custody solution, both institutions and individuals continue to be plagued by frequent financial losses due to mishandling of their keys.
Traditional cold storage solutions are not the answer to provide investors with proper key management.
The storage solutions offered by groups such as Xapo or Coinbase have an extremely limited accessibility that does not address most of the institutional custody needs.
Hot storage solutions are also inadequate with regard to key custody.
In short: anything connected to the Internet can be hacked. Taking into account the 4,000 million unfulfilled records that affect email providers, banks, and credit card accounts in the last two years, and given that more than $ 1.2 billion in Cryptocurrency have been stolen in that same period , it is clear that the traditional digital asset storage industry is compromised
Storage solutions are designed to meet your needs and control your business as it grows and changes in an effective and innovative way. Storage solutions provide excellent response times, high levels of availability and great scalability, allowing you to maintain the operational continuity of your mission critical systems. Solution for your cryptocurrency. Paper and USB keys can be lost, stolen or damaged
It is important to emphasize that data growth is inevitable for any organization.
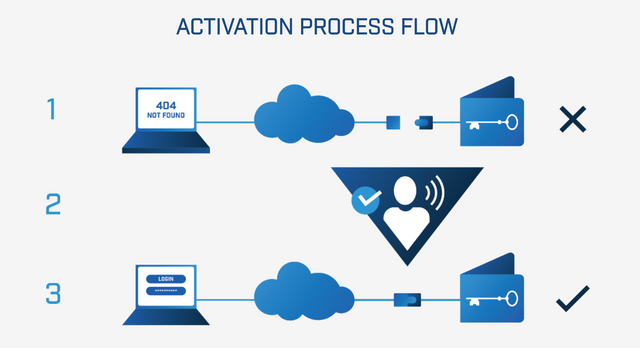
Goldilock's patent-pending technology treats these premises as requirements for the custody of private keys and the safer storage of personal data without sacrificing accessibility. Relying on a proven framework of innovative technologies and processes, Goldilock offers a unique solution for key storage and data storage.
Digital assets are real-world assets (property titles, automobile titles, currency, etc.) in the form of electronic data. The idea is to use smart contracts and digital identities that are enforced by law / verification.
The vision is to create a complete economy to operate using these contracts without the need to trust each other, all while it is traceable, transparent and free from intermediaries.
According to Neo's white paper, Neo has two forms of digital assets: global assets and contractual assets.
Goldilock chose the NEO network for the LOCK token because of our alignment with his vision and philosophy in the future of blockchain. Its focus on governance and compliance, digital assets, digital identity and Smart Contracts provides a solid foundation for Goldilock Security Suite. In addition, its investment in thematic and community ecosystems ensures that NEO will be able to meet the needs of its developers and consumers as an evolving platform. Goldilock is revolutionizing the way data is stored on the Internet by creating an ecosystem to protect cryptocurrencies and digital assets for individuals and institutions

NEO specializes in blockchain technology and aims to build an open network that uses digital assets, digital identities and smart contracts to serve the smart economy in the future. The dBFT consensus mechanism, the NeoContract intelligent contract system and the NeoX cross-chain protocol were originally developed by NEO, a technology expert community that specializes in blockchain core technologies. With the growth of the community, NEO has expanded from an open source project based in China to a leading public block chain in the world with the support of GOLDILOCK
**NeoContract** Neo has global assets within smart contracts that require the need for reliable replication across the network. That reproduction can only be achieved through the use of timestamps, random number generators or data storage. Using any of those three reference points, the chain of blocks can remain verified. If Neo did not have those three points of reference, it would mean that every time a contract was referenced by the blockchain, the network would have difficulties to verify the block. Another good feature of NeoContracts is that they are developer friendly, unlike Ethereum. The NeoContract intelligent contract system is the most important feature of integration of the existing developer ecosystem. The Neo Universal Light Virtual Machine, NeoVM, has the advantages of high security, high concurrency and high scalability. The NeoContract intelligent contract system will allow millions of developers around the world to quickly carry out the development of smart contracts.
The holders of NEO tokens are the owners and managers of networks, they manage the network through voting in the network. NEO tokens can be transferred. The NEO token holder can, by voting, choose the counter that he supports. The selected group of accountants, through the BFT algorithm, reaches consensus and generates new blocks.
The NEO dBFT consensus mechanism takes about 15 to 20 seconds to generate a block.
The LOCK token allows Goldilock to provide users with a record of their node's activity, while retaining the data owned by the encrypted and enclosed user, including everyone, including the Goldilock team.
Goldilock will obtain a total of 1 billion LOCK tokens as part of the implementation of the contract in the NEO Blockchain. Additional LOCK tokens will not be coined for use on the platform
Neo's block chain uses two Neo and Gas tokens.
Unlike Ethereum, Neo decoupled the gas from its base token. If you have ever paid or looked at a transaction in the ethereum network, you will see that the transaction costs are paid in gas.
While in the Neo block chain, Gas is a completely different token given to the Neo holders as a test of interest as an incentive. As Gas is required to execute smart contracts, the more companies that use the Neo platform, the more gas will be needed, which will provide purchasing pressure. This project is really useful for both individuals and companies. As the world becomes increasingly digital, more and more hackers are finding new ways to mess with people who do not have a high level of computer literacy. To preserve the project and protect taxpayers from selling tokens, there will be a mandatory period of six (6) months Moratorium on the sale of LOCK tokens for all founders and advisors. This policy will be integrated into the intelligent system.
The integrity of the blockchain payment system depends on the actions of independent "miners" who compete to solve the next cryptogenic blockchain puzzle. The solution to the puzzle creates a permanent record of bitcoin transactions, and the "mining" winner wins bitcoin as a reward, bitcoin is tightly controlled by open source software to ensure that the value of the cryptocurrency can never be degraded. Distributed blockchain ledger technology, which makes Bitcoin and other cryptocurrencies possible, supports a transnational payment system that does not need banks or governments to operate.
Unfortunately, the blockchain is not tamper-proof. A single "miner" with too much computing power can manipulate the time of the transactions in the chain of blocks and potentially falsify the cryptocurrency. This risk is greater than initially believed, and no government monitors the computing power of individual mining firms to guarantee the integrity of the blockchain payment mechanism. While the blockchain registers cryptocurrency payments between two virtual purses, bitcoin and other cryptocurrencies must have additional functionality to be viable substitutes for national currencies. For example, cryptocurrencies should be exchanged easily and securely by national currencies. To use a cryptocurrency exchange, the owner of a currency must transfer the virtual currency to the exchange or provide the change with the national currency to buy cryptocurrencies. In any case, the customer's cryptocurrency is stored in the virtual wallet of the exchange. Unlike regulated exchanges, there is no law or regulation that requires customer balances to be segregated from exchange balances. If the exchange is declared bankrupt due to fraud or mismanagement, or the virtual wallet of the stock market is pirated, the customer's cryptocurrency balances may be lost.
While the blockchain registers cryptocurrency payments between two virtual purses, bitcoin and other cryptocurrencies must have additional functionality to be viable substitutes for national currencies. For example, cryptocurrencies should be exchanged easily and securely by national currencies. To use a cryptocurrency exchange, the owner of a currency must transfer the virtual currency to the exchange or provide the change with the national currency to buy cryptocurrencies. In any case, the customer's cryptocurrency is stored in the virtual wallet of the exchange. Unlike regulated exchanges, there is no law or regulation that requires customer balances to be segregated from exchange balances. If the exchange is declared bankrupt due to fraud or mismanagement, or the virtual wallet of the stock market is pirated, the customer's cryptocurrency balances may be lost.

FOR THAT WE BRING YOU THE ONLY AND SECURE PLATFORM GOLDILOCK GENERATES US SAFETY AND SIMPLE AT THE TIME OF THE SECURITY OF YOUR VIRTUAL PURSE OR BAGLETERA
Since then we have found this system, a program that helps us save and keep once again your money in a virtual way, going beyond the extraordinary. Integrate and follow us. We guarantee absolute security.
A safe space for business The DPOS chains secure the blockchain network by allowing coin holders to choose representatives who then process the chain's transactions. It is this model of representative government, together with the superior software performance of EOS, that will make EOS the first block chain appropriate for companies.
Virtual wallets can be considered the most important financial innovation after the appearance of ATMs, depending on their usefulness and the security they provide, since their operation is through encrypted operations. A wallet or encrypted virtual wallet, is a means by which you can save, send and receive any cryptocurrency or data, therefore, it is a safe way to save funds
Virtual wallets can be compatible with a single cryptocurrency, be multi-crypto currency, or handle traditional currency issued by a government bank.
This technology is the result of the advances that have been experienced in recent years and that have a significant impact on our daily lives. The payment of goods and services through electronic means is becoming more widespread every day and among them virtual wallets are now counted, which turn the cell phone into a tool to carry out transactions. The management of personal finances through electronic means has had an impact on the gradual reduction of the dependence on cash, creating a system that allows us to carry out transactions immediately, through the use of mobile devices , especially of smartphones, whose use is the most widespread worldwide; hence, virtual wallets are emerging as a viable and convenient means of payment.
As this is a fairly recent issue, it is useful to contextualize and explain what virtual wallets are and other factors linked to them, such as the reduction of cash, the decrease in dependence on central banks, and the development of cryptocurrencies. At present, alternative means are generated to the currency issued by a central-government bank: The Cryptocurrencies.
A cryptocurrency or cryptocurrency is basically a digital medium of exchange, the first to be known was Bitcoin, in 2009. Since then, many more digital coins have appeared, similar with their features and protocols, which merit for handling, be stored in virtual wallets. The cryptocurrencies are a substitute for the money issued by the monetary authority, this makes them a kind of private money, because as we have pointed out, they are not controlled by any central bank and their quotation depends on the market supply and demand, and not of factors such as political and economic stability.
Digital personal identity data requires a high level of security. There are many services that require personal data to register, this can range from KYC to enrolling in an insurance policy. Traditionally, people physically handle documents or scan and e-mail the required information. The digital identity is currently booming in the field of marketing and is known as corporate digital identity, but in this work the concept of digital identity will be limited to everything that identifies an individual in the web environment. Neither the possible names adopted by Internet users nor their avatars will be addressed.
The purpose of this article is to address the issue of personal digital identity management, which is defined as the ability to successfully manage one's visibility, reputation and privacy in the network as an inseparable and fundamental component of the set of digital and information skills. which have become fundamental to live in the information society. Next, the concepts of visibility, reputation and privacy are detailed in more depth, and information and digital skills are defined.
The digital identity is what we are for others on the Net or, rather, what the Network says we are to others. It is not defined a priori and it is conforming with our participation, direct or inferred, in the different communities and Internet services
With Goldilock, users would be granted access to their documents by necessity. After the user has finished performing their identity verification, the data is again out of line, inaccessible for anyone to see or access.
In my case, I am a casino salsa dancer, and daily I have to travel from state to state; and it is difficult for me to load my documents, since I have to keep an eye on my suitcase and the protocol of the event.
Goldilock Team

Conclusión
For more information watch this short feature intro:
But with GOLDILOCK life became easier, simpler and SAFER, since I can leave my documents and my cryptocurrency wallet at home, where they belong. I can also store relevant data with Goldilock and access my data whenever I need it.
Only the best are those who are part of this great team. Composed of the brightest minds in the market that undoubtedly

From a simple commercial perspective, security at the highest level makes sense. Recent and persistent hacks of cryptocurrency exchanges, key theft and misuse have cost billions of dollars. We look for enough potential to make a curve in the cryptographic space. That there is knowledge of this platform, that people like it and that it seems attractive, safe and reliable when entering this GOLDILOCK program. There is something that is certain and is that this project challenges Ethereum and gives the vision a systematic echo for improvement. They have decades of experience in various fields ranging from hedge fund management to software development and cybersecurity.

This post has been submitted for the @OriginalWorks Sponsored Writing Contest!
You can also follow @contestbot to be notified of future contests!